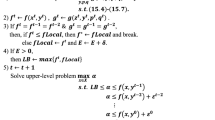Abstract
This article discusses a robust network interdiction problem considering uncertainties in arc capacities and resource consumption. The problem involves two players: an adversary seeking to maximize the flow of a commodity through the network and an interdictor whose objective is to minimize this flow. The interdictor plays first and selects network arcs to interdict, subject to a resource constraint. The problem is formulated as a bilevel problem, and an upper bound single level mix-integer linear formulation is derived. The upper bound formulation is solved using three heuristics tailored for this problem and the network structure, based on Lagrangian relaxation and Benders’ decomposition. On average, each heuristic provides a reduction in run time of at least 85% compared to a state-of-the-art solver. Enhanced Benders’ decomposition achieves a solution with an optimality gap of less than 5% for all tested instances. Sensitivity analyses are conducted for the level of uncertainty in network parameters and the uncertainty budget. Robust decisions are also compared to decisions not accounting for uncertainty to evaluate the value of robustness, showing a reduction in simulation maximum flows by as much as 89.5%.








Similar content being viewed by others
Notes
Gurobi optimizer reference manual (2019) URL: https://www.gurobi.com
References
Abusorrah, A., Alabdulwahab, A., Li, Z., & Shahidehpour, M. (2017). Minimax-regret robust defensive strategy against false data injection attacks. IEEE Transactions on Smart Grid, 10(2), 2068–2079.
Ahuja, R. K., Magnanti, T. L., & Orlin, J. B. (1993). Network flows: Theory, algorithms, and applications. Prentice-Hall Inc.
Ala, A., Alsaadi, F. E., Ahmadi, M., & Mirjalili, S. (2021). Optimization of an appointment scheduling problem for healthcare systems based on the quality of fairness service using whale optimization algorithm and nsga-ii. Scientific Reports, 11(1), 19,816.
Ala, A., & Chen, F. (2020). Alternative mathematical formulation and hybrid meta-heuristics for patient scheduling problem in health care clinics. Neural Computing and Applications, 32, 8993–9008.
Ala, A., Simic, V., Pamucar, D., & Tirkolaee, E. B. (2022). Appointment scheduling problem under fairness policy in healthcare services: Fuzzy ant lion optimizer. Expert Systems with Applications, 207, 117–949.
Altner, D. S., Ergun, Ö., & Uhan, N. A. (2010). The maximum flow network interdiction problem: Valid inequalities, integrality gaps, and approximability. Operations Research Letters, 38(1), 33–38.
Aminoshariae, A., Kulild, J., & Nagendrababu, V. (2021). Artificial intelligence in endodontics: Current applications and future directions. Journal of Endodontics, 47(9), 1352–1357.
Amjadian, A., & Gharaei, A. (2022). An integrated reliable five-level closed-loop supply chain with multi-stage products under quality control and green policies: Generalised outer approximation with exact penalty. International Journal of Systems Science: Operations & Logistics, 9(3), 429–449.
Arentze, T., & Timmermans, H. (2005). Information gain, novelty seeking and travel: A model of dynamic activity-travel behavior under conditions of uncertainty. Transportation Research Part A: Policy and Practice, 39(2–3), 125–145.
Askari, R., Sebt, M. V., & Amjadian, A. (2021). Logistics and supply chain management: 7th international conference, LSCM 2020, Tehran, Iran, December 23–24, 2020, Revised Selected Papers 7, (pp. 161–193). Springer.
Assimakopoulos, N. (1987). A network interdiction model for hospital infection control. Computers in Biology and Medicine, 17(6), 413–422.
Ayyildiz, E., Özçelik, G., & Gencer, C. T. (2018). Determining the most vital arcs on the shortest path for fire trucks in terrorist actions that will cause fire. Communications Series A1 Mathematics & Statistics, 68(1), 441–450.
