Abstract
In modern days, for the perseverance of monitoring the vigor of a specific individual, the Wireless Body Sensor Networks have been emerging as an auspicious platform. The foremost challenge such as energy, path loss, and transmission distance that is prevalent from early days has been addressed in this article. The focal notion specified in this exploration is to discover the sensor locations on a human body that is much suitable for interconnecting the information about the intact body thus satisfying all the objectives. The focal difference between the proposed technique and the existing methods is that the projected methodology enacts multiple objectives as an alternative of distinct impartial. Further, the problem of finding the locations of sensors has been executed on an online monitoring system using MATLAB platform where the consequences are found to be improved practically for about 65% when compared with existing literature.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In Wireless Sensor Network (WSN) every node entails a transceiver, control source and even small sensors which will be governed by the application expanse [1]. If WSNs comprise some intuiting stations such as dispersed and automated stations then, it is distinct that these are entitled as sensing nodes. For posing the exemplar swing and for the perseverance of identifying the ailments at prompt period, a dissection of wireless sensor networks which is termed as Wireless Body Sensor Network (WBSNs) is used [2,3,4] where, these types of WBSNs will accumulate and evaluate the dynamic insignia information that is taken from diverse persistent which is finally organized with some type of measuring device such as blood compression, body temperature, etc. This in turn will result in reducing the cost of health care for a protracted period time [5].
Further, the measuring device that is associated to bio-medical (sensor nodes) will be placed in an untiring form [6] which will direct the information that is intuited to a base station and will be positioned near the incarnation where the core depot will only be responsible for progressing the data to the sink node. As a final point, the data collected will be furthered to the destination for making decisions. Also, interactions between the bodies with the help of measuring devices will pretense some fascinating challenges such as allocating the resources, ensuring the quality of services and privacy [7]. Suppose if the interacting procedures are minimized then, it is fortuitous that this minimization will proliferate the network runtime. This in turn will have the consequence in forfeiting the quality of the network that is used in delicate medical applications. WBSNs can certainly be used in extensive applications [8] but the difficulty in these applications is that an integrated solution is only preferred even when different application-related protocols are available where the corresponding WBSNs will be smaller and will have a smaller amount of redundancy.
Additionally, if any node failure and system is cramming then, accumulating the sensor and path redundancy will not be deliberated as a vivacious tactic [9] in decreasing the form aspect and reserve convention. This type of accumulation the redundancy will certainly lead to inadequacies when functioning with the two to ten nodes. Besides, intellectual and supportive quality amenities must be provided to the sensor nodes in an intellect that both in and out body networks should always afford heterogeneity thus satisfying the constraints such as placement and sensors desires. In accumulation, the necessities of different applications vary considerably where few applications will rely on online networks and the remaining will be contingent on wireless networks services thus providing security at diverse locations of the entire body.
Still, some other applications exclusively depend on entrenched strategies which in turn offer only a small amount of communication [10]. It is stated [11,12,13] that some of the nominal encounters such as providing secured communication association in each part of the body, operating the nodes by consuming low power and overwhelming the failure of the linkage by triumphing zero latency have to be appropriately addressed as manipulating the data processing is very hierarchical. The procedure should be carefully tested for the persistence of ensuring the data when required. Moreover, this kind of technique will be able to internment a set of large data thus providing the quality requirements that will be used as inter-communication medical device.
Further, the authors [14,15,16] prompted that when the sensors are used for the bio-medical purposes the primary control source can never be supplanted which affords energy efficiency by covering the indigenous node depletion and the overall network epoch. It is also possible for battery replacement only when wearable bio-medical sensors are used. But the major drawback is that it provides discomfort to a huge number of patients. Thus, it is conveyed [17] that both indigenous node depletion and the overall network epoch are the central challenges that need to be addressed appropriately in WSN.
The sensor node communication will ingest much vitality thus a system epoch can be defined [18] as a stint from where the network flinches until the period when the starting node of the entire network terminates. Due to the verve constriction of entrenched measuring device and unfeasibility of interchanging it the network epoch is considered as an important factor in WBSNs. Thus, for saving energy a uniform clustering algorithm is projected which will make the lifetime of the network prolong for a long period time [19, 20].
For detecting certain categories of conveyance offensives the instigator [21] has commenced a new system which is known as network sentient repute using adaptive detection threshold where the entire lifetime of the network has been distributed by prearrangement of some impost stages. The WSN will evaluate the entire packet loss during the assessment period which will transpire concerning themselves and also between their neighboring nodes. The packet loss is thus deliberated for evaluating the conveyance comportment of each downstream neighbor with information progressing path. If any WSN is found to act as impish then, the corresponding node will be rejected based on infamy values. If the value of the particular node has traversed across the restraint value then it will be acknowledged as a haggled hub. Similarly, for transmitting the information to the sink node with the help of cluster head [22] an optimization algorithm that entails multiple objectives has been employed. Furthermore, the algorithm decodes the inverse of the total energy that is required for each cluster head and for each non-cluster head to pass the information. The cluster head will also inverse the number of nodes if it is only non-cluster based where the corresponding energy for transmitting the information will be directed to the cluster rudiments.
