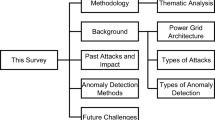
Abstract
Cyber-attacks on power system assets are increasingly causing disruption of operations for modern-day utilities. Intrusion detection systems are essential for the detection and categorization of these attacks in real-time. A large number of researchers and practitioners have developed such systems for protecting various power grid components against a number of possible attacks. In this paper, we review the studies and outline their significance. We first briefly describe various power system components that are vulnerable to attack. Then we categorize known attack types. Finally, we present the literature referring to these aspects of building intrusion detection systems for power grids.


Similar content being viewed by others
Data availability
The datasets analyzed during the current study are available at: ORNL-ICS Dataset [16]: https://sites.google.com/a/uah.edu/tommy-morris-uah/ics-data-sets. Electra Dataset [28]: http://perception.inf.um.es/ICS-datasets/. NSL-KDD Dataset [57]: https://www.unb.ca/cic/datasets/nsl.html. KDD Cup 1999 Dataset [56]: https://www.kaggle.com/datasets/galaxyh/kdd-cup-1999-data. All the aforementioned datasets are publicly available as mentioned in the section for data availability and are properly cited in the manuscript in Sect. 4: Benchmark Datasets.
References
Wang, Q., Tai, W., Tang, Y., Ni, M.: Review of the false data injection attack against the cyber-physical power system. IET Cyber Phys. Syst. Theory Appl. 4(2), 101 (2019)
Mo, Y., Kim, T.H.J., Brancik, K., Dickinson, D., Lee, H., Perrig, A., Sinopoli, B.: Cyber-physical security of a smart grid infrastructure. Proc. IEEE 100(1), 195 (2011)
He, H., Yan, J.: Cyber-physical attacks and defences in the smart grid: a survey. IET Cyber-Phys. Syst. Theory Appl. 1(1), 13 (2016)
Vellaithurai, C., Srivastava, A., Zonouz, S., Berthier, R.: CPIndex: cyber-physical vulnerability assessment for power-grid infrastructures. IEEE Trans. Smart Grid 6(2), 566 (2014)
Wang, W., Lu, Z.: Cyber security in the smart grid: survey and challenges. Comput. Netw. 57(5), 1344 (2013)
Genge, B., Kiss, I., Haller, P.: A system dynamics approach for assessing the impact of cyber attacks on critical infrastructures. Int. J. Crit. Infrastruct. Prot. 10, 3 (2015)
Yin, X.C., Liu, Z.G., Nkenyereye, L., Ndibanje, B.: Toward an applied cyber security solution in IoT-based smart grids: an intrusion detection system approach. Sensors 19(22), 4952 (2019)
van der Velde, D., Henze, M., Kathmann, P., Wassermann, E., Andres, M., Bracht, D., Ernst, R., Hallak, G., Klaer, B., Linnartz, P. et al.: Methods for actors in the electric power system to prevent, detect and react to ICT attacks and failures. In: 2020 6th IEEE International Energy Conference (ENERGYCon), pp. 17–22. IEEE (2020)
Tang, Y., Chen, Q., Li, M., Wang, Q., Ni, M., Fu, X.: Challenge and evolution of cyber attacks in cyber physical power system. In: 2016 IEEE PES Asia-Pacific Power and Energy Engineering Conference (APPEEC), pp. 857–862. IEEE (2016)
Sahu, A., Mao, Z., Wlazlo, P., Huang, H., Davis, K., Goulart, A., Zonouz, S.: Multi-source multi-domain data fusion for cyberattack detection in power systems. IEEE Access 9, 119118 (2021)
Pandey, R.K., Misra, M.: Cyber security threats—smart grid infrastructure. In: 2016 National Power Systems Conference (NPSC), pp 1–6. IEEE (2016)
Zhu, B., Joseph, A., Sastry, S.: A taxonomy of cyber attacks on SCADA systems. In: 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, pp. 380–388. IEEE (2011)
Han, C.H., Park, S.T., Lee, S.J.: The enhanced security control model for critical infrastructures with the blocking prioritization process to cyber threats in power system. Int. J. Crit. Infrastruct. Prot. 26, 100312 (2019)
Jarmakiewicz, J., Parobczak, K., Maślanka, K.: Cybersecurity protection for power grid control infrastructures. Int. J. Crit. Infrastruct. Prot. 18, 20 (2017)
Farajzadeh-Zanjani, M., Hallaji, E., Razavi-Far, R., Saif, M., Parvania, M.: Adversarial semi-supervised learning for diagnosing faults and attacks in power grids. IEEE Trans. Smart Grid 12(4), 3468 (2021)
