Abstract
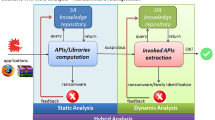
Ransomware attacks have captured news headlines worldwide for the last few years due to their criticality and intensity. Ransomware-as-a-service (RaaS) kits are aiding adversaries to launch such powerful attacks with little to no technical knowledge. Eventually, with the successful progression of ransomware attacks, organizations suffer financial loss, and their proprietary-based sensitive digital assets end up on the dark web for sale. Due to the severity of this situation, security researchers are seen to conduct static and dynamic analysis research for ransomware research. Both analyses have advantages and disadvantages, and prompt ransomware detection is expected to stop the irreversible encryption process. This research proposes a novel static-informed dynamic analysis approach, RWArmor, which includes the knowledge of the already-trained machine learning models based on static features to improve the ransomware detection capabilities during dynamic analysis. The effectiveness of our approach is evaluated by predicting a novel/unknown ransomware between 30 and 120 seconds of its execution. The random forest algorithm is utilized to accomplish this task and tested against 215 active cryptographic Windows ransomware collected between 2014 and 2022. Based on our empirical findings, our method achieves 97.67%, 92.38%, and 86.42% accuracy within 120, 60, and 30 seconds of behavioral logs, respectively.












Similar content being viewed by others
Research Data Policy and Data Availability Statements
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
Notes
IRPs Are Different From Fast I/O: https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/irps-are-different-from-fast-i-o.
https://www.virustotal.com/gui/file/
e3b7d39be5e821b59636d0fe7c2944cc.
References
Connolly, L.Y., Wall, D.S.: The rise of crypto-ransomware in a changing cybercrime landscape: Taxonomising countermeasures. Comput. Secur. 87, 101568 (2019)
Pont, J., Abu Oun, O., Brierley, C., Arief, B., Hernandez-Castro, J.: A roadmap for improving the impact of anti-ransomware research. In: Secure IT Systems: 24th Nordic Conference, NordSec 2019, Aalborg, Denmark, November 18–20, 2019, Proceedings, pp. 137–154. Springer (2019)
Jindal, C., Salls, C., Aghakhani, H., Long, K., Kruegel, C., Vigna, G.: Neurlux: dynamic malware analysis without feature engineering. In: Proceedings of the 35th Annual Computer Security Applications Conference, pp. 444–455 (2019)
Egele, M., Scholte, T., Kirda, E., Kruegel, C.: A survey on automated dynamic malware-analysis techniques and tools. ACM Comput. Surv. 44(2), 1–42 (2008)
Shaukat, S.K., Ribeiro, V.J.: RansomWall: a layered defense system against cryptographic ransomware attacks using machine learning. In: 2018 10th international conference on communication systems & networks (COMSNETS), pp. 356–363. IEEE (2018)
Hasan, M.M., Rahman, M.M.: RansHunt: a support vector machines based ransomware analysis framework with integrated feature set. In: 2017 20th International Conference of Computer and Information Technology (ICCIT), pp. 1–7. IEEE (2017)
Trizna, D.: Quo Vadis: hybrid machine learning meta-model based on contextual and behavioral malware representations. In: Proceedings of the 15th ACM Workshop on Artificial Intelligence and Security, pp. 127–136 (2022)
Ayub, M.A., Sirai, A.: Similarity analysis of ransomware based on portable executable (PE) file metadata. In: 2021 IEEE Symposium Series on Computational Intelligence (SSCI), pp. 1–6. IEEE (2021)
