Abstract
In hedonic games, players form coalitions based on individual preferences over the group of players they could belong to. Several concepts to describe the stability of coalition structures in a game have been proposed and analysed in the literature. However, prior research focuses on algorithms with time complexity that is at least linear in the input size. In the light of very large games that arise from, e.g., social networks and advertising, we initiate the study of sublinear time property testing algorithms for existence and verification problems under several notions of coalition stability in a model of hedonic games represented by graphs with bounded degree. In graph property testing, one shall decide whether a given input has a property (e.g., a game admits a stable coalition structure) or is far from it, i.e., one has to modify at least an \(\epsilon\)-fraction of the input (e.g., the game’s preferences) to make it have the property. In particular, we consider verification of perfection, individual rationality, Nash stability, (contractual) individual stability, and core stability. While there is always a Nash-stable coalition structure (which also implies individually stable coalitions), we show that the existence of a perfect coalition structure is not tautological but can be tested. All our testers have one-sided error and time complexity that is independent of the input size.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Hedonic games are a form of coalition formation games, in which players form teams in a decentralized manner based on individual preferences over coalitions, i.e., subsets of players. The solution to such a game is a coalition structure, i.e., a partition of the set of players. The main idea of hedonic games is that the players’ evaluation of a coalition structure only depends on their own coalitions and not on how other players work together [17]. These games have been formalized by Banerjee et al. [6] and Bogomolnaia and Jackson [8], independently. In order to evaluate the quality of a coalition structure, several solution concepts have been considered. These include, e.g., Nash stability, which states that no individual player wants to deviate from the coalition structure, and core stability, which requires that no group of players wants to deviate and form a coalition of their own.
Algorithmically, a key issue is to find suitable representations of hedonic games: Since the number of possible coalitions for a player is exponential in the number of players, there is a trade-off between compactness and expressivity of the preference profile. In the areas of Cooperative Games in Multiagent Systems (see [11] for details) and Computational Social Choice (see [2] for details), a number of representations and stability concepts are analysed with respect to the computational complexity of deciding whether there exists a stable solution, verifying whether a given solution is stable, and finding a stable solution. Even for restricted representations such as additively separable games, these questions are often intractable. For instance, it is often \(\mathrm {NP}\)-complete to decide whether a given game allows a Nash-stable coalition structure, see Peters [35] for an example. The existence of core-stability is often even \(\varSigma _2^p\)-complete to decide; examples can be found in Woeginger [39] and Ota et al. [34]. This strikes even harder when the considered game instances are very large because they arise from, e.g., social networks or the assignment of advertisements to available slots on web pages so that competing ads do not interfere (this can be configured in real advertisement services [26, 27]). Here, it might already be impractical to read the whole input once because the data does not fit into memory or the access is slow or restricted.
In this article, we study sublinear algorithms for hedonic games. We aim to decide in sublinear time whether a game has a stable coalition structure or is far from this with respect to the number of required changes of preferences such that it admits a stable coalition structure, as well as whether a game is stable under a given coalition structure \(\varGamma\) or is far from being stable under \(\varGamma\). When a coalition can be stabilized by only few compromises on the preferences, it may be acceptable to sustain the situation. When, however, too many modifications are required to obtain any stable situation, the current situation is too far off.
Graph representations provide a compact means to encode structural connections between players. A formal study of graphical hedonic games is provided by Peters [35]. A popular variant is to encode a game as a network where players correspond to vertices and edges illustrate friendship relations. Players that are not friends are often referred to as enemies. Preferences are extended either by prioritising appreciation of friends or aversion to enemies [16]. However, if the game is very large, many players may not be involved in any relationship. In this scenario, it is natural to consider a more general model. For each player, the set of other players is divided into three subsets: friends, enemies and neutral players [34], which is what we call the FEN-encoding. Furthermore, we bound the number of friends and enemies per player by a constant. For example, if the players are humans, it is known that each player can only maintain a limited number of stable relationships to other humans [18, 19]. This number is known as Dunbar’s number, and empirical estimates are smaller than 300 [29]. If the players are advertisements, advertisers might expect positive or negative effects for a limited number of other advertisements when placed on the same web page (e.g., an ad for a phone and an ad for an accessory item might up-sell while two ads for comparable phone models might only cross-sell). Under restrictions such as bounded degree and bounded treewidth, some stability questions become solvable in linear time [35]. Nevertheless, this still incurs the evaluation of the whole game in order to verify whether a coalition structure is stable. Given the local views of individual vertices within hedonic games, it would be preferable and much more practical to ask only a sample of players for their individual preferences and deduce global properties.
The area of property testing provides a framework to relax such decision problems in favour of sublinear complexity (see [23] for an overview). A property tester is a randomized algorithm that decides, with error probability at most \(\nicefrac {1}{3}\), whether the input satisfies some property \({\mathcal {P}}\) or is far from satisfying \({\mathcal {P}}\) by probing only a small part of it. In the setting of graph properties, a graph G with bounded vertex degree d is \(\epsilon\)-far from satisfying some property \({\mathcal {P}}\) (e.g., bipartiteness) if one has to modify at least \(\epsilon d n\) edges to make G have property \({\mathcal {P}}\). If the property tester always accepts graphs in \({\mathcal {P}}\), it has one-sided error; otherwise, it has two-sided error. The input graph G may be probed by the algorithm through an oracle that provides access to the entries of the adjacency lists of G, and the computational complexity of the property tester is measured in terms of queries it asks.
In comparison to classic decision problems, property testing problems allow for algorithms with sublinear complexity. For example, a randomized decision algorithm for graph connectivity needs to read the whole input to achieve constant error probability, which implies a linear lower bound on the complexity. In contrast, a property tester for connectivity has only constant complexity [24]. This difference arises because the property tester does not need to read the whole input, and, in fact, sublinear complexity renders this impossible. Therefore, the input model plays an important role in property testing. While there is a characterization for constant query testable properties in dense graphs (graphs with \(\varOmega (|V |^2)\) edges) [1], less is known for graphs with bounded degree and general graphs.
1.1 Our contribution
We study property testing of stability problems in FEN-hedonic games, where each player has a bounded number of symmetric relationships to friends and enemies as represented by labelled edges of an undirected graph, and preferences are extended to coalitions by any utility function linear in the number of friends and enemies in a coalition. The setting of hedonic games enhances graphs by rich semantics, which stands in contrast to purely combinatorial and geometric properties previously studied in graph property testing. We model the semantics of hedonic games as an additional layer on top of the combinatorial graph structure and analyse existence and verification problems for various stability concepts. In particular, we study common individual-based stability concepts such as perfection, individual rationality, Nash stability, and (contractual) individual stability as well as core stability .
While individually rational, Nash-stable, individually stable, and contractually individually stable coalitions always exist, there are games which do not allow a perfect coalition structure.
Theorem 1.1
Given an FEN-hedonic game G with bounded degree d, it can be tested whether G admits a perfect coalition structure with bounded coalition size c. The tester has one-sided error and query complexity \(\mathrm {poly}(\epsilon , c, d)\).
We provide the technical result as Theorem 4.8 in Sect. 4.2.
While the existence problem as to whether a game allows a stable outcome is a property of edge-labelled graphs, the verification problem of whether a game satisfies stability according to a given coalition structure \(\varGamma\) requires additional modelling: We assume that next to oracle access to the adjacency lists of the underlying bounded-degree graph of a game G, we have additional access to an oracle to \(\varGamma\), i.e., to the given partition of the vertex set.
Theorem 1.2
Given an FEN-hedonic game G with bounded degree d and a coalition structure \(\varGamma\), it can be tested whether G is stable under \(\varGamma\) with respect to perfection, individual rationality, Nash stability, individual stability and contractual individual stability with one-sided error and query complexity \(\mathrm {poly}(\epsilon , d)\). For core stability we obtain a one-sided error tester with query complexity dependent on \(\epsilon\), c, and d, where c is the maximum coalition size.
We provide the technical result as Theorem 4.6 based on Theorem 4.5 in Sect. 4.1.
Note that while we consider c and d to be of constant size, independent of the input size n, our statements remain valid if, for instance, \(d\in {\mathcal {O}}(\log n)\). We provide extensions of our theorems to weighted graphs (additively separable games) and directed graphs (asymmetric games) in Section 4.3.
A preliminary version [22] of this work was published in the proceedings of AAMAS 2019 (International Conference on Autonomous Agents and Multiagent Systems). This is a revised version that also extends the preliminary version by a verification tester for core stability (see Theorem 4.6), an extension of our main theorems to weighted graphs (see Theorems 4.12 and 4.13 ), an extension of our main theorem on verification testing to directed graphs (see Theorem 4.14) and a lower bound related to our main theorem on testing the existence of a perfect coalition structure for directed graphs (see Theorem 4.15).