Azizi, E., & Seifi, A. (2023). Shortest path network interdiction with incomplete information: A robust optimization approach. Annals of Operations Research. https://doi.org/10.1007/s10479-023-05350-1
Baggio, A., Carvalho, M., Lodi, A., & Tramontani, A. (2021). Multilevel approaches for the critical node problem. Operations Research, 69(2), 486–508.
Bao, S., Zhang, C., Ouyang, M., & Miao, L. (2019). An integrated tri-level model for enhancing the resilience of facilities against intentional attacks. Annals of Operations Research, 283(1), 87–117.
Benders, J. F. (1962). Partitioning procedures for solving mixed-variables programming problems. Numerische Mathematik, 4(1), 238–252.
Ben-Tal, A., El Ghaoui, L., & Nemirovski, A. (2009). Robust optimization (Vol. 28). Princeton University Press.
Ben-Tal, A., & Nemirovski, A. (1999). Robust solutions of uncertain linear programs. Operations Research Letters, 25(1), 1–13.
Ben-Tal, A., & Nemirovski, A. (2002). Robust optimization-methodology and applications. Mathematical Programming, 92(3), 453–480.
Bertsekas, D. P. (1991). Linear network optimization: algorithms and codes. MIT Press.
Bertsimas, D., Brown, D. B., & Caramanis, C. (2011). Theory and applications of robust optimization. SIAM Review, 53(3), 464–501.
Bertsimas, D., Nasrabadi, E., & Stiller, S. (2013). Robust and adaptive network flows. Operations Research, 61(5), 1218–1242.
Bertsimas, D., & Sim, M. (2003). Robust discrete optimization and network flows. Mathematical Programming, 98(1–3), 49–71.
Bertsimas, D., & Sim, M. (2004). The price of robustness. Operations Research, 52(1), 35–53.
Bingol, L. (2001). A Lagrangian heuristic for solving a network interdiction problem. Master’s thesis, Naval Postgraduate School Monterey, CA.
Borrero, J. S., Prokopyev, O. A., & Sauré, D. (2016). Sequential shortest path interdiction with incomplete information. Decision Analysis, 13(1), 68–98.
Borrero, J. S., Prokopyev, O. A., & Sauré, D. (2019). Sequential interdiction with incomplete information and learning. Operations Research, 67(1), 72–89.
Boyd, S. P., & Vandenberghe, L. (2004). Convex optimization. Cambridge University Press.
Chaerani, D., & Roos, C. (2006). Modelling robust design problems. Annual International Conference of the German Operations Research Society (GOR), Karlsruhe.
Chaerani, D., & Roos, C. (2007). Operations research proceedings 2006 (pp. 209–214). Springer.
Cheng, C., Qi, M., Zhang, Y., & Rousseau, L. M. (2018). A two-stage robust approach for the reliable logistics network design problem. Transportation Research Part B: Methodological, 111, 185–202.
Chen, R. L. Y., Musselman, A., & Wu, J. (2016). A robust optimization approach for network interdiction. Tech. rep.
Chen, A., Yang, H., Lo, H. K., & Tang, W. H. (2002). Capacity reliability of a road network: An assessment methodology and numerical results. Transportation Research Part B: Methodological, 36(3), 225–252.
Cormican, K. J. (1995). Computational methods for deterministic and stochastic network interdiction problems. Master’s thesis, Naval Postgraduate School Monterey, CA.
Costa, A., Georgiadis, D., Ng, T. S., & Sim, M. (2018). An optimization model for power grid fortification to maximize attack immunity. International Journal of Electrical Power & Energy Systems, 99, 594–602.
Dimitrov, N. B., Michalopoulos, D. P., Morton, D. P., Nehme, M. V., Pan, F., Popova, E., Schneider, E. A., & Thoreson, G. G. (2011). Network deployment of radiation detectors with physics-based detection probability calculations. Annals of Operations Research, 187(1), 207–228.