Subedi, K.P., Budhathoki, D.R., Dasgupta, D.: Forensic analysis of ransomware families using static and dynamic analysis. In: 2018 IEEE Security and Privacy Workshops (SPW), pp. 180–185. IEEE (2018)
Poudyal, S., Subedi, K.P., Dasgupta, D.: A framework for analyzing ransomware using machine learning. In: 2018 IEEE Symposium Series on Computational Intelligence (SSCI), pp. 1692–1699. IEEE (2018)
Poudyal, S., Dasgupta, D.: AI-powered ransomware detection framework. In: 2020 IEEE Symposium Series on Computational Intelligence (SSCI), pp. 1154–1161. IEEE (2020)
Poudyal, S., Dasgupta, D., Akhtar, Z., Gupta, K.: A multi-level ransomware detection framework using natural language processing and machine learning. In: 14th International Conference on Malicious and Unwanted Software” MALCON (2019)
Zhang, B., Xiao, W., Xiao, X., Sangaiah, A.K., Zhang, W., Zhang, J.: Ransomware classification using patch-based CNN and self-attention network on embedded N-grams of opcodes. Future Gener. Comput. Syst. 110, 708–720 (2020)
Medhat, M., Gaber, S., Abdelbaki, N.: A new static-based framework for ransomware detection. In: 2018 IEEE 16th International Conference on Dependable, Autonomic and Secure Computing, 16th International Conference on Pervasive Intelligence and Computing, 4th International Conference on Big Data Intelligence and Computing and Cyber Science and Technology Congress (DASC/PiCom/DataCom/CyberSciTech), pp. 710–715. IEEE (2018)
Ahmed, Y.A., Koçer, B., Huda, S., Al-rimy, B.A.S., Hassan, M.M.: A system call refinement-based enhanced Minimum Redundancy Maximum Relevance method for ransomware early detection. J. Netw. Comput. Appl. 167, 102753 (2020)
Al-rimy, B.A.S., Maarof, M.A., Prasetyo, Y.A., Shaid, S.Z.M., Ariffin, A.F.M.: Zero-day aware decision fusion-based model for crypto-ransomware early detection. Int. J. Integr. Eng. (2018). https://doi.org/10.30880/ijie.2018.10.06.011
Lu, T., Du, Y., Wu, J., Bao, Y.: Ransomware detection based on an improved double-layer negative selection algorithm. In: Testbeds and Research Infrastructures for the Development of Networks and Communications: 14th EAI International Conference, TridentCom 2019, Changsha, China, December 7–8, 2019, Proceedings 14, pp. 46–61. Springer (2020)
Sharif, M.I., Lanzi, A., Giffin, J.T., Lee, W.: Impeding malware analysis using conditional code obfuscation. In: NDSS (2008)
Collberg, C., Thomborson, C., Low, D.: A taxonomy of obfuscating transformations. Department of Computer Science, The University of Auckland, New Zealand, Tech. Rep (1997)
Collberg, C., Thomborson, C., Low, D.: Manufacturing cheap, resilient, and stealthy opaque constructs. In: Proceedings of the 25th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages, pp. 184–196 (1998)
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., Kirda, E.: Cutting the gordian knot: a look under the hood of ransomware attacks. In: International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, pp. 3–24. Springer (2015)
Continella, A., Guagnelli, A., Zingaro, G., De Pasquale, G., Barenghi, A., Zanero, S., Maggi, F.: Shieldfs: a self-healing, ransomware-aware filesystem. In: Proceedings of the 32nd Annual Conference on Computer Security Applications, pp. 336–347 (2016)
Kharraz, A., Arshad, S., Mulliner, C., Robertson, W.K., Kirda, E.: Unveil: a large-scale, automated approach to detecting ransomware. In: USENIX Security Symposium, vol. 25. Austin, Texas (2016)
Mehnaz, S., Mudgerikar, A., Bertino, E.: Rwguard: a real-time detection system against cryptographic ransomware. In: Research in Attacks, Intrusions, and Defenses: 21st International Symposium, RAID 2018, Heraklion, Crete, Greece, September 10–12, 2018, Proceedings, pp. 114–136. Springer (2018)
