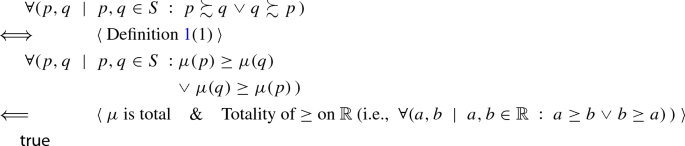Abstract
Information systems and cloud computing infrastructures are frequently exposed to various types of threats. Without detection and prevention mechanisms, the threats can materialize and cause different types of damages that usually lead to significant financial losses. The threats arise from a complex and multifaceted environment. Currently, organizations are struggling to identify the threats to their information assets and assess the overall damage they might inflict to their systems. In order to empower mangers to better plan for shielding their information systems, the paper presents two main contributions. First, a new approach to threat classification that leads to a security assessment model that is systematic, extendable, and modular. Second, a quantitative analysis of information systems based on the model.

Similar content being viewed by others
Notes
The study examines the costs incurred by 314 companies in 16 industry sectors after those companies experienced the loss or theft of protected personal data. The report shows that confidentiality data breaches are caused mainly by malicious or criminal attacks.
References
Aggarwal, C., Hinneburg, A., Keim, D.: On the surprising behavior of distance metrics in high dimensional space. In: International Conference on Database Theory (ICDT), vol 1973, Springer, pp. 420–434 (2001)
Alhabeeb, M., Almuhaideb, A., Le, P., Srinivasan, B.: Information security threats classification pyramid. In: IEEE 24th International conference on Advanced Information Networking and Applications Workshops (WAINA), IEEE Xplore Digital Library, pp 208–213 (2010)
Amini, A., Jamil, N., Ahmad, A., Zaba, M.: Threat modeling approaches for securing cloud computing. J. Appl. Sci. 15(7), 953–967 (2015)
Applegate, S., Stavrou, A.: Towards a cyber conflict taxonomy. In: 5th International Conference on Cyber Conflict, IEEE Xplore Digital Library (2013)
Argyropoulos, N., Angelopoulos, K., Mouratidis, H., Fish, A.: Decision-making in security requirements engineering with constrained goal models. Comput. Secur. 10683, 262–280 (2018)
Avižienis, A., Laprie, JC., Randell, B.: Dependability and its threats: a taxonomy. In: IFIP Congress Topical Sessions, pp. 91–120 (2004)
Baldwin, A., Beres, Y., Duggan, G., Mont, M., Johnson, H., Middup, C., Shiu, S.: Economic methods and decision making by security professionals. In: The Tenth Workshop on the Economics of Information Security (WEIS), Springer, pp 213–238 (2013)
Ben Aissa, A.: Vers une mesure économétrique de la sécurité des systémes informatiques. PhD Thesis, Faculty of Sciences of Tunis, Tunis, Tunisia (2012)
Ben Aissa, A., Abercrombie, R., Sheldon, F., Mili, A.: Quantifying security threats and their potential impact: a case study. Innov. Syst. Softw. Eng. 6(1), 269–281 (2010)
Ben Arfa Rabai, L., Jouini, M., Ben Aissa, A., Mili, A.: A cybersecurity model in cloud computing environments. J. King Saud Univ. Comput. Inf. Sci. 25(1), 63–75 (2013)
Chidambaram, V.: Threat modeling in enterprise architecture integration. In: Enterprise Architecture and Business Competitiveness, vol. 2, No. 4 (2004)
Cloud Security Alliance: The treacherous 12 top threats to cloud computing industry insights. Technical Report, Cloud Security Alliance (2017)
Curphey, M., Scambray, J., Olson, E.: Improving web application security: threats and counter measures. Microsoft Corporation, Sytem Computer Services (2003)
Dyer, J.: Remarks on the analytic hierarchy process. Manag. Sci. 36(3), 249–258 (1990)
EY.: Is cybersecurity about more than protection? Global Information Security Survey 2018–19. Technical Report, EY (2018)
Farahmand, F., Navathe, S., Sharp, G., Enslow, P.: A management perspective on risk of security threats to information systems. Inf. Technol. Manag. Arch. 6(2), 202–225 (2005)
Geric, S., Hutinski, Z.: Information system security threats classifications. J. Inf. Organ. Sci. 1(31), 51–61 (2007)
Howard, M., Leblanc, D.: Writing Secure Code. Microsoft Press, Redmond (2002)
Jouini, M., Ben Arfa Rabai, L., Ben Aissa, A.: Classification of security threats in information systems. In: ANT/SEIT 2014, Procedia Computer Science, vol. 32, pp. 489–496 (2014)
Jouini, M., Ben Arfa Rabai, L., Khedri, R.: A multidimensional approach towards a quantitative assessment of security threats. In: ANT/SEIT 2015, Elsevier, Procedia Computer Science, vol. 52, pp. 507–514 (2015)