The approach [23] employs a routing algorithm that is based on prophecy and this tactic uses a kalman filter for such predictions. Enhanced extrapolation will be realized as the kalman filter is employed in the WBSN link thus directing the data packets in a secured manner which in turn improves the reliability. With this process [23] the unsuccessful transmissions will be reduced and the network will cover up to long-range. But the major drawback is that the medical information of a particular person can be easily hacked. The data thus collected can also be altered to a preferred location using stable links where each health parameter is employed for extenuating the error triggered by each WSN. The strategic development has been developed for electromagnetic wireless networks [24] which employs an effectual forwarding system for improving the communication enactment. The projected technique explores the consequence of absorption, dispersion loss, and surveillance where harvesting the energy is essential for constantly operating the nodes. The main disadvantage that is prevailing in communication protocol is the low dispensation and inadequate battery power. Therefore, the employed scheme enables an energy-efficient procedure that will be entirely dependent on multi-hop communication.
To expand the consumption of power that is expended by the sensors [25] has projected a technique that is based on the segregation of data. Also, the routing architecture has been propounded for taming the reliability of data in case of failure in the gateway device where this method will segregate the readings taken from all the sensors and specifies this as an instant package to be sent to the gateway. In the process of transferring the data, the packets which are not commended will be plunged. But the major drawback of this method [25] is that smartphones should be contemporary therefore, the corresponding patients can be generally identified by wearing a WBAN sensor.
On the contrary [26] established a sentient technique for calculating the concealed lanes within a plane. In this technique, there will be a prearranged stretch for estimating the hidden areas that raises from source to the destination where, the brute force method which is characterized as graph transformation planning is involved for examining the optimal solution. The major disadvantage listed in [26] is that the radii evading strategy cannot be implemented virtually due to the time intricate concerning the endpoints. Analogous to [26], a multi-objective formulation for examining the data packets to choose the optimal solution using the energy-efficient routing protocol and extended-OCER protocols have been suggested [27]. The same technique has been implemented in [26] without considering the inter-node communication. But, when the inter-node communication is inoculated in the patient body then, the WSN will forward the necessary information to the entire body controller in an effectual manner.
As endowed in [28] a set of eight WSNs has been used for providing an efficient and consistent network that will be highly stable. The process takes place in such a way that the recorded data will be finally forwarded to the sink nodes. The WSN transforms itself as a forwarder node for gathering the essential data where the estimation of cost function needs two parameters if the WSN is selected as forwarder node. Further, for saving energy the multi-hop arrangement is used. Therefore, as a result, the network lifetime and the energy consumption is accomplished at the estimated level.
The strategic advances on [29, 30] focused on secured cluster forming protocol where [29] developed a model in which the human body residues as a group and therefore the group head will be selected. This is done for making an improved system lifetime. Correspondingly, for overwhelming the hotspot dispute [30] incorporated the method of cognizance in such a way the data traffic will be distributed consistently. This in turn minimizes the conception of hotspots and the most secured node will be finally selected for passing the required information. Therefore, compared to [29], the throughput will be much higher when a malicious node is present. However, an automated system is necessary for monitoring the health of individuals therefore, Learning Automata Based Multilevel Heterogeneous Routing (LA-MHR) protocol [31] is used for sharing the spectrum of individual data. But, the lifetime of the entire network is improved to a margin of 10% which is much lesser. To improve the network lifetime a heterogeneous protocol has been integrated [32] where three-node networks are used and the main drawback for this heterogeneous protocol method is that the base station is not at a fixed position. After fixing the base station at a fixed position an energy-efficient heterogeneous protocol has been designed [33] where different threshold levels are considered. Nevertheless, for monitoring the health conditions different threshold levels cannot be used [33].
For solving the drawback in [33] a single threshold level is used by establishing LEACH protocol [34]. Even though a common threshold level is considered the distance of sensors remains fixed which makes the cost of implementation to be much higher [34]. Therefore, for varying the distance a cluster-based protocol is established [35]. This method [35] has the advantage of handling the network if it is updated to 5G but it always requires the node to be in an active condition which results in low power-saving operation.
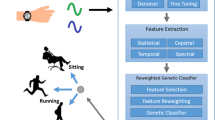
In line with the above concern, the delinquent of prudently picking the forwarder nodes is mislaid in the exceeding literature [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35]. Therefore, a multi-objective function is sensibly selected and a suitable methodology is thus estimated in this article. The functional block diagram of the proposed method is shown in Fig. 1.
2 Research gap and motivation
Integrating the proposed system with WBSNs is a challenging task and for overcoming the encounters such as communication distance and path loss a lot of techniques have been offered [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35]. Also, few measures are able to overcome these challenging tasks. But all the procedures enumerated [1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35] grieves from any one of the drawbacks. Therefore, the entire system thus needs an effective methodology for integrating the network with WBSNs thus satisfying the consistency desires. As an outcome for assimilating the WBSNs and for observing the entire network performance, an Energy Proficient Reliable Multi-hop Routing (EPMR) protocol using optimal clustering and path selection techniques has been projected. In the proposed model first, the conditional spider optimization (CSO) algorithm is integrated for balanced clustering. Subsequently, the flower-bee search (FBS) algorithm has been smeared to compute the best optimal path among the multiple paths.
2.1 Novelty and contribution of proposed work
The major objective of the proposed model is to integrate low-weight wrist-type wearable body sensors for measuring various parameters that are associated with the intact form of a humanoid. For monitoring persistence, three different sensors will be integrated and all measured data will be stored and secured using blockchain technology. Since an intelligent sensing device is implemented five different scenarios are deliberated for solving the proposed system model which includes three minimization problems such as packet loss, cost of implementation and consumption of energy. In addition, two maximization problems are also measured such as extending the lifetime of sensor nodes and distance of measurement using unguided media. All aforementioned objectives will be performed using a set of rules by defining Energy Proficient Reliable Multi-hop Routing (EPMR) protocol using optimal clustering and path selection techniques and by relating both CSO and FBD algorithms in two creases.