Gómez-Hernández, J.A., Álvarez-González, L., García-Teodoro, P.: R-Locker: thwarting ransomware action through a honeyfile-based approach. Comput. Secur. 73, 389–398 (2018)
Moore, C.: Detecting ransomware with honeypot techniques. In: 2016 Cybersecurity and Cyberforensics Conference (CCC), pp. 77–81. IEEE (2016)
Yuill, J., Zappe, M., Denning, D., Feer, F.: Honeyfiles: deceptive files for intrusion detection. In: Proceedings from the Fifth Annual IEEE SMC Information Assurance Workshop, 2004, pp. 116–122. IEEE (2004)
Bowen, B.M., Hershkop, S., Keromytis, A.D., Stolfo, S.J.: Baiting inside attackers using decoy documents. In: International Conference on Security and Privacy in Communication Systems, pp. 51–70. Springer (2009)
Abdelsalam, M., Gupta, M., Mittal, S.: Artificial intelligence assisted malware analysis. In: Proceedings of the 2021 ACM Workshop on Secure and Trustworthy Cyber-Physical Systems, pp. 75–77 (2021)
McDole, A., Abdelsalam, M., Gupta, M., Mittal, S.: Analyzing CNN based behavioural malware detection techniques on cloud IaaS. In: CLOUD 2020 (2020)
McDole, A., Gupta, M., Abdelsalam, M., Mittal, S., Alazab, M.: Deep learning techniques for behavioural malware analysis in cloud IaaS. In Malware Analysis Using Artificial Intelligence and Deep Learning. Springer (2021)
Kimmell, J.C., Abdelsalam, M., Gupta, M.: Analyzing machine learning approaches for online malware detection in cloud. In: IEEE conference on smart computing (SMARTCOMP) 2021 (2021)
Kimmell, J.C., McDole, A.D., Abdelsalam, M., Gupta, M., Sandhu, R.: Recurrent neural networks based online behavioural malware detection techniques for cloud infrastructure. IEEE Access 9, 68066–68080 (2021)
Scaife, N., Carter, H., Traynor, P., Butler, K.R.: Cryptolock (and drop it): stopping ransomware attacks on user data. In: 2016 IEEE 36th International Conference on Distributed Computing Systems (ICDCS), pp. 303–312. IEEE (2016)
Sgandurra, D., Muñoz-González, L., Mohsen, R., Lupu, E.C.: Automated dynamic analysis of ransomware: benefits, limitations and use for detection. arXiv preprint arXiv:1609.03020 (2016)
Kharraz, A., Kirda, E.: Redemption: real-time protection against ransomware at end-hosts. In: Research in Attacks, Intrusions, and Defenses: 20th International Symposium, RAID 2017, Atlanta, GA, USA, September 18–20, 2017, Proceedings, pp. 98–119. Springer (2017)
Palisse, A., Durand, A., Le Bouder, H., Le Guernic, C., Lanet, J.L.: Data aware defense (DaD): towards a generic and practical ransomware countermeasure. In: Secure IT Systems: 22nd Nordic Conference, NordSec 2017, Tartu, Estonia, November 8–10, 2017, Proceedings 22, pp. 192–208. Springer (2017)
Chen, Z.G., Kang, H.S., Yin, S.N., Kim, S.R.: Automatic ransomware detection and analysis based on dynamic API calls flow graph. In: Proceedings of the International Conference on Research in Adaptive and Convergent Systems, pp. 196–201 (2017)
Daku, H., Zavarsky, P., Malik, Y.: Behavioral-based classification and identification of ransomware variants using machine learning. In: 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), pp. 1560–1564. IEEE (2018)
Homayoun, S., Dehghantanha, A., Ahmadzadeh, M., Hashemi, S., Khayami, R., Choo, K.K.R., Newton, D.E.: DRTHIS: deep ransomware threat hunting and intelligence system at the fog layer. Future Gener. Comput. Syst. 90, 94–104 (2019)
Al-rimy, B.A.S., Maarof, M.A., Shaid, S.Z.M.: Crypto-ransomware early detection model using novel incremental bagging with enhanced semi-random subspace selection. Future Gener. Comput. Syst. 101, 476–491 (2019)
