Abstract
Given the ever-increasing advances in science and technology in recent years, the security and authentication issues using elliptic curve cryptography (ECC) have gained a lot of attentions especially for smart cards in a variety of networks, such as smart homes and medical-based care systems being based on the Internet of things (IoT). In systems such as health care, patient information is always crucial and no one should have access to this information. Recently, much research has been conducted in the area of security and authentication for medical care systems being based on the IoT using RFID technology. One of these schemes is the Alamr et al.’s protocol, which bears high computational cost for authentication between card and reader. In this paper, we have proposed a scheme based on ECC in order to establish a mutual authentication within RFID technology in the IoT. In the proposed scheme, computational cost, communication cost and elliptic curve point multiplication running time and data storage cost are investigated. Moreover, security requirements and various attacks have also been considered in the proposed protocols. AVISPA software has also been used for security analysis. The analyses represent that the proposed scheme has lower computational costs, lower communication costs and less elliptic curve point multiplication time compared with those of similar protocols. It has also resolved the security shortcomings of the RFID authentication protocol.
Similar content being viewed by others
1 Introduction
The debate on the Internet technology of objects is steadily increasing, and numerous research works have been done on this technology. This technology introduces an intelligent management and has a variety of models, including those models having many uses such as radio waves and bar codes [1]. The IoT these days has created a situation in which the lifeless things around us interact with and know each other [2]. These physical objects can be interconnected in a variety of ways, and some of them are: Wireless Fidelity, Radio Frequency Identification, and Quick Response Code [1]. The IoT has many uses in our society and today's life, including smart homes, smart cities, industrial Internet, connected machines, smart networks, intelligent retail, smart health, etc. The devices used in IOT communicate by radio communications, and security in such a network is low. However, the data transmitted in theme are of high importance; therefore, it is essential to provide a solid security scheme for these networks.
The RFID, discussed in research work, uses the wireless communication channels between cards and card readers; depending on the type of communication, it is determined that the transmitting space of spatial information is completely open and vulnerable and numerous attacks can threaten this connection; some of these probable attacks can be: eavesdropping, tracking and network scanning [3]. Therefore, there are many ways to secure this technology. An advantage of RFID technology is that if there is a direct distance, the objects can be identified and interconnected without contacting each other; this can be done using radio waves. Generally, a complete RFID system consists of three parts: card, card reader and a backup server or database. The cards can be divided into two active and passive categories according to their power supply; in addition, cards can use low-frequency waves, high-frequency waves or super-high-frequency waves. [3].
Several articles have used various cryptographies to provide security for RFID technology, some of them have used ECC, which is of asymmetric algorithms [4,5,6,7,8], and some of them are based on symmetric algorithms [9, 10]. ECC is a public key encryption approach based on the algebraic structure of elliptic curves in finite fields. ECCs also require smaller keys to provide relative security; this is the reason for its superiority [11, 12]. For current cryptographic purposes, an elliptic curve has been placed on a finite field (instead of actual numbers), where the points of interest have been specified along an infinite point. The use of an elliptic curve for cryptography was proposed by Neal Koblitz and Victor S. Miller in 1985. The elliptic curve started to be widely used in cryptography between 2004 and 2005 [13, 14]. The first RFID authentication protocol, being based on the elliptic curve algorithm, was presented by Tuyls and Banita [15]. Banita et al. presented a similar scheme of elliptic curve in 2007 using the Okamoto authentication scheme, but their protocols had problems that violated privacy [1]. Recently, papers such as Alamr et al. [3] and Liao [16] have used ECC for RFID authentication; however, they have had many computational costs. Another study proposed by Yang [17] addresses the problems of the Kaur [18] scheme which has a high computational cost. Yang [17] has made changes to the Kaur scheme and presented a new scheme reducing the high cost of computation.
A recent study done by Sowjanya et al. [19] has reviewed protocol proposed by Li et al. [20]. They have reviewed Li’s “ECC” and then questioned security problems such as man in the middle and lack of mutual authentication. Finally, they have proposed a new authentication protocol using ECC for monitoring of the healthcare system, having a lower computational cost. It has three phases: initialization, registration and authentication. Although it is a good protocol, it has a high computational cost. Dang et al. [21] who has developed Wang et al. protocol [22] have utilized ECC and cloud servers. They claimed that their scheme is energy efficient, but it has high computational cost. Li et al. [23] have also proposed another protocol for mutual authentication in distant healthcare system using cloud servers, but their scheme has high communicative cost. It also suffers from some security problems like forging attack, lack of message authentication, and session key threatening. Kumara et al. [24] also proposed another protocol. They have reviewed and discussed Li et al. [23] security problem scheme. They have decreased the communication cost and also resolved the security problems.