3 Problem formulation
The objective function is carefully chosen in such a way the primary intention is an assortment of forwarder nodes that consumes less interactive expanse, minimizing the consumption of energy, and low path loss. The projected methodology in this article is stated in [36] where a multi-objective function is enabled with an adaptive evolutionary multi-hop routing protocol.
3.1 Energy consumption
A two-way radio communication should be preferred between transmitter and receiver for transmitting the packets in a way such that the single-hop energy will always remain identical to the energy that is transmitted as shown in Eq. 1.
where
∆E, denotes the verve for transmitting and receiving a one bit message; ∆Eamp, represents the amplified energy; p, is the dimension of the packet; l, represents the distance between two nodes.
Conferring to the standard (IEEE 802.15.6), it is indicated that a maximum of two-hop communication will be allowed in WBSNs. As a result, the multi-hop network is considered that allows a two-hop transmission between transmitter and receiver as indicated in Eq. (3),
where h, is the number of hops per second; ∆Edata, represents the energy related to data aggregation; ∆Erec, represents the energy related to data reception.
If all the paths have analogous hops then, it is tranquil to select the node that is given second priority. The reason behind this is the low energy dissipation. Therefore, the objective function of the multi-hop can be expressed as,
The total energy for transmitting the data from sender end is written as,
where ∆Esal, represents the energy during transmission of salutation; ∆ECA, represents the energy related to channel access procedure.
The initial energy which is represented in Joules depends on the transmitted energy (TEe). Therefore, for the projected method minimum energy of initialization will be 0.0032 J. But, when total energy is considered then all the parameters will be considered and therefore the energy consumption will be higher and it depends on the number of communication cycles. It is observed that during the transmission of data packets more energy is wasted when compared to sensing. Also, in case the data does not reach the receiver (due to less signal strength) at a precise interval then, it leads to path loss where the path loss depends on two factors (i) Frequency of transmission and (ii) Distance between transmission and reception.
3.2 Path loss
The path loss can be defined by the following equation,
where l, embodies the distance between transmitter and receiver; l0, is the reference distance; Pathloss(0), signifies the reference distance; w, exemplifies the scattering parameter.
The reference distance (Pathloss(0)) can be calculated from Eq. (7),
The signal thus transmitted will get affected if the human body possesses different attacks. Therefore, the cost (Eq. (8)) can be calculated by considering the energy and distance between each node.
The consumption of energy and rump routing can be expressed with minimization of cost such that,
where Z, represents the number of available sensors.
3.3 Throughput
Throughput is demarcated as the aggregate quantity of effectively transmitted and received packets where, it is an obligatory constraint that throughput of the intact network should be exploited. Therefore, the optimization process for maximizing the throughput is expressed as,
where TRi, represents the number of successfully transmitted packets and it entirely depends on network life time (N).
The necessity for transmission range is to discover minimum amount of sensors which in turn examines each physical point with the help of a functioning measuring device where, a set of sensors are distributed over a large geographical area. For decreasing the power consumption, a minimum set of working nodes are carefully chosen which in turn makes the network lifetime longer.
where Snd and Sn0, represent the degree of preferred node and current node; Гk, denotes the coverage area that balances the extent that is concealed by the cluster.
3.4 Constraints
The network throughput as indicated in Eq. (10) is imperiled to subsequent constraints,
where Eq. (11) specifies the dropped information packets when the transmission occurs between i and k.
The constraint indicated in Eq. (12) indicates that a data transmission has not yet transpired as the transmitted energy is very much lesser than the multi hop energy.
3.5 Communication distance
The communication of data packets between two nodes should be maximized in such a way that the distance of the first link is deliberated from the training node to the applicant node. Then, after estimating the distance of the first link, the detachment of the second link is recognized form applicant node to sink node. Therefore, the distance stricture will always guarantee the delivery of the packet to the destination node which is given by the subsequent equivalence,
Since three different sensors are used for examining the body condition of each individual the distance of separation for each sensor between transmitter and receiver should be calculated and it is expressed as follows,
where \({d}_{i}\), represents the distance of separation between each sensor in meters.
Equation (15) represents the exact distance where three different sensors have to be placed with respect to each other. Since for each sensor it is necessary to determine its own position from gratified objects the measured distance is censored to half. Therefore, distance of separation will be lesser even though three sensors are being used and it produces low noise and path loss with high throughput.
4 Optimization algorithms
An Energy Proficient reliable Multi-hop Routing (EPMR) protocol for WBSNs using optimal clustering and path selection techniques is combined with the Conditional Spider Optimization (CSO) algorithm for balanced clustering. Generally, clustering consists of cluster formation and cluster head selection. Subsequently, the flower-bee search (FBS) algorithm is pooled to compute the best optimal path among the multiple paths.
4.1 Security measures using block chain
The major persistence of applying blockchain for body sensor networks is that details of various patients and their monitored body conditions will be preserved where it should not be available in common community. This block chain technology is integrated with projected formulations for providing high security to avoid dread conditions. In proposed security method probable conditions to assimilate blockchain protocol with three installed sensors, is conceded and all information will be saved in the cloud using a 32 bit authentication key. Also, it is found that block chain technology provides the precise solution for body sensors when it is integrated with flower bee algorithm where, the integrated algorithm provides high amount of flexibility than other algorithms since it is existing with different clusters.
