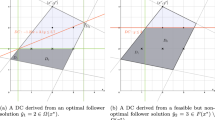
Abstract
Cut generation and lifting are key components for the performance of state-of-the-art mathematical programming solvers. This work proposes a new general cut-and-lift procedure that exploits the combinatorial structure of 0–1 problems via a binary decision diagram (BDD) encoding of their constraints. We present a general framework that can be applied to a wide range of binary optimization problems and show its applicability for second-order conic inequalities. We identify conditions for which our lifted inequalities are facet-defining and derive a new BDD-based cut generation linear program. Such a model serves as a basis for a max-flow combinatorial algorithm over the BDD that can be applied to derive valid cuts more efficiently. Our numerical results show encouraging performance when incorporated into a state-of-the-art mathematical programming solver, significantly reducing the root node gap, increasing the number of problems solved, and reducing the run-time by a factor of three on average.



Similar content being viewed by others
Notes
The code is available at https://github.com/MargaritaCastro/dd-cut-and-lift.
Numerical testing suggested that this was the best strategy across all techniques.
Numerical testing suggested that \(\texttt {CPLEX}\) performs better on the problem sets when Presolve is deactivated.
References
Ahuja, R.K., Magnanti, T.L., Orlin, J.B.: Network Flows: Theory, Algorithms, and Applications. Prentice-Hall Inc, Hoboken (1993)
Andersen, H.R., Hadzic, T., Hooker, J.N., Tiedemann, P.: A constraint store based on multivalued decision diagrams. In: International Conference on Principles and Practice of Constraint Programming–CP 2007, pp. 118–132. Springer (2007)
Atamtürk, A., Bhardwaj, A.: Network design with probabilistic capacities. Networks 71(1), 16–30 (2018)
Atamtürk, A., Muller, L.F., Pisinger, D.: Separation and extension of cover inequalities for conic quadratic knapsack constraints with generalized upper bounds. INFORMS J. Comput. 25(3), 420–431 (2013)
Atamtürk, A., Narayanan, V.: The submodular knapsack polytope. Discret. Optim. 6(4), 333–344 (2009)
Atamtürk, A., Narayanan, V.: Conic mixed-integer rounding cuts. Math. Program. 122(1), 1–20 (2010)
Balas, E.: Facets of the knapsack polytope. Math. Program. 8(1), 146–164 (1975)
Balas, E.: Disjunctive Programming. Springer, Berlin (2018)
Balas, E., Ceria, S., Cornuéjols, G.: A lift-and-project cutting plane algorithm for mixed 0–1 programs. Math. Program. 58(1–3), 295–324 (1993)
Balas, E., Ceria, S., Cornuéjols, G.: Mixed 0–1 programming by lift-and-project in a branch-and-cut framework. Manag. Sci. 42(9), 1229–1246 (1996)
Becker, B., Behle, M., Eisenbrand, F., Wimmer, R.: BDDs in a branch and cut framework. In: International Workshop on Experimental and Efficient Algorithms, pp. 452–463. Springer, Berlin (2005)
Behle, M.: Binary decision diagrams and integer programming. Ph.D. Thesis (2007)
Bergman, D., Cardonha, C., Mehrani, S.: Binary decision diagrams for bin packing with minimum color fragmentation. In: International Conference on Integration of Constraint Programming, Artificial Intelligence, and Operations Research–CPAIOR 2019, pp. 57–66. Springer, Berlin (2019)
Bergman, D., Cire, A.A.: Discrete nonlinear optimization by state-space decompositions. Manag. Sci. 64(10), 4700–4720 (2018)
Bergman, D., Cire, A.A., van Hoeve, W.J., Hooker, J.N.: Variable ordering for the application of BDDs to the maximum independent set problem. In: International Conference on Integration of Constraint Programming, Artificial Intelligence, and Operations Research–CPAIOR 2012, pp. 34–49. Springer, Berlin (2012)
