Abstract
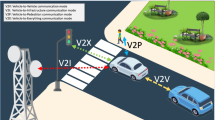
Vehicular ad hoc networks (VANETs) refer to ad hoc networks where many vehicles and other devices connect to wireless communications and exchange their information. The combination of VANETs in a heterogeneous Internet of Things (IoT) allows vehicles belonging to different cryptosystems to communicate with each other. An essential purpose of the VANET is to implement Vehicle-to-Roadside units (V2R) and Vehicle-to-Vehicle (V2V) communications over a reliable telecommunication channel. Therefore, authentication and privacy are the prime goals of a secure connection. This paper proposes a practical heterogeneous signcryption system for vehicular communication (PHSC-VC) with a pairing free to make V2V communication in VANETs more secure. In PHSC-VC, a vehicle registered in a Certificateless Cryptosystem (CLC) environment can exchange its information with another vehicle registered in a Public-Key Infrastructure (PKI) environment. The recommended protocol meets VANET security requirements such as authentication, unforgeability, confidentiality, and integrity simultaneously at a lower cost. Also, it is effective in high-traffic areas. Besides, under the Computational Diffie-Hellman (CDH) and Discrete logarithm (DL) concerns, the random oracle model reveals that PHSC-VC scheme is secure. Finally, as shown in the performance analysis, our protocol shows lower computation cost, better communication efficiency, and lower power consumption. Hence, PHSC-VC is practical and efficient in achieving cryptography in limited devices such as VANETs.






Similar content being viewed by others
References
Rodrigo-Salazar L, Gonzalez-Carrasco I, Garcia-Ramirez AR (2021) An iot-based contribution to improve mobility of the visually impaired in smart cities. Computing 103(6):1233–1254
Debnath A, Basumatary H, Dhar M, Debbarma MK, Bhattacharyya BK (2021) Fuzzy logic-based VANET routing method to increase the QoS by considering the dynamic nature of vehicles. Computing 103(7):1391–1415
Mchergui A, Moulahi T, Nasri S (2020) Qos evaluation model based on intelligent fuzzy system for vehicular ad hoc networks. Computing 102:2501–2520
Elkhalil A, Zhang J, Elhabob R (2021) An efficient heterogeneous blockchain-based online/offline signcryption systems for internet of vehicles. Clust Comput 24(3):2051–2068
Malhi AK, Batra S, Pannu HS (2020) Security of vehicular ad-hoc networks: a comprehensive survey. Comput Secur 89:101664
Elkhalil A, Elhabob R, Eltayieb N et al (2021) An efficient signcryption of heterogeneous systems for internet of vehicles. J Syst Archit 113:101885
Joshi GP, Perumal E, Shankar K, Tariq U, Ahmad T, Ibrahim A (2020) Toward blockchain-enabled privacy-preserving data transmission in cluster-based vehicular networks. Electronics 9(9):1358
Lin C, He D, Huang X, Kumar N, Choo KKR (2020) Bcppa: a blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks. IEEE Trans Intell Transp Syst 22(12):7408–7420
Shukla D, Kumar V, Prakash A (2020) Performance evaluation of IEEE 802.11 p physical layer for efficient vehicular communication. In: Advances in VLSI, communication, and signal processing, Springer, pp 51–60
Sharma T, Sharma AK, et al (2020) Heterogeneous-internet of vehicles (het-iov) in twenty-first century: a comprehensive study. In: Handbook of computer networks and cyber security, Springer, pp 555–584
Vasudev H, Das D, Vasilakos AV (2020) Secure message propagation protocols for IoVs communication components. Comput Electr Eng 82:106555
Mukherjee S, Gupta DS, Biswas G (2019) An efficient and batch verifiable conditional privacy-preserving authentication scheme for VANETs using lattice. Computing 101(12):1763–1788
Jaballah WB, Conti M, Lal C (2020) Security and design requirements for software-defined VANETs. Comput Netw 169:107099
Wang F, Zhu H, Liu X, Lu R, Li F, Li H, Zhang S (2018) Efficient and privacy-preserving dynamic spatial query scheme for ride-hailing services. IEEE Trans Veh Technol 67(11):11084–11097
Li Y, Qi Y, Lu L (2017) Secure and efficient v2v communications for heterogeneous vehicle ad hoc networks. In: 2017 International conference on networking and network applications (NaNA), IEEE, pp 93–99
Kaur R, Ramachandran RK, Doss R, Pan L (2021) The importance of selecting clustering parameters in VANETs: a survey. Comput Sci Rev 40:100392
Garg S, Mehrotra D, Pandey HM, Pandey S (2021) Accessible review of internet of vehicle models for intelligent transportation and research gaps for potential future directions. Peer-to-Peer Netw Appl 14(2):978–1005
