Abstract
Unmanned Aerial Vehicle (UAV) swarms not only expanded the application areas of UAVs but also brought more complex challenges to security. Both the data collected by UAVs and UAVs themselves are easy targets for hackers. Once a hacker has intercepted communication information or hijacked a UAV, it can cause the disclosure of information and even affect the normal flight of the UAV. In terms of authentication, existing research focuses on building peer-to-peer networks through devices that support blockchain deployments at the edge nodes to form blockchain networks. UAVs cannot run blockchains directly, so fog nodes need to be introduced to assist UAVs in achieving authentication. This paper proposes a UAV authentication solution based on the fog node-assisted blockchain. The solution incorporates smart contracts to ensure trust, along with on-chain registration and authentication for UAVs. In the design of this paper, the main use is made of fog nodes at the edge of each block. The fog nodes serve as agents to register and authenticate the UAVs in their area on the blockchain, thus enabling the authentication of UAVs in different fog node areas. In this paper, the analysis of gas consumption yields a total economic benefit cost of about \(\yen \) 12.77, which is negligible for the safety of the UAVs. Meanwhile, the paper compares the computational overheads, and within 10 UAVs, the computational overhead of this scheme is less than 50 ms, which is significantly lower than the other two schemes.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Clusters of UAVs need ground control base stations (GCS) and a communication network for exchanging information between them to work with each other to accomplish specific missions. With low cost, small size, ease of deployment, low maintenance costs, and high mobility, UAVs are now widely used in civil applications such as urban planning, engineering supervision, logistics, and distribution. Safety is therefore one of the main concerns of UAVs. For UAV clusters, it must be ensured that information can be communicated and shared in real time between UAV and UAV, and between UAV and GCS, and that the information sent and received must be reliable to further make real-time and effective decisions and collaborate safely.
In the context of UAV cluster cooperative operations, information connection channels need to be built between UAVs to form a mobile self-organizing UAV network. Compared with traditional mobile self-organizing networks, UAV networks have characteristics such as fast node movement, strong interference in the working environment, long working hours, and high real-time, which brings more complex security issues for UAV cluster collaboration [1]. At the same time, UAV technology has become a powerful data-gathering tool that can be used to acquire massive amounts of information. However, the accompanying challenge is that effective privacy protection mechanisms must be in place when sensitive information and confidential data are involved. Particularly in cases where data collected by UAVs may be subject to security threats, a data breach could trigger serious and immeasurable consequences. To prevent these threats, a series of measures need to be actively taken in UAV design and application. First, for the UAV itself, security measures must be enhanced to ensure that it is protected from the risk of hacking and remote control. Second, data transmission should be encrypted end-to-end to protect data from being stolen or tampered with during transmission. In addition, strict authentication and access control mechanisms should be established to ensure that only authorized personnel have access to sensitive information.
Authentication technology is the basic guarantee of system security, which provides a mechanism to verify and confirm the identity of users by identifying and authenticating their characteristics. The establishment of a complete authentication mechanism is the basis on which other access control policies can be implemented for resource requests within the system, thus fundamentally safeguarding and protecting the system. More attention should be given to the security of communication between UAVs [2].
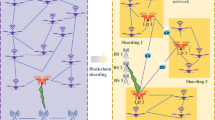
Blockchain is a distributed system for organizing, storing, and verifying data created to solve credit problems. Blockchain has developed at a rapid pace in recent years, and as such has been hailed as a disruptive technology for the technology revolution [3]. As a reliable distributed ledger technology, blockchain has a decentralized database system that allows any valid operation to be based on traceability and verification. In addition to its widespread application in cryptocurrencies, it has also attracted active participation from various industries due to its characteristics, such as immutability, openness, transparency, traceability, and ease of maintenance. Moreover, it is rapidly gaining traction in other popular research areas, such as distributed data storage and consensus mechanisms [4]. The structure of UAVs combined with blockchain is illustrated in Fig. 1.
Combining the relevance of a secure trusted and distributed identity process, blockchain-based identity technology is gradually being proposed. They mainly use blockchain’s secure authentication system to solve the problem of third-party breach of trust in traditional centralized authentication systems, designing and implementing a preliminary solution with interactivity and reliability. The application of blockchain technology breaks the barriers of existing authentication technologies, effectively solve the problems of key leakage, certificate management, collaborative authentication, and cross-domain authentication in the process of authentication, and quickly establishes trust between distributed authentication nodes and users while guaranteeing security, which is a forward-looking breakthrough of both theoretical value and practical significance. The main contributions of this paper are as follows:
-
(1)
This paper proposes an identity authentication model for fog node-assisted blockchain, which can ensure fast identity authentication among different UAV fleets.
-
(2)
This paper designs a trusted computing scheme to calculate the credibility of UAVs and fog nodes to ensure that both the UAVs involved in registration and the fog nodes aided in authentication are safe and reliable.
-
(3)
This paper analyzes the security and practicality of this scheme by experimentally calculating the gas consumption and the efficiency of UAV authentication.