Bergman, D., Cire, A.A., van Hoeve, W.J., Hooker, J.N.: Discrete optimization with decision diagrams. INFORMS J. Comput. 28(1), 47–66 (2016)
Bergman, D., Lozano, L.: Decision diagram decomposition for quadratically constrained binary optimization. Optimization Online e-prints (2018)
Bhardwaj, A.: Binary conic quadratic knapsacks. Ph.D. thesis, UC Berkeley (2015)
Bixby, R.E., Fenelon, M., Gu, Z., Rothberg, E., Wunderling, R.: Mixed-integer programming: a progress report. In: The Sharpest Cut: The Impact of Manfred Padberg and His Work, pp. 309–325. SIAM (2004)
Bryant, R.E.: Graph-based algorithms for boolean function manipulation. IEEE Trans. Comput. 100(8), 677–691 (1986)
Castro, M.P., Cire, A.A., Beck, J.C.: An MDD-based Lagrangian approach to the multicommodity pickup-and-delivery tsp. INFORMS J. Comput. 32(2), 263–278 (2019)
Castro, M.P., Piacentini, C., Cire, A.A., Beck, J.C.: Relaxed BDDs: an admissible heuristic for delete-free planning based on a discrete relaxation. In: Proceedings of the International Conference on Automated Planning and Scheduling, pp. 77–85 (2019)
Cire, A.A., van Hoeve, W.J.: Multivalued decision diagrams for sequencing problems. Oper. Res. 61(6), 1411–1428 (2013)
Cohen, M.C., Keller, P.W., Mirrokni, V., Zadimoghaddam, M.: Overcommitment in cloud services: bin packing with chance constraints. Manag. Sci. 65(7), 3255–3271 (2019)
Davarnia, D., van Hoeve, W.J.: Outer approximation for integer nonlinear programs via decision diagrams. Math. Program. 187, 111–150 (2020)
Gomory, R.E.: Some polyhedra related to combinatorial problems. Linear Algebra Appl. 2(4), 451–558 (1969)
Gu, Z., Nemhauser, G.L., Savelsbergh, M.W.: Lifted cover inequalities for 0–1 integer programs: Computation. INFORMS J. Comput. 10(4), 427–437 (1998)
Gu, Z., Nemhauser, G.L., Savelsbergh, M.W.: Lifted cover inequalities for 0–1 integer programs: Complexity. INFORMS J. Comput. 11(1), 117–123 (1999)
Gurobi Optimization, L.: Gurobi optimizer reference manual (2020)
Hammer, P.L., Johnson, E.L., Peled, U.N.: Facet of regular 0–1 polytopes. Math. Program. 8(1), 179–206 (1975)
Hoda, S., Van Hoeve, W.J., Hooker, J.N.: A systematic approach to MDD-based constraint programming. In: International Conference on Principles and Practice of Constraint Programming–CP 2010, pp. 266–280. Springer, Berlin (2010)
Hooker, J.N.: Job sequencing bounds from decision diagrams. In: International Conference on Principles and Practice of Constraint Programming–CP 2017, pp. 565–578. Springer, Berlin (2017)
IBM: ILOG CPLEX Studio 12.9 Manual (2019)
Joung, S., Park, S.: Lifting of probabilistic cover inequalities. Oper. Res. Lett. 45(5), 513–518 (2017)
Kılınç-Karzan, F.: On minimal valid inequalities for mixed integer conic programs. Math. Oper. Res. 41(2), 477–510 (2016)
Kılınç-Karzan, F., Yıldız, S.: Two-term disjunctions on the second-order cone. Math. Program. 154(1–2), 463–491 (2015)
Kinable, J., Cire, A.A., van Hoeve, W.J.: Hybrid optimization methods for time-dependent sequencing problems. Eur. J. Oper. Res. 259(3), 887–897 (2017)
Lobo, M.S., Vandenberghe, L., Boyd, S., Lebret, H.: Applications of second-order cone programming. Linear Algebra Appl. 284(1–3), 193–228 (1998)
Lodi, A.: Mixed integer programming computation. In: 50 Years of Integer Programming 1958–2008, pp. 619–645. Springer, Berlin (2010)
Lodi, A., Tanneau, M., Vielma, J.P.: Disjunctive cuts for mixed-integer conic optimization. arXiv preprint arXiv:1912.03166 (2019)
