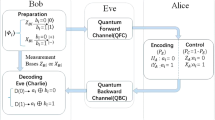
Abstract
In Appl. Opt. 55, 4720-4728 (2016), authors demonstrated the vulnerability of Linear Canonical Transform (LCT)-based optical encryption system. One of the primary reasons for this is the predictable nature of the security keys (i.e., simulated random keys) used in the encryption process. To alleviate, in this work, we are presenting a Physically Unclonable Function (PUF) for producing a robust encryption key for the digital implementations of any optical encoding systems. We note a correlation function of the scattered perfect optical vortex (POV) beams is utilized to generate the encryption keys. To the best of our knowledge, this is the first report on properly utilizing a scattered POV for the optical encryption systems. To validate the generated keys, the standard Linear Canonical Transform-based Double Random Phase Encoding (LCT-DRPE) technique is used. Experimental and simulation result validates the proposed key generation method as an effective alternative to the digital encryption keys.






Similar content being viewed by others
References
S. Vaudenay, A classical introduction to cryptography (Springer, New York, 2008)
W. Stallings, Cryptography and network security principles and practice (Prentice Hall, New York, 2011)
S.M. Bellovin, Frank Miller: inventor of the one - time pad. Cryptologia 35(3), 203–222 (2011)
I. Muniraj, J.T. Sheridan, Optical encryption and decryption (SPIE Press Book, 2019)
P. Refregier, B. Javidi, Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20(7), 767–769 (1995)
A. VanderLugt, Optical signal processing (Wiley Series in Pure and Applied Optics, New York, 2005)
S. Liu, C. Guo, J.T. Sheridan, A review of optical image encryption techniques. Opt. Laser Technol. 57, 327–342 (2014)
O. Matoba, B. Javidi, Encrypted optical memory system using three-dimensional keys in the Fresnel domain. Opt. Lett. 24(11), 762–764 (1999)
G. Unnikrishnan, J. Joseph, K. Singh, Optical encryption by double-random phase encoding in the fractional Fourier domain. Opt. Lett. 25(12), 887–889 (2000)
L. Chen, D. Zhao, Optical image encryption with Hartley transforms. Opt. Lett. 31(23), 3438–3440 (2006)
G. Unnikrishnan, K. Singh, Optical encryption using quadratic phase systems. Opt. Commun. 193(1–6), 51–67 (2001)
N. Rawat, B. Kim, I. Muniraj, G. Situ, B.G. Lee, Compressive sensing based robust multispectral double-image encryption. Appl. Opt. 54(7), 1782–1793 (2015)
H. Li, C. Guo, I. Muniraj, B.C. Schroeder, J.T. Sheridan, S. Jia, Volumetric light-field encryption at the microscopic scale. Sci Rep. 7, 40113 (2017)
I. Muniraj, C. Guo, R. Malallah, J.P. Ryle, J.J. Healy, B.G. Lee, J.T. Sheridan, Low photon count based digital holography for quadratic phase cryptography. Opt. Lett. 42(14), 2774–2777 (2017)
C. Guo, I. Muniraj, J.T. Sheridan, Phase-retrieval-based attacks on linear-canonical-transform-based DRPE systems. Appl. Opt. 55(17), 4720–4728 (2016)
P. Ravikanth, B. Recht, J. Taylor, N. Gershenfeld, Physical one-way functions. Science 297(5589), 2026–2030 (2002)
Y. Gao, S.F. Al-Sarawi, D. Abbott, Physical unclonable functions. Nat. Electron. 3, 81–91 (2020)
B. Gassend, D. E. Clarke, M. van Dijk, S. Devadas, Silicon physical random functions. ACM Conference on Computer and Communications Security, 148–160, (2002)
C. Bohm, M. Hofer, Physical unclonable functions in theory and practice (Springer Publishers, 2013)