1.2 Related work
Hedonic games were formally defined by Banerjee et al. [6] and Bogomolnaia and Jackson [8]. A well-known application of a restricted variant with size-two coalitions is the stable-roommates problem [9] for the allocation of student houses. Mostly, hedonic games have been analysed from a computational complexity point of view with respect to a trade-off between expressivity, succinct representation and tractability of stability decision problems. The complexity of general hedonic games has first been studied by Ballester [5]. The worst-case complexity of stability problems for various representations and different stability concepts has been studied extensively since: Popular representations include additively separable hedonic games [3, 8, 39], singleton encodings [10], hedonic coalition nets [21], and dichotomous preferences [4]; see also Aziz and Savani [2] and Chalkiadakis et al. [11] for an overview. Peters and Elkind [36] analysed causes of and conditions for hardness. The existence of Nash stability and other individual stability concepts is often (if not guaranteed to exist) \(\mathrm {NP}\)-complete to decide (see Sung and Dimitrov [38] for an analysis of additively separable games). For core stability, this is often even harder, namely \(\varSigma _2^p\)-complete [34, 39]. Dimitrov et al. [16] defined restricted hedonic games based on a network of friends and enemies. A more general version including neutral players was defined by Ota et al. [34]. Games with neutral players and partial individual evaluations were studied by Lang et al. [31] and Peters [35]. In the latter work, in particular, the authors considered a constant bound on the number of individual preferences and studied graphical hedonic games with bounded treewidth. With this restriction, it can be decided in linear time whether, for instance, a Nash-stable coalition structure exists. A graphical model restricting to the formation of coalitions between players that are connected in the underlying graph was studied by Igarashi and Elkind [30]. Darmann et al. [15] studied games where players have preferences over different types of coalitions (activities) and their sizes instead of the participating players (this can also be expressed as a hedonic game). For the case that there is only one type of coalition, Lee and Shoham [32] and Lee and Williams [33] extended the setting by Darmann et al. so that each player may have a bounded number of friend-enemy relationships to other players.
The most related work to ours in the area of property testing is that for classic properties of graphs as there is, to the best of the authors’ knowledge, no work on game theory so far. For example, Goldreich and Ron [24] showed that well-known properties of bounded-degree graphs like cycle freeness are testable with constant query complexity and two-sided error. However, for one-sided error testing of cycles freeness, \(\varTheta (\sqrt{n})\) queries are required [24] as well as sufficient as Czumaj et al. [13] show. Property testing of annotated (or labelled) graphs has been studied for geometric graphs mainly, e.g., by Ben-Zwi et al. [7], Czumaj and Sohler [12] and Hellweg et al., [28].
Learning hedonic games was studied by Sliwinski and Zick [37]. While property testing focuses on testing whether a game admits a stable outcome or whether an outcome is stable with sublinear complexity, PAC learning constructs a good hypothesis and PAC stabilization uses this hypothesis to learn a stable outcome (if possible) using a superlinear number of samples (with possibly linear size). As far as we know, no sublinear algorithms have been developed for hedonic games, yet.
2 Preliminaries
In this article, we consider graphs with vertex degrees bounded by a constant d. If not stated otherwise, graphs are undirected and unweighted. For a graph \(G=(V,E)\) at hand, we write \(n = |V |\). Without loss of generality, we assume that \(V = [n] = \{1,\dots ,n\}\).
2.1 Hedonic games
A hedonic game \((N,\succeq )\) consists of a set of players \(N=[n]\) and a preference profile \(\succeq =(\succeq _1,\dots ,\succeq _n)\), where \(\succeq _i\) is player i’s preference relation over \({\mathcal {N}}_i=\{C\subseteq N\mid i\in C\}\). A subset \(C\subseteq N\) of players is called a coalition. An output of a hedonic game is a coalition structure, i.e., a partition \(\varGamma\) of the player set. Let \(\varGamma (i)\in \varGamma\) be the coalition containing \(i\in N\). We say that player i weakly prefers coalition A to coalition B, if \(A\succeq _i B\). Player i prefers A to B, denoted by \(A\succ _i B\), if \(A\succeq _i B\), but \(B\not \succeq _i A\); i is indifferent between A and B, denoted by \(A\sim _i B\), if \(A\succeq _i B\) and \(B\succeq _i A\).
Since the set \({\mathcal {N}}_i\) of coalitions a player is contained in has an exponential size in the number of players, a central question in the study of hedonic games is to define representations that are adequately compact and at the same time as expressive as possible.
One common representation is that of a graph network, where the players in N are vertices in the graph. In the encoding as defined by Ota et al. [34], for each player \(i\in N\), there exists a set \(N_i^+\subseteq N\setminus \{i\}\) of friends and a set \(N_i^-\subseteq N\setminus \{i\}\) of enemies, \(N_i^+\cap N_i^-=\emptyset\). The remaining players are considered as neutral \(N_i^0=N\setminus (N_i^+\cup N_i^-\cup \{i\})\). We call this representation FEN-encoding. It can be represented by a labelled graph \(G=(N,F\cup E)\) with \(F\cap E=\emptyset\), where \(j\in N_i^+\) if and only if \((i,j)\in F\), and \(j\in N_i^-\) if and only if \((i,j)\in E\). We distinguish between the following cases:
-
undirected, unweighted FEN-encoding If not stated otherwise, we consider undirected and unweighted graphs. Hence, we have symmetric preferences, i.e., \(i\in N_j^+\) if and only if \(j\in N_i^+\) and \(i\in N_j^-\) if and only if \(j\in N_i^-\).
-
directed, unweighted FEN-encoding If the graph is directed, preferences can be asymmetric, e.g., player i can consider j as a friend, but j can consider i as neutral or even an enemy.
-
weighted FEN-encoding In addition edges can be weighted, i.e., each player i specifies a value w(i, j) for each other player \(j\in N_i\). We assume that w(i, j) is positive if \(j\in N_i^+\), and negative if \(j\in N_i^-\). Here edges can also be either undirected (\(w(i,j)=w(j,i)\)) or directed (possibly different values for w(i, j) and w(j, i)).
The latter two cases are studied in Sect. 4.3. In the unweighted case, we extend the players’ relations to preferences in the following manner. A value function is specified such that each player \(i\in N\) assigns a fixed positive value to each friend and a fixed negative value to each enemy. Formally, for two values \(f,e\in {\mathbb {R}}_{>0}\), a corresponding utility function \(u_i:{\mathcal {N}}_i\rightarrow {\mathbb {R}}\), \(i\in N\), is defined additively by
For instance, friends appreciation can be represented by \(f=d\) and \(e=1\), and enemies aversion by \(f=1\) and \(e=d\). The preference extension is obtained by \(A\succeq _i B\iff u_i(A)\ge u_i(B)\).
Definition 2.1
(FEN-hedonic game) Let \((N,\succeq )\) be a hedonic game represented by an undirected and unweighted FEN-encoding, with preference profile \(\succeq\) extended via utility function \(u_i\). We call \((N,\succeq )\) FEN-hedonic game.
For directed and weighted FEN-encodings, we refer to such games as directed and weighted FEN-hedonic games, respectively.
Figure 1 below shows two examples of a FEN-hedonic game. This conforms to the definition of a graphical hedonic game [35] such that a player i’s preference of a coalition \(C\in {\mathcal {N}}_i\) over a coalition \(D\in {\mathcal {N}}_i\) only depends on i’s neighbourhood \(N_i=N_i^+\cup N_i^-\):
Note that responsiveness is always satisfied, i.e., \(C\cup \{j\}\succ _i C\) and \(C\succ _i C\cup \{j'\}\), for each \(i\in N\), and each \(C\in {\mathcal {N}}_i\) and \(j\in N_i^+\), \(j'\in N_i^-\).
Weighted and directed FEN-hedonic games are equivalent to additively separable hedonic games [8] via \(w(i,j)=0\) for \(j\in N_i^0\) and
weighted, undirected FEN-hedonic games are equivalent to symmetric additively separable hedonic games.
Furthermore, we make the following assumptions. We consider graphs of bounded degree \(\vert N_i\vert \le d\) represented by an adjacency list; in particular, it can be decided in time independent of the number n of players whether \(C\succeq _i D\), and independent of the coalition size \(\vert C\vert\) and \(\vert D\vert\). Moreover, it is often useful to restrict the coalition size, e.g., when players are people that have to communicate or when a coalition represents all ads displayed on a single web page. Therefore, we also consider a bounded coalition size of \(\vert C\vert \le c\).
By \({\mathfrak {G}}_n\) we denote the set of graphs with n vertices that represent such a game. The set of coalition structures partitioning n players is denoted by \({\mathfrak {C}}_n\). In the following, let \(G=(N,F\cup E)\) be a graph that represents a FEN-hedonic game and let \(\varGamma \in {\mathfrak {C}}_n\) be a coalition structure solving this game. There are several solution concepts motivated from different perspectives on the game. Note that in comparison to the definitions in the literature we take into account the bound on the coalition size \(|C|\le c\). Whenever \(c=n\) holds, the stability concepts are equivalent to their original definition. Let \(\mathrm {Fav}(i)\) denote the set of player i’s favourite coalitions of size at most c, i.e., those coalitions that i weakly prefers over all other coalitions \(C\in {\mathcal {N}}_i\) of size \(\vert C\vert \le c\). On the one hand, \(\varGamma\) is called
-
perfect if each player \(i\in N\) weakly prefers \(\varGamma (i)\) to every coalition, i.e., \(\varGamma (i)\in \mathrm {Fav}(i)\).
This property reflects an ideal situation, but is rather rarely fulfilled.
On the other hand, \(\varGamma\) is called
-
individually rational if for each \(i\in N\), \(\varGamma (i)\) is acceptable, i.e., \(\varGamma (i)\succeq _i\{i\}\).