Since three different sensors are used a back end transfer process will be created for designing an intelligent algorithm with distributed storage system. The working model of block chain with flower bee algorithm is designed so that a sensor will be positioned in suitable objects like a mask, helmet, or other objects that individuals are continually using. Therefore, the installed temperature sensor will monitor corresponding parameter and it reports to the central station which is treated as a receiver in corresponding sub-interval areas. Virtually, in this case more duplicate blocks will be created during the transmission and reception of data, so it becomes difficult for the hacker to steal the patient data. To recognize this blockchain technology the difficulty in inspecting the process should be known. Thus, the difficulty can be defined using Eq. (16) as,
where \({\sigma }_{i}\), denotes probable exertion that is associated among N distributed blocks.
After calculating the probable exertions, exact probability rate should be calculated and for the proposed method, more number of blocks is created to suppress number of external data attackers. This can be denoted in mathematical form as,
where \(\varphi \), denotes that a fractional data is present for excluding data with a probability of 0.5.
4.2 Balanced clustering
In CSO the search space is presumed to be a collective web spider. Therefore, in the populace each candidate will epitomize the spider. From the calculated fitness value each and every spider will receive an encumbrance. This is done in order to embody each spider.
The approach models two different search set of evolutionary operators that simulate different cooperative behaviors that are assumed in the colony. For solving the optimization problem the CSO uses the population candidate solution where, the solution embodies the position of the spider. In addition, there will be general web which will characterize the search space. For the purpose of pretending real spider colony the number of females is selected between 65 to 95 percent out of entire population. Therefore, the weight can be calculated as follows,
where \(fv_{j}\), represents the fitness value of the jth spider; \(wfv\), represents the worst fitness value; \(bfv\), represents the best fitness value in the intact population.
The fitness function hinges on the lumpy cliques dependency degree and it takes into contemplation the number of selected features. The foremost contrivance that is underlying in CSO is the optimization procedure which is pretended by means of vibrations that is formed in the web. The implementation procedure of CSO for EPMR protocol is illustrated in Fig. 2.
Therefore, the vibration alleged can be modeled as,
At the initial stage of the CSO algorithm N number of spiders was operated for defining the number of iterations. Diverse evolutionary operators were accompanied depending on the gender of each individual.
4.3 Improved flower bee algorithm
The primary objective of integrating the flower bee algorithm is to find the optimal solution for the objective functions as described in (3), (5), (9), (10) and (11) by satisfying a set of constraints as indicated in (12) and (13). The advantage of implementing the flower bee algorithm is that it can perform both exploitative neighborhood search and random explorative search. In proposed article there are eight scenarios where to code each scenarios individual attention to each issue is required. To simplify the complications and to ensure the individual attention of all cases the algorithm is designed in two folds. The first algorithm which is called conditional spider optimization will compare the existing data with the current one that is obtained at the output and the spiders will aggregate the data in a sequential way. Then, the aggregated data will be passed to flower bee algorithm where, the fitness function will be calculated for providing precise values. Finally all the values will be passed to the individual form the network server.
The flower bee algorithm will have both forward and backward phase where, a set of partial solutions will be generated in the forward pass stage with individual exploration and collective experience which will then be employed at the backward pass stage. In the backward pass stage the probability information is utilized to make the decision whether to explore the current solution in the next forward pass or to start the neighborhood of the new selected ones. From Fig. 3 it is clear that the new one is determined using probabilistic techniques such as the roulette wheel selection. Combined neighborhood size change and site rejection strategy has been integrated in flower bee algorithm which will avoid local minima by changing the neighborhood size adaptively. The algorithm will initially start by instigating the shrinking strategy which will work on a preeminent position only after accomplishing certain amount of recurrences. Once the recurrence halts then, the shrinking strategy will also be clogged. Conversely, if the recurrence surges for a large number of iterations then, an enhancement strategy will be utilized. If the recurrence still proliferates then, the corresponding site will be uninhibited. Therefore, as a result a new site will be automatically engendered. This will have the solution as follows,
4.3.1 Implementation step of improved flower bee algorithm after balanced clustering
-
1.
i = 0
-
2.
Generate initial population.
-
3.
Evaluate Fitness Value of initial population.
-
4.
Sort the initial population based on the fitness result.
$$ {\mathbf{While}}\,{\mathbf{i}} \le \, {\mathbf{fitness}}\,{\mathbf{value}} \le {\mathbf{error}} $$ -
5.
i = i + l;
-
6.
Select the elite patches and non-elite best patches for neighborhood search.
-
7.
Recruit the forager bees to the elite patches and non-elite best patches.
-
8.
Evaluate the fitness value of each patch
-
9.
Sort the results based on their fitness
-
10.
Allocate the rest of the bees for global search to the non-best locations.
-
11.
Evaluate the fitness value of non-best patches.
-
12.
Sort the overall results based on their fitness.
-
13.
Run the algorithm until termination criteria met.
The cumulative effect of this proposed work is as follows, the EPMR methodology is based on centralized procedure that is the sink node is utilized in all types of calculations. Since, the sink node will be the hub to co-ordinate and receive all the information’s like the remaining battery level (Which is used to calculate the remaining life term) and the position the neighboring node (Current location status of the all the nearby nodes) as well these information have been updated to the sink node in each and every rounds. Figure 3 represents the integration of flower bee algorithm with proposed system model where, in first phase maximum and minimum number of individuals will be determined for monitoring persistence and exact values will be provided. Once the population of individuals are provided then system model with different scenarios will be incorporated for balancing the outcomes. In the next phase fitness function i.e., to check whether the examined values are within boundary conditions has to be processed and if boundary values are correct the algorithm will select precise solution. Once precise solution is known outcome values are reproduced.
