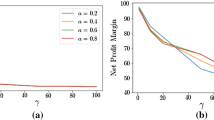
Abstract
Hub-and-spoke networks play a critical role in reducing cost and enhancing service levels in various infrastructural sectors since hubs act as the consolidation and transshipment points of the flows. The failure of hubs in such a network can cause severe disruptions. While disruptions can be natural or man-made, a disruption by a rational individual or entity can be significantly detrimental to the network and is often studied as an interdiction problem. It is important to take interdiction effects at the design stage; therefore, we study the three-level capacitated hub-and-spoke network design problem from the perspective of a defender who considers the risk of interdiction by a rational attacker. Within the three levels, the upper level represents the network design level, and the lower two levels represent the bi-level hub interdiction problem. The introduction of capacity constraints within an interdiction model dramatically increases the complexity of the problem, as there can be some unfulfilled flows post-interdiction. Moreover, a flow may or may not be fulfilled through the least-cost route using the nearest hubs. This work makes two major contributions: the first contribution is on the efficient handling of the bi-level hub interdiction problem using the Dual-based approach and the Penalty-based approach, and the second contribution is on solving the overall three-level problem using a super valid inequality. These two contributions allow us to solve large-scale versions of the capacitated multiple allocation p-median hub location problem under the risk of interdiction, which is otherwise mathematically intractable and can be handled only using complete enumeration techniques.





Similar content being viewed by others
References
Aksen, D., Piyade, N., & Aras, N. (2010). The budget constrained r-interdiction median problem with capacity expansion. Central European Journal of Operations Research, 18(3), 269–291.
Altner, D. S., Ergun, Ö., & Uhan, N. A. (2010). The maximum flow network interdiction problem: Valid inequalities, integrality gaps, and approximability. Operations Research Letters, 38(1), 33–38.
Alumur, S. A., Campbell, J. F., Contreras, I., Kara, B. Y., Marianov, V., & O’Kelly, M. E. (2021). Perspectives on modeling hub location problems. European Journal of Operational Research, 291(1), 1–17.
Alumur, S., & Kara, B. Y. (2008). Network hub location problems: The state of the art. European Journal of Operational Research, 190(1), 1–21.
Audet, C., Hansen, P., Jaumard, B., & Savard, G. (1997). Links between linear bilevel and mixed 0–1 programming problems. Journal of Optimization Theory and Applications, 93(2), 273–300.
Baggio, A., Carvalho, M., Lodi, A., & Tramontani, A. (2021). Multilevel approaches for the critical node problem. Operations Research, 69(2), 486–508.
Boland, N., Krishnamoorthy, M., Ernst, A. T., & Ebery, J. (2004). Preprocessing and cutting for multiple allocation hub location problems. European Journal of Operational Research, 155(3), 638–653.
Campbell, J. F. (1994). Integer programming formulations of discrete hub location problems. European Journal of Operational Research, 72(2), 387–405.
Campbell, J. F., & O’Kelly, M. E. (2012). Twenty-five years of hub location research. Transportation Science, 46(2), 153–169.
Church, R. L., & Scaparra, M. P. (2007). Protecting critical assets: The r-interdiction median problem with fortification. Geographical Analysis, 39(2), 129–146.
Church, R. L., Scaparra, M. P., & Middleton, R. S. (2004). Identifying critical infrastructure: The median and covering facility interdiction problems. Annals of the Association of American Geographers, 94(3), 491–502.
Collado, R. A., & Papp, D. (2012). Network interdiction: Models, applications, unexplored directions. Rutcor Res Rep, RRR4, Rutgers University, New Brunswick, NJ.
Contreras, I. (2015). Hub location problems. In Location science (pp. 311–344). Springer.
Contreras, I., & O’Kelly, M. (2019). Hub location problems. In Location science (pp. 327–363). Springer.
Contreras, I., Díaz, J. A., & Fernández, E. (2009). Lagrangean relaxation for the capacitated hub location problem with single assignment. OR Spectrum, 31(3), 483–505.