Individual rationality is guaranteed by \(\{\{i\}\mid i\in N\}\). Other stability notions are based, for example, on the lack of deviations of a single player to another (possibly empty) existing coalition. A coalition structure \(\varGamma\) is called
-
Nash-stable if no player wants to move to another existing or empty coalition, i.e., for each player \(i\in N\) and each coalition \(C\in \varGamma \cup \{\emptyset \}\) with \(\vert C\vert < c\), it holds that \(\varGamma (i)\succeq _i C\cup \{i\}\);
-
individually stable if no player can move to another preferred coalition without making a player in the new coalition worse off, i.e., for each player \(i\in N\) and for each coalition \(C\in \varGamma \cup \{\emptyset \}\) with \(\vert C\vert < c\), it holds that \(\varGamma (i)\succeq _i C\cup \{i\}\) or there exists a player \(j\in C\) such that \(C\succ _j C\cup \{i\}\);
-
contractually individually stable if no player can move to another preferred coalition without making a player in the new coalition or in the old coalition worse off, i.e., for each player \(i\in N\) and for each coalition \(C\in \varGamma \cup \{\emptyset \}\) with \(\vert C\vert < c\), it holds that \(\varGamma (i)\succeq _i C\cup \{i\}\), or there exists a player \(j\in C\) such that \(C\succ _j C\cup \{i\}\), or there exists a player \(j'\in \varGamma (i)\setminus \{i\}\) such that \(\varGamma (i)\succ _{j'}\varGamma (i)\setminus \{i\}\).
Note that Nash stability implies individual stability, which, in turn, implies contractual individual stability.
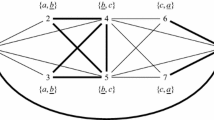
Two FEN-hedonic games G, H with bounded degree 4 and 7 players, a–g. Friend edges are solid green; enemy edges are dashed red. Assume enemies aversion, i.e., \(f=1\) and \(e=4\) for the utility function \(u_i\) that defines the preference extension \(\succeq\) (see Definition 2.1 and its preliminaries). The coalition structure \(\varGamma = \{ \{a, c\}\), \(\{b, d, f\}, \{e, g\} \}\) is perfect in G if the bound on the coalition size is \(c \ge 3\), otherwise there is no perfect coalition structure. Even for unbounded coalition size, there is no perfect coalition structure in H. However, the coalition structure \(\varGamma\) is core-stable and Nash-stable in H (and due to Nash-stability, it is also individually stable and contractually individually stable)
A further popular stability concept is based on group deviation. A coalition structure \(\varGamma\) is called
-
core stable if no coalition blocks \(\varGamma\), i.e., for each non-empty coalition \(C\subseteq N\) with \(\vert C\vert \le c\), there exists a player \(i\in C\) such that \(\varGamma (i)\succeq _i C\).
Figure 1 shows two examples of FEN-hedonic games and the stability concepts defined above. For a stability concept, questions of interest are:
-
Verification Given a game and a coalition structure, is it stable?
-
Existence Is a given game stable, i.e., does there exist a stable coalition structure?
2.2 Graph property testing
Let \(G = ({N,F \cup E})\) be a graph with vertex degrees bounded by d and let \({\mathcal {P}}\) be a graph property, i.e., a set of graphs (e.g., let \({\mathcal {P}}\) be all graphs that admit a perfect coalition structure). We say that G is \(\epsilon\)-far from a property \({\mathcal {P}}\) if more than \(\epsilon d n\) edges of G have to be modified (i.e., added or removed) in order to convert it into a graph that satisfies the property \({\mathcal {P}}\), otherwise G is \(\epsilon\)-close to \({\mathcal {P}}\). A property tester has access to G by querying a function \(f_G: N \times [n] \rightarrow [n] \cup \{\mathrm {null}\}\), where \(f_G(v,i)\) denotes the \(i^{th}\) neighbour of v if v has at least i neighbours. Otherwise, \(f_G(v,i) = \mathrm {null}\).
Definition 2.2
(one-sided testers) A one-sided error \(\epsilon\)-tester for a property \({\mathcal {P}}\) of bounded-degree graphs with query complexity q is a randomized algorithm \({\mathcal {A}}\) that makes q neighbourhood queries to \(f_G\) for an input graph G. The algorithm \({\mathcal {A}}\) accepts G if G has the property \({\mathcal {P}}\). If G is \(\epsilon\)-far from \({\mathcal {P}}\), then \({\mathcal {A}}\) rejects G with probability at least \(\nicefrac {2}{3}\).
Similarly to one-sided error decision algorithms, a one-sided error tester has to accept all graphs that have the property at hand. Therefore, it has to present a witness against the property when it rejects.
Many classic graph properties (e.g., planarity) are maintained when edges are removed from the graph; we observe the same for properties of hedonic games.
Definition 2.3
(edge-monotonicity) A graph property \({\mathcal {P}}\) is edge-monotone if for every \(G=(N, F \cup E) \in {\mathcal {P}}\), \(\{ (N, F' \cup E') \mid F' \subseteq F \wedge E' \subseteq E \} \subseteq {\mathcal {P}}\). In other words, every subgraph of G is also in \({\mathcal {P}}\).
3 The model of property testing for stability concepts
To test stability concepts, we slightly generalize the standard edit distance that underlies the definition of being \(\epsilon\)-far as follows. Since we consider graphs \(G = (V, F \cup E)\) that represent FEN-hedonic games, we have to account for the two types of edges: friends and enemies. Therefore, an edge modification is one insertion of an element to or one removal of an element from \(F \cup E\), respectively, while maintaining \(F \cap E = \emptyset\). In particular, turning a friend edge into an enemy edge is counted as two edge modifications (removing it from F and inserting it into E). The intuition of these semantics is that edge modifications measure the number of compromises that are needed to reach a stable situation. If a partition is too far from being stable, too many compromises are necessary, and the partition should be discarded. Everything in-between is not an ideal situation, but may be affordable.
Now, the existence of a stable outcome in a game is modelled as a graph property as follows.
Definition 3.1
(stability existence property) The set of stable graphs with respect to some stability concept (e.g., Nash stability) is the set of all graphs that admit a stable coalition structure.
For some stability concepts, the existence of a stable outcome is guaranteed. Nevertheless, the question of whether a given partition \(\varGamma\) satisfies the stability property can still be hard to decide. For all stability concepts mentioned above, the worst case time that is needed to verify stability of \(\varGamma\) is at least linear in the number of players. We can, however, tackle the following problem in sublinear time: Given a graph G and a partition of vertices \(\varGamma\), is \(\varGamma\) a stable outcome for the game represented by G, or is G \(\epsilon\)-far from being a stable instance for \(\varGamma\)?
Definition 3.2
(\(\varGamma\)-stability verification property) Let \(n \in {\mathbb {N}}\), and let \(\varGamma\) be a partition of [n]. The set of \(\varGamma\)-stable graphs with respect to some stability concept (e.g., Nash stability) is the set of n-vertex graphs G such that \(\varGamma\) is stable for G.
Note that, unlike the existence of a stable coalition structure, a stability property is not closed under isomorphism as long as \(\varGamma\) is not permuted accordingly. Therefore, extending the basic model of graph property testing to reflect the semantics of hedonic games is the foundation of our main contribution, and it is the main difference between our model and the vanilla model of graph property testing.
Definition 3.3
(query access to \(\varGamma\)) Access to \(\varGamma\) is provided by a set oracle that supports two queries. A find query returns, given a vertex v, the key of the set that contains v. A member query returns, given a key k and an index i, the i-th element of the set represented by k, or \(\mathrm {null}\) if no such element exists.
4 Property testing results in the FEN-model
In this section we study property testers for stability verification problems, resulting in Theorem 1.2, as well as stability existence problems, resulting in Theorem 1.1, for various individual-based stability notions within the previously defined model of FEN-hedonic games.
4.1 Testing verification problems
In the following we prove Theorem 1.2, the testability of verification problems with query complexity dependent only on the degree bound, but independent of the input graph’s size, which is restated in Theorem 4.6 below. Our algorithm can test the verification problem for every stability concept that can be defined using the notion of feasible player properties (see Definition 4.2), which is what we prove in Theorem 4.5. We state the feasible player properties for all of the stability concepts in Table 1 and prove the query complexity of Algorithm 1 for these properties (see Theorem 4.6).
We observe that due to responsiveness in all preference extensions of FEN-hedonic games, an edge modification that benefits one player, can never be a disadvantage for other players.
Observation 4.1
Let \(i,j\in N\) be two players in the FEN-hedonic game represented by a graph \(G=(N,F\cup E)\). Furthermore, let \(\succeq _i\) be i’s original preference relation, and \(\succeq _i'\) the preference relation of i after deleting edge (i, j). Formally, the resulting game is represented by the graph \(G'=(N,F \cup E \setminus \{(i,j)\})\) with the same preference extension. The following statements hold:
-
1.
If \((i,j) {\in } E\), for each \(C\in {\mathcal {N}}_i\), \(j\notin C\), it holds that \(C\succ _i C\cup \{j\}\) and \(C\cup \{j\}\sim _i' C\),
-
2.
If \((i,j) {\in } F\), for each \(C\in {\mathcal {N}}_i\), \(j\notin C\), it holds that \(C\cup \{j\}\succ _i C\) and \(C\cup \{j\}\sim _i' C\),
-
3.
If \((i,j) {\in } E\), and \(C\succ _i D\) for two coalitions \(C,D\in {\mathcal {N}}_i\) with \(j\in C\), it holds that \(C\succ _i' D\).