5 Results and discussion
The result and discussion focuses to give clear focus on how the proposed methodology produces better results in compactions with the existing methodologies.
5.1 Simulation setup
The proposed methodology is executed through online monitoring system and the values are plotted in MATLAB. The proposed method is executed and compared with existing works such as temperature and energy aware protocol (M-ATTEMPT), a distance & energy aware protocol (SIMPLE), the even energy consumption & backside routing protocol (EECBR) and (EMPR) protocol. The major reason for comparing the proposed method with M-ATTEMPT is that since more number of data is executed there is a high possibility that more data will be similar to each other and in this case the best data path will be compared and selected. Similarly, EMPR and EECBR have been associated for detecting the backside motion of the individual and for aggregating the backside data. The aforementioned implementation of protocols [37, 38] forms the basis of the proposed work where, the network specifications fed from the sensors as input are shown in Table 1. Even in recent research [39] the authors have performed a survey where three sensors have not been integrated at low cost system. Also, data security scheme is involved in the process [40] but a block chain technology is appropriate for the system with high storage. In addition a fuzzy based model is examined with energy aware protocol [41] but lifetime of network for sensors is about 15 years which is already higher therefore no separate model is required and all these inadequacies have been astounded by six different scenarios.
There are many smart technologies that are used for monitoring body conditions of each individual where, in all cases an intelligent sensing device termed as sensors will be preferred. The reason behind implementation of sensors is that it is light weight in its proportions and cost of implementing such sensing device is lesser. Also, this type of smart technology can store all monitored values in cloud using data sharing platform only when authorized users requests it. The only way implementation model differs is by the way of wearing it because many type of wearable models are created such as integration of sensors in wrist band, pointer watches, limb rings etc. If a particular individual is in need to monitor only blood pressure that is also completely possible by placing the wearable device in proper position. Moreover it is possible to integrate the working model of all different sensors in a single prototype for performing multiple functionalities. Even a strip type can be directly inserted inside the body but due to safety protections the usage of direct insertion of sensor strips is avoided. Most frequently a weight less material will be preferred for using this smart technology. By considering all pros and cons the authors have developed a light weight wearable device which is only 25 g and it is made with foam and black canvas. This type of low weight material can be used as a wearable band for elderly people without any inconvenience.
For the proposed scheme three different sensor data will be aggregated and it will be monitored using a cloud based online monitoring system (Thing speak). Therefore, this cloud storage will be treated as base station for transmitting the health condition of each individual. From this cloud based storage only the observed parametric values are taken and simulated using MATLAB. This makes the proposed model more flexible because network cost will be reduced and even the specialists can monitor the health of individuals at their respective locations. All the protocols such as M-ATTEMPT, EECBR and EMPR are used without any parametric evaluation such as energy consumption, throughput, path loss and no swarm intelligent algorithm has been integrated for the aforementioned protocols. Therefore, exact prediction of data is not possible whereas, for the proposed method since data aggregation process is involved using CSO, exact data can be sent to the online monitoring system. This makes the proposed scheme to perform much better than existing methods.
For each case three different type of sensors will be used such as Motion sensors, Hear beat sensors (Pulse sensors) and Temperature sensors. For all the aforementioned sensors the parameters such as energy consumption, path loss, cost and throughput will be measured. The input value will be fed from the sensor by using the command digitalWrite (Pin, Input) to the hardware boards such as Arduino or Raspberry Pi.
5.2 Rounds
In the proposed work number of rounds has been chosen to obtain a better simulation result. One round represents one cycle of information exchange between the deployed nodes to sink node. It is necessary that maximum number of rounds (Within 10,000) should be provided so that maximum power will be achieved and the power consumption in case of sensors will be reduced. This is much important in the proposed method because three different sensors are employed for monitoring the condition of individuals.
5.3 Path loss
Path loss refers to amount of power that is required to operate the senor and it is necessary that maximum number of rounds (Within 10,000) should be provided so that within the maximum round maximum power will be achieved and the power consumption in case of sensors will be reduced. This is much important in the proposed method because three different sensors are employed for monitoring the condition of individuals. In these body sensors each time the sensing nodes transmission time and energy utilized from the battery is taken into consideration for the path loss calculation. When the number of rounds increases drastically the energy spent by the protocol is very less comparing to the existing methodologies.
For example, in proposed method number of rounds is considered between 1 to 10,000 under scale of 100 where, path loss for every round have been calculated for proposed method and all existing technologies under different positions. It can be seen from Fig. 4 that when number of rounds increases from 1 to 100 the path loss for all devices remains constant at 50 dB whereas after the installed sensors crosses few number of rounds i.e., between 1000 to 10,000 the path loss varies extremely much higher. Therefore, it is much important to observe path loss at the aforementioned rounds and it is found that only the proposed method reduces the path loss of sensors to much higher extent. In the proposed method when number of rounds crosses 7800 then path loss decreases from 50 to 35 dB. Further, if the installed sensors cross number of rounds to 8400 then path loss will reduce from 35 to 31.66 dB which is very much lesser when compared to all associated methods that deliberates different algorithms. In addition, the major advantage of projected method is that it uses three different sensors and for all its types the path loss is lesser which is equal to 31.66 dB. Hence, Fig. 4 and Table 2 clearly depicts that the proposed methodology outperforms the entire existing schema by the way of making confirmed delivery of the data which in terns reflects that the very less loss during the data transmission.