Louveaux, Q., Wolsey, L.A.: Lifting, superadditivity, mixed integer rounding and single node flow sets revisited. Q. J. Belg. Fr. Ital. Oper. Res. Soc. 1(3), 173–207 (2003)
Lozano, L., Smith, J.C.: A binary decision diagram based algorithm for solving a class of binary two-stage stochastic programs. Math. Program. 1–24 (2018)
Modaresi, S., Kılınç, M.R., Vielma, J.P.: Split cuts and extended formulations for mixed integer conic quadratic programming. Oper. Res. Lett. 43(1), 10–15 (2015)
Nemhauser, G.L., Wolsey, L.A.: Integer and Combinatorial Optimization. Wiley-Interscience, New York (1988)
Padberg, M.W.: On the facial structure of set packing polyhedra. Math. Program. 5(1), 199–215 (1973)
Padberg, M.W.: A note on zero-one programming. Oper. Res. 23(4), 833–837 (1975)
Perregaard, M., Balas, E.: Generating cuts from multiple-term disjunctions. In: International Conference on Integer Programming and Combinatorial Optimization, pp. 348–360. Springer, Berlin (2001)
Raghunathan, A.U., Bergman, D., Hooker, J.N., Serra, T., Kobori, S.: Seamless multimodal transportation scheduling. arXiv preprint arXiv:1807.09676 (2018)
Santana, A., Dey, S.S.: Some cut-generating functions for second-order conic sets. Discret. Optim. 24, 51–65 (2017)
Şen, A., Atamtürk, A., Kaminsky, P.: A conic integer optimization approach to the constrained assortment problem under the mixed multinomial logit model. Oper. Res. 66(4), 994–1003 (2018)
Stubbs, R.A., Mehrotra, S.: A branch-and-cut method for 0–1 mixed convex programming. Math. Program. 86(3), 515–532 (1999)
Tjandraatmadja, C., van Hoeve, W.J.: Target cuts from relaxed decision diagrams. INFORMS J. Comput. 31(2), 285–301 (2019)
van den Bogaerdt, P., de Weerdt, M.: Multi-machine scheduling lower bounds using decision diagrams. Oper. Res. Lett. 46(6), 616–621 (2018)
van den Bogaerdt, P., de Weerdt, M.: Lower bounds for uniform machine scheduling using decision diagrams. In: International Conference on Integration of Constraint Programming, Artificial Intelligence, and Operations Research–CPAIOR 2019, pp. 565–580. Springer, Berlin (2019)
Van de Panne, C., Popp, W.: Minimum-cost cattle feed under probabilistic protein constraints. Manag. Sci. 9(3), 405–430 (1963)
Vielma, J.P., Ahmed, S., Nemhauser, G.L.: A lifted linear programming branch-and-bound algorithm for mixed-integer conic quadratic programs. INFORMS J. Comput. 20(3), 438–450 (2008)
Vielma, J.P., Dunning, I., Huchette, J., Lubin, M.: Extended formulations in mixed integer conic quadratic programming. Math. Program. Comput. 9(3), 369–418 (2017)
Wolsey, L.A.: Technical note–facets and strong valid inequalities for integer programs. Oper. Res. 24(2), 367–372 (1976). https://doi.org/10.1287/opre.24.2.367
Wolsey, L.A., Nemhauser, G.L.: Integer and Combinatorial Optimization, vol. 55. Wiley, New York (1999)
Zemel, E.: Easily computable facets of the knapsack polytope. Math. Oper. Res. 14(4), 760–764 (1989)
Acknowledgements
We thank the editors and reviewers whose valuable feedback helped improve the paper. Funding was provided by Agencia Nacional de Investigación y Desarrollo de Chile (Becas Chile) and the Natural Sciences and Engineering Research Council of Canada (Grant Nos. RGPIN-2015-05072, RGPIN-2015-04152, RGPIN-2020-06054, RGPIN-2020-04039).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Relaxed BDD construction procedure for second-order cones
We now present the relaxed BDD construction procedure for SOC inequalities based on the RSOC model. The construction algorithm is analogous for the case of SOC knapsack constraints and the RSOC-K model.