-
4.
If \((i,j) {\in } F\), and \(C\succ _i D\) for two coalitions \(C,D\in {\mathcal {N}}_i\) with \(j\notin C\), it holds that \(C\succ _i' D\).
Many stability concepts are of the form such that stability holds if and only if no player i satisfies a certain condition \(\phi (i)\). If there exists a player j that satisfies this condition \(\phi (j)\), we call j a witness for non-stability. Let \(\phi\) denote such a player property assigning each player i either value 1 (i is a witness against the property) or value 0 (i is not a witness). In the following proofs we require certain conditions to hold for \(\phi\) and show that all concepts in Table 1 share these conditions, which enables us to devise a unified testing scheme.
Definition 4.2
(feasible player property) Let \(\gamma\) be a stability concept and let \(\phi :{\mathfrak {G}}_n\times {\mathfrak {C}}_n \rightarrow \{0,1\}^{n}\) be a function that is parameterized by \(n \in {\mathbb {N}}\). If, for every n-player game \(G \in {\mathfrak {G}}_n\), every coalition structure \(\varGamma \in {\mathfrak {C}}_n\) and every \(i\in N\), it holds that \(\phi _i(G,\varGamma )=0\) if and only if \(\varGamma\) is stable in G with respect to \(\gamma\), then \(\phi\) is a player property. We say that \(\phi\) is feasible if for every \(n \in {\mathbb {N}}\), every \(G=(N, F\cup E)\in {\mathfrak {G}}_n\) and every \(\varGamma \in {\mathfrak {C}}_n\) the following conditions are met for each \(i\in N\).
-
(i)
\(\varGamma (i)\in \mathrm {Fav}(i) \implies \phi _i(G,\varGamma )=0\).
-
(ii)
The value \(\phi _i(G,\varGamma )\) can be determined with a constant number of queries to the oracles for G and \(\varGamma\) (i.e., dependent on \(\epsilon , d\), but independent of n).
-
(iii)
If \(\phi _i(G,\varGamma )=0\) and an edge (j, i), \(j\notin \varGamma (i)\) is removed from F, resulting in a new game \(G'\), it holds that \(\phi _i(G',\varGamma )=0\) remains valid.
-
(iv)
If \(\phi _i(G,\varGamma )=0\) and an edge (j, i), \(j\in \varGamma (i)\) is removed from E, resulting in a new game \(G'\), it holds that \(\phi _i(G',\varGamma )=0\) remains valid.
Player properties for the stability concepts we consider are summarized in Table 1. We note that if \(\phi\) is feasible, then \(\phi\) is edge-monotone. Feasibility (including edge-monotonicity) and the following two lemmas act as the tie between stability concepts we consider and property testing. In particular, they expose characteristics of the stability concepts that can be exploited by a property tester.
In our constructions we relate to the players’ favourite coalitions and make use of the following lemma that states that we can easily modify a player’s local surroundings to turn the current coalition into a favourite coalition. In other words, only a constant number of compromises suffice to optimise one player’s current situation. In particular, this turns a witness according to a feasible player property into a non-witness.
Lemma 4.3
Let \(G=(N,F\cup E)\) be a graph with bounded degree d and let \(\varGamma\) be a coalition structure of N. For each \(i\in N\), \({\mathcal {O}}(d)\) queries and d edge modifications are sufficient to turn \(\varGamma (i)\) into one of i’s favourite coalitions in the FEN-hedonic game represented by G.
Proof
If for player i, it already holds that \(\varGamma (i)\in \mathrm {Fav}(i)\), no modification is required. Otherwise we can proceed as follows: Accessing the (at most d) members of \(N_i\) requires at most d neighbourhood queries. Moreover, we can issue one find query each in order to determine whether a player \(j\in N_i=N_i^+\cup N_i^-\) is contained in \(\varGamma (i)\). For each \(j\in \varGamma (i)\cap N_i^-\), delete the edge (i, j) from E; for each \(j\in N_i^+\setminus \varGamma (i)\), remove the edge (i, j) from F. This requires at most \(|N_i^+|+ |N_i^-|\le d\) edge modifications. Note that this is independent of any bound c of the coalition size. The obtained coalition now only contains friends of i and i does not have any friends outside of \(\varGamma (i)\). Hence, for all preference extensions of FEN-hedonic games, no coalition is preferred to the current coalition \(\varGamma (i)\). \(\square\)
The following lemma extends Lemma 4.3 to multiple players. Essentially, it allows us to conclude that if a game is \(\epsilon\)-far from being stable for a stability concept that has a feasible player property, there must be roughly \(\epsilon n\) witnesses.
Lemma 4.4
Let \(G=(N,F\cup E) \in {\mathfrak {G}}_n\) be a FEN-hedonic game and let \(\varGamma\) be a coalition structure of N. Furthermore, let \(\gamma\) be a stability concept for which there exists a feasible player property \(\phi\). If there are at most k witnesses, \(k\cdot d\) edge modifications are sufficient to make the game stable with respect to \(\gamma\).
Proof
By Lemma 4.3, for each witness i, d edge modifications are enough to turn \(\varGamma (i)\) into a favourite coalition, thus, \(\phi (i)=1\) is no longer satisfied. For each player j that is not a witness, \(\phi (j)=0\) already holds which does not change due to Conditions (iii) and (iv) of Definition 4.2. If there are at most k witnesses, \(k\cdot d\) edge modifications are sufficient such that no player satisfies \(\phi (i)\), thus, stability with respect to \(\gamma\) holds. \(\square\)
With the help of this lemma we are now ready to prove that Algorithm 1 provides a property tester for the verification problem of each stability concept with a feasible player property.

Theorem 4.5
Let \(\gamma\) be a stability concept for which there exists a feasible player property \(\phi\). It holds that Algorithm 1 is a one-sided error property tester for \(\varGamma\)-stability verification with respect to \(\gamma\).
Proof
If \(\gamma\) holds, there is no witness for non-stability, i.e., for each sampled vertex \(\phi (i)=0\) holds. Therefore, the tester decides in Line 6 that \(\gamma\) holds with probability 1.
If \(\varGamma\) is \(\epsilon\)-far from being stable with respect to \(\gamma\), at least \(\epsilon d n\) edge modifications are required. Thus, by Lemma 4.4, there are at least \(\nicefrac {\epsilon d n}{d}=\epsilon n\) witnesses. Hence, the probability that a sampled player is a witness is at least \({\epsilon n}\cdot \nicefrac {1}{n}=\epsilon\).
Then, the algorithm correctly rejects if at least one witness is sampled, i.e., the condition in Line 5 is true. The probability of this event is 1 minus the probability that for each sampled player the condition in Line 5 is false, i.e., \(\phi _i(G,\varGamma )=0\). The latter probability is at most
Thus, the probability that the tester correctly rejects is at least \(\nicefrac 2 3\).
Since \(\phi\) is feasible, \(\phi _i(G,\varGamma )\) can be determined in constant query time. Hence, the tester requires constant query time dependent on the applied function \(\phi\). \(\square\)
Now it remains to show that each stability concept in Table 1 has such a feasible player property \(\phi\). By Theorem 4.5, Algorithm 1 is a verification tester with a query complexity depending on \(\phi\). As mentioned in Sect. 2.2, a one-sided error tester needs to present a witness when it rejects. Therefore, the query complexity of a one-sided error tester is at least the minimum size of a witness. This is, in particular, relevant for testing stability verification of core stability, as core stability puts conditions on the preferences of all participants of a potentially blocking coalition (see the corresponding player property in Table 1). Therefore, we parametrize by the maximum coalition size for testing stability verification of core stability.
Theorem 4.6
For the FEN-hedonic game model, the \(\varGamma\) -stability verification property can be tested with respect to
-
1.
perfection and individual rationality with query complexity in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\),
-
2.
Nash stability, individual and contractual individual stability with query complexity in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\),
-
3.
core stability with query complexity in \({\mathcal {O}}(\nicefrac {c^2\cdot d^{c^2{+1}}\cdot e^c}{\epsilon })\), where c is the maximum coalition size.
Proof
For each stability concept in Table 1 we show that there exists a feasible player property by considering the four conditions of Definition 4.2. This allows us to apply Theorem 4.5. In each case we determine the exact query complexity of the tester.
perfect The corresponding player property is
-
(i)
Condition (i) holds by definition of perfection.
-
(ii)
We have \(\phi _i(G,\varGamma )=1\) if and only if \(\varGamma (i)\) is missing one of i’s friends or contains one of i’s enemies, which can be verified in constant query time by asking whether j is in the same coalition as i for each \(j\in N_i\). Therefore, Condition (ii) is met with d queries per sampled player. In total, the query complexity is in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\).
-
(iii), (iv)
Conditions (iii) and (iv) are implied immediately by Observation 4.1, since the relation \(\varGamma (i)\succeq _i C\) remains valid in each relevant case.
individually rational Here, the player property is
-
(i)
Condition (i) holds, since \({\varGamma (i)} \in \mathrm {Fav}(i)\) implies that \({\varGamma (i)} \succeq _i\{i\}\).
-
(ii)
Since the decision whether \(\{i\}\succ _i\varGamma (i)\) only depends on \(|\varGamma (i)\cap N_i|\), d queries are sufficient, i.e., a total query complexity in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\), which satisfies Condition (ii).
-
(iii), (iv)
Again, Conditions (iii) and (iv) can be implied by Observation 4.1.