Related work
UAV networks are very different from other wireless networks such as Mobile Adaptive Networks (MANETs) [5, 6] due to the greater node mobility and various security threats associated with UAV nodes. Therefore, existing MANET security solutions and other traditional wireless networks cannot be adapted to these networks. He et al. have explained the basic characteristics of UAV communications and identified the requirements for UAV security protocols in their article [7]. They have shown that traditional security techniques (e.g., anomaly detection) cause significant delays and therefore cannot be used for time-critical applications such as those in UAV networks [8, 9].
Although many security protocols have been designed in recent years, they are not sufficient to prevent common attacks [10]. Zhang et al. [11] proposed a lightweight certificate-based Authentication and Key Agreement scheme in combination with the characteristics of UAVs. However, the performance of the protocol is poor and only a few protocols have been compared. Srinivas et al. [12] proposed an anonymous lightweight user authentication mechanism in Internet of Drones (IoD) environments based on temporal credentials. However, Ali et al. pointed out that the protocol [13] is not resistant to traceability and stolen authentication attacks. Chen et al. [14] propose a direct anonymous proof with mutual authentication (MA-DAA) scheme for networked UAVs, however, as their scheme is based on a Trusted Platform Module (TPM), it leads to higher costs. In the literature [15], Abdullah et al. propose a lightweight security scheme for monitoring UAV networks, but their scheme can only ensure one-way authentication, not mutual authentication. The scheme in the article [16] is a certificate-free group key authentication protocol for untrusted UAV networks, however, their work is mainly based on bilinear pairing and elliptic curve cryptography (ECC) and is therefore not lightweight. In [17], the author proposed a context-aware and multi-service trust management system to meet the new requirements of the Internet of Things, but the system is not suitable for UAV networks. Du et al. [18] proposed a lightweight flight self-organizing network bidirectional identity authentication scheme based on an adaptive trust strategy, which selects the UAV with the highest trust degree from the UAV group and the ground control station for identity authentication.
The current technology involved in UAVs is information sharing between nodes [19], which raises the question of how individual nodes can trust other nodes and how much information nodes share to protect privacy. To solve this issue, the research community has proposed trust management mechanisms [20], which allow nodes to maintain trust and reduce the risk of communication and information sharing with malicious and compromised nodes. The motivation behind providing trust management mechanisms is to make UAV nodes robust to misbehaving and compromised nodes [21]. Therefore, trust mechanisms are introduced to remove security constraints. A dynamic trust management protocol (DTP) is proposed in the literature [22] for IoT-based applications. In DTP, each node acts as an autonomous node to manage trust in other nodes. A trustworthiness management mechanism (TMM-IOT) for social IoT is proposed in the article [23], the trust elements used in this mechanism are the feedback system, total number of transactions, relationship factor, trustworthiness, transaction factor, computational power, and centrality concept. The subjective model is also mentioned as having a delayed response. The target model suffers when a node is trustworthy to the whole network but may contain opinions from malicious or compromised nodes. In the article [24], an alternative trust management scheme is proposed to mitigate switching attacks using distributed trust management. However, a limitation of this scheme is that it relies solely on direct observation for trust assessment. An adaptive IoT trust measurement scheme is proposed in the article [25] which combines communication history and stereotypical reputation. The proposed scheme works by assessing the user’s trust value in the node. Furthermore, the scheme combines the user’s trust value with personal trust from the interaction history. A reliable and efficient system based on edge computing and blockchain is proposed in [26]. A new group agent policy with trust computing is designed to ensure the reliability of edge devices during the interaction and improve transmission efficiency.
Model design
The UAV authentication model based on fog node-assisted blockchain designed in this paper mainly includes the following three parts, as shown in Fig. 2.
System model
UAV fleet: While each UAV possesses a pair of public and private keys along with its unique Ethereum address, and each UAV is mapped to a different fog node, the requirement for fog nodes arises due to the absence of a direct link and interface between UAVs and smart contracts. Each UAV mainly queries the blockchain through the fog node. After the trusted centre verifies the identity of the UAV, the fog node mainly returns the verification structure to the device.
Fog node: The fog nodes are mainly located near the location of the UAVs, such as traffic lights deployed on roads, as a way to reduce the latency and response time of the system and maintain the operation of the blockchain. Each fog node has a pair of public and private keys and a unique Ethereum address. Each fog node is responsible for managing a set of UAVs flying within a certain radius. The main user of the fog node queries the ticket structure in the chain, verifies the identity of the UAV devices registered to the blockchain within the region, and assists in the mutual authentication between UAVs within the region.
Smart contracts and ledgers: Smart Contracts are mainly used as a ledger that holds authentication information to implement the query and authentication functions of the authentication service. The ledger mainly records the pseudonym, the real identity, the public key, the time limit of the public key, and the public dynamic parameters of the legitimate UAV. The public dynamic parameters here refer to one of the random factors.
Blockchain management centre (BMC): BMC is responsible for managing the identity of UAVs and enabling the registration of UAV devices. It is also the owner of the UAV identity registration contract and is responsible for generating trusted tickets for UAV authentication information. The main task of the BMC is to smoothly write information about the UAV device into the blockchain. UAVs that are registered through BMC are reliable.