Roy, K.C., Chen, Q.: DeepRan: attention-based BiLSTM and CRF for ransomware early detection and classification. Inf. Syst. Front. 23, 299–315 (2021)
Kok, S., Abdullah, A., Jhanjhi, N.: Early detection of crypto-ransomware using pre-encryption detection algorithm. J. King Saud Univ. Comput. Inf. Sci. 34(5), 1984–1999 (2022)
Tang, F., Ma, B., Li, J., Zhang, F., Su, J., Ma, J.: RansomSpector: an introspection-based approach to detect crypto ransomware. Comput. Secur. 97, 101997 (2020)
Alhawi, O.M., Baldwin, J., Dehghantanha, A.: Leveraging machine learning techniques for windows ransomware network traffic detection. In: Cyber Threat Intelligence, pp. 93–106 (2018)
Moussaileb, R., Cuppens, N., Lanet, J.L., Le Bouder, H.: Ransomware network traffic analysis for pre-encryption alert. In: Foundations and Practice of Security: 12th International Symposium, FPS 2019, Toulouse, France, November 5–7, 2019, Revised Selected Papers 12, pp. 20–38. Springer (2020)
Khammas, B.M.: Ransomware detection using random forest technique. ICT Express 6(4), 325–331 (2020)
Kok, S., Abdullah, A., Jhanjhi, N., Supramaniam, M.: Prevention of crypto-ransomware using a pre-encryption detection algorithm. Computers 8(4), 79 (2019)
Shijo, P., Salim, A.: Integrated static and dynamic analysis for malware detection. Procedia Comput. Sci. 46, 804–811 (2015)
Walker, A., Sengupta, S.: Insights into malware detection via behavioral frequency analysis using machine learning. In: MILCOM 2019-2019 IEEE Military Communications Conference (MILCOM), pp. 1–6. IEEE (2019)
Al-Rimy, B.A.S., Maarof, M.A., Alazab, M., Alsolami, F., Shaid, S.Z.M., Ghaleb, F.A., Al-Hadhrami, T., Ali, A.M.: A pseudo feedback-based annotated TF-IDF technique for dynamic crypto-ransomware pre-encryption boundary delineation and features extraction. IEEE Access 8, 140586 (2020)
Javaheri, D., Hosseinzadeh, M., Rahmani, A.M.: Detection and elimination of spyware and ransomware by intercepting kernel-level system routines. IEEE Access 6, 78321–78332 (2018)
Cohen, A., Nissim, N.: Trusted detection of ransomware in a private cloud using machine learning methods leveraging meta-features from volatile memory. Expert Syst. Appl. 102, 158–178 (2018)
Bekerman, D., Shapira, B., Rokach, L., Bar, A.: Unknown malware detection using network traffic classification. In: 2015 IEEE Conference on Communications and Network Security (CNS), pp. 134–142. IEEE (2015)
Azmoodeh, A., Dehghantanha, A., Conti, M., Choo, K.K.R.: Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient Intell. Hum. Comput. 9, 1141–1152 (2018)
Cusack, G., Michel, O., Keller, E.: Machine learning-based detection of ransomware using SDN. In: Proceedings of the 2018 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, pp. 1–6 (2018)
Aghakhani, H., Gritti, F., Mecca, F., Lindorfer, M., Ortolani, S., Balzarotti, D., Vigna, G., Kruegel, C.: When malware is packin’heat; limits of machine learning classifiers based on static analysis features. In: Network and Distributed Systems Security (NDSS) Symposium 2020 (2020)
Garfinkel, T., Adams, K., Warfield, A., Franklin, J.: Compatibility is not transparency: VMM detection myths and realities. In: HotOS (2007)
Lindorfer, M., Kolbitsch, C., Milani Comparetti, P.: Detecting environment-sensitive malware. In: Recent Advances in Intrusion Detection: 14th International Symposium, RAID 2011, Menlo Park, CA, USA, September 20–21, 2011. Proceedings 14, pp. 338–357. Springer (2011)
Raffetseder, T., Kruegel, C., Kirda, E.: Detecting system emulators. In: Information Security: 10th International Conference, ISC 2007, Valparaíso, Chile, October 9–12, 2007. Proceedings 10, pp. 1–18. Springer (2007)