Nash-stable A witness i against Nash stability satisfies
-
(i)
Condition (i) holds, since \(\varGamma (i)\in \mathrm {Fav}(i)\) implies \(\varGamma (i)\succeq _i C\); in particular, this is true if \(C=C'\cup \{i\}\) for a \(C'\in \varGamma \cup \{\emptyset \}\).
-
(ii)
We consider the following cases regarding Condition (ii):
-
(a)
If \(\varGamma (i)\cap N_i^+\ne \emptyset\), i wants to deviate to a coalition C with \(u_i(C \cup \{ i \}) > u_i(\varGamma (i))\). Due to the linearity of the preferences, this can only be \(\{ i \}\) (with \(u_i(\{ i \}) = 0\)) or a coalition in \(\varGamma\) that contains at least one friend. There are at most \(|N_i^+|\le d\) coalitions in \(\varGamma\) that contain a friend, namely \(\varGamma (j)\), \(j\in N_i^+\). Hence, at most d comparisons of coalitions are sufficient, which can be done with at most d neighbour and d find queries by Equation (1).
-
(b)
If \(\varGamma (i)\cap N_i^+=\emptyset\), but \(N_i^+\ne \emptyset\), the analysis is analogous to (a).
-
(c)
If \(N_i^+=\emptyset\) and \(\varGamma (i)\cap N_i^-=\emptyset\), \(\varGamma (i)\) is already one of i’s favourite coalitions, hence \(\phi _i(G,\varGamma )=0\).
-
(d)
If \(N_i^+=\emptyset\) and \(\varGamma (i)\cap N_i^-\ne \emptyset\), i wants to deviate to the single player coalition \(\{i\}\), hence \(\phi _i(G,\varGamma )=1\).
It can be decided with d neighbour queries which of the four cases holds for \(\varGamma (i)\). The at most d coalition comparisons require at most d additional find queries. Therefore, \(\phi _i(G,\varGamma )\) can be decided with \({\mathcal {O}}(d)\) queries, satisfying Condition (ii). The total query complexity of Algorithm 1 is in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\).
-
(a)
-
(iii), (iv)
Again, Conditions (iii) and (iv) are implied by Observation 4.1.
individually stable A witness i against individual stability satisfies
-
(i)
Hence, if i is not a witness for a Nash deviation, it cannot be a witness here, either. Therefore, Condition (i) holds.
-
(ii)
Since \(C\cup \{i\}\succ _i\varGamma (i)\) was already discussed for the case of Nash stability, it remains to consider the additional condition \(\forall j\in C: C\cup \{i\}\succeq _j C\) that extends the player property of Nash stability. If i wants to deviate, this is due to one of the cases (a), (b), or (d) from the case distinction of Nash stability above. In cases (a) and (b), we have to consider at most \(|N_i^+|\) candidate coalitions, i can deviate to. For each neutral player \(j\in N_i^0\), it holds that \(\varGamma (j)\sim _j\varGamma (j)\cup \{i\}\). Thus, we only have to ask i’s neighbours for permission to enter the new coalition, which are in total at most d. In fact, due to the symmetry of preferences, friends always welcome i, and enemies never do. In case (d), \(\varGamma (i)\) is not acceptable, and i is always welcome in \(\{i\}\).
We obtain \(\phi _i(G,\varGamma )=0\) if and only if there are no enemies in C, which we can decide with at most d queries.
Thus, we can employ the same queries as for Nash stability in order to determine \(\phi _i(G,\varGamma )\), which satisfies Condition (ii). The total query complexity of Algorithm 1 is in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\).
-
(iii)
If i wants to move to another coalition \(C\subseteq \varGamma \cup \{\emptyset \}\) but there exists a player \(j\in C\) with \(C\succ _j C\cup \{i\}\), then j is i’s enemy due to Observation 4.1. Therefore, deleting edges from F cannot make \(C \cup \{ i \}\) a feasible deviation if it was not feasible before. If i is not a witness because there does not exist any preferred coalition to move to, the arguments for Nash stability can be applied. Thus, Condition (iii) is met.
-
(iv)
If an edge (i, j) is deleted from E and \(j\in \varGamma (i)\), Condition (iv) can only be false if \(\varGamma (j) \succ _j \varGamma (j)\cup \{i\}\). However, \(i \in \varGamma (j)\) because \(\varGamma (j) = \varGamma (i)\), which is a contradiction. If i is not a witness because there does not exist any preferred coalition to move to, the arguments for Nash stability can be applied. Therefore, Condition (iv) is met.
contractually individually stable: A witness i against contractually individual stability satisfies
-
(i)
Condition (i) holds analogously to individual stability.
-
(ii)
Observe that for neutral players \(j'\in N_i^0\cap \varGamma (i)\) it holds that \(\varGamma (i)\sim _{j'} \varGamma (i)\setminus \{i\}\) and for enemies \(j'\in N_i^-{\cap \varGamma (i)}\) it holds that \(\varGamma (i)\setminus \{i\}\succ _{j'}\varGamma (i)\).
Again, if i wants to deviate to a coalition, cases (a), (b) and (d) from Nash stability remain. In case (a) i has friends in \(\varGamma (i)\) that i contractually depends on. Here \(\phi _i(G,\varGamma )=0\). In cases (b) and (d) there are no friends in \(\varGamma (i)\), which means there is no contractual dependence. Then, i is a witness against contractual individual stability if and only if it is a witness against individual stability. Thus, in case (d) \(\phi _i(G,\varGamma )=1\) and in case (b) that same queries as above can be applied. Thus, we need at most \({\mathcal {O}}(d)\) queries in order to determine \(\phi _i(G,\varGamma )\). The total query complexity of Algorithm 1 is in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\), which satisfies Condition (ii).
-
(iii), (iv)
Conditions (iii) and (iv) hold with analogous arguments as above.
core-stable A witness i against core-stability satisfies
Observe that if there exists a coalition blocking \(\varGamma\), its connected components also block \(\varGamma\). Hence, we can assume that C is connected. It either holds that \(\varGamma (i)\) is not acceptable for i, and \(C=\{i\}\) or C is a neighbouring coalitionFootnote 1 to i.
-
(i)
Condition (i) holds, since i cannot strictly prefer a blocking coalition to a favourite coalition.
-
(ii)
In order to detect a connected blocking coalition C that contains i, we have to query the oracle as follows: We verify whether \(\varGamma (i)\) is acceptable for i by considering the intersection of i’s neighbours \(N_i\) with \(\varGamma (i)\). If it is not acceptable, \(C=\{i\}\) holds, and thus, \(\phi _i(G,\varGamma )=1\). If \(\varGamma (i)\) is acceptable, C can only be any of i’s neighbouring coalitions that are connected and of size \(|C|\le c\). There are at most
$$\begin{aligned} \sum _{{\ell }=1}^c\left( {\begin{array}{c}d^c\\ {\ell }\end{array}}\right) \le \sum _{{\ell }=1}^c\left( \frac{d^c\cdot e}{{\ell }}\right) ^{\ell }\le c\cdot d^{c^2}\cdot e^c \end{aligned}$$possible such coalitions. For each of these coalitions C, we ask the at most c contained players \(j\in C\) whether they prefer C to \(\varGamma (j)\) by querying their at most d neighbours. This is sufficient to verify whether one of the coalitions blocks \(\varGamma\) and, thus, whether i is a witness. Therefore, the total query complexity of Algorithm 1 is in \({\mathcal {O}}(\nicefrac {c^2\cdot d^{c^2{+1}}\cdot e^c}{\epsilon })\) and Condition (ii) holds.
-
(iii), (iv)
Let \(\phi _i(G,\varGamma )=0\), i.e., for each neighbouring coalition C to i, there exists some \(j\in C\) such that \(\varGamma (j)\succeq _j C\). Condition (iii) holds by the following argument. Assume, an edge (i, k) is removed from F, \(k\in \varGamma (i)\). Then, it holds that: If \(k\ne j\) and \(i\ne j\), \(\phi _i(G,\varGamma )=0\) remains valid. If \(i=j\), \(\varGamma (i)\succeq _i C\) implies that \(\varGamma (i)\succeq '_i C\) by Observation 4.1. If \(k=j\) and \(i\ne j\), \(\varGamma (k)\succeq _k C\) implies that \(\varGamma (k)\succeq '_k C\) by Observation 4.1. Similarly, Condition (iv) is obtained by Observation 4.1.
\(\square\)
4.2 Testing existence problems
Now we prove Theorem 1.1. In general, there always exists an individually rational coalition structure (all coalitions are singletons). Bogomolnaia and Jackson [8] show that in symmetric additively separable hedonic games there always exists a Nash-stable coalition structure. Note that in our model the argument that if a player deviates, the social welfare increases, remains valid, even for bounded coalition size. Their result and its proof extend easily to the case of bounded coalitions sizes, and a sketch of the proof is provided for the sake of referencing to parts of it later.
Lemma 4.7
([8]) Each symmetric FEN-hedonic game (such as all preference extensions of FEN-hedonic games) allows a Nash-stable, and consequently individually stable and contractually individually stable coalition structure.