Jouini, M., Ben Arfa Rabai, L., Khedri, R.: Software requirements for an ultra large scale system to compute multi dimension mean failure cost. In: PDCAT 2018, Springer, pp. 361–370 (2018)
Kruchten, P.: Architectural blueprints—the “4+1” view model of software architecture. IEEE Softw. 12(6), 42–50 (1995)
Li, Y., Zhou, F., Qin, Y., Lin, M., Xu, Z.: Integrity-verifiable conjunctive keyword searchable encryption in cloud storage. Int. J. Inf. Secur. 17(5), 549–568 (2018)
Lia, J., Lia, M., Wua, D., Song, H.: An integrated risk measurement and optimization model for trustworthy software process management. Inf. Sci. 15(191), 47–60 (2012)
Mavoungou, S., Kaddoum, G., Taha, M., Matar, G.: Survey on threats and attacks on mobile networks. In: Security in Wireless Communications and Networking, IEEE Xplore Digital Library, pp. 4543–4572 (2016)
Mell, P., Grance, T.: The nist definition of cloud computing. Technical Report, National Institute of Standards and Technology (2011)
Munir, R., Disso, J., Awan, I., Mufti, M.: Quantitative enterprise network security risk assessment, broadband and wireless computing. In: BWCCA, pp. 437–442 (2013)
Ou, X., Singhal, A.: Quantitative Security Risk Assessment of Enterprise Networks. SpringerBriefs in Computer Sciencee, Springer (2011)
Ponemon Institute: 2014 cost of data breach study: Global analysis. Technical Report, Ponemon Institute LLC (2014)
Ponemon Institute: Cost of a data breach report 2019. Technical Report, Ponemon Institute (2019)
Pw, C.: Managing cyber risks in an interconnected world: Key finding from the global state of information security survey 2015. Technical Report, PwC (2015)
Pw, C.: Strengthening digital society against cyber shocks: key findings from the global state of information security survey 2018. Technical Report, PwC (2018)
Rashid, M., Mufti, M., Awan, I., Hu, YF., Disso, J.: Detection, mitigation and quantitative security risk assessment of invisible attacks at enterprise network. In: FiCloud, pp. 256–263 (2015)
Ross, R.: Guide for conducting risk assessments. NIST SP-800-30rev1 (2012)
Rudin, C.: Ranking with a p-norm push. In: International Conference on Computational Learning Theory (COLT), vol 4005, pp 589–604, Springer (2006)
Saaty, T.: Decision making with the analytic hierarchy process. Int. J. Serv. Sci. 1(1), 83–98 (2008)
Schlette, D., Bohm, F., Caselli, M., Pernul, G.: Measuring and visualizing cyber threat intelligence quality. Int. J. Inf. Secur. 19(2), 1–18 (2020)
Sommestad, T., Ekstedt, M., Holm, H.: The cyber security modeling language: a tool for assessing the vulnerability of enterprise system architectures. IEEE Syst. J. 7(7), 363–373 (2013)
Subashini, S., Kavitha, V.: A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 34(1), 1–11 (2011)
Swiderski, F., Snyder, W.: Threat Modeling. Microsoft Press, Redmond (2004)
Symantec.: Internet security threat report (ISTR). Technical Report, Symantec (2016)
Technical white paper.: Cloud infrastructure architecture case study vmware vsphere 5.0 and vmware vshield app 5.0. Technical Report 1.0, Technical white paper (2012)
Toreini, E., Shahandashti, S., Mehrnezhad, M., Hao, F.: Domtegrity: ensuring web page integrity against malicious browser extensions. Int. J. Inf. Secur. 18(6), 659–679 (2019)
van Staalduinen, M., Khan, F., Gadag, V., Reniers, G.: Functional quantitative security risk analysis (qsra) to assist in protecting critical process infrastructure. Reliab. Eng. Syst. Saf. 157, 23–34 (2017)
Varia, J.: Architecting for the cloud: Best practices. Technical Report, Amazon.com (2011)
von Solms, R., van Niekerk, J.: From information security to cyber security. Comput. Secur. 38, 97–102 (2013)
Wangen, G., Hallstensen, C., Snekkenes, E.: A framework for estimating information security risk assessment method completeness. Int. J. Inf. Secur. 17(6), 681–699 (2018)
Zio, E., Sanseverino, C.: Security assessment in complex networks exposed to terrorist hazard: a simulation approach. IJCIS 4(1/2), 80–95 (2008)
Funding
This study was funded by Natural Sciences and Engineering Research Council of Canada—NSERC—(CA) (RGPIN-6115-2014).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
This paper presents a revised and extended version of the material presented in [19].