Definition of programmed steps
The scheme in this paper consists of four main parts: reputation mechanism, key generation, registration phase, and authentication. The symbols and definitions of the main parameters involved are given in Table 1.
Reputation mechanism: The reputation mechanism is mainly used to assess the security of UAV and fog nodes. As a fog node is responsible for managing a group of UAVs in its area, the operation performed must be correct and trustworthy. The reputation mechanism enables the trust value of the fog node to be evaluated, the higher the trust value, the more likely it is to be selected as the representative fog node responsible for the registration of UAV.
Key generation: In this scheme, the elliptic curve algorithm is employed to sign some messages for authentication. The public and private keys utilized by the UAV, the fog node, and BMC are all generated mainly through the elliptic curve algorithm, and they all carry a pair of their respective Ethernet addresses (EA).
Registration phase: The registration phase is mainly done by the fog node. UAVs in the same region are managed by the same fog node. The fog node generates a unique address number for each UAV and then writes a hash of the address number and the UAV’s identity ID into the blockchain. After the UAV is registered, a registration token is generated by the private key.
Authentication phase: The authentication of UAVs is primarily the responsibility of the BMC. This stage is mainly to authenticate the identity of the UAVs that have been registered. When the BMC receives the registration information sent by the UAV, it will use a smart contract to judge the authenticity and integrity of the token therein.
Safety objectives
The security objectives to be achieved by the scheme designed in this paper are shown below.
Authenticity of identity: The UAVs can authenticate each other directly via pre-registered information on the blockchain. This ensures that there is no impersonation of identities.
Confidentiality: Confidentiality is concerned with ensuring the integrity of all data in communication.
Data integrity: Thanks to the introduction of blockchain technology, the consensus mechanism ensures that communication data is difficult to tamper with.
Anonymity: The true identity of each UAV should be protected, and anonymity used during communication. These anonymities should be updated before each new mission.
Non-repudiation: Non-repudiation means that the actions they have performed and the messages they have sent cannot be rejected between UAVs.
Robustness: Blockchain-based authentication schemes are effective against simulation and modification attacks due to their immutability and consistency, and perform well against replay attacks, man-in-the-middle attacks, and authentication table theft attacks due to the uniqueness of the identity registry and can effectively face those attacks that exist in wireless ad hoc networks.
Detailed authentication scheme
In this phase, first, the system calculates the credibility values of the UAVs and fog nodes. The BMC then generates public parameters for the subsequent authentication process, and then all UAVs involved in the mission should register with the BMC for the system to receive blockchain-assisted authentication services. As shown in Fig. 3, first, instead of the UAV, the fog node will initiate a registration or authentication request to the BMC. Second, the smart contract queries whether the UAV information has already been registered. Finally, if the UAV is not registered, the blockchain creates a new block for registration, and if it is already registered, the information of the UAV that needs to be authenticated is queried for authentication, and the result is returned to the fog node.
Credibility calculation
When a UAV has requested to join the system before, it is likely to have been maliciously attacked or has been kidnapped. When a malicious UAV keeps sending incorrect authentication requests to the blockchain network, the traffic on the blockchain network increases dramatically, which causes the blockchain node network to crash. That is why it must evaluate the credibility of the UAV device as a way to determine if the UAV is normal. Typically, the certification period is set to the amount of time it takes for the UAV swarm to complete a mission cycle to ensure that the trustworthiness of each UAV is assessed prior to the start of each mission. Before the UAV swarm executes a mission, unregistered UAVs need to complete the initial registration. The system calculates the trustworthiness value of the UAV based on the previously recorded UAV flight missions, as shown in the following Eq. (1). Where \(value_{U_{i}}(t)\) represents the credibility value of the UAV at moment t and c represents the number of reliable transactions. When the UAV has not yet been registered to the blockchain, the initial credibility value of the UAV is 0. When the UAV has been registered, the credit value is initialized to 1. From Eq. (1), it can be seen that the credibility value of the UAV also increases with the number of trusted transactions the UAV has made. Conversely, if the UAV fails to authenticate, \(value_{U_{i}}(t)\) is reduced by \(a(0<a<1)\). When the value of \(value_{U_{i}}(t)\)is negative, the blockchain will no longer accept requests from the UAV.
Before UAVs execute missions with the assistance of fog nodes, reliable fog nodes need to be selected to verify the identity of the UAVs and process the data collected by the UAVs. Therefore, it is crucial to select a reliable fog node capable of handling the UAV’s tasks, preferably one with a proven track record (i.e., a fog node with a good history). UAVs are evaluated and scored based on the relevant performance of the fog node. If the credibility value of a UAV is low, it is not involved in evaluating the credibility of the fog node. The credibility of the fog node is mainly calculated by its evaluation score and the UAV’s evaluation score of its credibility. The UAVs assessed for fog node reputation have been assessed for system reputation, so there is no significant impact on the UAV’s honesty in assessing fog node. \(ass_{U_{i}}(t)\) denotes the assessment of the fog node attributes by the UAV at time t. \(value_{U-fog}(t)\) denotes the reputation score of the fog node at time t, as shown in Eq. (2). valueFog(t) denotes the total reputation value assessed by the fog node at time t, as shown in Eq. (3).
