Abstract
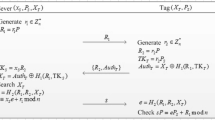
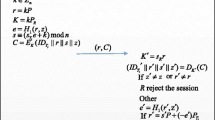
Medication errors are very dangerous even fatal since it could cause serious even fatal harm to patients. In order to reduce medication errors, automated patient medication systems using the Radio Frequency Identification (RFID) technology have been used in many hospitals. The data transmitted in those medication systems is very important and sensitive. In the past decade, many security protocols have been proposed to ensure its secure transition attracted wide attention. Due to providing mutual authentication between the medication server and the tag, the RFID authentication protocol is considered as the most important security protocols in those systems. In this paper, we propose a RFID authentication protocol to enhance patient medication safety using elliptic curve cryptography (ECC). The analysis shows the proposed protocol could overcome security weaknesses in previous protocols and has better performance. Therefore, the proposed protocol is very suitable for automated patient medication systems.



Similar content being viewed by others
References
Annual report. Technical report, London School of Hygiene and Tropical Medicine report, 2012.
Hung, Y. K., The study of adopting RFID technology in medical institute with the perspectives of cost benefit. International Medical Informatics Symposium in Taiwan, Taiwan, 2007.
Katz, J. E., and Rice, R. E., Public views of mobile medical devices and services: a US national survey of consumer sentiments towards RFID healthcare technology. Int. J. Med. Inform. 78(2):104–114, 2009.
Yu, C., Chen, C., Liao, P., and Lee, Y., RFID-based operation room and medicare system for patient safety enhancement—a case study of keelung branch. J. Inf. Manag. 15:97–122, 2008.
Leu, J. G., The benefit analysis of RFID use in the health management center—The experience in Shin Kong Wu Ho-Su Memorial Hospital. National Taiwan University, 2010.
Najera, P., Lopez, J., and Roman, R., Real-time location and inpatient care systems based on passive RFID. J. Netw. Comput. Appl. 34(3):980–989, 2011.
He, D., Chen, J., and Zhang, R., A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems 36(3):1989–1995, 2012.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Wei, J. G., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Pu, Q., Wang, J., and Zhao, R., Strong authentication scheme for telecare medicine information systems. J. Med. Syst. 36(4):2609–2619, 2012.
Chen, H.-M., Lo, J.-W., and Yeh, C.-K., An efficient and secure dynamic ID-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907–3915, 2012.
Zhao, Z., An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38:13, 2014.
Huang, H. H., and Ku, C. Y., A rfid grouping proof protocol for medication safety of inpatient. J. Med. Syst. 33(6):467–474, 2009.
Chien, H. Y., Yang, C. C., Wu, T. C., and Lee, C. F., Two rfid based solutions to enhance inpatient medication safety. J. Med. Syst. 35(3):369–375, 2011.
Peris-Lopez, P., Orfila, A., Mitrokotsa, A., and van der Lubbe, J. C., A comprehensive rfid solution to enhance inpatient medication safety. Int. J. Med. Inform. 80(1):13–24, 2011.
Chen, Y. Y., Wang, Y. J., and Jan, J. K., A secure 2G-RFID-Sys mechanism for applying to the medical emergency system. J. Med. Syst. 37(3):1–10, 2013.
Safkhani, M., Bagheri, N., and Naderi, M., On the designing of a tamper resistant prescription rfid access control system. J. Med. Syst. 36(6):3995–4004, 2012.
Wu, Z., Chen, L., and Wu, J., A Reliable RFID Mutual Authentication Scheme for Healthcare Environments. Journal of Medical Systems 37, 9917, 2013.
Picazo-Sanchez, P., Bagheri, N., and Peris-Lopez, P., Two RFID Standard-based Security Protocols for Healthcare Environments. Journal of Medical Systems 37, 9962, 2013.
Tuyls, P., and Batina, L., RFID-tags for Anti-Counterfeiting. In: Topics in cryptology-CT-RSA 2006, 115–131, 2006.
Batina, L., Guajardo, J., Kerins, T., Mentens, N., Tuyls, P., and Verbauwhede, I., Public-key cryptography for RFID-tags. Fifth annual IEEE international conference on PerCom workshops’ 07. IEEE, pp 217–222, 2007.
Lee, Y., Batina, L., and Verbauwhede, I., EC-RAC (ECDLP based randomized access control): provably secure RFID authentication protocol. In: 2008 I.E. international conference on RFID. IEEE, pp 97–104, 2008.
Liao, Y., and Hsiao, C., A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Networks, DOI: 10.1016/j.adhoc.2013.02.004, 2013.
Peeters, R., and Hermans, J. Attack on Liao and Hsiao’s Secure ECC-based RFID Authentication Scheme integrated with ID-Verifier Transfer Protocol. http://eprint.iacr.org/2013/399.pdf, 2013.
Chou, J.-S., A secure RFID authentication protocol to enhance patient medication safety using elliptic curve cryptography. J. Supercomput. 2014. doi:10.1007/s11227-013-1073-x.
Han, W., and Zhu, Z., An ID-based mutual authentication with key agreement protocol for multiserver environment on elliptic curve cryptosystem. Int. J. Commun. Syst. 2012. doi:10.1002/dac.2405.
He, D., Chen, J., and Hu, J., An ID-based client authentication with key agreement protocol for mobile client–server environment on ECC with provable security. Inf Fusion 13(3):223–230, 2012.
He, D., and Wang, D., Robust biometrics-based authentication scheme for multi-server environment. IEEE Syst. J. 2013. doi:10.1109/JSYST.2014.2301517.
He, D., Kumar, N., Khan, M. K., and Lee, J.-H., Anonymous two-factor authentication for consumer roaming service in Global Mobility Networks. IEEE Trans. Consum. Electron. 59(4):811–817, 2013.
Godor G, Giczi N, Imre S (2010) Elliptic curve cryptography based mutual authentication protocol for lowcomputational capacity RFID systems-performance analysis by simulations. In: IEEE international conference on wireless communications, networking and information security (WCNIS), 2010. IEEE, pp 650–657
Acknowledgments
The authors thank Prof. Jesse Ehrenfeld and anonymous reviewers for their valuable comments. This research was supported by National Natural Science Foundation of China (Nos. 51190093, 51309098, 200926) and the Ministry of Water Resources Public Welfare Special Industry Research (No. 201301039).
Conflict of interest
The author declares that he has no conflict of interest.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Patient Facing Systems
Rights and permissions
About this article
Cite this article
Zhang, Z., Qi, Q. An Efficient RFID Authentication Protocol to Enhance Patient Medication Safety Using Elliptic Curve Cryptography. J Med Syst 38, 47 (2014). https://doi.org/10.1007/s10916-014-0047-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0047-8