Contreras, I., Díaz, J. A., & Fernández, E. (2011). Branch and price for large-scale capacitated hub location problems with single assignment. INFORMS Journal on Computing, 23(1), 41–55.
Contreras, I., Tanash, M., & Vidyarthi, N. (2017). Exact and heuristic approaches for the cycle hub location problem. Annals of Operations Research, 258(2), 655–677.
Cormican, K. J., Morton, D. P., & Wood, R. K. (1998). Stochastic network interdiction. Operations Research, 46(2), 184–197.
Dolan, E. D., & Moré, J. J. (2002). Benchmarking optimization software with performance profiles. Mathematical Programming, 91(2), 201–213.
Ebery, J., Krishnamoorthy, M., Ernst, A., & Boland, N. (2000). The capacitated multiple allocation hub location problem: Formulations and algorithms. European Journal of Operational Research, 120(3), 614–631.
Elhedhli, S., & Hu, F. X. (2005). Hub-and-spoke network design with congestion. Computers & Operations Research, 32(6), 1615–1632.
Elhedhli, S., & Wu, H. (2010). A Lagrangean heuristic for hub-and-spoke system design with capacity selection and congestion. INFORMS Journal on Computing, 22(2), 282–296.
Ernst, A. T., & Krishnamoorthy, M. (1996). Efficient algorithms for the uncapacitated single allocation p-hub median problem. Location Science, 4(3), 139–154.
Ernst, A. T., & Krishnamoorthy, M. (1998). Exact and heuristic algorithms for the uncapacitated multiple allocation p-hub median problem. European Journal of Operational Research, 104(1), 100–112.
Ernst, A. T., & Krishnamoorthy, M. (1999). Solution algorithms for the capacitated single allocation hub location problem. Annals of Operations Research, 86, 141–159.
Farahani, R. Z., Hekmatfar, M., Arabani, A. B., & Nikbakhsh, E. (2013). Hub location problems: A review of models, classification, solution techniques, and applications. Computers & Industrial Engineering, 64(4), 1096–1109.
Fischetti, M., Ljubić, I., Monaci, M., & Sinnl, M. (2017). A new general-purpose algorithm for mixed-integer bilevel linear programs. Operations Research, 65(6), 1615–1637.
Fischetti, M., Ljubić, I., Monaci, M., & Sinnl, M. (2019). Interdiction games and monotonicity, with application to knapsack problems. INFORMS Journal on Computing, 31(2), 390–410.
Frangioni, A. (1995). On a new class of bilevel programming problems and its use for reformulating mixed integer problems. European Journal of Operational Research, 82(3), 615–646.
Furini, F., Ljubić, I., San Segundo, P., & Zhao, Y. (2021). A branch-and-cut algorithm for the edge interdiction clique problem. European Journal of Operational Research, 294(1), 54–69.
Ghaffarinasab, N., & Atayi, R. (2018). An implicit enumeration algorithm for the hub interdiction median problem with fortification. European Journal of Operational Research, 267(1), 23–39.
Ghaffarinasab, N., & Motallebzadeh, A. (2018). Hub interdiction problem variants: Models and metaheuristic solution algorithms. European Journal of Operational Research, 267(2), 496–512.
Israeli, E., & Wood, R. K. (2002). Shortest-path network interdiction. Networks: An International Journal, 40(2), 97–111.
Kleinert, T., Labbé, M., Ljubić, I., & Schmidt, M. (2021). A survey on mixed-integer programming techniques in bilevel optimization. EURO Journal on Computational Optimization, 9, 100007.
Lei, T. L. (2013). Identifying critical facilities in hub-and-spoke networks: A hub interdiction median problem. Geographical Analysis, 45(2), 105–122.
Lim, C., & Smith, J. C. (2007). Algorithms for discrete and continuous multicommodity flow network interdiction problems. IIE Transactions, 39(1), 15–26.
Lozano, L., Smith, J. C., & Kurz, M. E. (2017). Solving the traveling salesman problem with interdiction and fortification. Operations Research Letters, 45(3), 210–216.