Fischetti, M., Ljubić, I., Monaci, M., & Sinnl, M. (2019). Interdiction games and monotonicity, with application to knapsack problems. INFORMS Journal on Computing, 31(2), 390–410.
Fisher, M. L. (1981). The Lagrangian relaxation method for solving integer programming problems. Management Science, 27(1), 1–18.
Fisher, M. L. (1985). An applications oriented guide to Lagrangian relaxation. Interfaces, 15(2), 10–21.
Gabrel, V., Murat, C., & Thiele, A. (2014). Recent advances in robust optimization: An overview. European Journal of Operational Research, 235(3), 471–483.
Gharaei, A., & Almehdawe, E. (2020). Economic growing quantity. International Journal of Production Economics, 223, 107–517.
Gharaei, A., Amjadian, A., Amjadian, A., Shavandi, A., Hashemi, A., Taher, M., & Mohamadi, N. (2023). An integrated lot-sizing policy for the inventory management of constrained multi-level supply chains: Null-space method. International Journal of Systems Science: Operations & Logistics, 10(1), 2083,254.
Gharaei, A., Amjadian, A., & Shavandi, A. (2023). An integrated reliable four-level supply chain with multi-stage products under shortage and stochastic constraints. International Journal of Systems Science: Operations & Logistics, 10(1), 1958,023.
Gharaei, A., Hoseini Shekarabi, S. A., & Karimi, M. (2020). Modelling and optimal lot-sizing of the replenishments in constrained, multi-product and bi-objective EPQ models with defective products: Generalised cross decomposition. International Journal of Systems Science: Operations & Logistics, 7(3), 262–274.
Gharaei, A., Hoseini Shekarabi, S. A., & Karimi, M. (2023). Optimal lot-sizing of an integrated EPQ model with partial backorders and re-workable products: An outer approximation. International Journal of Systems Science: Operations & Logistics, 10(1), 2015,007.
Gharaei, A., Hoseini Shekarabi, S. A., Karimi, M., Pourjavad, E., & Amjadian, A. (2021). An integrated stochastic EPQ model under quality and green policies: Generalised cross decomposition under the separability approach. International Journal of Systems Science: Operations & Logistics, 8(2), 119–131.
Gharaei, A., Karimi, M., & Hoseini Shekarabi, S. A. (2019). An integrated multi-product, multi-buyer supply chain under penalty, green, and quality control polices and a vendor managed inventory with consignment stock agreement: The outer approximation with equality relaxation and augmented penalty algorithm. Applied Mathematical Modelling, 69, 223–254.
Gharaei, A., Karimi, M., & Hoseini Shekarabi, S. A. (2020). Joint economic lot-sizing in multi-product multi-level integrated supply chains: Generalized benders decomposition. International Journal of Systems Science: Operations & Logistics, 7(4), 309–325.
Gharaei, A., Karimi, M., & Hoseini Shekarabi, S. A. (2023). Vendor-managed inventory for joint replenishment planning in the integrated qualitative supply chains: Generalised benders decomposition under separability approach. International Journal of Systems Science: Operations & Logistics, 10(1), 1962,,428.
Goldberg, A. V., & Tarjan, R. E. (1988). A new approach to the maximum-flow problem. Journal of the ACM (JACM), 35(4), 921–940.
Gorissen, B. L., Yanıkoğlu, İ, & den Hertog, D. (2015). A practical guide to robust optimization. Omega, 53, 124–137.
Gottschalk, C., Koster, A. M., Liers, F., Peis, B., Schmand, D., & Wierz, A. (2018). Robust flows over time: Models and complexity results. Mathematical Programming, 171(1–2), 55–85.
Grépin, K. A., Ho, T. L., Liu, Z., Marion, S., Piper, J., Worsnop, C. Z., & Lee, K. (2021). Evidence of the effectiveness of travel-related measures during the early phase of the COVID-19 pandemic: A rapid systematic review. BMJ Global Health, 6(3), e004,537.