5.4 Throughput
The purpose of determining throughput parameter in the proposed work is to check whether data has reached the receiver correctly. This parametric evaluation is most important in case of WBSN because in the proposed work two different algorithms has been integrated for data aggregation. Throughput which is expressed in terms of bits per second should always be higher for successful data transmission and reception.
It can be seen from Fig. 5 and Table 3 that the proposed method (EPMR) achieves very high throughput when compared to existing methods. After observing the compared test results with seven different state of art approaches it is apparent that quantity of test data for EPMR is increased to a great extent which indicates that associated measurable data is much sufficient for achieving high throughput. However, in existing methods [4, 5, 7, 8, 19, 21, 34] the value of throughput differs for all rounds and the test result values for proposed method is observed to be lesser for only one case i.e., when number of rounds is equal to 4000 then one of the compared existing method [21] provides higher throughput value and after intersection of certain rounds the same system proves to be less efficient then EPMR. Even other system techniques after following certain standard protocols cannot able to achieve high throughput value due to low quantity of available data. Since the data involves important values that are related to a human body it needs to be sent to the receiver accurately without any error. This is possible by the proposed EPMR because the throughput in this case is 37% higher than the existing methods. In case if amount of rounds are reduced then it is not possible to observe occupied rise in terms of throughput that is provided as an end result after sensing the body parameters. Moreover of quantity of data is provided at least equal to proposed EPMR then throughput can be achieved as expected within short period of time but if exact contrasting situation persists then it is difficult to achieve the same during such conflict periods.
5.5 Energy
It is significant that energy which is consumed by the nodes should be calculated for determining the exact power. In the proposed work three different sensors are employed therefore, it is much important to calculate the energy of nodes and the energy consumed by these three sensor nodes is always lesser even when they are operated continuously.
The energy parameter is expressed in terms of Joules where, the simulation results shows that after some communication cycle the proposed technique reduces the total energy spent by individual nodes and increases the individual life term as shown in Fig. 6. From Fig. 6 and Table 4 it can be seen that the proposed work utilized less energy when compared to M-ATT, SIMPLE, EECBR, and EMPR. Even though after integrating EPMR it is adequate that at low energy, high throughput is achieved but by comparing the proposed method with various baseline approaches it is observed that when number of rounds reaches 10,000 and above no energy is dissipated. In addition, at starting corpulent the energy that is consumed by all methods is equal to 16 Joules and after transient number of rounds i.e., when sequences are equal to 2000 then [21] achieves low energy state and at next sequence which is equal to 4000 subsequent state of low energy is observed. In both abovementioned sequences the proposed method using EPMR cannot able to deliver such low energy states but it is nearly equal to consumed energy where throughput is higher.
5.6 Cost
It is necessary that the cost of implementing sensors and corresponding nodes should be as low as possible. It can be seen form Fig. 7 that total cost of implementing three sensors with corresponding nodes (8 and 16) has been calculated and it is represented as total cost ($). The simulation results in Fig. 7 clearly represents the expenditure of individual sensing nodes are lesser when compared to the existing methodologies. For example if the number of nodes is 8 then, the cost value for EPMR will be 1653.71$ whereas for the existing methods the cost of implementation will be 2315.20$ (EMPR), 2447.49$ (EECBR), 3307.43$ (SIMPLE) and 3638.17$ (M-ATT), respectively. Therefore, the proposed method requires less cost of installation when compared to existing methods.
5.7 Network life time
If the sensors are integrated in a network then the life time of the entire network should be as higher as possible. Therefore, for checking the network life time maximum number of rounds has been taken into consideration. If the life time of network is maximum within a short communication cycle (rounds) then, the network will remain stable for a long period.
Figure 8 and Table 5 shows the life time of the proposed method where, EPMR achieves good network lifetime within a short communication cycle. But the other methods such as M-ATT, SIMPLE, EECBR, and EMPR achieves only less life lime and the network will not be stable for maximum period of time. It can be perceived from Table 5 that if network life time is zero then a short communication cycle can be easily established and the same trial method has been carried out and compared with several existing methods [4, 5, 7, 8, 19, 21, 34] and it is found that connected nodes are present during certain period of time which indicates that existing methods cannot be applied in real time without neighboring nodes. Although the presence of neighboring nodes is important it is also eminent that neighboring nodes will consume more energy. Thus to avoid such circumstance neighboring nodes are not associated and at final stage of evaluation 16 different neighboring nodes are attached. In addition the existing approach [21] can able to provide short communication cycle at zero network life time at later stages after crossing 4000 rounds but the proposed method using EPMR can provide short communication cycle at starting stage itself which proves that in real time without the presence of neighboring nodes EPMR will function effectively within a short communication cycle.
5.8 Stability analysis
For implementing wireless system the entire operation should remain stable within less communication cycle. Therefore, the stability analysis has been carried out for EMPR protocol to check the stability conditions. If the sensor network is not stable then, the values such as heart rate and temperature provided to the online monitoring system will not be stable and it results in big problem which makes the specialists difficult to provided solutions.
From Fig. 9 and Table 6 it can be seen that exact prediction with a stable wireless network has been obtained only with EMPR whereas, the other methods are less stable within a short communication cycle. Even though the existing methods achieve stability it is not possible with short interval of time therefore, more data will be erroneous when compared with EMPR.