The state information at the core of our BDD construction algorithm is based on recursive model RSOC. This information is stored in each node of the BDD and used to identify infeasible assignments and decide how to widen the BDD (i.e., split nodes). Our state information keeps track of each of the \(l+1\) linear components in inequality (14), i.e., \(\varvec{a}^\top \varvec{x}\) and \(\varvec{d}_k^\top \varvec{x}- h_k\) for each \(k \in \{1,\ldots ,l\}\). Thus, each node \(u \in {\mathcal {N}}_i\) has two \(l+1\) dimensional vectors for top-down information, \(Q^{\downarrow \mathsf {min}}(u)\) and \(Q^{\downarrow \mathsf {max}}(u)\), that approximate the linear components considering the partial assignments from \({\mathbf {r}}\) to u. We set the top-down state information at the root node as \(Q^{\downarrow \mathsf {min}}_0({\mathbf {r}}):= Q^{\downarrow \mathsf {max}}_0({\mathbf {r}}):= 0\) and \(Q^{\downarrow \mathsf {min}}_k({\mathbf {r}}):= Q^{\downarrow \mathsf {max}}_k({\mathbf {r}}):= -h_k\) for all \(k \in \{1,\ldots ,l\}\). Then, for any \(u \in {\mathcal {N}}_i\), \(i \in \{2,\ldots ,n\}\), and \(k \in \{1,\ldots , l\}\) we update the states as:
Similarly, we use two \(l+1\) dimensional vectors, \(Q^{\uparrow \mathsf {min}} (u)\) and \(Q^{\uparrow \mathsf {max}}(u)\), for our bottom-up state information for each node \(u \in {\mathcal {N}}\). The information is initialized at the terminal node as \(Q^{\uparrow \mathsf {min}} _0({\mathbf {t}} ):= Q^{\uparrow \mathsf {max}}_0({\mathbf {t}} ):= 0\) and \(Q^{\uparrow \mathsf {min}} _k({\mathbf {t}} ):= Q^{\uparrow \mathsf {max}}_k({\mathbf {t}} ):= 0\) for all \(k \in \{1,\ldots ,l\}\). Then, for any \(u \in {\mathcal {N}}_i\), \(i \in \{1,\ldots ,n-1\}\), and \(k \in \{1,\ldots , l\}\), we have:
For each node \(u \in {\mathcal {N}}\), the state information under and over approximates the value of the linear components of (14) for all \({\mathbf {r}}-u\) paths (i.e., top-down information) and for all \(u-{\mathbf {t}} \) paths (i.e., bottom-up information). We use the state information to identify if an arc corresponds to an infeasible assignment, i.e., all paths traversing it correspond to infeasible solutions of (14). In particular, we can remove an arc \(a=(u,u')\in {\mathcal {A}}_i\) if the following condition holds:
where \(g_k(a)\) for \(k \in \{1,\ldots , l\}\) is given by:
Notice that \(g_k(a)\) under approximates \((\varvec{d}_k^\top \varvec{x}-d_k)^2\) for all paths traversing arc \(a\in {\mathcal {A}}\), and so the left-hand side (LHS) of (18) under approximates the LHS of (14) for all paths traversing arc \(a\in {\mathcal {A}}_i\). Then, all paths traversing an arc a that satisfy (18) correspond to invalid assignments for (14).
If \(Q^{\downarrow \mathsf {max}}_k(u) = Q^{\downarrow \mathsf {min}}_k(u)\) for all nodes \(u \in {\mathcal {N}}\), we recover the exact BDD based on the recursive model RSOC and condition (18) is equivalent to (15d). Thus, our splitting procedure tries to achieve this property by selecting nodes u with \(Q^{\downarrow \mathsf {max}}_k(u) - Q^{\downarrow \mathsf {min}}_k(u) \ge \delta \) (\(\delta > 0\)) for some \(k \in \{0,\ldots ,l\}\) and then split it into two new nodes, \(u'\) and \(u''\), so \(Q^{\downarrow \mathsf {max}}_k(u') - Q^{\downarrow \mathsf {min}}_k(u')<\delta \) and \(Q^{\downarrow \mathsf {max}}_k(u'') - Q^{\downarrow \mathsf {min}}_k(u'')<\delta \). The splitting procedure then duplicates the outgoing arcs of u and assigns them to both \(u'\) and \(u''\) to keep the same set of paths in \({\mathcal {B}}\).

Our construction procedure creates a relaxed BDD \({\mathcal {B}}=({\mathcal {N}},{\mathcal {A}})\) by limiting its width \(w({\mathcal {B}})\) by a positive value \({\mathcal {W}}\), where \(w({\mathcal {B}}):=\max _{i\in I}\{|{\mathcal {N}}_i|\}\) represents the maximum number of nodes in each layer. The complete BDD construction procedure is shown in Algorithm 2. The algorithm starts creating a width-one BDD for the SOC constraint (line 2) and then updates the bottom-up information for all the nodes (line 4). During the top-down pass through the BDD (lines 5–9), the procedure updates the top-down information of layer \({\mathcal {N}}_i\), splits the nodes until we reach the width limit \({\mathcal {W}}\), and filters the emanating arcs of \({\mathcal {N}}_i\). The algorithm then checks if the BDD has been updated (line 3) and repeats the bottom-up and top-down iterations until the BDD cannot be updated any more. Lastly, we reduce the BDD (line 10) following the standard procedure in the literature [20].