Rossow, C., Dietrich, C.J., Grier, C., Kreibich, C., Paxson, V., Pohlmann, N., Bos, H., Van Steen, M.: Prudent practices for designing malware experiments: status quo and outlook. In: 2012 IEEE Symposium on Security and Privacy, pp. 65–79. IEEE (2012)
Lee, K., Lee, S.Y., Yim, K.: Machine learning based file entropy analysis for ransomware detection in backup systems. IEEE Access 7, 110205 (2019)
Kim, D.Y., Choi, G.Y., Lee, J.H.: White list-based ransomware real-time detection and prevention for user device protection. In: 2018 IEEE International Conference on Consumer Electronics (ICCE), pp. 1–5. IEEE (2018)
Jung, S., Won, Y.: Ransomware detection method based on context-aware entropy analysis. Soft Comput. 22, 6731–6740 (2018)
Chew, C.J., Kumar, V.: Behaviour Based Ransomware Detection. EasyChair (2019)
May, M.J., Laron, E.: Combating ransomware using content analysis and complex file events. In: 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), pp. 1–5. IEEE (2019)
Hirano, M., Kobayashi, R.: Machine learning based ransomware detection using storage access patterns obtained from live-forensic hypervisor. In: 2019 Sixth International Conference on Internet of Things: Systems, Management and security (IOTSMS), pp. 1–6. IEEE (2019)
Microsoft Docs: Example I/O Request—An Overview—Windows drivers (2017). https://docs.microsoft.com/en-us/windows-hardware/drivers/kernel/example-i-o-request---an-overview
Ayub, M.A., Continella, A., Siraj, A.: An I/O request packet (IRP) driven effective ransomware detection scheme using artificial neural network. In: 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), pp. 319–324. IEEE (2020)
Harang, R., Rudd, E.M.: SOREL-20M: a large scale benchmark dataset for malicious PE detection. arXiv preprint arXiv:2012.07634 (2020)
Abdi, H., Williams, L.J.: Principal component analysis. Wiley Interdiscip. Rev. Comput. Stat. 2(4), 433–459 (2010)
Pedregosa, F., Varoquaux, G., Gramfort, A., Michel, V., Thirion, B., Grisel, O., Blondel, M., Prettenhofer, P., Weiss, R., Dubourg, V., Vanderplas, J., Passos, A., Cournapeau, D., Brucher, M., Perrot, M., Duchesnay, E.: Scikit-learn: machine learning in Python. J. Mach. Learn. Res. 12, 2825–2830 (2011)
Acknowledgements
We thank the anonymous reviewers to review this manuscript and share valuable feedback to further improve its quality. We are grateful to VirusTotal and Any Run for generously giving us Academic Premium Subscription without any cost to use their platforms. We are thankful to Dr. Andrea Continella for providing us with the I/O Request Packet (IRP)-based dataset, published in [22]. We extend our sincere gratitude to Cybersecurity Education, Research & Outreach Center (CEROC) at Tennessee Tech University for supporting this research since its inception.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors certify that they have no affiliations with or involvement in any organization or entity with any financial interest or non-financial interest in the subject matter or materials discussed in this manuscript.
Compliance with Ethical Standards
All authors confirm that accepted principles of ethical and professional conduct have been followed and declare that they have no conflict of interest. Additionally, this article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ayub, M.A., Siraj, A., Filar, B. et al. RWArmor: a static-informed dynamic analysis approach for early detection of cryptographic windows ransomware. Int. J. Inf. Secur. 23, 533–556 (2024). https://doi.org/10.1007/s10207-023-00758-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-023-00758-z