Recently, another protocol has been proposed by Noori et al. [25] which has a lower computational cost rather than other schemes. Furthermore, unlike most of the previous works, this protocol has 3 phases including: initialization, authentication and scalability phase. Some of key advantages of this protocol are that: This protocol is faster than other ones, and various attacks are considered in this protocol. Chinnasamy et al. [26] also proposed another protocol. They combine elliptic curve and Blowfish cryptography. In the combined algorithm of these authors, it is claimed that it has high confidentiality and security for patient data. In another protocol proposed by Dhanda et al. [27], the method of ECC has been compared with other Black Cypher methods, in which ECC and AES have been the most suitable lightweight cryptographic methods.
The structure of the paper is organized as follows: In subsection 1.2, first, we review A.A. Alamr et al. scheme. Next, in Sect. 2 we discussed about the method and the proposed scheme, including the initialization phase and the authentication phase; then, the analysis of the proposed solution as well as security and its efficiency have been addressed in Sect. 3, and finally, we presented the conclusions in Sect. 4.
1.1 Review of Alamr’s scheme
The Alamr et al. [3]. scheme is made up of two phases of initialization and authentication. The signs are shown in Table 1 to have a better view.
1.1.1 Initialization phase
In this phase, the server generates system parameters. To do this, the server selects a random number \({P}_{{r}_{R}}\in {F}_{P}\) as the private key of the card reader, and then, using Eq. (1), it generates a public key for the card reader:
In addition, the server selects a random number \({P}_{{r}_{T}}\in {F}_{P}\) as the private key of card, and then, using Eq. (2), it generates a public key for the card as well:
Then, the card and the card reader store their pair of keys in their memories, as well as the system parameters and parameters required in Table 2.
1.1.2 Authentication phase
This phase includes the following steps:
Step 1 The card reader generates a random number that is given in Eq. (3) and then calculates a point on an elliptic curve such as Eq. (4), and then, the card reader sends \({R}_{1}\) to the card.
Step 2 Once \({R}_{1}\) is received by card from the card reader, it generates a random number mentioned in Eq. (5) and then calculates a point on the elliptic curve such as Eq. (6). In the next step, the card creates 2 secret key using Eq. (7); then, the secret keys are encrypted using Eq. (8), and in the final step, the card sends \({C}_{1},{T}_{1}\) to the card reader.
Step 3 Once \({T}_{1}\) and \({C}_{1}\) are received, the card reader generates two temporary secret keys to reconstruct the encryption keys shown in (9) and then calculates Eq. (10) and compares it with Eq. (8); if they are the same, then the card will be authenticated (11). Next, the card reader calculates Eq. (12); in addition, it produces a new random number (13) and an elliptic curve point (14) for being used in the key agreement. After that, the card reader sends \({C}_{2},{R}_{2}\) to the card.
Step 4 The card calculates Eq. (15) and compares it with (12); if the result is the same, then the card reader is also authenticated (16).
Step 5 Then, the agreed keys are formed between the two sides, the card's key is equal to Eq. (17) and the card reader's is equal to (18).
1.1.3 The costs of A.A. Alamr’s scheme
The costs of this scheme as indicated by Alamr itself have 3 random numbers, 9 multiplications and 2 additions of the elliptic curve points, without hashing process.
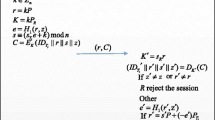
The authentication phase of Alamr scheme [3] is illustrated in Fig. 1.
The authentication protocol of Alamr scheme [3]
2 Methods
Lately, a scheme has been proposed by Alamr et al. [3], which has used an ECC algorithm for RFID authentication, being described as a good scheme. However, after having studied and reviewed this reference carefully, we found that the proposed scheme had higher computational costs, higher communication cost, and higher elliptic curve point multiplication running time while operating.
Thus, we propose a scheme based on the present research that has two phases: the Initialization phase and the authentication phase. Our scheme, providing the necessary security, has several benefits: It has reduced the computational and communication cost and lowered elliptic curve point multiplication running time. The Alamr scheme is discussed in detail in Sect. 1.2.