The resulting BDD starts with all possible variable assignments (i.e., a width-one BDD) and removes arcs using condition (18). Thus, the procedure is guaranteed to construct a relaxed BDD for a SOC constraint. Notice that for a big enough \({\mathcal {W}}\), the procedure will return an exact BDD.
Example 5
Consider the following binary set defined by an SOC inequality \(X= \{\varvec{x}\in \{0,1\}^3: 3x_1+x_2+x_3 + \sqrt{ (x_1+x_2+2x_3)^2 + (x_1+3x_2-x_3+3)^2 } \le 8 \}\). Figure 4 depicts some of the steps to construct an exact BDD for X. The left most diagram corresponds to a width-one BDD for this problem. The top-down state information in the root node is \(( (Q^{\downarrow \mathsf {min}}_0({\mathbf {r}}), Q^{\downarrow \mathsf {max}}_0({\mathbf {r}})),\;(Q^{\downarrow \mathsf {min}}_1({\mathbf {r}}), Q^{\downarrow \mathsf {max}}_1({\mathbf {r}})),\) \( (Q^{\downarrow \mathsf {min}}_2({\mathbf {r}}), Q^{\downarrow \mathsf {max}}_2({\mathbf {r}})) )= ( (0,0),\; (0,0),\; (3,3) )\), while for node \(u_1\) is \(( (0,3), \; (0,1),\; (3,4)) \).
The middle BDD illustrates the resulting BDD after splitting node \(u_1\). The resulting nodes, \(u_1'\) and \(u_1''\), have top-down state information \( ( (0,0),\; (0,0),\; (3,3) )\) and \( ( (3,3),\; (1,1),\) (4, 4) ), respectively. In addition, the gray arc from \(u_1''\) to \(u_2\) corresponds to an invalid assignment: the bottom-up information of \(u_2\) is \( ( (0,1),\; (0,2),\; (-1,0) )\), thus, (18) evaluates to \(10.3 > 8\).
BDD construction procedure for set X defined in Example 5. The figure depicts a width-one BDD (left), a BDD after the splitting and filtering procedure over \({\mathcal {N}}_2\) (middle), and the resulting exact reduced BDD (right)
Experiments comparing different BDD widths
Table 4 presents the average performance for \(\texttt {CPLEX}\) and our four alternatives (i.e., \(\texttt {B-Flow}\), \(\texttt {B-Flow+L}\), \(\texttt {B-Gen}\), and \(\texttt {B-Gen+L}\)) with three different maximum width values, \({\mathcal {W}}\in \{2000,3000,4000\}\), over the SOC-CC instances. The table shows the number of instances solved, average root gap, and average final gap for all techniques. Our four alternatives with \({\mathcal {W}}\in \{2000,3000,4000\}\) each outperform \(\texttt {CPLEX}\). \({\mathcal {W}}=4000\) achieves the best overall performance across the four combinatorial cut-and-lift alternatives. Similarly, \({\mathcal {W}}=4000\) achieves the best or comparable performance across the five BDD approaches over the SOC-K instances (right).
Similarly, Table 5 presents the average performance over the SOC-K instances for \(\texttt {CPLEX}\), our four alternatives (i.e., \(\texttt {B-Flow}\), \(\texttt {B-Flow+L}\), \(\texttt {B-Gen}\), and \(\texttt {B-Gen+L}\)) with three different maximum width values, \({\mathcal {W}}\in \{2000,3000,4000\}\). Overall, \({\mathcal {W}}=4000\) achieves the best or comparable performance across the five BDD approaches. Bold numbers in Tables 4 and 5 correspond to the largest values in column “#Solve” and the smallest values in the other columns.
We note that these three BDD widths achieve competitive results with respect to \(\texttt {CPLEX}\) in our dataset. However, problems with more variables (i.e., \(n > 125\)) would probably required a larger width to create a tight BDD relaxation and, thus, strong cuts.