Guo, Q., An, B., Zick, Y., & Miao, C. (2016). Proceedings of the twenty-fifth international joint conference on artificial intelligence (IJCAI-16), pp. 2507–2513.
Han, S., Peng, Z., & Wang, S. (2014). The maximum flow problem of uncertain network. Information Sciences, 265, 167–175.
Hoseini Shekarabi, S. A., Gharaei, A., & Karimi, M. (2019). Modelling and optimal lot-sizing of integrated multi-level multi-wholesaler supply chains under the shortage and limited warehouse space: generalised outer approximation. International Journal of Systems Science: Operations & Logistics, 6(3), 237–257.
Israeli, E., & Wood, R. K. (2002). Shortest-path network interdiction. Networks: An International Journal, 40(2), 97–111.
James, L. P., Salomon, J. A., Buckee, C. O., & Menzies, N. A. (2021). The use and misuse of mathematical modeling for infectious disease policymaking: Lessons for the COVID-19 pandemic. Medical Decision Making, 41(4), 379–385.
Johnson, M. P., Gutfraind, A., & Ahmadizadeh, K. (2014). Evader interdiction: Algorithms, complexity and collateral damage. Annals of Operations Research, 222(1), 341–359.
Kenney, M. C. (2003). Intelligence games: Comparing the intelligence capabilities of law enforcement agencies and drug trafficking enterprises. International Journal of Intelligence and CounterIntelligence, 16(2), 212–243.
Ketkov, S. S., Prokopyev, O. A., & Burashnikov, E. P. (2019). An approach to the distributionally robust shortest path problem. arXiv preprint arXiv:1910.08744.
Kosmas, D., Sharkey, T. C., Mitchell, J. E., Maass, K. L., & Martin, L. (2022). Multi-period max flow network interdiction with restructuring for disrupting domestic sex trafficking networks. Annals of Operations Research. https://doi.org/10.1007/s10479-022-05087-3
Laporte, G., Mesa, J. A., & Perea, F. (2010). A game theoretic framework for the robust railway transit network design problem. Transportation Research Part B: Methodological, 44(4), 447–459.
Lasdon, L. S. (2002). Optimization theory for large systems. Dover Publications Inc.
Lee, C., Lee, K., Park, K., & Park, S. (2012). Branch-and-price-and-cut approach to the robust network design problem without flow bifurcations. Operations Research, 60(3), 604–610.
Lim, C., & Smith, J. C. (2007). Algorithms for discrete and continuous multicommodity flow network interdiction problems. IIE Transactions, 39(1), 15–26.
Li, X., & Ouyang, Y. (2011). Reliable sensor deployment for network traffic surveillance. Transportation Research Part B: Methodological, 45(1), 218–231.
Loh, K. H. (1991). Modelling strategic strikes against transportation networks. Master’s thesis, Naval Postgraduate School Monterey, CA.
Losada, C., Scaparra, M. P., Church, R. L., & Daskin, M. S. (2012). The stochastic interdiction median problem with disruption intensity levels. Annals of Operations Research, 201(1), 345–365.
Lozano, L., & Smith, J. C. (2019). A brief overview of interdiction and robust optimization. Optimization in Large Scale Problems: Industry 4.0 and Society 5.0 Applications. https://doi.org/10.1007/978-3-030-28565-4_7
Lunday, B. J., & Sherali, H. D. (2012). Network interdiction to minimize the maximum probability of evasion with synergy between applied resources. Annals of Operations Research, 196(1), 411–442.
MacKay, R. S., Johnson, S., & Sansom, B. (2020). How directed is a directed network? Royal Society open science, 7(9), 201,138.
Magliocca, N. R., McSweeney, K., Sesnie, S. E., Tellman, E., Devine, J. A., Nielsen, E. A., Pearson, Z., & Wrathall, D. J. (2019). Modeling cocaine traffickers and counterdrug interdiction forces as a complex adaptive system. Proceedings of the National Academy of Sciences, 116(16), 7784–7792.