The signs are shown in Table 3 to have a better view.
2.1 Initialization phase
In this phase, the server generates system parameters. To do this, the server selects a random number \({P}_{{r}_{R}}\in {F}_{P}\) as the private key of the card reader. Then, a public key is generated for the card reader using Eq. (19) as follows:
The server also selects a random number \({P}_{{r}_{T}}\in {F}_{P}\) as the private key of the card. Then, a public key is generated for the card using Eq. (20):
Then, the card and card reader store their pair of keys with the system parameters and parameters required in Table 4 in their memory.
2.2 Authentication phase
This phase includes the following steps:
Step 1 The card reader generates a random number produced by Eq. (21) and next calculates a point on the elliptic curve, such as Eq. (22), and then, \(R\) is sent to the card by the card reader.
Step 2 After the card receives \(R\) from the card reader, it generates a random number being mentioned in Eq. (23) and then calculates a point on the elliptic curve such as Eq. (24). In the next step, the card creates a secret key through Eq. (25), and finally, the card calculates Eq. (26) for the encryption of the secret key and then sends \({C}_{1},T\) to the card reader.
Step 3 After receiving T and \({C}_{1}\), the card reader generates a secret key for reconstructing the encrypted key shown in Eq. (27),and then, it calculates Eq. (28) and compares it with Eq. (26). If they were identical, then the card is authenticated (29). Next, the card reader creates a secret key given in Eq. (30) and then calculates Eq. (31). After that, the card reader sends \({C}_{2}\) to the card.
Step 4 The card calculates the secret key using Eq. (32) and uses it to calculate Eq. (33) and then compares it with Eq. (31); if they are the same, the card reader is authenticated as well (34).
Step 5 Then, agreed keys are formed between the two sides, the side of the card is equal to Eq. (35) and the side of the card reader is equal to Eq. (36).
The authentication phase of proposed scheme is illustrated in Fig. 2.
2.3 The costs of proposed scheme
As it is known, the proposed scheme has two random numbers, 6 multiplications as well as 4 hashing processes.
3 Security and performance results and discussion
3.1 Security
In this section, we compare the proposed scheme with recent articles based on some of the important security requirements, such as mutual authentication, confidentiality, anonymity, availability, data integrity, privacy and forward security; moreover, the resistance of the proposed scheme to some major attacks has been scrutinized, including man-in-the-middle attack, replay attack, DoS attack and forging attack. Furthermore, in order to confirm the security of the proposed scheme against active and inactive attacks, we will use AVISPA software and HLPSL descriptor language.
In these networks, forging attacks are hard to detect, as the ID of the licensed card is forged in this attack. Now, let us assume the attacker is trying to get the card's secret key; to do this the attacker should solve the discrete logarithm for the elliptic curve. Given the resistance of the discrete logarithm for the elliptic curve, as outlined in Johnson [28] and Barker [29], the proposed scheme will be reliable against this attack.
3.1.1 Man-in-the-middle attack
In this attack, the attacker tries to destroy the communication channel between the card and the card reader. In this case, the attacker cannot extract any useful information that triggers the attack. If we assume that the attacker gets \({C}_{1}\) while exchanging, based on ECDLP, the attacker cannot get the private key to use it and communicate with the card reader and cannot calculate the correct X value if he/she uses an invalid private key for the card reader.
3.1.2 Replay attack
In this attack, the attacker tries to use a repeated message in the network and perform the authentication process. Since the random number is generated for each connection, the attacker cannot use repeated messages. As an example, imagine an attacker has received all the messages exchanged between the card and the card reader in one session. Now, the attacker wants to prove itself as permitted card in the new session by T, \({C}_{1}\) parameters from the previous session. The card reader then will be able to identify the attacker by \({C}_{1}\).
Figure 3 shows illegal card identification. Also, if the attacker wants to prove itself by \({C}_{2},R\) from the previous session as permitted card reader in new session, the card will be able to identify it by \({C}_{2}\) parameter.
As a result, the proposed protocol is resistant to replay attack. Figure 4 shows illegal card reader identification.
3.1.3 Mutual authentication
In the proposed protocol, if the value of X is equal to \({C}_{1}\), the card reader will be able to authenticate the card:
In addition, the card can also validate the card reader using Y and \({C}_{2}\) values if these two values are equal:
3.1.4 Confidentiality
Based on ECDLP, the attacker cannot retrieve the private key from the messages.