Proof
(sketch) Let \(\varGamma\) be a coalition structure containing coalitions \(\varGamma (i)\) and \(C\subseteq N\) with \(|C|\le c-1\). We assume that \(C\cup \{i\}\succ _i\varGamma (i)\). Moreover, let \(\varGamma '\) be the coalition structure obtained if i deviates to C, i.e., \(\varGamma '\) contains \(\varGamma (i)\setminus \{i\}\) and \(C\cup \{i\}\). The social welfare \(\mathrm {SW}(\varGamma )\) of a coalition structure \(\varGamma\) is the sum of all players’ utilities of their current coalition. We observe that the difference of the social welfare of \(\varGamma '\) and \(\varGamma\) always increases, which means that there exists a local maximum resulting in a Nash-stable coalition structure. It holds that the difference \(\mathrm {SW}(\varGamma ')-\mathrm {SW}(\varGamma )\) equals
Hence, there always exists a Nash-stable coalition structure, even if the coalition size is bounded. Since Nash stability implies individual and contractual individual stability, they are guaranteed to exist as well. \(\square\)
There does not necessarily exist a perfect coalition structure. For example, there does not exist any perfect coalition structure for \(G=(\{1,2,3\},F \cup E)\), where \(F=((1,2), (2,3))\), \(E=(3,1)\). On the other hand, if \(F = \emptyset\), the utility of any coalition structure is at most 0, so singleton coalitions are perfect; if \(E = \emptyset\), there exists a perfect coalition structure if and only if no connected component is larger than c. For the general case \(|E |, |F |\ge 0\), we show that there exists a tester with one-sided error.
Theorem 4.8
There is a one-sided error property tester with constant query complexity for the existence of a perfect coalition structure in the FEN-hedonic game model with a constant coalition size bound c.
Proof
Let \(v \in N\), and observe that C is a favourite coalition of v if and only if \(C \cap N^+_v = N^+_v\) and \(C \cap N^-_v = \emptyset\). It follows that there exists a perfect coalition structure \(\varGamma\) if and only if there does not exist any edge in E between vertices of the same connected component of \(G[N_F]\), where \(N_F\) is the set of endpoints in F, i.e., \(N_F = \{u \mid (u,v) \in F \}\). This suggests the following algorithm: first, sample a set S of \(|S |= \nicefrac {1}{\epsilon } \ln 3\) vertices at random. For each \(v \in S\), we run a BFS that follows only edges in F. If, at any point during its execution, the BFS has explored more than c vertices or has visited two endpoints u, w of the same edge \((u,w) \in E\), the tester rejects.Footnote 2 Otherwise, i.e., if none of these two conditions is met during the BFS for any \(v \in S\), the tester accepts the graph.
By the above observation, every path in G that contains only edges from F must be in the same coalition in a perfect coalition structure. The algorithm rejects only when it finds a path P such that for every coalition structure \(\varGamma\) such that some coalition \(C \in \varGamma\) contains P, C also contains \((u,v) \in E\), which is a witness against the existence of a perfect coalition structure.
If G is \(\epsilon\)-far from having a perfect coalition structure, then at least \(\epsilon d n\) edges in \(F \cup E\) have to be removed in order to make G have a perfect coalition structure because having a perfect coalition structure is an edge-monotone property (i.e., adding edges never decreases the graph’s distance to the property, see also Lemma 4.4). Let R be a minimal set of edges that have to be removed. Since every vertex is incident to at most d other vertices, at least \(2 |R |/ d> 2 \epsilon d n / d > \epsilon n\) vertices must be incident to an edge from \(|R |\). If a vertex that is incident to an edge in R is in S, the algorithm finds a witness. The probability that none of the vertices in S is incident to an edge in R is at most
As argued above, if a vertex in S is incident to an edge from R, the tester finds (u, v) and rejects. \(\square\)
4.3 Extensions to weighted and directed encodings
Weighted, Undirected FEN-Encodings. The resulting games are equivalent to additively separable hedonic games [8]. If each edge contributes equally to the edit distance (that underlies the definition of \(\epsilon\)-far), this does not affect our proofs and Lemma 4.7 because they rely on the linearity of the utility function only. If an edge contributes proportional to its weight, we can use the following standard techniques from property testing. The first option is to require that the weights are bounded by some value W so that we can simply increase the sampling size in our algorithms by a factor of W. To see why this works, imagine an edge with weight w as w parallel edges, which essentially increases the bound on the vertex degrees to \(W \cdot d\). On the other hand, unbounded weights cannot be handled in the standard model by constant-query testers because a single edge that has weight \(2 \epsilon d n\) can make a graph \(\epsilon\)-far, yet it is very unlikely to find this edge by sampling O(1) vertices uniformly. Therefore, another option is to allow vertex sampling proportional to the weights of incident edges or, equivalentlyFootnote 3, sampling edges proportionally to their weight.
We describe the modifications that are required to make our algorithms work with edge-weighted graphs and weight-proportional vertex sampling. Let \(G = (N,F \cup E)\) be a graph with edge weights \(w : F \rightarrow \ (0, \infty )\) and \(w : E \rightarrow \ (-\infty , 0)\), and define the weight of a vertex v as \(w(v) = \sum _{e \in N_v} |w(e) |\). For the sake of simplicity, we write \(w : F \cup E \rightarrow (0, \infty ) \cup (-\infty , 0)\) in the following.
Definition 4.9
(weight-aware graph distance) A graph \(G = (N, F \cup E)\) with weights \(w : F \cup E \rightarrow (0, \infty ) \cup (-\infty , 0)\) is \(\epsilon\)-far from an edge-monotoneFootnote 4 property \({\mathcal {P}}\) if there is no set of edges \(R \subseteq F \cup E\) with weight \(w(R) := \sum _{e \in R} |w(e) |\le \epsilon \cdot |w(F \cup E) |\) such that the graph \(G' = (V, (F \cup E) \setminus R)\) is in \({\mathcal {P}}\).
Definition 4.10
(weight-proportional distribution) Given a set S that is weighted by a function \(w : S \rightarrow (0, \infty )\), the weight-proportional distribution \({\mathcal {W}}_w(S)\) assigns probability mass w(x) /w(S) to \(x \in S\), i.e., if \(X \sim {\mathcal {W}}_w(S)\) is a random variable, then \(\Pr [X = s] = w(x) / \sum _{y \in S} w(y)\).
Definition 4.11
(weight-aware tester) A wait-aware one-sided error tester for graphs \(G = (N, F \cup E)\) with edge weights \(w : F \cup E \rightarrow (0, \infty ) \cup (-\infty , 0)\) is a one-sided error tester (see Definition 2.2) that has oracle access to i.i.d. samples from the distribution \({\mathcal {W}}_w(N)\).
Weighted Verification Problems. Lemma 4.3 and Lemma 4.4 hold without modifications for edge-weighted graphs. We modify Algorithm 1 as follows: in Line 3, we sample s players from N proportional to the sum of weights of their incident edges, i.e., the sum of weights of the relations to their friends and enemies. The resulting algorithm is given by Algorithm 2.

Theorem 4.12
(Theorem 4.5, weighted version)Let \(\gamma\) be a stability concept for which there exists a feasible player property \(\phi\). It holds that Algorithm 2 is a weight-aware one-sided error property tester for \(\varGamma\)-stability verification with respect to \(\gamma\).
Proof
The modified algorithm still accepts all stable coalitions \(\varGamma\). If \(\varGamma\) is \(\epsilon\)-far from being stable with respect to \(\gamma\), every edge set \(R \subseteq F \cup E\) whose removal stabilizes \(\varGamma\) has weight at least \(\epsilon \sum _{e \in F \cup E} w(F \cup E)\) by the weight-aware definition of \(\epsilon\)-far from above. Hence, the probability that a sampled player is a witness is at least
The proof continues as the proof of Theorem 4.5. \(\square\)
Weighted Existence Problems. Lemma 4.7 still holds for symmetric, additively separable hedonic games. The tester for the existence of a perfect coalition structure can be generalized as follows.
Theorem 4.13
(Theorem 4.8, weighted version)There is a weight-aware one-sided error tester with constant query complexity for the existence of a perfect coalition structure in the FEN-hedonic game model with a constant coalition size bound c.
Proof
Let \(G = (N, F \cup E)\) be the input graph. Consider the following algorithm: first, sample a set S of \(|S |= \nicefrac {1}{\epsilon } \ln 3\) vertices from \({\mathcal {W}}_w(N)\). For each \(v \in S\), we run a BFS that follows only edges in F. If, at any point during its execution, the BFS has explored more than c vertices or has visited two endpoints u, w of the same edge \((u,w) \in E\), the tester rejects. Otherwise, i.e., if none of these two conditions is met during the BFS for any \(v \in S\), the tester accepts the graph.
As in the proof of Theorem 4.8, we can argue that the algorithm never rejects a graph that has a perfect coalition. Therefore, let G be \(\epsilon\)-far from having a perfect coalition, let \(R \subseteq F \cup E\) be such that \((N, (F \cup E) \setminus R)\) is in \({\mathcal {P}}\) and w(R) is minimal among all such sets. We only need to prove that a properly adapted version of Inequality 3 holds. Observe that \(\sum _{v \in \{x, y \mid (x,y) \in R \}} |w(v) |\ge 2 \epsilon \cdot w(F \cup E)\) by the weight-aware definition of \(\epsilon\)-far (see Definition 4.9). Therefore, the probability that none of the vertices in S is incident to an edge in R is at most
\(\square\)
Directed, Unweighted FEN-Encodings. In this case, friendship relations are no longer necessarily symmetric. For instance, this can be the case in social networks with a follower system. In property testing, there are two different models of directed graphs.