Pan, S., Morris, T., Adhikari, U.: Developing a hybrid intrusion detection system using data mining for power systems. IEEE Trans. Smart Grid 6(6), 3104–3113 (2015)
Stavroulakis, P., Stamp, M.: Handbook of Information and Communication Security. Springer Science & Business Media, Berlin (2010)
Liao, H.J., Lin, C.H.R., Lin, Y.C., Tung, K.Y.: Intrusion detection system: a comprehensive review. J. Netw. Comput. Appl. 36(1), 16–24 (2013)
Fuchsberger, A.: Intrusion detection systems and intrusion prevention systems. Inf. Secur. Tech. Rep. 10(3), 134 (2005)
Karatas, G., Demir, O., Sahingoz, O.K.: Deep learning in intrusion detection systems. In: 2018 International Congress on Big Data, Deep Learning and Fighting Cyber Terrorism (IBIGDELFT), pp. 113–116. IEEE, (2018)
Syrmakesis, A.D., Alcaraz, C., Hatziargyriou, N.D.: Classifying resilience approaches for protecting smart grids against cyber threats. Int. J. Inf. Secur. 21(5), 1189 (2022)
Alimi, O.A., Ouahada, K., Abu-Mahfouz, A.M.: A review of machine learning approaches to power system security and stability. IEEE Access 8, 113512–113531 (2020)
Hink, R.C.B., Beaver, J.M., Buckner, M.A., Morris, T., Adhikari, U., Pan, S.: Machine learning for power system disturbance and cyber-attack discrimination. In: 2014 7th International Symposium on Resilient Control Systems (ISRCS), pp. 1–8. IEEE (2014)
Chan, H., Hammad, E., Kundur, D.: Investigating the impact of intrusion detection system performance on communication latency and power system stability. In: Proceedings of the Workshop on Communications, Computation and Control for Resilient Smart Energy Systems, pp. 1–6 (2016)
Chen, Q., Kholidy, H.A., Abdelwahed, S., Hamilton, J.: Towards realizing a distributed event and intrusion detection system. In: International Conference on Future Network Systems and Security, pp. 70–83. Springer (2017)
Keshk, M., Moustafa, N., Sitnikova, E., Creech, G.: Privacy preservation intrusion detection technique for SCADA systems. In: 2017 Military Communications and Information Systems Conference (MilCIS), pp. 1–6. IEEE (2017)
Min, E., Long, J., Liu, Q., Cui, J., Cai, Z., Ma, J.: Su-ids: A semi-supervised and unsupervised framework for network intrusion detection. In: International Conference on Cloud Computing and Security, pp. 322–334. Springer (2018)
Gómez, Á.L.P., Maimó, L.F., Celdrán, A.H., Clemente, F.J.G., Sarmiento, C.C., Masa, C.J.D.C., Nistal, R.M.: On the generation of anomaly detection datasets in industrial control systems. IEEE Access 7, 177460 (2019)
Haghnegahdar, L., Wang, Y.: A whale optimization algorithm-trained artificial neural network for smart grid cyber intrusion detection. Neural Comput. Appl. 32(13), 9427 (2020)
Yao, H., Fu, D., Zhang, P., Li, M., Liu, Y.: MSML: a novel multilevel semi-supervised machine learning framework for intrusion detection system. IEEE Internet Things J. 6(2), 1949 (2018)
Li, Y., Ji, X., Li, C., Xu, X., Yan, W., Yan, X., Chen, Y., Xu, W.: Cross-domain anomaly detection for power industrial control system. In: 2020 IEEE 10th International Conference on Electronics Information and Emergency Communication (ICEIEC), pp. 383–386. IEEE (2020)
Farrukh, Y.A., Ahmad, Z., Khan, I., Elavarasan, R.M.: A sequential supervised machine learning approach for cyber attack detection in a smart grid system. In: 2021 North American Power Symposium (NAPS), pp. 1–6. IEEE (2021)
Upadhyay, D., Manero, J., Zaman, M., Sampalli, S.: Intrusion detection in SCADA based power grids: Recursive feature elimination model with majority vote ensemble algorithm. IEEE Trans. Netw. Sci. Eng. 8(3), 2559 (2021)
Jiang, J.R., Chen, Y.T.: Industrial control system anomaly detection and classification based on network traffic. IEEE Access 10, 41874 (2022)
Kezunovic, M.: In The Electrical Engineering Handbook, pp. 787–803. Elsevier (2005)
Alimi, O.A., Ouahada, K., Abu-Mahfouz, A.M., Rimer, S., Alimi, K.O.A.: A review of research works on supervised learning algorithms for SCADA intrusion detection and classification. Sustainability 13(17), 9597 (2021)