3.1.5 Anonymity
It can be said that anonymity is one of the subtypes of confidentiality. Since a new random number is generated at each step, the attacker cannot guess the private key and ID.
3.1.6 Forward security
If we assume that the attacker has acquired the private and public keys of the card with a physical attack, he cannot predict the previously exchanged messages of the card, because he does not know the random number generated and used.
3.1.7 Location privacy
The variety of messaging between the card and the card reader, as well as the rules in the ECDLP, make it very difficult for the attacker to track the card.
3.1.8 Data integrity
In data integrity, the data exchanged between card reader and card must not be changed by the attacker. In the proposed protocol, public and private keys have already been loaded in both card reader and card and keys including \({{C}_{1},{C}_{2},SK1}_{T},{SK2}_{T},{SK1}_{R},{SK2}_{R}\) have been generated by them at the authentication phase. This means that any change done by attacker on encrypted data will mismatch at the receiver side. Therefore, the attack will be detected. Because of this, the proposed protocol is strong enough against this attack and can guarantee the data integrity.
3.1.9 Denial of service attack
As no secret keys in card or even card reader in our proposed protocol is updated concurrently, it is then resistant to DoS attack [25, 30]. Also, imagine an attacker wants to down the authentication between the card and the card reader by DoS attack. As our proposed scheme has mutual authentication, it is then able to resist to DoS attack. To do that, the attacker must in fact change one of these keys: \({{SK1}_{T},SK2}_{T},{SK1}_{R},{SK2}_{R}\). However, this is an impossibility because of ECDLP. As a result, DoS attack is not possible on our proposed protocol.
3.1.10 Availability
As mentioned before, no secret keys in our proposed protocol are updated synchronously, and it can then run between the card and the card reader and is also available. Table 5 shows the security comparison between related protocols and the proposed method:
3.2 Performance
To evaluate the performance, we have compared our proposed method with similar recent research papers such as Alamr [3], Liao [16], Sowjanya [19] and Dang [21]. We estimated the computation costs, communication costs, data storage costs and the execution time of the elliptical curve point multiplication of authentication phase for each of the five methods, for both the card reader and card. In Table 6, we present some of the various symbols used in this section.
On the other hand, according to the methods proposed in NikooGhadam et al. and Koblitz et al. [31, 32], the complexity of time for implementation of various operational phases has been calculated using modular exponentiation. The results are specified in Table 7.
The comparison between five methods is shown in Table 8. Since all of the public and private keys and other main parameters are loaded into the card and card reader in the initialization phase, thus, the computational cost of the private and public keys and other parameters are zero. In the authentication phase of our method, the computational cost is 4 \({T}_{H}\) + 6 \({T}_{PM}\) for the card and card reader. Therefore, our proposed method has lower computational cost, when compared to other methods.
It is also possible to calculate the execution time of the most complex operations on elliptic curve, that is, the elliptic curve point multiplication in milliseconds. For instance, we assume that all of the related articles use an elliptic curve with an equal key length of 160 bits. The execution time of the elliptical curve point multiplication on 5 MHZ cards equals 0.064 s [33]. The running time of the elliptic curve point multiplication among the related protocols for both the card and the card reader is given in Table 9.
Also, in proposed protocol, the communication cost between tag and card reader at the authentication phase has been calculated by the message length calculation which was sent. In our proposed protocol, messages \({C}_{1}\), R, T,\({C}_{2}\) are exchanged between card and card reader at the authentication phase. As it is known that the elliptic curve has X and Y coordinates. If we imagine the elliptic curve length is 160 bits, we will then have 320 bits. Consequently, our communication cost will be: 320 + 160 + 160 + 320 = 960, whereas Alamr’s communication cost sum is 320 + 320 + 320 + 320 + 320 = 1600. Table 10 shows list of variables and their values in bits.
The communication cost among related protocols in authentication phase is shown in Table 11.
We have also calculated information storage cost for card reader and card in our proposed protocol. Cards must store parameters like \({P}_{{u}_{T}},{P}_{{r}_{T}},{P}_{{u}_{R}},P,n,H,a,b,q\) as they do in Alamr’s scheme. A parameter named H has been added to it, and the sum is then 2080 bits. Card reader’s cost is exactly similar to Alamr’s scheme. The only difference is that parameter H has been added to it. Parameter J indicates how many cards there are. Table 12 shows information storage cost among related protocols.