Average performance comparison for Knapsack chance constraints
We now present additional results for the SOC-K dataset. As in Figs. 3, 5 illustrate the performance of each algorithm for the SOC-K dataset. We see a clear dominance of \(\texttt {B-Gen+L}\), \(\texttt {B-Target}\), and \(\texttt {B-Ta+Fl+L}\) and also the positive impact of our combinatorial lifting in instances solved and gap reduction.
The following tables show average results for each parameter configuration over the SOC-CC benchmark. We present results for our four variants (i.e., \(\texttt {B-Flow}\), \(\texttt {B-Flow+L}\), \(\texttt {B-Gen}\), and \(\texttt {B-Gen+L}\)), cover cut variants (i.e., \(\texttt {Cover}\), \(\texttt {CoverLift}\), and \(\texttt {Cover+L}\)), \(\texttt {CPLEX}\), and best performing BDD-based cuts (i.e., \(\texttt {B-Target}\) and \(\texttt {B-Ta+Fl+L}\)). All techniques add cuts only at the root node of the tree search. Tables 6, 7, and 8 show the number of instances solved, average root gap, and average final gap for each n, m, and \(\varOmega \) combination with \({\mathcal {W}}=4000\), respectively. Similarly, Tables 9 and 10 show the average number of nodes in the branch-and-bound search and the average run time for the instances that all techniques solved to optimality. Bold numbers in Tables 6, 7, 8, 9, and 10 correspond to the largest values in column “#Solve” and the smallest values in the other columns.
Average performance comparison for general chance constraints
We now present additional results for the SOC-CC dataset. Figure 6 shows two plots comparing the root gap of \(\texttt {B-Gen+L}\) and \(\texttt {CPLEX}\) for the SOC-CC instances and different values of \(\varOmega \) and t. In each plot, an (x, y) point represents the root gap for an instance given by the x-axis and the y-axis technique, respectively. Overall, we can see that \(\texttt {B-Gen+L}\) achieves a smaller or equal root gap to \(\texttt {CPLEX}\), however, the difference is considerably larger when \(\varOmega \ge 3\) and \(t=0.1\).
The problems become more challenging with a larger \(\varOmega \) (i.e., a predominant quadratic term) due to a weak SOC relaxation and linearization. Thus, our procedure can potentially generate stronger cuts than \(\texttt {CPLEX}\). In fact, the left plot in Fig. 6 shows all instances with \(\varOmega =1\) close to the diagonal, while problems with \(\varOmega \in \{3,5\}\) have larger gap reductions. Lastly, the right plot of Fig. 6 shows that \(\texttt {B-Gen+L}\) has significantly smaller gaps than \(\texttt {CPLEX}\) over instances with a small t (i.e., small solution sets). Our relaxed BDDs are close to exact BDDs in these cases, thus, making our cuts more effective.
The following tables show average results for each parameter configuration over the SOC-CC benchmark. We present results for our four variants (i.e., \(\texttt {B-Flow}\), \(\texttt {B-Flow+L}\), \(\texttt {B-Gen}\), and \(\texttt {B-Gen+L}\)), \(\texttt {CPLEX}\), and best performing BDD-based cuts (i.e., \(\texttt {B-Target}\) and \(\texttt {B-Ta+Fl+L}\)). All techniques add cuts only at the root node of the tree search. Tables 11, 12, and 13 show the number of instances solved, average root gap, and average final gap for each n, m, \(\varOmega \), and t combination, with \({\mathcal {W}}=4000\). Similarly, Tables 14 and 15 show the average number of nodes in the branch-and-bound search and the average run time for the instances that all techniques solved to optimality. Bold numbers in Tables 11, 12, 13, 14, and 15 correspond to the largest values in column “#Solve” and the smallest values in the other columns.
We note that in most instances the BDD cut algorithms have better performance than \(\texttt {CPLEX}\). However, \(\texttt {CPLEX}\) is competitive when \(t=0.3\) and \(\varOmega = 1\), as expected from the behavior observed in Fig. 6. We also note that \(\texttt {CPLEX}\) has similar performance to the BDD techniques when \(n=125\), which suggest that a tighter BDD relaxation (i.e., bigger BDD width) might be needed for larger problem instances.
Rights and permissions
About this article
Cite this article
Castro, M.P., Cire, A.A. & Beck, J.C. A combinatorial cut-and-lift procedure with an application to 0–1 second-order conic programming. Math. Program. 196, 115–171 (2022). https://doi.org/10.1007/s10107-021-01699-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10107-021-01699-y