Initialization phase
The steps are as follows:
-
(1)
The fog node selects a large prime n and defines a non-singular elliptic curve E(n). The curve consists of n points forming an additive group G of order q, where P is the generator.
-
(2)
The fog node selects a \(SK_{pub}\in Z_{q}^{*} \) as the private key and computes the public key of the system:
$$\begin{aligned} PK_{pub}=SK_{pub}\cdot P \end{aligned}$$(4) -
(3)
The system chooses three hash functions:\(h_{1}: \left\{ 0,1 \right\} ^{*} \longrightarrow Z_{q}^{*} \), \(h_{2}: \left\{ 0,1 \right\} ^{*} \longrightarrow \left\{ 0,1 \right\} ^{l} \), \(h_{3}: \left\{ 0,1 \right\} ^{*} \longrightarrow \left\{ 0,1 \right\} ^{k} \). Where l is the length of the identity and k is the length of the encrypted key.
-
(4)
The fog node is responsible for saving the private key and publishing the public parameters: \(\big \{n,q,P,PK_{pub},h_{1}, h_{2},h_{3} \big \} \).
Registration stage
The registration phase of the UAVs is mainly performed by the fog nodes. Each fog node has a unique Ethereum address \(Eads_{fog}\) generated by a public key. UAVs in the same region are registered uniformly by the fog node in that region. The fog node writes the hash of the UAV’s pseudo-identity \(AID_{i}\) and the hash of the address number of the region in which it is located to the blockchain via a smart contract.
-
(1)
UAV \(U_{i}\) picks a random number \(m\in Z_{q}^{*} \) and calculates the public key \(PK_{i}\), private key \(SK_{i}\), and anonymous identity \(AID_{i}\) of the UAV, represented by Eqs. (5), (6), and (7) respectively. \(U_{i}\) keeps its private key as a password and chooses a random number \(d_{i}\in Z_{q}^{*}\) as a private dynamic parameter and calculates a public dynamic parameter \(D_{i}\), represented by Eq. (8). The system uploads this dynamic parameter through the fog node to the book of authenticated identities to prepare for subsequent authentication.
$$\begin{aligned} PK_{i}= & {} SK_{i}\cdot P\end{aligned}$$(5)$$\begin{aligned} SK_{i}= & {} h_{1}(ID_{i}\parallel SK_{pub}\parallel m) \end{aligned}$$(6)$$\begin{aligned} AID_{i}= & {} ID_{i}\oplus h_{2}(SK_{i}\cdot PK_{pub}) \end{aligned}$$(7)$$\begin{aligned} D_{i}= & {} d_{i}\cdot P. \end{aligned}$$(8) -
(2)
First, the fog node generates an address number \(adsID=keccak256(number_{fog},Eads_{T})\) for the UAVs in its area, where \(number_{fog}\) is the area number of the fog node’s location and \(Eads_{T}\) is the Ether address of the BMC. Second, the fog node creates a transaction message through the elliptic curve encryption algorithm as shown in Eq. (9), which is shared among users within the blockchain. Finally, when the BMC receives an identity request from the fog node, it first decrypts Eq. (9) with its private key to obtain the address number of the UAV and the pseudo-identity of the UAV as shown in Eq. (10).
$$\begin{aligned}{} & {} Tra1=Enc(adsID,AID_{i})\end{aligned}$$(9)$$\begin{aligned}{} & {} Dec(Tra1)=(adsID,AID_{i}). \end{aligned}$$(10) -
(3)
The system verifies the UAV address number and whether there is registered identity information by means of the smart contract. First, the system verifies the identity \(AID_{i}\) of the UAV. If \(AID_{i}\) exists, the UAV has already been registered and the registration process is aborted; if \(AID_{i}\) does not exist but adsID exists, the UAV has not been registered. The blockchain will create a new block and broadcast Tra1 in the block to reach message sharing.
-
(4)
The fog node creates a ticket function through a smart contract to generate a ticket \(Ticket_{U_{i}}=(adsID,AID_{i},Eads_{fog},Eads_{TC},t)\) for the UAV device and sends the ticket to the BMC, where t is the time duration of the ticket. BMC writes the hash \(h_{3}(Ticket_{U_{i}})\) of the ticket to the blockchain through a contract to calculate the ticket hash function \(setHashTicket(\,)\), creates and shares with the fog node a transaction Tra2 as shown in Eq. (11), and the fog node shares Tra2 with the UAVs in its region.
$$\begin{aligned} Tra2=Enc(Ticket_{U_{i}}). \end{aligned}$$(11)
Certification stage
The authentication stage focuses on the mutual authentication of identities between UAVs that have already been registered.
-
(1)
When \(U_{i}\) receives a message \(M_{i}\), where \(M_{i}=\big \{AID_{i}\parallel T\parallel M_{i}\parallel f \big \} \), it first determines the identity of both parties. The UAV will first receive \(Ticket_{U_{i}}\) and \(M_{i}\) from the fog node, create a \(token_{U_{i}}=(adsID,Ticket_{U_{i}})\) via the contract function \(createToken(\,)\), and compute \(h_{3}(Token_{U_{i}})\). \(U_{i}\) computes \(f_{i}=d_{i}+SK_{i}\cdot h_{1}(PID_{i}\parallel T\parallel M_{i}) \), where T is the current timestamp. and sends \(f_{i}\) to fog node.