Matisziw, T. C., & Murray, A. T. (2009). Modeling s-t path availability to support disaster vulnerability assessment of network infrastructure. Computers & Operations Research, 36(1), 16–26.
Meyer, A. D., & Anderson, D. P. (2008). The air national guard and the war on drugs: Non-state actors before 9/11. Air Power History, 55(3), 12–29.
Minoux, M. (2009). On robust maximum flow with polyhedral uncertainty sets. Optimization Letters, 3(3), 367–376.
Mirzaei, M., Al-e, S. M. J. M., Shirazi, M. A., et al. (2021). A maximum-flow network interdiction problem in an uncertain environment under information asymmetry condition: Application to smuggling goods. Computers & Industrial Engineering, 162, 107–708.
Monaci, M., Pferschy, U., & Serafini, P. (2013). Exact solution of the robust knapsack problem. Computers & operations research, 40(11), 2625–2631.
Morton, D. P., Pan, F., & Saeger, K. J. (2007). Models for nuclear smuggling interdiction. IIE Transactions, 39(1), 3–14.
Nguyen, D. H., & Smith, J. C. (2022). Network interdiction with asymmetric cost uncertainty. European Journal of Operational Research, 297(1), 239–251.
Noyan, N., Rudolf, G., & Lejeune, M. (2018). Distributionally robust optimization with decision-dependent ambiguity set. Optimization Online http://www.optimization-online.org/DBHTML/2018/09/6821.html.
Pan, F., & Morton, D. P. (2008). Minimizing a stochastic maximum-reliability path. Networks: An International Journal, 52(3), 111–119.
Parvaresh, F., Husseini, S. M., Golpayegany, S. H., & Karimi, B. (2014). Hub network design problem in the presence of disruptions. Journal of Intelligent Manufacturing, 25(4), 755–774.
Paul, J. A., & Wang, X. J. (2019). Robust location-allocation network design for earthquake preparedness. Transportation Research Part B: Methodological, 119, 139–155.
Peng, P., Snyder, L. V., Lim, A., & Liu, Z. (2011). Reliable logistics networks design with facility disruptions. Transportation Research Part B: Methodological, 45(8), 1190–1211.
Rahmaniani, R., Crainic, T. G., Gendreau, M., & Rei, W. (2017). The benders decomposition algorithm: A literature review. European Journal of Operational Research, 259(3), 801–817.
Reddy, K. N., Kumar, A., Choudhary, A., & Cheng, T. E. (2022). Multi-period green reverse logistics network design: An improved benders-decomposition-based heuristic approach. European Journal of Operational Research, 303(2), 735–752.
Rocco, C. M. S., & Ramirez-Marquez, J. E. (2010). A bi-objective approach for shortest-path network interdiction. Computers & Industrial Engineering, 59(2), 232–240.
Rodgers, N., Tiňo, P., & Johnson, S. (2023). Strong connectivity in real directed networks. Proceedings of the National Academy of Sciences, 120(12), e2215752,120.
Royset, J. O., & Wood, R. K. (2007). Solving the bi-objective maximum-flow network-interdiction problem. INFORMS Journal on Computing, 19(2), 175–184.
Sadana, U., & Delage, E. (2020). The value of randomized strategies in distributionally robust risk averse network interdiction games. arXiv preprint arXiv:2003.07915.
Schrijver, A., et al. (2003). Combinatorial optimization: Polyhedra and efficiency (Vol. 24). Springer.
Smith, J. C., & Song, Y. (2019). A survey of network interdiction models and algorithms. European Journal of Operational Research. https://doi.org/10.1016/j.ejor.2019.06.024
Snyder, L. V., Scaparra, M. P., Daskin, M. S., & Church, R. L. (2006). Models, methods, and applications for innovative decision making (INFORMS), pp. 234–257.