McMasters, A. W., & Mustin, T. M. (1970). Optimal interdiction of a supply network. Naval Research Logistics Quarterly, 17(3), 261–268.
O’Hanley, J. R., & Church, R. L. (2011). Designing robust coverage networks to hedge against worst-case facility losses. European Journal of Operational Research, 209(1), 23–36.
O’Kelly, M. E. (1986). Activity levels at hub facilities in interacting networks. Geographical Analysis, 18(4), 343–356.
O’Kelly, M. E. (1987). A quadratic integer program for the location of interacting hub facilities. European Journal of Operational Research, 32(3), 393–404.
O’Kelly, M. E., & Bryan, D. (1998). Hub location with flow economies of scale. Transportation Research Part B: Methodological, 32(8), 605–616.
Parvaresh, F., Husseini, S. M., Golpayegany, S. H., & Karimi, B. (2014). Hub network design problem in the presence of disruptions. Journal of Intelligent Manufacturing, 25(4), 755–774.
Ramamoorthy, P., Jayaswal, S., Sinha, A., & Vidyarthi, N. (2018). Multiple allocation hub interdiction and protection problems: Model formulations and solution approaches. European Journal of Operational Research, 270(1), 230–245.
Scaparra, M. P., & Church, R. L. (2008). A bilevel mixed-integer program for critical infrastructure protection planning. Computers & Operations Research, 35(6), 1905–1923.
Scaparra, M. P., & Church, R. L. (2008). An exact solution approach for the interdiction median problem with fortification. European Journal of Operational Research, 189(1), 76–92.
Smith, J. C., Lim, C., & Sudargho, F. (2007). Survivable network design under optimal and heuristic interdiction scenarios. Journal of Global Optimization, 38(2), 181–199.
Tahernejad, S., Ralphs, T. K., & DeNegre, S. T. (2020). A branch-and-cut algorithm for mixed integer bilevel linear optimization problems and its implementation. Mathematical Programming Computation, 12, 529–568.
Ullmert, T., Ruzika, S., & Schöbel, A. (2020). On the p-hub interdiction problem. Computers & Operations Research, 124, 105056.
Wood, R. K. (1993). Deterministic network interdiction. Mathematical and Computer Modelling, 17(2), 1–18.
Funding
No funding was received to assist with the preparation of this manuscript.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix A Proofs of Propositions
Appendix A Proofs of Propositions
1.1 A.1 Proof of Proposition 1
There are two possible cases:
-
Case 1: Total capacity of the surviving hubs < Total flow demand of the network
There will be at least one source-destination pair (i, j) for which Constraint (12) will have a strict inequality. And so, there is going to be some unfulfilled flow demand. For this case, any positive value of \(P_{ij}\) will work to incur a penalty for not fulfilling the demand.
-
Case 2: Total capacity of the surviving hubs \(\ge \) Total flow demand of the network
In this case, all the flow demands have to be satisfied by taking any route having an unsaturated hub. Suppose for a given source-destination pair (i, j), only \(\eta \) fraction of the flow is remaining to be allocated. In the worst-case scenario, this demand will be satisfied through the only possible path having the highest transportation cost. Then, from the objective function (11), we can see that:
Worst case cost to fulfill this demand = \( \eta W_{ij} \max _{k,m} \{d_{ijkm}\}\).
On the other hand, the cost of not fulfilling this demand = \( \eta P_{ij}\).
Hence, to ensure that the remaining unfulfilled demand is satisfied, as we have enough capacity left to accommodate that, the following condition needs to be satisfied
$$\begin{aligned}&\eta P_{ij}> \eta W_{ij} \max _{k,m} \{d_{ijkm}\} \\&\quad \implies P_{ij} > W_{ij} \max _{k,m} \{d_{ijkm}\} \end{aligned}$$
Hence, \( \tilde{P}_{ij} = W_{ij} \max _{k,m} \{d_{ijkm}\} + \epsilon \) is a valid value for \(P_{ij}\) for any positive \(\epsilon \).