3.3 Simulation using AVISPA tool
The AVISPA simulation tool is an extensively used security verification software which checks whether the authentication protocol is SAFE or UNSAFE against any active and passive attacks. The high-level language supported by this tool is High-Level Protocol Specification Language (HLPSL) [19].
AVISPA software is deployed as a simulator to assess the security of different protocols and determine whether or not different security protocols are secure. For the proposed scheme, the authentication steps for all the main roles, the card and the card reader have been written in HLPSL, and finally, the input codes were entered into the AVISPA software. The output of the proposed scheme is secure confirming the security of the proposed scheme against various attacks. The role of writing for the card reader is shown in Fig. 5.
The role of writing for the card is shown in Fig. 6; in the end, the characteristics of the roles and the working session between them for authentication are given in Fig. 7.
Then, for each role, the written codes were entered into AVISPA software and a safe output was obtained by the software. Figure 8 shows the entered codes into the AVISPA software, and Figs. 9 and 10 display the output using OFDM and ATSE, respectively.
4 Conclusion
Using ECC in smart cards can be highly effective in maintaining information security in different networks. Medical networks are obvious examples in which patient information is of great importance. In this paper, we have presented a scheme based on the ECC, which has a lower computational and communication cost and also lower elliptic curve point multiplication running time compared to the other present protocols. Data storage cost has also been analyzed and examined in this proposed protocol. Security requirements such as mutual authentication, confidentiality, data integrity, availability, anonymity, forwards security, location privacy, avoiding forgery attack, avoiding replay attack, avoiding man-in-the-middle attack and avoiding DoS attack have been considered, which provide a reasonable security for RFID authentication in networks based on IoT. AVISPA software was also used for security analysis of the proposed protocol, and a safe output was obtained by the software. For future work, a hardware implementation can also be done in order to evaluate precise security and computational cost of the proposed method.
Availability of data and materials
Not applicable.
Abbreviations
- ECC:
-
Elliptic curve cryptography
- IoT:
-
Internet of things
References
J. Gubbi, R. Buyya, S. Marusic, M. Palaniswami, Internet of things (IoT): a vision, architectural elements, and future directions. Futur. Gener. Comput. Syst. 29(7), 1645–1660 (2013)
P.P. Ray, A survey on internet of things architectures. J. King Saud Univ. Comput. Inform. Sci. 30(3), 291–319 (2018)
A.A. Alamr, F. Kausar, J. Kim, C. Seo, A secure ECC-based RFID mutual authentication protocol for internet of things. J. Supercomput. 74(9), 4281–4294 (2018)
L. Atzori, A. Iera, G. Morabito, The internet of things: a survey. Comput. Netw. 54(15), 2787–2805 (2010)
Z. Zhang, Q. Qi, An efficient RFID authentication protocol to enhance patient medication safety using elliptic curve cryptography. J. Med. Syst. 38(5), 47 (2014)
H.-Y. Chien, Elliptic curve cryptography-based RFID authentication resisting active tracking. Wireless Pers. Commun. 94(4), 2925–2936 (2017)
H. Shen, J. Shen, M.K. Khan, J.-H. Lee, Efficient RFID authentication using elliptic curve cryptography for the internet of things. Wireless Pers. Commun. 96(4), 5253–5266 (2017)
M.S. Farash, O. Nawaz, K. Mahmood, S.A. Chaudhry, M.K. Khan, A provably secure RFID authentication protocol based on elliptic curve for healthcare environments. J. Med. Syst. 40(7), 165 (2016)
F. Rahman, M.Z.A. Bhuiyan, S.I. Ahamed, A privacy preserving framework for RFID based healthcare systems. Futur. Gener. Comput. Syst. 72, 339–352 (2017)
L. Gao, L. Zhang, M. Ma, Low cost RFID security protocol based on rabin symmetric encryption algorithm. Wireless Pers. Commun. 96(1), 683–696 (2017)