-
(2)
When a fog node receives a message sent to it, first, it checks whether the timestamp T is fresh or not as a way to judge the freshness of \(M_{i}\). Next, by invoking the smart contract, it gets \(PK_{i}\) and \(D_{i}\) of \(U_{i}\) in the authentication ledger and determines whether the formula \(f\cdot P=D_{i}+h_{1}(AID_{i}\parallel t\parallel M_{i})\cdot PK_{i}\) holds. If it fails, the message is incorrect; if the formula holds, then the authentication of \(U_{i}\) passes and the correct address number adsID and \(token_{U_{i}}\) are obtained. The following formula is judged:
$$\begin{aligned} \begin{aligned} f\cdot P&= d_{i}\cdot P+SK_{i}\cdot h_{1} (AID_{i}\parallel t\parallel M_{i})\cdot P \\&= D_{i}+PK_{i}\cdot h_{1} (AID_{i}\parallel t\parallel M_{i}). \end{aligned} \end{aligned}$$(12) -
(3)
If adsID does not exist in the blockchain, then the authentication fails; if adsID exists, the integrity of \(Ticket_{U_{i}}\) in the token \(token_{U_{i}}\) of the UAV needs to be verified. The system calculates the hash value \(h_{3}(Ticket_{U_{i}})\) of \(Ticket_{U_{i}}\) and compares it with the \(h_{3}(Ticket_{U_{i}})\) written in the blockchain at the time of registration; if \(h_{3}(Ticket_{U_{i}})\,\)=\(\,h_{3}(Ticket_{U_{i}})\), then the authentication of the UAV is successful and the BMC returns the authentication result to the UAV via the fog node.
-
(4)
After the UAV identity is successfully confirmed, the fog node generates a blockchain ticket \(BTicket_{T}=BTicket_{T}(adsID,Eads_{T},T)\) through the smart contract function creatBTicket() and calculates its hash value \(h_{3}(BTicket_{T})\). It is written into the blockchain through \(setHashTicket(\,)\). The system will create a transaction Tra3 as shown in Eq. (13) and share it in the blockchain.
$$\begin{aligned} Tra3=h_{3}(BTicket_{T}). \end{aligned}$$(13)
Smart contracts
The main structure of a smart contract is defined as shown below.
-
(1)
The fog node is responsible for the on-chain action of UAV registration and is the creator and deployer of the UAV registration contract. The fog node generates an address number adsID for the region where the UAV is located and is mainly responsible for determining whether the address number of the UAV and its pseudo-identity \(AID_{i}\) exist on the blockchain.
-
(2)
The creation of a smart contract will consume a certain amount of gas. This paper only allows the system-specified Ethereum account address to be called.
-
(3)
Two main subjects are defined in the smart contract, \(U_{i}\) and Ticket. \(U_{i}\) refers to a certain UAV, which is mainly responsible for storing its own \(AID_{i}\). The main information of the UAV ticket is stored in Ticket, including the Ethernet address \(Eads_{U_{i}}\) of the UAV, the Ethernet address number \(adsID_{i}\) of the region where the UAV is located, the Ethernet address \(Eads_{fog}\) of the fog node, and the pseudo-identity \(AID_{i}\) of the UAV.
-
(4)
A log of the UAV device’s transaction information is recorded in real-time in the smart contract to facilitate listening to events.
Reputation value calculation contract
The reputation value calculation contract mainly includes two parts: the reputation value calculation contract of the UAV, and the reputation value calculation contract of the fog node. The reputation value calculation contract is mainly used to evaluate the reputation of fog nodes and UAV nodes in the system. When the UAV is successfully registered for the first time, the system will give the UAV an initial trust value of 0. When the UAV’s reputation value is lower than 0, the blockchain will no longer serve the UAV. Algorithm 1 mainly calculates the trust value of UAVs and fog nodes. Among them, \(value(\,)\) is mainly to calculate the reputation value of the UAV. By judging whether the message is a UAV that exists in the blockchain. If it is, and it is a newly registered UAV, it has an initial reputation value of 0; if it is successfully registered in the past, the reputation value is increased or decreased according to the transaction situation. \(valueFog(\,)\) mainly calculates the trust value of fog nodes. This paper defines an array \(score[\,]\), which is responsible for storing the reputation score of fog nodes. The system calculates the reputation value of fog nodes by triggering the event \(valueScore(\,)\).
UAV registration contract
Algorithm 1 contains four main contracts, the contract to write UAV information to the blockchain, the contract to verify that the UAV is registered on the blockchain, the ticket generation contract, and the contract to write ticket information to the blockchain. The contract for writing the UAV to the blockchain is primarily responsible for recording the address number of the area where the UAV is located, the pseudo-identity of the UAV, and the Ether address number of the fog node on the blockchain.