In the bidirectional model, we may see all incoming and outgoing edges (followed players and followers can be queried). Assuming bounded out-degree, verification is not affected by the bidirectional model.
In the unidirectional model, we may see only one type - usually outgoing edges (only followed players can be queried). For the unidirectional model with outgoing edges, the verification problems remain testable. While being a witness against perfection, individual rationality, or Nash stability only depends on players’ own preferences, the query complexity for individual stability and contractually individual stability depends on (the minimum of) the in-degree or the maximum coalition size: the case analysis changes because we are required to evaluate the preferences of the other members of the (still at most O(d)) affected coalitions.
Although there is a lossy but still sublinear transformation from constant-query testers in the bidirectional model into the unidirectional model [14], the unidirectional model is often much harder to analyse and yields testers with worse query complexity. In detail, we obtain the following results.
Directed Verification Problems. Observation 4.1, Definition 4.2, and Lemma 4.3 are stated from a single player’s perspective. Hence they remain valid assuming the standard notation that (i, j) represents an arc from i to j. Lemma 4.4, Algorithm 1, and Theorem 4.5 are unaffected by the generalisation. In fact the changes only depend on the player properties of the stability notions.
Theorem 4.14
(Theorem 4.6, directed, unidirectional version)For the FEN-hedonic game model, the \(\varGamma\)-stability verification property can be tested with respect to
-
1.
perfection, individual rationality, and Nash stability with query complexity in \({\mathcal {O}}(\nicefrac {d}{\epsilon })\),
-
2.
individual and contractual individual stability with query complexity in \({\mathcal {O}}(\nicefrac {d(d+c)}{\epsilon })\),
-
3.
core stability with query complexity in \({\mathcal {O}}(\nicefrac {c^2\cdot d^{c^2{+1}}\cdot e^c}{\epsilon })\), where c is the maximum coalition size.
Proof
Conditions (i), (iii), and (iv) remain valid for the unidirectional case. For perfection, individual rationality, and Nash stability Condition (ii) still holds with the same query complexity, since only queries for outgoing edges are made for each potential witness.
For individual stability, there are still at most \({\mathcal {O}}(d)\) possible coalitions, a sampled player i might want to deviate to. Whenever player i wants to deviate to a new coalition C, now each player j in C needs to be asked whether (j, i) is an edge in E. If, for all \(j\in C\), that is not the case, i is a witness. This requires \({\mathcal {O}}(d(d+c))\) queries, which satisfies Condition (ii). The total complexity of Algorithm 1 is in \({\mathcal {O}}(\nicefrac {d(d+c)}{\epsilon })\).
Similarly, for contractually individual stability, a player k only lets i move to a new coalition, if (k, i) is not an edge in F. If for each \(k\in \varGamma (i)\) that is the case, i is a witness.
For core stability, we already employ all necessary queries to new coalition members in the proof of the undirected case. Therefore, the query complexity remains the same. \(\square\)
Directed Existence Problems. Lemma 4.7 is not true anymore in general (note that Equation (2) does not hold in general due to asymmetry; see [8] for an example). A perfect coalition structure exists if the weakly connected components induced by F do not induce any edges from E. Exploring weakly connected components causes no problem in the bidirectional model, but in the unidirectional model it can render exploration almost impossible. For example, consider a cycle of length c with alternating edge direction and all but one edge being friend edges. This graph makes it impossible to form perfect coalitions, and having \(\epsilon d n\) copies of it as subgraphs makes a graph \(\epsilon\)-far from admitting a perfect coalition structure. In fact, we show that testing the existence of a perfect coalition structure requires almost linear query complexity.
Theorem 4.15
Let \(\epsilon > 0\) and \(c \ge \nicefrac {1}{\epsilon d}\). There is no one-sided error \(\epsilon\)-tester for the existence of a perfect coalition structure with coalition size bound c in the unidirectional model that uses \(o(n^{1 - 2 \epsilon d})\) queries.
Proof
For all even \(\ell \ge 6\), we define an alternating-cycle gadget \(H_{\ell }=(V_{\ell },F_{\ell } \cup E_{\ell })\), where \(V_{\ell } = \{ 0, \ldots , \ell -1 \}\), \(F_{\ell } = \{ (i, i-1) \mid i \in \{1, 3, \ldots , \ell -1 \} \} \cup \{ (i, i+1) \mid i \in \{1, 3, \ldots , \ell -3 \} \}, E_{\ell } = \{(\ell -1, 0)\}\) (see Fig. 2). Let \(n \ge \ell\); we construct the graph \(G_{\ell }\) as the union of \(\lfloor \nicefrac {n}{\ell } \rfloor\) copies of \(H_{\ell }\) and \(n - \ell \cdot \lfloor \nicefrac {n}{\ell } \rfloor\) isolated vertices. Without loss of generality, to simplify the argument from now on, we assume that n is divisible by \(\ell\) and that \(\ell\) is even. The graph \(G_{\ell }\) is \(\epsilon\)-far from having a perfect coalition structure if \(\nicefrac {n}{\ell } > \epsilon d n \Leftrightarrow \ell < \nicefrac {1}{\epsilon d}\).
A one-sided error tester \({\mathcal {T}}\) needs to sample all odd vertices of an alternating-cycle gadget to certify that \(G_{\ell }\) does not have a perfect coalition structure. Without loss of generality, we may assume that whenever \({\mathcal {T}}\) queries a vertex v, it gets all vertices reachable from v in return (not just the \(i^{th}\) neighbour of v it queried for). This modification makes the queries that \({\mathcal {T}}\) can issue only stronger but since at most 2 vertices are reachable from v, this reduces the query complexity of the tester by at most a factor \(\nicefrac {1}{3}\). Therefore, whenever \({\mathcal {T}}\) queries for a vertex v, the answer is either an isolated vertex \(\{ v \}\) if v is an even vertex, or a triple \(\{u, v, w\}\) if v is an odd vertex. Note that due to the strengthening of queries, querying u or w after querying v does not reveal more information to \({\mathcal {T}}\). We use Yao’s principle and prove the theorem by lower-bounding the query complexity of any deterministic algorithm on the following input distribution. We generate all feasible vertex labelings of \(G_{\ell }\) (isomorphic copies of \(G_\ell\)) and construct the uniform distribution \({\mathcal {D}}\) over these graphs. To simplify the analysis, we may assume that the labels are lazily assigned to an initially unlabeled version of \(G_\ell\), i.e., when the vertex corresponding to a label is queried by or returned to \({\mathcal {T}}\) for the first time. It is known that the resulting random graph is drawn from \({\mathcal {D}}\) [25, Proof of Claim 5.5.2].
Consider running a tester \({\mathcal {T}}\) for perfection on a graph G sampled from \({\mathcal {D}}\). Let s be an upper bound on the query complexity of \({\mathcal {T}}\), and without loss of generality, assume that \(s \le \nicefrac {n}{6}\). Let \(S = (t_1, \ldots , t_s)\) be the sequence of all vertices from V that are queried by \({\mathcal {T}}\). Fix an arbitrary alternating-cycle gadget H in G. Intuitively, to discover all odd vertices of H, an odd vertex must be revealed at \(\ell / 2\) positions of S. There are \(\left( {\begin{array}{c}s\\ \ell /2\end{array}}\right)\) ways to choose these positions. The probability to discover an odd vertex is roughly \(\nicefrac {\ell /2}{n}\), but since the set of unknown vertices is reduced by every query and the number of unknown odd vertices from H decreases, we take slightly more care.
Formally, for \(j \ge 1\), consider the \(j^{th}\)-smallest i such that \(t_{i} \in V(H)\) and \(t_{i}\) is an odd vertex. When this query is issued, the probability that it reveals an odd vertex from H is \((\ell /2 - (j-1)) / (n-k_{i})\), where \(k_i\) is the number of assigned labels before this query. By repetitively applying the definition of conditional probability to the event that the \(j^{th}\) odd vertex of H is discovered conditioned on the \(1^{st}\) to the \((j-1)^{th}\) odd vertex being discovered, we can rearrange the probability that all odd vertices of H are revealed to obtain a product of the former probabilities. It follows that the probability that S contains all \(\ell /2\) odd vertices of H is at most
Since, for all \(i \in [s]\), we have \(k_i \le 3s\), the subtrahend 3s accounts for the fact that each query may reveal at most 3 vertices to \({\mathcal {T}}\). Inequality \((\star )\) follows from the assumption \(s \le \nicefrac {n}{6}\).
For any \(i \in [s]\), let \(E_i\) be the event that S contains all odd vertices of the alternating-cycle gadget that \(t_i\) is part of. By the union bound over \((E_i)_{i \in [s]}\), S contains all odd vertices of at least one alternating-cycle gadget with probability at most \(s \cdot ( \frac{6s}{n} )^{\ell /2-1}\). We conclude that
Assuming \(s \in o(n^{1-2 \epsilon d})\) contradicts the assumption that \({\mathcal {T}}\) is a tester with error probability at most \(\nicefrac {1}{3}\). \(\square\)
5 Open questions
A natural question that is related to finding stable partitions is the following: Given a graph G and a partition \(\varGamma\), is the partition \(\varGamma\) far from being stable in G (instead of the graph being far from \(\varGamma\)-stable)? This can be generalized further: Property testing is a special case of local computation algorithms (LCA), where one shall provide oracle access to a solution, given oracle access to the input. In property testing, the solution is a single bit (accept or reject). While it is beyond the scope of sublinear algorithms to actually compute a stable partition, one may seek to develop an LCA that gives oracle access to it.