Y.K. Lee, L. Batina, I. Verbauwhede, EC-RAC (ECDLP based randomized access control): Provably secure RFID authentication protocol, in 2008 IEEE international conference on RFID, 2008, pp. 97–104: IEEE
S. Kavitha, P. Alphonse, Y.V. Reddy, An improved authentication and security on efficient generalized group key agreement using hyper elliptic curve based public key cryptography for IoT health care system. J. Med. Syst. 43(8), 260 (2019)
N. Koblitz, Elliptic curve cryptosystems. Math. Comput. 48(177), 203–209 (1987)
V.S. Miller, Use of elliptic curves in cryptography, in Conference on the theory and application of cryptographic techniques, (Springer, Berlin Heidelberg, 1985), pp. 417–426
P. Tuyls, L. Batina, RFID-tags for anti-counterfeiting, in Cryptographers’ Track at the RSA Conference, (Springer, Berlin Heidelberg 2006), pp. 115–131
Y.-P. Liao, C.-M. Hsiao, A secure ECC-based RFID authentication scheme using hybrid protocols, in Advances in Intelligent Systems and Applications-Volume 2: (Springer, Berlin Heidelberg, 2013), pp. 1–13
X. Yang, X. Yi, Y. Zeng, I. Khalil, X. Huang, S. Nepal, An improved lightweight RFID authentication protocol for internet of things, in International Conference on Web Information Systems Engineering, (Springer, Cham, 2018), pp. 111–126
K. Kaur, N. Kumar, M. Singh, M.S. Obaidat, Lightweight authentication protocol for RFID-enabled systems based on ECC, in 2016 IEEE Global Communications Conference (GLOBECOM), 2016, pp. 1–6: IEEE
K. Sowjanya, M. Dasgupta, S. Ray, An elliptic curve cryptography based enhanced anonymous authentication protocol for wearable health monitoring systems. Int. J. Inf. Secur. 19(1), 129–146 (2020)
X. Li, J. Peng, S. Kumari, F. Wu, M. Karuppiah, K.-K.R. Choo, An enhanced 1-round authentication protocol for wireless body area networks with user anonymity. Comput. Electr. Eng. 61, 238–249 (2017)
T.K. Dang, C.D. Pham, T.L. Nguyen, A pragmatic elliptic curve cryptography-based extension for energy-efficient device-to-device communications in smart cities. Sustain. Cities Soc. 56, 102097 (2020)
K.-H. Wang, C.-M. Chen, W. Fang, T.-Y. Wu, A secure authentication scheme for Internet of Things. Pervasive Mob. Comput. 42, 15–26 (2017)
C.-T. Li, D.-H. Shih, C.-C. Wang, Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Comput. Methods Programs Biomed. 157, 191–203 (2018)
V. Kumar, M. Ahmad, A. Kumari, A secure elliptic curve cryptography based mutual authentication protocol for cloud-assisted TMIS. Telematics Inform. 38, 100–117 (2019)
D. Noori, H. Shakeri, M. Niazi Torshiz, Scalable, efficient, and secure RFID with elliptic curve cryptosystem for Internet of Things in healthcare environment. EURASIP J. Inform. Security (2020). https://doi.org/10.1186/s13635-020-00114-x
P. Chinnasamy, S. Padmavathi, R. Swathy, S. Rakesh, Efficient data security using hybrid cryptography on cloud computing, in Inventive Communication and Computational Technologies, (Springer, Singapore, 2021), pp. 537–547
S.S. Dhanda, B. Singh, P. Jindal, Lightweight cryptography: a solution to secure IoT. Wirel. Pers. Commun. (2020). https://doi.org/10.1007/s11277-020-07134-3
D. Johnson, A. Menezes, S. Vanstone, The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 1(1), 36–63 (2001)
E. Barker, W. Barker, W. Burr, W. Polk, M. Smid, Recommendation for key management part 1: General (revision 3). NIST Spec. Publ. 800(57), 1–147 (2012)
Z. Zhao, A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem. J. Med. Syst. 38(5), 46 (2014)
M. Nikooghadam, A. Zakerolhosseini, M.E. Moghaddam, Efficient utilization of elliptic curve cryptosystem for hierarchical access control. J. Syst. Softw. 83(10), 1917–1929 (2010)
N. Koblitz, A. Menezes, S. Vanstone, The state of elliptic curve cryptography. Des. Codes Crypt. 19(2–3), 173–193 (2000)
P. Alexander, R. Baashirah, A. Abuzneid, Comparison and feasibility of various RFID authentication methods using ECC. Sensors 18(9), 2902 (2018)
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Noori, D., Shakeri, H. & Niazi Torshiz, M. An elliptic curve cryptosystem-based secure RFID mutual authentication for Internet of things in healthcare environment. J Wireless Com Network 2022, 64 (2022). https://doi.org/10.1186/s13638-022-02146-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-022-02146-y