6 Conclusions
In current generation there is a huge requisite for monitoring the health of each individual at their remote locations by using an intelligent sensing device. Also a lot of supplies are available for monitoring the health of individuals with high speed network connectivity and storage systems in the cloud. In addition, there are lot of wearable devices that can be implanted in body of each individual. Therefore, by using the underlying concept of sensors a new flanged technique for monitoring the health of individuals has been discussed. The major difference from existing methodologies is that a light weight material will be used which is made of foam and black canvas. Therefore, more number of sensors can be placed inside it and can be used as a wearable device in any part of the body contingent to corresponding parameters. When sensors are integrated in any system model the basic parameters such as path loss, energy consumption and communication distance for transmitting the necessary information have to be tested. So in proposed model multiple objectives for testing sensors have been integrated using EPMR protocol with cluster head. Additionally, block chain technology is implemented for providing high security to all monitored parameters. Further, the entire prototype is integrated with online monitoring system and observed values are simulated using MATLAB. From the simulation results it is distinctive that the projected method yields an improved solution when compared with the prevailing literatures. In future, the proposed work can be extended for various applications that are allied to healthcare and by relating the appropriate data that is congregated form wearable sensors for monitoring the heart rate.
References
Ashok RL, Agrawal DP (2003) Next-generation wearable networks. Computer (Long Beach Calif) 36:31–39. https://doi.org/10.1109/MC.2003.1244532
MacIa-Fernandez G, Garcia-Teodoro P, Diaz-Verdejo J (2009) Fraud in roaming scenarios: an overview. IEEE Wirel Commun 16:88–94. https://doi.org/10.1109/MWC.2009.5361183
Su H, Zhang X (2009) Battery-dynamics driven TDMA MAC protocols for wireless body-area monitoring networks in healthcare applications. IEEE J Sel Areas Commun 27:424–434. https://doi.org/10.1109/JSAC.2009.090507
Manfredi S (2014) Congestion control for differentiated healthcare service delivery in emerging heterogeneous wireless body area networks. IEEE Wirel Commun 21:80–90. https://doi.org/10.1109/MWC.2014.6812295
He Y, Zhu W, Guan L (2011) Optimal resource allocation for pervasive health monitoring systems with body sensor networks. IEEE Trans Mob Comput 10:1558–1575. https://doi.org/10.1109/TMC.2011.83
Ghasemzadeh H, Loseu V, Ostadabbas S, Jafari R (2010) Burst communication by means of buffer allocation in body sensor networks: Exploiting signal processing to reduce the number of transmissions. IEEE J Sel Areas Commun 28:1073–1082. https://doi.org/10.1109/JSAC.2010.100912
Zhang X, Jiang H, Zhang L et al (2010) An energy-efficient ASIC for wireless body sensor networks in medical applications. IEEE Trans Biomed Circuits Syst 4:11–18. https://doi.org/10.1109/TBCAS.2009.2031627
Rebeiz E, Caire G, Molisch AF (2012) Energy-delay tradeoff and dynamic sleep switching for bluetooth-like body-area sensor networks. IEEE Trans Commun 60:2733–2746. https://doi.org/10.1109/TCOMM.2012.12.110143A
Robles T, Kadelka A, Velayos H et al (2001) QoS support for an all-IP system beyond 3G. IEEE Commun Mag 39:64–72. https://doi.org/10.1109/35.940038
Thotahewa KMS, Khan JY, Yuce MR (2014) Power efficient ultra wide band based wireless body area networks with narrowband feedback path. IEEE Trans Mob Comput 13:1829–1842. https://doi.org/10.1109/TMC.2013.120
Ghosh A, Halder A, Dhar AS (2012) A variable RF carrier modulation scheme for ultralow power wireless body-area network. IEEE Syst J 6:305–316. https://doi.org/10.1109/JSYST.2011.2173612
Abouei J, Brown JD, Plataniotis KN, Pasupathy S (2011) Energy efficiency and reliability in wireless biomedical implant systems. IEEE Trans Inf Technol Biomed 15:456–466. https://doi.org/10.1109/TITB.2011.2105497
Chang JY, Ju PH (2014) An energy-saving routing architecture with a uniform clustering algorithm for wireless body sensor networks. Futur Gen Comput Syst 35:128–140. https://doi.org/10.1016/j.future.2013.09.012
Bader A, Abed-Meraim K, Alouini MS (2012) An efficient multi-carrier position-based packet forwarding protocol for wireless sensor networks. IEEE Trans Wirel Commun 11:305–315. https://doi.org/10.1109/TWC.2011.120911.110674
Sharma S, Jena SK (2015) Cluster based multipath routing protocol for wireless sensor networks. Comput Commun Rev 45:14–20. https://doi.org/10.1145/2766330.2766333
Babaie S, Zadeh AK, Amiri MG (2010) The new clustering algorithm with cluster members bounds for energy dissipation avoidance in wireless sensor network. In: 2010 international conference on computer design and applications (ICCDA), vol 2, pp 3–7. https://doi.org/10.1109/ICCDA.2010.5541280
Elhabyan RSY, Yagoub MCE (2015) Two-tier particle swarm optimization protocol for clustering and routing in wireless sensor network. J Netw Comput Appl 52:116–128. https://doi.org/10.1016/j.jnca.2015.02.004