Generalizing the results we obtained, one may seek to obtain sublinear algorithms for games with unbounded coalition size. Here, the main difficulty is to obtain insights into the local structure of very large, say, linear sized coalitions. Following a slightly different line of thought, one may consider other graphs models like the dense model, where (almost) all players relate to each other and one may ask how two players i, j relate, or the general graph model, where vertices have arbitrary degrees. These models are quite different from the bounded-degree model, as well as from each other. For the dense graph model, a characterization using Szemerédi regular partitions is known [1], and it seems possible that coalition formation could be expressed in terms of regular partitions. Much less is known about the general model. So far, most research is still focused on elementary graph problems like counting the number of constant-size cliques [20]. It would be interesting to see whether stability properties are also constant-query testable in these two models. Another direction for further studies is property testers with two-sided error. These testers do not need to provide a witness against the property, but rather sufficient statistics that a graph is far from a property with constant probability.
As mentioned in the introduction, there exist also plenty of other stability concepts like Pareto-optimality and popularity that can operate on the same preference extension, which may be interesting to analyse in order to obtain a deeper understanding of locality mechanics in FEN-hedonic games. Here, the main difficulty is to circumvent the usually high computational complexity of the exact decision problems.
Finally, one may study other models of hedonic games, in particular with ordinal preferences (e.g., rankings over known edges [31]). This requires further modelling of the oracle access and considered distance measures.
Notes
We call \(C\subseteq {\mathcal {N}}_i\) a neighbouring coalition if at least one agent \(j\in C\), \(j\ne i\), is a neighbour of i in \(N_i\) (i.e., j is either a friend in \(N_i^+\) or an enemy in \(N_i^-\)).
We note that the algorithm does not wrongly detect infeasible blocking coalitions when rejecting after exploring c vertices. A necessary condition for a coalition structure to be perfect is that for every connected component H in (N, F), all vertices of H must be in the same coalition. If H is larger than c, it follows that there is no coalition structure with bounded coalition size c such that every player is in one of their favourite coalitions. In other words, H is a witness.
The following way to convert from one into the other is known: (i) Sample a vertex proportional to its weight and pick an incident edge with probability proportional to the edge’s weight relative to the weight of all incident edges, (ii) sample an edge proportional to its weight, and pick an incident vertex uniformly at random.
All properties that we consider are edge-monotone. Note that it is not clear how to define \(\epsilon\)-far in general for properties that are not edge-monotone because one would need to assign weights to added edges. To minimize the distance of G to \({\mathcal {P}}\), one could always choose the smallest weight, i.e., 1, but this might break the semantics of the weights.
References
Alon, N., Fischer, E., Newman, I., & Shapira, A. (2009). A combinatorial characterization of the testable graph properties: It s all about regularity. SIAM J. Comput., 39(1), 143.
Aziz, H., & Savani, R. (2016). Hedonic games. In: Handbook of Computational Social Choice, Cambridge University Press.
Aziz, H., Brandt, F., & Seedig, H.G. (2013). Computing desirable partitions in additively separable hedonic games. Artificial Intelligence 195.
Aziz, H., Harrenstein, P., Lang, J., & Wooldridge, M. (2016). Boolean hedonic games. In: Proceedings of the 15th international conference on principles of knowledge representation and reasoning.
Ballester, C. (2004). NP-completeness in hedonic games. Games Econom. Behavior, 49(1), 1–30.
Banerjee, S., Konishi, H., & Sönmez, T. (2001). Core in a simple coalition formation game. Social Choice and Welfare 18
Ben-Zwi, O., Lachish, O., & Newman, I. (2007). Lower bounds for testing euclidean minimum spanning trees. Inf. Process. Lett., 102(6), 219.
Bogomolnaia, A., & Jackson, M. O. (2002). The stability of hedonic coalition structures. Games Econom. Behavior., 38(2), 201.
Cechlárová, K. (2002). On the complexity of exchange-stable roommates. Descrete Appl. Math., 116, 279.
Cechlárová, K., & Romero-Medina, A. (2001). Stability in coalition formation games. International Journal of Game Theory 29
Chalkiadakis, G., Elkind, E., & Wooldridge, M. J. (2011). Computational aspects of cooperative game theory. California: Morgan and Claypool Publishers.
Czumaj, A., & Sohler, C. (2008). Testing euclidean minimum spanning trees in the plane. ACM Trans. Algorithms, 4(3), 1–23.
Czumaj, A., Goldreich, O., Ron, D., Seshadhri, C., Shapira, A., & Sohler, C. (2014). Finding cycles and trees in sublinear time. Random Struct. Algorithm., 45(2), 139.
Czumaj, A., Peng, P., & Sohler, C. (2016). Relating two property testing models for bounded degree directed graphs. In: Proceedings of the 48th annual ACM symposium on theory of computing.
Darmann, A., Elkind, E., Kurz, S., Lang, J., Schauer, J., & Woeginger, G. J. (2018). Group activity selection problem with approval preferences. Int. J. Game Theor., 47(3), 767.
Dimitrov, D., Borm, P., Hendrickx, R., & Sung, S. C. (2006). Simple priorities and core stability in hedonic games. Soc. Choice Welfare, 26(2), 421.
Drèze, J. H., & Greenberg, J. (1980). Hedonic coalitions: Optimality and stability. Econometrica, 48(4), 987.
Dunbar, R. (1992). Neocortex size as a constraint on group size in primates. J. Hum. Evol., 22(6), 469.
Dunbar, R., & Dunbar, R. I. M. (1998). Grooming, Gossip, and the Evolution of Language. Cambridge: Harvard University Press.
Eden, T., Ron, D., & Seshadhri, C. (2018). On approximating the number of k-cliques in sublinear time. In: Proceedings of the 50th annual ACM SIGACT symposium on theory of computing.
Elkind, E., & Wooldridge, M. (2009). Hedonic coalition nets. In: Proceedings of the 8th international conference on autonomous agents and multiagent systems.
Fichtenberger, H., Krivošija, A., & Rey, A. (2019). Testing individual-based stability properties in graphical hedonic games. In: Proceedings of the 18th international conference on autonomous agents and multiAgent systems.
Goldreich, O. (2017). Introduction to property testing. Cambridge: Cambridge University Press.
Goldreich, O., & Ron, D. (2002). Property testing in bounded degree graphs. Algorithmica,32(2).
Goldreich, O., & Ron, D. (2011). On proximity-oblivious testing. SIAM J. Comput., 40(2), 534.
Google. (2020a). Prevent competing ads on a page with labels. Retrieved 18 May 2020 from https://support.google.com/admanager/answer/190582?hl=en.
Google. (2020b). Prevent competitors from serving together. Retrieved 18 May 2020 from https://support.google.com/admanager/answer/6145371?hl=en.
Hellweg, F., Schmidt, M., & Sohler, C. (2010). Testing euclidean spanners. In: Proceedings of the European symposium on algorithms.
Hernando, A., Villuendas, D., Vesperinas, C., Abad, M., & Plastino, A. (2010). Unravelling the size distribution of social groups with information theory in complex networks. Eur. Phys. J. B, 76(1), 87.
Igarashi, A., & Elkind, E. (2016). Hedonic games with graph-restricted communication. In: Proceedings of the 15th international conference on autonomous agents and multiagent systems.
Lang, J., Rey, A., Rothe, J., Schadrack, H., & Schend, L. (2015). Representing and solving hedonic games with ordinal preferences and thresholds. In: Proceedings of the 14th international conference on autonomous agents and multiagent systems.
Lee, H., & Shoham, Y. (2015). Stable invitations. In: Proceedings of the 29th AAAI conference on artificial intelligence.
Lee, H., & Williams, V. (2017). Complexity of the stable invitations problem. In: Proceedings of the 31th AAAI conference on artificial intelligence.
Ota, K., Barrot, N., Ismaili, A., Sakurai, Y., & Yokoo, M. (2017). Core stability in hedonic games among friends and enemies: Impact of neutrals. In: Proceedings of the 26th international joint conference on artificial intelligence.
Peters, D. (2016). Grahical hedonic games of bounded treewidth. In: Proceedings of the 13th AAAI conference on artificial intelligence.
Peters, D., & Elkind, E. (2015). Simple causes of complexity in hedonic games. In: Proceedings of the 24th international joint conference on artificial intelligence.
Sliwinski, J., & Zick, Y. (2017). Learning hedonic games. In: Proceedings of the 26th international joint conference on artificial intelligence.
Sung, S. C., & Dimitrov, D. (2010). Computational complexity in additive hedonic games. Eur. J. Oper. Res., 203(3), 635.
Woeginger, G. J. (2013). A hardness result for core stability in additive hedonic games. Math. Soc. Sci., 65(2), 101.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
A preliminary version of this work was published in the proceedings of AAMAS 2019 (International Conference on Autonomous Agents and Multiagent Systems).
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Fichtenberger, H., Rey, A. Testing stability properties in graphical hedonic games. Auton Agent Multi-Agent Syst 35, 26 (2021). https://doi.org/10.1007/s10458-021-09505-x
Accepted:
Published:
DOI: https://doi.org/10.1007/s10458-021-09505-x