1.2 A.2 Proof of Proposition 2
Suppose \(\bar{P}_{ij}\) is the tight value of \(P_{ij}\) such that \(\bar{P}_{ij} < \tilde{P}_{ij}\). Then, \(\bar{P}_{ij} = W_{ij} \max _{k,m} \{d_{ijkm}\}\). Now, consider case 1 of the proof for Proposition 1. As the cost for fulfilling this demand through the only available path having the highest cost is equal to the penalty for not fulfilling it, there is a possibility that the mathematical program leaves this demand unfulfilled even when the network has sufficient capacity to fulfill it. So, \(\bar{P}_{ij}\) is not a valid value for \(P_{ij}\). Therefore, \(\tilde{P}_{ij}\) is the best-known value of \(P_{ij}\), and any value less than this may lead to under-utilization of the available capacity.
1.3 A.3 Proof of Proposition 3
From constraint sets (21),(22) and (25), we get
As \(\delta _{ijk}\) appears with a negative sign in the maximization type objective function (16), it will take the minimum possible value which satisfies the constraints having \(\delta _{ijk}\). Now, rewriting these equations as follows:
\(\phi _{ij}\) and \(\theta _{k}\) are the dual variables associated with the constraint sets (12) and (14) in \(\hbox {HIMP}_{{2L}}\), respectively. And hence their values will be the shadow prices associated with those constraints. Then, we can clearly see that
-
\(\hat{\phi }_{ij} = 0\) as the minimum possible change in the objective function (11) will happen when the complete flow demand from the source i to destination j can not be met post-interdiction. For a given source-destination pair (i, j), if the right-hand side of constraint (12) is 0, then it will cost objective function a value of \(P_{ij}\); while if the right side is increased to 1, then because of the limited capacity this complete demand will incur a penalty of \(P_{ij}\) for not being met. So, there will be no change in the objective function.
-
\(\hat{\theta }_{k} = 0 \) as the minimum possible change in the objective function (11) will happen when there is more than enough capacity with surviving hub k. So, even if the right-hand side of constraint (14) is increased by 1 unit, there will be no change in the objective function.
Therefore, to satisfy the above set of conditions on \(\delta _{ijk}\), we can set the worst case (maximum possible) value of \(\delta _{ijk}\) as follows:
Hence, \(\hat{M}_{ijk} = P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\} \) is a valid value of \(M_{ijk}\) for the \(\hbox {HIMP}_{{DF}}\) formulation.
1.4 A.4 Proof of Proposition 4
As \(\hat{M}_{ijk} = P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\} \), so \(\bar{M}_{ijkm} = P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\} + \epsilon \)
\(M_{ijkm}\) should take such value so that there is no flow through an interdicted hub. There are three possible cases for a given source-destination pair (i, j), a positive fraction (\(\eta \)) of flow demand between i and j via hub k and hub m in that order:
-
Case 1: Both of the hubs are surviving
Any value of \(M_{ijkm}\) will work as \(q_{k} = q_{m} = 1\) in the objective function (29) making the associated terms 0.
-
Case 2: One of the two hubs is interdicted
Suppose only hub k is interdicted; while hub m is surviving,i.e., \(q_{k} = 0\) and \(q_{m} = 1\) Then,
-
The total cost for fulfilling such flow = \(\eta W_{ij} d_{ijkm} + \eta \bar{M}_{ijkm}\)
-
On the other hand, the total cost for not fulfilling such flow = \(\eta P_{ij}\)
In order to restrict the flow from passing through the interdicted hub, the cost for fulfillment should be greater than that of unfulfilled flow.
$$\begin{aligned}&\eta W_{ij} d_{ijkm} + \eta \bar{M}_{ijkm}> \eta P_{ij} \\&\quad \implies W_{ij} d_{ijkm} + \bar{M}_{ijkm}> P_{ij} \\&\quad \implies W_{ij} d_{ijkm} + P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\} + \epsilon> P_{ij} \\&\quad \implies W_{ij} \left( d_{ijkm} - \min _{m} \{d_{ijkm}\}\right) + \epsilon > 0 \end{aligned}$$which is true and hence a valid value.