Soyster, A. L. (1973). Convex programming with set-inclusive constraints and applications to inexact linear programming. Operations Research, 21(5), 1154–1157.
Steinrauf, R. L. (1991). Network interdiction models. Master’s thesis, Naval Postgraduate School Monterey, CA.
Stozhkov, V., Boginski, V., Prokopyev, O. A., & Pasiliao, E. L. (2017). A simple greedy heuristic for linear assignment interdiction. Annals of Operations Research, 249, 39–53.
Sullivan, K. M., Morton, D. P., Pan, F., & Cole Smith, J. (2014). Securing a border under asymmetric information. Naval Research Logistics (NRL), 61(2), 91–100.
Sumalee, A., Uchida, K., & Lam, W. H. (2011). Stochastic multi-modal transport network under demand uncertainties and adverse weather condition. Transportation Research Part C: Emerging Technologies, 19(2), 338–350.
Taleizadeh, A. A., Safaei, A. Z., Bhattacharya, A., & Amjadian, A. (2022). Online peer-to-peer lending platform and supply chain finance decisions and strategies. Annals of Operations Research, 315(1), 397–427.
Towle, E., & Luedtke, J. (2018). New solution approaches for the maximum-reliability stochastic network interdiction problem. Computational Management Science, 15(3–4), 455–477.
Uygun, A. (2002). Network interdiction by lagrandian relaxation and branch-and-bound. Master’s thesis, Naval Postgraduate School Monterey; CA.
Wada, K., Usui, K., Takigawa, T., & Kuwahara, M. (2018). An optimization modeling of coordinated traffic signal control based on the variational theory and its stochastic extension. Transportation Research Part B: Methodological, 117, 907–925.
Wei, N., & Walteros, J. L. (2022). Integer programming methods for solving binary interdiction games. European Journal of Operational Research, 302(2), 456–469.
Wood, R. K. (1993). Deterministic network interdiction. Mathematical and Computer Modelling, 17(2), 1–18.
Wood, R. K. (2010). Bilevel network interdiction models: Formulations and solutions. Wiley.
Yuan, W., Wang, J., Qiu, F., Chen, C., Kang, C., & Zeng, B. (2016). Robust optimization-based resilient distribution network planning against natural disasters. IEEE Transactions on Smart Grid, 7(6), 2817–2826.
Acknowledgements
This work was supported by the National Science Foundation through grants CMMI-1826320/1826337: Collaborative Research: Real-Time Stochastic Matching Models for Freight Electronic Marketplace, CMMI-1562109/1562291: Collaborative Research: Non-Additive Network Routing and Assignment Models, and CMMI-1254921: CAREER: Integrated Multiresolution Transportation Network Modeling.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A Lagrangian relaxation sub-problems
The sub-problems of the Lagrangian Dual (presented in Sect. 4.2) and their solutions are:
Sub-problem 1:
The dual of the sub-problem 1 results in a maximum flow problem with updated capacities, as in Bingol (2001).
Sub-problem 2:
The solution to the above problem is trivial.
Sub-problem 3:
The solution to the above problem is trivial.
Sub-problem 4:
The solution to the above problem is trivial.
Sub-problem 5:
The solution to the above problem is trivial.
Note that without the upper bounds found in Sect. 4.1, the sub-problems 2–5 could result in unbounded solutions.
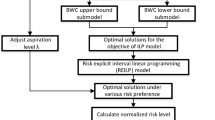
Appendix B Simultaneous penalty heuristic for Benders’ decomposition master problem
A heuristic is designed for quick computation of the master problem of Benders’ decomposition. It should be noted that the heuristic solution provides and approximate solution for the master problem. The equivalent formulation of the master problem of Benders’ decomposition as noted in Eqs. 81–89, is given as:
where, O is the set of Benders’ decomposition optimality cuts, and \(\gamma ^o_{ij}\) represents \(\gamma _{ij}\) values for the cut o. Equation B3 is the resource robustness constraint for the RNIP, written as a set of combinatorially many constraints instead of a single constraint with maximization, which was dualized in order to obtain the final RNIP model formulation (refer MODEL 2 in Sect. 3.4).