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Primary threat classification catalog
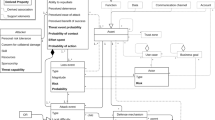
In this “Appendix,” we developed a catalog (see Table 12) including the primaries perspectives and their dimensions to help users in the assessment of the multiple facets of the problem. The proposed catalog can be extended as other dimensions may be relevant to the security of the system.
Ordinal scale measurement proof
We show that the three properties of Definition 1 are satisfied.
-
1.
Proving that
 .
. 
-
2.
Proving that

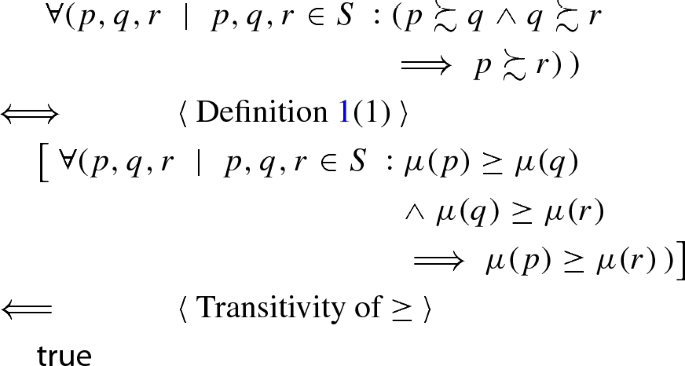
-
3.
Proving that
 .
. 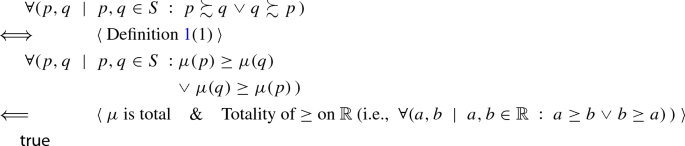
Since \(\mu \) is total, for every site we have a score that is a real number. Then every two sites are comparable through their scores.
Multidimension mean failure cost (\(M^{2}\)FC) with regard to components dimension
We deal in this “Appendix” with architectural components dimension. We will show the impact of the dimension Components on the values of the multidimension mean failure cost (\(M^{2}\)FC). In fact, this “Appendix” shows the computation details of the \(M^{2}\)FC.
We generate in this step the matrices giving Probabilities of Failure in meeting Requirements \(\text{ PFR}_{s}\) presented in Tables 13 and 14.
The list of threats relating to the three locations: Site1. Site2, and Site3 are illustrated respectively in the \(C_{s}\) matrices presented in Tables 15, 16, and 17.
The threats vector for three sites is given in Table 18.
Rights and permissions
About this article
Cite this article
Jouini, M., Ben Arfa Rabai, L. & Khedri, R. A quantitative assessment of security risks based on a multifaceted classification approach. Int. J. Inf. Secur. 20, 493–510 (2021). https://doi.org/10.1007/s10207-020-00515-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-020-00515-6




 .
. 

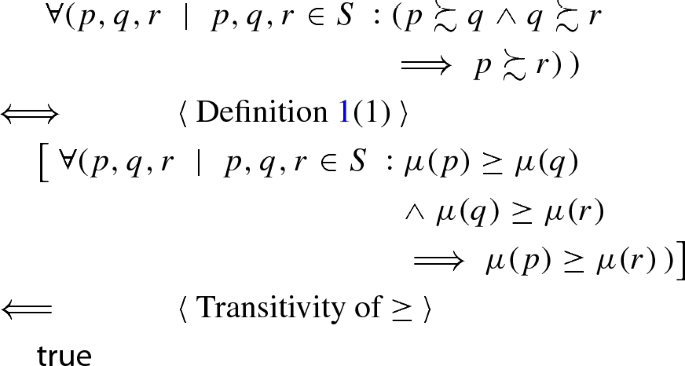
 .
.