The function \(setUAV(number_{fog},AID,Eads_{fog})\) is mainly used to write the new UAV information to the blockchain. Firstly, the system determines whether the user writing to the blockchain is a fog node or not. Then, the hash \(h_{3}(adsID)\) of the address number adsID of the area where the fog node is located and the hash \(h_{3}(AID_{i})\) of the pseudo-identity \(AID_{i}\) of the UAV are stored in the array \(HashUAV[\,]\). The function \(checkUAV(AID_{i},adsID)\) is mainly to verify that the UAV is registered on the blockchain. \(creatTicket(number,AID_{i},Eads_{T},Eads_{fog})\) is a ticket generation function that mainly generates the registered ticket information after the successful registration of the UAV. Function \(setHashTicket(adsID,AID_{i},Eads_{T},Eads_{fog})\) is to write the hash of the ticket information into the blockchain. The main data written include the Ethernet address number of the region where the UAV is located, the pseudo-identity of the UAV, the Ethernet address number of BMC, and the Ethernet address number of the fog node.
UAV certification contract
Algorithm 3 below is the contract for the UAV certification phase. The authentication contract for the fog-node-based UAV consists of three main parts, the contract for creating the registration token, the contract for ticket generation after successful authentication, and the contract for hash calculation of the ticket. This phase is primarily responsible for verifying the integrity and authenticity of the identity information of the UAVs registered on the chain by the BMC. After the fog nodes query the information of the UAVs on the chain, the identity information of the UAVs is judged, so as to achieve the purpose of authenticating the identity information of the UAVs.
\(createToken(adsID,AID_{i},Eads_{T},Eads_{fog})\) is mainly to create the registration token token. The token information mainly includes: the Ethernet address number of the area where the UAV is located, and the ticket information of the UAV. \(createBTicket(adsID,AID_{i},Eads_{T},Eads_{fog})\) is mainly for the successful addition of the UAV’s identity to the blockchain, BMC generates the ticket information for the transaction saved on the blockchain. \(setHashBTicket(adsID,Eads_{T})\) is to generate the hash of the blockchain ticket, which is then written to the blockchain.
System analysis
To ensure the safe and effective operation of the UAV network and the security and trustworthiness of the services, some necessary security requirements need to be met in this scheme. This section analyzes the security of the proposed authentication scheme and compares it with several existing authentication schemes against common network attacks. The following analysis is performed for these security requirements.
Safety analysis
Theorem 1: Ensuring the authenticity of the UAV’s identity. The authentication scheme designed focuses on authentication through fog nodes. Since the UAV has no direct access to the blockchain information, the fog node is required to query the blockchain for information about the nodes on both sides of the authentication. The authentication of both parties can be achieved through the fog nodes, and the scheme is secure enough under the assumption that there are enough fog nodes and that they are not corrupted.
Theorem 2: Ensures the integrity of the UAV’s identity. The paper has designed the authentication to be carried out mainly on the blockchain. When authenticating between UAVs, the information of both parties is authenticated through the fog nodes, so once the identity information of the UAVs etc. is uploaded to the blockchain, due to the nature of the blockchain, the identity information cannot be tampered with in unless an attacker can destroy more than half of the fog nodes, but that is very difficult to achieve.
Theorem 3: Ensures the privacy of the UAV’s identity. In this solution, each UAV is authenticated with an anonymous identity, and due to the nature of the hash its true identity is only owned by the UAV itself, thus avoiding the theft of identity information by other UAVs.
Theorem 4: Non-repudiation of transactions. In the solution, as the information of each transaction is recorded and uploaded to the blockchain, it cannot be tampered with or denied.
Theorem 5: Provides ticket security. All the information involved in the transaction is hashed and written into the blockchain, so the notes written into the blockchain are tamper-proof, thus ensuring the security of the tickets.
Theorem 6: Trusted UAV provided. In the trust scheme, both the UAV and the fog node perform a reputation value calculation, through which the reliability and security of the authentication system is maintained.
Attack model analysis
The scheme proposed in this paper can effectively resist the following attacks.
Spoofing attacks: In the scheme designed in this paper, the real identity ID and private key of the UAV, and the address number of the area where it is located, are not likely to be leaked, so an attacker cannot obtain the identity information of the UAV from the blockchain thereby forging the identity of the legitimate UAV.
Man-in-the-middle attack: The scheme designed in this paper is mainly based on the difficulty of the ECC problem of the elliptic curve encryption algorithm, so whether the UAV is successfully registered on the blockchain or not, a malicious attacker cannot crack its private key.
Denial of service attack: According to the uniqueness of the blockchain, data in the blockchain will be shared at multiple points, so it will not cause the problem of a single point of failure, and even if one node has a problem, the whole system will not be affected.
System requirements
The proposed scheme in this paper demonstrates scalability in comparison to Semal’s scheme discussed in literature [27], resulting in optimized system performance and enhanced efficiency in data processing and decision-making for UAV applications. In UAV operations, diverse tasks often require the use of different UAV types, leading to potential interoperability issues that can impact the entire system’s performance. To address this challenge, the scheme in this paper utilizes fog nodes to manage trust values among UAVs. By centralizing the management and coordination of trust values at fog nodes, the scheme in this paper bridges the trust value gap between different types of UAVs and facilitates seamless sharing of trust values and cross-mission communication. The scheme in this paper offers several advantages over existing registration and Public Key Infrastructure (PKI) approaches, including reducing the risk of a single point of failure and the risk of potential privacy breaches. Additionally, as the number of UAVs increases, data congestion is minimized, ensuring smoother data flow and seamless system operation.