The motivation for the heuristic is to account for \( |O |\) constraints (in Eq. B2) using a single constraint. This would reduce the master problem to a network interdiction problem with resource consumption uncertainty only (NIPRCU). NIPRCU can be solved by first finding the min-cut of the network using representative capacities, and determining the arc set available for interdiction (\(A_I\)). Then, determining \(\delta \) (the interdiction decision) variables is a robust knapsack problem with arc capacities as item values, resource consumption as item weights, and \(\Delta \) is the capacity of the knapsack (solution procedure proposed by Lee et al. (2012) is used for solving the robust knapsack problem). Once, \(\delta \) variables are determined, the \(\beta \) variables can be easily determined, as they are forward arcs of the minimum cut which are not interdicted.
Calculating representative arc capacities of the network with respect to \({o^{th}}\) optimality cut:
The method simultaneously penalizes the presence of optimality cuts in the set \(O\backslash \{o\}\) with respect to the \(o^{th}\) optimality cut to calculate the representative arc capacities for the network. The penalty with respect to the \(o^{th}\) optimality cut is calculated as:
The representative arc capacities of the network with respect to the \(o^{th}\) optimality cut (\(\tilde{u}^o\)) are then given as:
Steps for solving the Benders’ Master Problem using the simultaneous penalty heuristic:
For each \(o \in O\),
-
1.
Calculate the representative arc capacities for the network (\(\tilde{u}^o\)) with respect to optimality cut o.
-
2.
Determine the min-cut (\(N_s,N_t\)) of the network. The variable \(\alpha ^o\) and the interdiction arc set (\(A_I\)) for the network are given as:
$$\begin{aligned} \alpha ^o_i&= {\left\{ \begin{array}{ll} 1 &{} ; \text {if}\, i \in N_t \\ 0 &{} ; \text {if}\,i \in N_s \end{array}\right. } \\ A_I&= \big \{(i,j) \in A' \,\, \big |\,\, \alpha ^o_j-\alpha ^o_i = 1 \text { and } r_{ij}\le \Delta \text { and } \gamma ^o_{ij}=0 \big \} \end{aligned}$$ -
3.
Initialize \(\delta ^o\) variables by solving the robust knapsack problem with parameters \(c=\tilde{u}^o\), \(w = r\), \(\hat{w} = \hat{r}\), \(b = \Delta \), \(N = A_I\), and \(\Gamma = \Pi \) (refer Bertsimas and Sim 2003)
-
4.
The value of \(\zeta ^o\) is the \(\Pi ^{th}\) largest value of \(\hat{r}_{ij}\delta ^o_{ij}\).
-
5.
The values of variables \(\sigma ^o\) are given as: \(\sigma ^o_{ij}= \max \{0, \hat{r}_{ij} - \zeta ^o \}\)
-
6.
Determine the \(\beta ^o\) variables as follows:
$$\begin{aligned} \beta ^o_{ij} = {\left\{ \begin{array}{ll} 1 &{} ; \text {if}\, \alpha ^o_j - \alpha ^o_i = 1{ and}\delta ^o_{ij} = 1\\ 0 &{} ; \text {otherwise} \end{array}\right. } \end{aligned}$$(B11) -
7.
The value of \(z^o\) is \(\sum \limits _{(i,j)\in A'}\tilde{u}^o_{ij}\beta ^o_{ij}\)
The solution of the master problem is then given as:
Appendix C Monte-Carlo simulation for evaluating value of robustness
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chauhan, D., Unnikrishnan, A., Boyles, S.D. et al. Robust maximum flow network interdiction considering uncertainties in arc capacity and resource consumption. Ann Oper Res 335, 689–725 (2024). https://doi.org/10.1007/s10479-023-05812-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10479-023-05812-6