Du T, Qu S, Liu F, Wang Q (2015) An energy efficiency semi-static routing algorithm for WSNs based on HAC clustering method. Inf Fusion 21:18–29. https://doi.org/10.1016/j.inffus.2013.05.001
Mahajan S, Malhotra J, Sharma S (2014) An energy balanced QoS based cluster head selection strategy for WSN. Egypt Inform J 15:189–199. https://doi.org/10.1016/j.eij.2014.09.001
Handy MJ, Haase M, Timmermann D (2002) Low energy adaptive clustering hierarchy with deterministic cluster-head selection. In: 2002 4th international conference on mobile wireless communications, networking, MWCN, pp 368–372. https://doi.org/10.1109/MWCN.2002.1045790
Ren J, Zhang Y, Zhang K, Shen X (2016) Adaptive and channel-aware detection of selective forwarding attacks in wireless sensor networks. IEEE Trans Wirel Commun 15:3718–3731. https://doi.org/10.1109/TWC.2016.2526601
Hacioglu G, Kand VFA, Sesli E (2016) Multi objective clustering for wireless sensor networks. Expert Syst Appl 59:86–100. https://doi.org/10.1016/j.eswa.2016.04.016
Anwar A, Duraisamy S (2018) A predictive routing algorithm for WBSN based on Kalman filter iterations. IEEE Sens J 18:7741–7748. https://doi.org/10.1109/JSEN.2018.2847049
Kambourakis G, Damopoulos D, Papamartzivanos D, Pavlidakis E (2014) Co Co. 2973–2980. https://doi.org/10.1002/sec
Afsana F, Asif-Ur-Rahman M, Ahmed MR et al (2018) An energy conserving routing scheme for wireless body sensor nanonetwork communication. IEEE Access 6:9186–9200. https://doi.org/10.1109/ACCESS.2018.2789437
Chen DR, Hsu CC, Chen MY, Guo CF (2018) A power-aware 2-covered path routing for wireless body area networks with variable transmission ranges. J Parallel Distrib Comput 118:379–397. https://doi.org/10.1016/j.jpdc.2017.08.006
Kaur N, Singh S (2017) Optimized cost effective and energy efficient routing protocol for wireless body area networks. Ad Hoc Netw 61:65–84. https://doi.org/10.1016/j.adhoc.2017.03.008
Khan RA, Mohammadani KH, Soomro AA et al (2018) An energy efficient routing protocol for wireless body area sensor networks. Wirel Pers Commun 99:1443–1454. https://doi.org/10.1007/s11277-018-5285-5
Sangeetha Priya N, Sasikala R, Alavandar S, Bharathi L (2018) Security aware trusted cluster based routing protocol for wireless body sensor networks. Wirel Pers Commun 102:3393–3411. https://doi.org/10.1007/s11277-018-5374-5
Bhangwar AR, Kumar P, Ahmed A, Channa MI (2017) Trust and thermal aware routing protocol (TTRP) for wireless body area networks. Wirel Pers Commun 97:349–364. https://doi.org/10.1007/s11277-017-4508-5
Tanwar S, Tyagi S, Kumar N, Obaidat MS (2019) LA-MHR: learning automata based multilevel heterogeneous routing for opportunistic shared spectrum access to enhance lifetime of WSN. IEEE Syst J 13:313–323. https://doi.org/10.1109/JSYST.2018.2818618
Tanwar S, Kumar N, Rodrigues JJPC (2015) A systematic review on heterogeneous routing protocols for wireless sensor network. J Netw Comput Appl 53:39–56. https://doi.org/10.1016/j.jnca.2015.03.004
León O, Hernández-Serrano J, Soriano M (2010) Securing cognitive radio networks. Int J Commun Syst 23:633–652. https://doi.org/10.1002/dac
Tyagi S, Gupta SK, Tanwar S, Kumar N (2013) EHE-LEACH: Enhanced heterogeneous LEACH protocol for lifetime enhancement of wireless SNs. In: Proceedings of 2013 international conference on advanced computing and communications informatics (ICACCI), pp 1485–1490. https://doi.org/10.1109/ICACCI.2013.6637399
Tyagi S, Tanwar S, Gupta SK et al (2015) A lifetime extended multi-levels heterogeneous routing protocol for wireless sensor networks. Telecommun Syst 59:43–62. https://doi.org/10.1007/s11235-014-9884-5
Esmaeili H, Minaei Bidgoli B (2018) EMRP: evolutionary-based multi-hop routing protocol for wireless body area networks. AEU Int J Electron Commun 93:63–74. https://doi.org/10.1016/j.aeue.2018.06.003
Javaid N, Abbas Z, Fareed MS et al (2013) M-ATTEMPT: a new energy-efficient routing protocol for wireless body area sensor networks. Procedia Comput Sci 19:224–231. https://doi.org/10.1016/j.procs.2013.06.033
Ha I (2016) Even energy consumption and backside routing: an improved routing protocol for effective data transmission in wireless body area networks. Int J Distrib Sens Netw 12:1–11. https://doi.org/10.1177/1550147716657932
Jabeen T, Ashraf H, Ullah A (2021) A survey on healthcare data security in wireless body area networks. J Ambient Intell Hum Comput. https://doi.org/10.1007/s12652-020-02728-y
Hajar MS, Omar Al-Kadri M, Kalutarage HK (2021) A survey on wireless body area networks: architecture, security challenges and research opportunities. Comput Secur 104:10211. https://doi.org/10.1016/j.cose.2021.102211
Wang X, Zheng G, Ma H et al (2021) Fuzzy control-based energy-aware routing protocol for wireless body area networks. J Sensors. https://doi.org/10.1155/2021/8830153
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The authors declare that no conflict of interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Teekaraman, Y., Manoharan, H. & Kuppusamy, R. Examining the effect of intellectual devices for healthiness using flower bee algorithm. Neural Comput & Applic 35, 22971–22987 (2023). https://doi.org/10.1007/s00521-022-07172-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-022-07172-x