-
-
Case 3: Both the hubs are interdicted
Here, \( q_k = q_m = 0\). Then,
-
The total cost for fulfilling such flow = \(\eta W_{ij} d_{ijkm} + 2 \eta \bar{M}_{ijkm}\)
-
On the other hand, the total cost for not fulfilling such flow = \(\eta P_{ij}\)
In order to restrict the flow from passing through the interdicted hub, the cost for fulfillment should be greater than that of unfulfilled flow.
$$\begin{aligned}&\eta W_{ij} d_{ijkm} + 2 \eta \bar{M}_{ijkm}> \eta P_{ij} \\&\quad \implies W_{ij} d_{ijkm} + 2 \bar{M}_{ijkm}> P_{ij} \\&\quad \implies W_{ij} d_{ijkm} + 2 \left( P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\} + \epsilon \right)> P_{ij} \\&\quad \implies W_{ij} (d_{ijkm} - \min _{m} \{d_{ijkm}\}) + \left( P_{ij} - W_{ij}\min _{m} \{d_{ijkm}\}\right) + 2 \epsilon > 0 \end{aligned}$$which is true and hence a valid value.
-
1.5 A.5 Proof of Proposition 5
There are three possible cases for a given source-destination pair (i, j), a positive fraction (\(\eta \)) of flow demand between i and j through hub k and hub m:
-
Case 1: Both of the hubs are surviving
Any value of \(M_{ijkm}\) will work as \(q_{k} = q_{m} = 1\) in the objective function (29) making the associated terms 0.
-
Case 2: One of the two hubs is interdicted
Suppose only hub k is interdicted while hub m is surviving,i.e., \(q_{k} = 0\) and \(q_{m} = 1\) Then,
-
The total cost for fulfilling such flow = \(\eta W_{ij} d_{ijkm} + \eta M_{ijkm}\)
-
On the other hand, the total cost for not fulfilling such flow = \(\eta P_{ij}\)
-
-
Case 3: Both the hubs are interdicted
Here, \( q_k = q_m = 0\). Then,
-
The total cost for fulfilling such flow = \(\eta W_{ij} d_{ijkm} + 2 \eta M_{ijkm}\)
-
On the other hand, the total cost for not fulfilling such flow = \(\eta P_{ij}\)
-
Here, we are concerned about only Case 2 and Case 3, as in Case 1, any value of \(M_{ijkm}\) will work. The value of \(M_{ijkm}\) applicable for Case 2 will also be a valid value for Case 3. So, we are going to analyze only Case 2.
The total cost of flow using the path containing an interdicted hub should be greater than the cost of not fulfilling the same, in order to discourage any flow using an interdicted hub. This means,
Hence, \(\tilde{M}_{ijkm} = P_{ij} - W_{ij}d_{ijkm} + \epsilon \) is a valid as well as the best-known value of \(M_{ijkm}\) for a given source-destination pair (i, j) and routing of flow through hubs k and m in \(\hbox {HIMP}_{{PDF}}\), where \(\epsilon \) is a positive infinitesimal quantity.
1.6 A.6 Proof of Proposition 6
We know,
1.7 A.7 Proof of Proposition 7
We know \(\tilde{P}_{ij}\) is the best-known value of \(P_{ij}\) for \(\hbox {HIMP}_{{2L}}\) such that any other value of \(P_{ij}\) less than \(\tilde{P}_{ij}\) will result into under-utilization of the capacity of hubs. As
Therefore, \(\bar{P}_{ij}\) is a valid value of \(P_{ij}\) for SP, which is a \(\hbox {HIMP}_{{2L}}\).
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Bansal, V., Jayaswal, S. & Sinha, A. Capacitated multiple allocation hub location problems under the risk of interdiction: model formulations and solution approaches. Ann Oper Res 332, 213–251 (2024). https://doi.org/10.1007/s10479-023-05563-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10479-023-05563-4