Compared with the schemes proposed in the literature [27] and [28], the scheme proposed in this paper has a fog node dependency though, and the operation and performance of the system can be affected by the operational status of the fog nodes. In rare cases, if a large number of fog nodes are faulty or down, it may lead to an increase in the communication delay and overhead of the system. However, given the extremely low likelihood of such a scenario occurring in real-world situations, the operation of the system is generally unaffected. On the other hand, the reliance on fog nodes helps to reduce the burden on cloud servers. Usually, cloud servers are responsible for storing and processing large-scale data, but directly transferring all UAV data to the cloud may lead to network congestion and increased processing latency. By introducing fog nodes, some of the data processing and computation can take place near the endpoints, allowing the cloud server to focus more on advanced data analysis and decision-making, thus increasing the efficiency and throughput of the entire system. Dependence on fog nodes plays a key role in system design, as shown in Table 2.
Simulation and discussion
In Fig. 4, different malicious UAVs probabilities are set to verify the effectiveness of the proposed scheme. The experiments set the malicious UAV probability between 10\(\%\) and 70\(\%\), which is due to the fact that considering the actual situation there is generally not a large number of malicious UAVs because it requires a huge monetary cost. It can be seen that as the probability of malicious UAVs increases, the effectiveness of the scheme for identifying malicious UAVs remains at a stable level, and some small differences are acceptable considering the effect of random factors. Additionally, it is evident that as the number of edge device to UAV interactions increases, it does not significantly impact the recognition rate.
It can be seen in Fig. 5 that the trustworthiness of the UAV increases linearly with the number of good interactions. However, the number of different reliable transactions does not have much effect on the growth rate. This is because the number is so small that it has a negligible effect on the trust score. Nevertheless, the trustworthiness of the UAV increases as long as interactions with non-malicious behaviors are performed, which is in line with the proposed idea. In addition, the experiment selected different initial trust values for comparison, and it can be seen that different initial trust values determine the starting point of UAV trust building, so the impact of this factor on trustworthiness should be taken into account in practical situations.
Feasibility analysis
In the whole algorithm flow of this paper, there are three transaction information Tra1, Tra2 and Tra3 written into the blockchain. Where \(Tra1=Enc(adsID,AID_{i})\) is the operation transaction that encrypts the address number and pseudo-identity of the UAV. \(Tra2=Enc(Ticket_{U_{i}})\) is the transaction information after encrypting the ticket of the UAV device. \(Tra3=h_{3}(BTicket{T})\) is the transaction information of the blockchain ticket generated by the UAV after passing the authentication. The storage overhead of the Enc() encryption operation is 256 bits. The hash operation \(h_{3}()\) converts the ticket data of the blockchain of any length into a binary number of fixed lengths of 32 bits. The three transactions, therefore, occupy the storage space of the blockchain as shown in Table 3.
Efficiency analysis
Although performing manipulations on the blockchain is arithmetic intensive and incurs cost consumption (gas execution consumption), a blockchain-based solution guarantees the reliability of the authentication. The solution in this paper focuses on an Ethereum blockchain built on a virtual machine, Linux Ubuntu 16.04. Smart contracts are mainly written in Solidity language as a way to analyze the cost consumption of the article design solution. In this article, the contract is tested on Rinkeby and the smart contract is deployed after successful testing. Based on the current time the price of Ether is: Ether is approximately equal to \(2.0377\times 10^{4} \) CNY. The paper analyzed the cost of the smart contract creation and execution function, as shown in Table 4.
Fig. 6 clearly illustrates the cost consumption of each smart contract.
From Fig. 6 it can be seen that the creation of the ticket contract has the highest cost consumption, followed by the initialization phase, the authenticated ticket generation contract, the creation of the token contract, the authenticated ticket hash contract, the registered ticket contract, the registered ticket hash contract, the UAV reputation calculation contract, and the fog node reputation calculation contract, respectively. The consumption costs of these contracts are approximate: \(\yen \)2.46, \(\yen \)2.18, \(\yen \)1.81, \(\yen \)1.80, \(\yen \)1.66, \(\yen \)1.37, \(\yen \)0.84, \(\yen \)0.43, and \(\yen \)0.25 respectively. This gives a total monetary cost of approximately $12.77 for this scenario.
Although there is some monetary consumption associated with this scenario, this is negligible relative to the current value of the UAV and the economic benefits generated by the UAV application.
In Fig. 7 the overhead costs required by the schemes for different numbers of UAVs are compared, for 1–10 UAVs, with the schemes of literature [27] and literature [28]. The comparison graph shows that the authentication scheme designed in this paper has a lower computational overhead than the other two schemes for different numbers of UAVs. In the particular environment of UAV networks, the lower the computational overhead, the higher the security of the whole system. Therefore, the scheme in this paper is better than the other two compared schemes and has more reliable security.