Upadhyay, D., Sampalli, S.: Scada (supervisory control and data acquisition) systems: vulnerability assessment and security recommendations. Comput. Secur. 89, 101666 (2020)
Cifranic, N., Hallman, R.A., Romero-Mariona, J., Souza, B., Calton, T., Coca, G.: Decepti-SCADA: a cyber deception framework for active defense of networked critical infrastructures. Internet Things 12, 100320 (2020)
Yadav, G., Paul, K.: Architecture and security of SCADA systems: a review. Int. J. Crit. Infrastruct. Prot. 34, 100433 (2021)
Miller, B., Rowe, D.: A survey SCADA of and critical infrastructure incidents. In: Proceedings of the 1st Annual Conference on Research in Information Technology, pp. 51–56 (2012)
Rakas, S.V.B., Stojanović, M.D., Marković-Petrović, J.D.: A review of research work on network-based SCADA intrusion detection systems. IEEE Access 8, 93083 (2020)
Stojanović, M.D., Rakas, S.V.B.: Cyber Security of Industrial Control Systems in the Future Internet Environment. IGI Global, Pennsylvania (2020)
Morris, T.H., Gao, W.: Industrial control system cyber attacks. In: 1st International Symposium for ICS & SCADA Cyber Security Research 2013 (ICS-CSR 2013) 1, pp. 22–29 (2013)
Asri, S., Pranggono, B.: Impact of distributed denial-of-service attack on advanced metering infrastructure. Wireless Pers. Commun. 83(3), 2211 (2015)
Borkar, A., Donode, A., Kumari, A.: A survey on Intrusion Detection System (IDS) and Internal Intrusion Detection and protection system (IIDPS). In: 2017 International Conference on Inventive Computing and Informatics (ICICI), pp. 949–953. IEEE (2017)
Lazarevic, A., Kumar, V., Srivastava, J.: Intrusion detection: a survey. In: Managing cyber threats, pp. 19–78. Springer (2005)
Arya, B., Chandrasekaran, K.: A client-side anti-pharming (CSAP) approach. In: 2016 International Conference on Circuit, Power and Computing Technologies (ICCPCT), pp. 1–6. IEEE (2016)
Sun, J., Qi, G., Zhu, Z.: A sparse neural network based control structure optimization game under dos attacks for des frequency regulation of power grid. Appl. Sci. 9(11), 2217 (2019)
Ashraf, S., Shawon, M.H., Khalid, H.M., Muyeen, S.: Denial-of-service attack on IEC 61850-based substation automation system: A crucial cyber threat towards smart substation pathways. Sensors 21(19), 6415 (2021)
Zargar, S.T., Joshi, J., Tipper, D.: A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Commun. Surv. Tutor. 15(4), 2046 (2013)
Majidi, S.H., Hadayeghparast, S., Karimipour, H.: FDI attack detection using extra trees algorithm and deep learning algorithm-autoencoder in smart grid. Int. J. Crit. Infrastruct. Prot. 37, 100508 (2022)
Pilz, M., Naeini, F.B., Grammont, K., Smagghe, C., Davis, M., Nebel, J.C., Al-Fagih, L., Pfluegel, E.: Security attacks on smart grid scheduling and their defences: a game-theoretic approach. Int. J. Inf. Secur. 19, 427 (2020)
Musleh, A.S., Chen, G., Dong, Z.Y.: A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Trans. Smart Grid 11(3), 2218 (2020). https://doi.org/10.1109/TSG.2019.2949998
Chen, P.Y., Yang, S., McCann, J.A., Lin, J., Yang, X.: Detection of false data injection attacks in smart-grid systems. IEEE Commun. Mag. 53(2), 206 (2015). https://doi.org/10.1109/MCOM.2015.7045410
Ahmed, M., Pathan, A.S.K.: False data injection attack (FDIA): an overview and new metrics for fair evaluation of its countermeasure. Complex Adapt. Syst. Model. 8(1), 1 (2020)
Tavallaee, M., Bagheri, E., Lu, W., Ghorbani, A.A.: A detailed analysis of the KDD CUP 99 data set. In: 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, pp. 1–6 (2009). https://doi.org/10.1109/CISDA.2009.5356528
Revathi, S., Malathi, A.: A detailed analysis on NSL-KDD dataset using various machine learning techniques for intrusion detection. Int. J. Eng. Res. Technol. (IJERT) 2(12), 1848 (2013)
Zhang, Y., Wang, L., Sun, W., Green, R.C., II., Alam, M.: Distributed intrusion detection system in a multi-layer network architecture of smart grids. IEEE Trans. Smart Grid 2(4), 796 (2011)
Poston, H.E.: A brief taxonomy of intrusion detection strategies. In: 2012 IEEE National Aerospace and Electronics Conference (NAECON), pp. 255–263 (2012). https://doi.org/10.1109/NAECON.2012.6531064