Khan S, Sharma I, Aslam M, Khan MZ, Khan S (2021) Security challenges of location privacy in VANETs and state-of-the art solutions: a survey. Future Internet 13(4):96
Arif M, Wang G, Bhuiyan MZA, Wang T, Chen J (2019) A survey on security attacks in VANETs: communication, applications and challenges. Veh Commun 19:100179
Wang P, Liu Y (2021) Sema: secure and efficient message authentication protocol for VANETs. IEEE Syst J 15(1):846–855
Tantaoui M, Laanaoui MD, Kabil M (2021) Big data accident prediction system in green networks and intelligent transportation systems. In: Emerging trends in ICT for sustainable development, Springer, pp 121–127 (2021)
Yao M, Wang X, Gan Q, Lin Y, Huang C (2021) An improved and privacy-preserving mutual authentication scheme with forward secrecy in VANETs. Secur Commun Netw
Lozupone V (2018) Analyze encryption and public key infrastructure (PKI). Int J Inf Manag 38(1):42–44
Narayana VL, Bharathi C (2017) Identity based cryptography for mobile ad hoc networks. J Theor Appl Inf Technol 95(5):1173
Al-Riyami SS, Paterson KG (2003) Certificateless public key cryptography. In: International conference on the theory and application of cryptology and information security, Springer, pp 452–473
Tso R, Huang X, Susilo W (2012) Strongly secure certificateless short signatures. J Syst Softw 85(6):1409–1417
He D, Chen J, Zhang R (2012) An efficient and provably-secure certificateless signature scheme without bilinear pairings. Int J Commun Syst 25(11):1432–1442
Tian M, Huang L (2013) Cryptanalysis of a certificateless signature scheme without pairings. Int J Commun Syst 26(11):1375–1381
Yin A, Liang H (2015) Certificateless hybrid signcryption scheme for secure communication of wireless sensor networks. Wireless Personal Commun 80(3):1049–1062
Zhou F, Li Y, Ding Y (2019) Practical v2i secure communication schemes for heterogeneous VANETs. Appl Sci 9(15):3131
Jin C, Chen G, Yu C, Shan J, Zhao J, Jin Y (2018) An efficient heterogeneous signcryption for smart grid. PLoS ONE 13(12):e0208311
Ali I, Lawrence T, Omala AA, Li F (2020) An efficient hybrid signcryption scheme with conditional privacy-preservation for heterogeneous vehicular communication in vanets. IEEE Trans Veh Technol 69(10):11266–11280
Omala AA, Mbandu AS, Mutiria KD, Jin C, Li F (2018) Provably secure heterogeneous access control scheme for wireless body area network. J Med Syst 42(6):108
Zhou Y, Yang B, Zhang W (2016) Provably secure and efficient certificateless generalized signcryption. Chin J Comput 39:543–551
Shao Z, Gao Y (2014) A provably secure signature scheme based on factoring and discrete logarithms. Appl Math Inf Sci 8(4):1553
Ullah I, Alomari A, Ul Amin N, Khan MA, Khattak H (2019) An energy efficient and formally secured certificate-based signcryption for wireless body area networks with the internet of things. Electronics 8(10):1171
Naresh VS, Reddi S, Kumari S, Allavarpu VD, Kumar S, Yang M-H (2021) Practical identity based online/off-line signcryption scheme for secure communication in internet of things. IEEE Access 9:21267–21278
Caixue Z (2018) Certificateless signcryption scheme without random oracles. Chin J Electron 27(5):1002–1008
Sun Y, Li H (2010) Efficient signcryption between TPKC and IDPKC and its multi-receiver construction. Sci China Inf Sci 53(3):557–566
Li F, Han Y, Jin C (2016) Practical access control for sensor networks in the context of the internet of things. Comput Commun 89:154–164
Luo M, Wen Y, Hu X (2019) Practical data transmission scheme for wireless sensor networks in heterogeneous IoT environment. Wireless Personal Commun 109(1):505–519
Saeed MES, Liu Q, Tian G, Gao B, Li F (2018) Hoosc: heterogeneous online/offline signcryption for the internet of things. Wireless Netw 24(8):3141–3160
Shim K-A, Lee Y-R, Park C-M (2013) Eibas: an efficient identity-based broadcast authentication scheme in wireless sensor networks. Ad Hoc Netw 11(1):182–189
Barreto PS, Kim HY, Lynn B, Scott M (2002) Efficient algorithms for pairing-based cryptosystems. In: Annual international cryptology conference, Springer, pp. 354–369
Barreto PS, Galbraith SD, hÉigeartaigh CÓ, Scott M (2007) Efficient pairing computation on supersingular abelian varieties. Des Codes Cryptogr 42(3):239–271
Acknowledgements
This work was supported by the Fund for the National Nature Science Foundation of China (Grant: 61671392).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Elkhalil, A., zhang, J. Practical heterogeneous signcryption system for vehicular communication in VANETs. Computing 105, 89–113 (2023). https://doi.org/10.1007/s00607-022-01114-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00607-022-01114-0