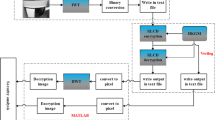
Abstract
Image data is frequently processed in multimedia, wireless, mobile communication etc. The digital images transmitted over the internet are prone to security threats and thus providing security for the images and videos becomes an essential issue for individuals, business and governments. Moreover, applications in the automobile, banking, medical, construction and fashion industry require designs, scanned data, and blue-prints to be protected against attackers. Though many cryptographic algorithms are proposed in literatures, there is no much effort concentrated on the design of low-power hardware-efficient cryptosystem architectures. In this work, we propose a novel crypto architecture using multiple Boolean reversible blocks with logic control inputs derived from standard test images. The pre-processing and shuffling on the control pixel bits decide the depth of logic operation of the crypto system. The proposed design involves Gray Code Image Scrambling block for pre-processing, Reversible Shuffling Unit for bit plane modification and final merger for plane regrouping and is designated as Reversible Logic-Image Key (RL-IK) design. The use of reversible logic unit for shuffling combined with Gray code image scrambling in key generation improves the security of the processed images from the encryption unit at the expense of increase in area. To optimize the proposed RL-IK design in terms of area and security metrics, Gray Code bit plane processing is eliminated in the least n/2–1 bits as the contribution of least significant bits in the pixel intensity is less. The proposed Area and Security Optimized RL-IK Architecture (AS-RL-IK) involves same process as that of its standard counterpart in n/2 + 1 Most Significant Bits bits. As the weight based shuffling block is the critical unit of the proposed architecture that contributes for high delay and hardware area, for portable non-critical applications high speed hardware efficient variant of RL-IK is proposed. The proposed High Speed Area Efficient RL-IK (HSAE-RL-IK) design eliminates the weight based shuffling unit and employs only the multi-logic reversible block to produce the intermediate cipher image. The proposed crypto systems are designed using structural Verilog HDL. Simulations with 180 nm and 45 nm Application Specific Integrated Circuit technology reveals that RLC-IK design and its optimized variants exhibits 37% less power consumption and 35% less delay than Integer Wavelet Transform-Heterogeneous Key Generation (IWT-HKG) design with optimized security to the least when compared to the best of designs.





















Similar content being viewed by others
Data availability
Data are available from the corresponding author on reasonable request.
References
F. Aulí-Llinàs, M.W. Marcellin, Scanning order strategies for bitplane image coding. IEEE Trans. Image Process. 21(4), 1920–1933 (2012)
C.H. Bennett, IBM J. Res. Dev. 17(6), 525 (1973)
S.S. Devi, V. Bhanumathi, Design of reversible logic based full adder in current-mode logic circuits. Microprocess. Microsyst. 76, 103100 (2020)
S.S. Devi, V. Bhanumathi, Reversible logic based MOS current mode logic implementation in digital circuits. CMC-Comput. Mater. Continua 70(2), 3609–3624 (2022)
R.P. Feynman, Found. Phys. 16(6), 507 (1986)
S. Karunamurthi, V.K. Natarajan, VLSI implementation of reversible logic gates cryptography with LFSR key. Microprocess. Microsyst. 69, 68–78 (2019)
I. Koyuncu, A.T. Özcerit, The design and realization of a new high speed FPGA-based chaotic true random number generator. Comput. Electr. Eng. 58, 203–214 (2017)
B. Koziel, R. Azarderakhsh, M.M. Kermani, D. Jao, Post-quantum cryptography on FPGA based on isogenies on elliptic curves. IEEE Trans. Circuits Syst. I Regul. Pap. 64, 86–99 (2017)
B. Koziel, R. Azarderakhsh, M.M. Kermani, A high-performance and scalable hardware architecture for isogeny-based cryptography. IEEE Trans. Comput. 67, 1594–1609 (2018)
S. Kuchhal, R. Verma, Security design of DES using reversible logic. Int. J. Comput. Sci. Netw. Secur. 15, 81 (2015)
R. Landauer, IBM J. Res. Dev. 5(3), 183 (1961)
A. Malik, S. Gupta, S. Dhal, Analysis of traditional and modern image encryption algorithms under realistic ambience. Multimed. Tools Appl. 79, 27941–27993 (2020)
S. Mozaffari, Parallel image encryption with bit plane decomposition and genetic algorithm. Multimed. Tools Appl. 77, 25799–25819 (2018)
K.A.K. Patro, B. Acharya, A secure block operation based bit-plane image encryption using chaotic maps, in First International Conference on Power, Control and Computing Technologies, 411–416 (2020).
V. Rathore, A.K. Pal, An image encryption scheme in bit plane content using Henon map based generated edge map. Multimed. Tools Appl. 80(14), 22275–22300 (2021)
K. Saranya, K.N.A. Vijeyakumar, Low Area FPGA implementation of reversible gate encryption with heterogeneous key generation. Circuits Systems Signal Process. 40, 3836–3865 (2021)
S. Somaraj, M.A. Hussain, Securing medical images by image encryption using key image’. Int. J. Comput. Appl. 104(3), 30–34 (2014)
Y. Zhou, W. Cao, C.P. Chen, Image encryption using binary bitplane’. Signal Process. 100, 197–207 (2014)
Y. Zhou, K. Panetta & S. Agaian, Image encryption using binary key-images, in 2009 IEEE International Conference on Systems, Man and Cybernetics, pp. 4569–4574(2009)
C. Zhu, K. Sun, Cryptanalysis and improvement of a class of hyper chaos based image encryption algorithms. Acta Physica Sinica 61(12), 120503 (2012)
H. Zodpe, A. Sapkal, An efficient AES implementation using FPGA with enhanced security features. J. King Saud Univ. Eng. Sci. 32, 115–122 (2018)
Funding
This study was not funded by any organization.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Saranya, K., Vijeyakumar, K.N. Design of area, energy and security optimized reversible architectures for digital image cryptography. Circuits Syst Signal Process 42, 5358–5384 (2023). https://doi.org/10.1007/s00034-023-02354-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-023-02354-x