Garcia-Teodoro, P., Diaz-Verdejo, J., Maciá-Fernández, G., Vázquez, E.: Anomaly-based network intrusion detection: techniques, systems and challenges. Comput. Secur. 28(1–2), 18 (2009)
Ahmed, C.M., MR, G.R., Mathur, A.P.: Challenges in machine learning based approaches for real-time anomaly detection in industrial control systems: In: Proceedings of the 6th ACM on Cyber-physical System Security Workshop, pp. 23–29 (2020)
Zhu, B., Sastry, S.: SCADA-specific intrusion detection/prevention systems: a survey and taxonomy. In: Proceedings of the 1st workshop on secure control systems (SCS), vol. 11, p. 7 (2010)
Premaratne, U.K., Samarabandu, J., Sidhu, T.S., Beresh, R., Tan, J.C.: An intrusion detection system for iec61850 automated substations. IEEE Trans. Power Deliv. 25(4), 2376 (2010)
Zhang, Y., Wang, J., Chen, B.: Detecting false data injection attacks in smart grids: a semi-supervised deep learning approach. IEEE Trans. Smart Grid 12(1), 623 (2020)
Shi, H., Xie, L., Peng, L.: Detection of false data injection attacks in smart grid based on a new dimensionality-reduction method. Comput. Electr. Eng. 91, 107058 (2021)
Guo, X., Wang, S., Sun, Y., Sun, T., Feng, L., Jin, Z.: Detection of false data injection attack in power grid based on machine learning. In: Advances in Intelligent Information Hiding and Multimedia Signal Processing, pp. 363–371. Springer (2021)
Xiong, X., Hu, S., Sun, D., Hao, S., Li, H., Lin, G.: Detection of false data injection attack in power information physical system based on SVM–GAB algorithm. Energy Rep. 8, 1156 (2022)
Wang, X., Yi, P.: Security framework for wireless communications in smart distribution grid. IEEE Trans. Smart Grid 2(4), 809 (2011). https://doi.org/10.1109/TSG.2011.2167354
Hindy, H., Brosset, D., Bayne, E., Seeam, A., Tachtatzis, C., Atkinson, R., Bellekens, X.: A taxonomy and survey of intrusion detection system design techniques, network threats and datasets (2018)
Hamed, T., Ernst, J.B., Kremer, S.C.: A survey and taxonomy of classifiers of intrusion detection systems, Computer and network security essentials (2018)
Ou, Y.j., Lin, Y., Zhang, Y., Ou, Y.j.: In: 2010 Third International Symposium on Intelligent Information Technology and Security Informatics, pp. 595–598 (2010)
Cho, S.B., Park, H.J.: Efficient anomaly detection by modeling privilege flows using hidden Markov model. Comput. Secur. 22(1), 45 (2003)
Varma, P.R.K., Kumari, V.V., Kumar, S.S.: A survey of feature selection techniques in intrusion detection system: a soft computing perspective. In: Pattnaik, P.K., Rautaray, S.S., Das, H., Nayak, J. (eds.) Progress in Computing, Analytics and Networking, pp. 785–793. Springer Singapore, Singapore (2018)
Aljawarneh, S., Aldwairi, M., Yassein, M.B.: Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J. Comput. Sci. 25, 152–160 (2018)
Grochocki, D., Huh, J.H., Berthier, R., Bobba, R., Sanders, W.H., Cárdenas, A.A., Jetcheva, J.G.: In: 2012 IEEE Third International Conference on Smart Grid Communications, IEEE (2012)
Ullah, I., Mahmoud, Q.H.: In: 2017 IEEE 30th Canadian Conference on Electrical and Computer Engineering (CCECE), pp. 1–5. IEEE (2017)
Funding
This study was part of a project sponsored by Central Power Research Institute (Prof. Sir C V Raman Road, Sadashivanagar P. O., P.B. No. 8066, Bangalore—560 080) undertaken in the Computer Science and Engineering Department, Indian Institute of Technology, Kharagpur.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no competing interests to declare that are relevant to the content of this article.
Ethical standards
The authors hereby confirm that this research survey does not involve any research activities with human participants or animals.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Dasgupta, R., Pramanik, M., Mitra, P. et al. Intrusion detection for power grid: a review. Int. J. Inf. Secur. 23, 1317–1329 (2024). https://doi.org/10.1007/s10207-023-00789-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-023-00789-6