U. Ruhrmair, J. Solter, F. Sehnke, On the foundations of physical unclonable functions. IACR Cryptol. ePrint Arch. 2009, 277 (2009)
G.E. Suh, S. Devadas, Physical unclonable functions for device authentication and secret key generation (DAC, 2007), pp.9–14
M.S. Kim, G.J. Lee, J.W. Leem, S. Choi, Y.L. Kim, Y.M. Song, Revisiting silk: a lens-free optical physical unclonable function. Nat. Commun. 13, 247 (2022)
K. Chen, F. Huang, P. Wang, Y. Wan, D. Li, Y. Yao, Fast random number generator based on optical physical unclonable functions. Opt. Lett. 46(19), 4875–4878 (2021)
P. Wang, F. Chen, D. Li, S. Sun, F. Huang, T. Zhang, Q. Li, K. Chen, Y. Wan, X. Leng, Y. Yao, Authentication of optical physical unclonable functions based on single-pixel detection. Phys. Rev. Appl. 16, 054025 (2021)
A. Shamsoshoara, A. Korenda, F. Afghah, S. Zeadally, A survey on physical unclonable function (PUF)-based security solutions for internet of things. Comp. Net. 183, 107593 (2020)
R. Arppe-Tabbara, M. Tabbara, Thomas just Sørensen versatile and validated optical authentication system based on physical unclonable functions. ACS Appl. Mater. Interfaces 11(6), 6475–6482 (2019)
M. Georgios, Nikolopoulos, optical scheme for cryptographic commitments with physical unclonable keys. Opt. Exp. 27(20), 29367–29379 (2019)
A.S. Ostrovsky, C.R. Parrao, V. Arrizon, Generation of the ‘perfect’ optical vortex using a liquid crystal spatial light modulator. Opt. Lett. 38(4), 534–536 (2013)
J.W. Goodman, Speckle phenomena in optics: theory and applications (SPIE Press Book, 2020)
J.C. Dainty, Laser speckle and related phenomena (Springer, 1976)
S.G. Reddy, P. Chithrabhanu, S. Prabhakar, A. Anwar, R.P. Singh, Recovering the vorticity of a light beam after scattering. Appl. Phys. Lett. 107, 021104 (2015)
C.H. Acevedo, A. Dogariu, Non-evolving spatial coherence function. Opt. Lett. 43(23), 5761–5764 (2018)
I.S. Gradshteyn, I.M. Ryzhik, Table of integrals, series, and products (Academic Press, USA, 2007)
P. Vanitha, N. Lal, A. Rani, B.K. Das, S.G. Reddy, R.P. Singh, Correlations in scattered perfect optical vortices. J. Opt. 23(9), 095601 (2021)
L. Mandel, E. Wolf, Optical coherence and quantum optics (Cambridge University Press, 1995)
M. Wan, I. Muniraj, R. Malallah, N. Chen, J.J. Healy, J.P. Ryle, J.T. Sheridan, Orthographic projection images-based photon-counted integral Fourier holography. Appl. Opt. 58(10), 2656–2661 (2019)
N. Chen, Z. Ren, E.Y. Lam, High-resolution Fourier hologram synthesis from photographic images through computing the light field. Appl. Opt. 55, 1751–1756 (2016)
Acknowledgements
SGR likes to acknowledge the financial support from DST-SERB under grant number SRG/2019/000857.
Author information
Authors and Affiliations
Contributions
PV and BM have performed optical experiments and PV wrote the initial draft. SGR designed and formulated the ideas and was responsible for completion of the manuscript, IM worked on encryption part. SA and RPS critically examined/monitored each step of the work as the mentor and further reviewed/updated the manuscript.
Corresponding authors
Ethics declarations
Conflict of interest
The authors declare no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Vanitha, P., Manupati, B., Muniraj, I. et al. Augmenting data security: physical unclonable functions for linear canonical transform based cryptography. Appl. Phys. B 128, 183 (2022). https://doi.org/10.1007/s00340-022-07901-z
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s00340-022-07901-z