Conclusions
This paper focuses on designing an authentication scheme suitable for the UAV scenario through the decentralized and tamper-evident nature of blockchain. Through the fog node as the central node, it assists the UAVs to register on the blockchain as a way to join the blockchain system. When the registered UAVs on the blockchain authenticate with each other, the system queries the registered transaction information on the blockchain through the fog node, thus achieving fast and efficient authentication. After the security analysis, and experiments, it can conclude that the solution in this paper is somewhat costly but can meet the basic security needs of UAVs. After comparing the overheads with the other two solutions, this solution is less expensive than the other two solutions for different numbers of UAVs.
Data availability
The data supporting the results of this study can be found in Google Finance at https://www.google.com/finance/quote/ETH-USD, from which the data in Fig. 6 is derived.
References
Alzahrani BA, Chaudhry SA, Barnawi A, Al-Barakati A, Alsharif MH (2020) A privacy preserving authentication scheme for roaming in IoT-based wireless mobile networks’’. Symmetry. https://doi.org/10.3390/sym12020287
Yunmok S (2018) Noh, Juhwan, Choi, Jaeyeong, Kim, and Yongdae, "GyrosFinger: Fingerprinting drones for location tracking based on the outputs of MEMS gyroscopes". Acm Trans Privacy Secur 21(5):1–25. https://doi.org/10.1145/3177751
Gai K, Guo J, Zhu L, Yu S (2020) Blockchain Meets Cloud Computing: A Survey. IEEE Communications Surveys & Tutorials 22(3):2009–2030. https://doi.org/10.1109/COMST.2020.2989392
Shammar EA, Zahary AT, Al-Shargabi AA (2021) A Survey of IoT and Blockchain Integration: Security Perspective. IEEE Access 9:156114–156150. https://doi.org/10.1109/ACCESS.2021.3129697
Gai K, Guo J, Zhu L, Yu S (2020) Blockchain Meets Cloud Computing: A Survey. IEEE Communications Surveys & Tutorials 22:2009–2030. https://doi.org/10.1109/COMST.2020.2989392
Al-Turjman F, Ever YK, Ever E, Nguyen HX, David DB (2017) Seamless key agreement framework for mobile-sink in IoT based cloudcentric secured public safety sensor networks. IEEE Access 5:24617–24631. https://doi.org/10.1109/ACCESS.2017.2766090
He D, Chan S, Guizani M (2016) Communication security of unmanned aerial vehicles. IEEE Wireless Commun 24(4):134–139. https://doi.org/10.1109/MWC.2016.1600073WC
Hassija V, Chamola V, Krishna DNG, Guizani M (2020) A distributed framework for energy trading between UAVs and charging stations for critical applications. IEEE Trans Veh Technol 69(5):5391–5402. https://doi.org/10.1109/TVT.2020.2977036
Hassija V, Saxena V, Chamola V (2020) Scheduling drone charging for multi-drone network based on consensus time-stamp and game theory. Comput Commun 149:51–61. https://doi.org/10.1016/j.comcom.2019.09.021
Lin C, He D, Kumar N, Choo K-KR, Vinel A, Huang X (2018) Security and privacy for the Internet of drones: Challenges and solutions. IEEE Commun Mag 56(1):64–69. https://doi.org/10.1109/MCOM.2017.1700390
Zhang Y, He D, Li L, Chen B (2020) A lightweight authentication and key agreement scheme for Internet of drones. Comput Commun 154:455–464. https://doi.org/10.1016/j.comcom.2020.02.067
Srinivas J, Das AK, Kumar N, Rodrigues JJ (2019) Tcalas: Temporal credential-based anonymous lightweight authentication scheme for Internet of drones environment. IEEE Trans Veh Technol 68(7):6903–6916. https://doi.org/10.1109/TVT.2019.2911672
Ali Z, Hussain S, Rehman RHU, Munshi A, Liaqat M, Kumar N, Chaudhry SA (2020) Itssaka-ms: An improved three-factor symmetrickey based secure aka scheme for multi-server environments. IEEE Access 8:107993–108003. https://doi.org/10.1109/ACCESS.2020.3000716
Chen L, Qian S, Lim M, Wang S (2018) An enhanced direct anonymous attestation scheme with mutual authentication for network-connected UAV communication systems. China Commun 15(5):61–76. https://doi.org/10.1109/CC.2018.8387987
Abdallah MZ, Ali J. Mišić, Mišić VBJ (2019) Efficient security scheme for disaster surveillance UAV communication networks. Information. https://doi.org/10.3390/INFO10020043
Semal K, Markantonakis and Akram RN (2018) A certificateless group authenticated key agreement protocol for secure communication in untrusted UAV networks. In: Proc. IEEE/AIAA 37th Digital Avionics Syst. Conf., pp. 1-8. https://doi.org/10.1109/DASC.2018.8569730
A Y B S , A A O , B D Z , et al (2013) Trust management system design for the Internet of Things: A context-aware and multi-service approach[J]. Comput Secur 39(1):351-365. https://doi.org/10.1016/j.cose.2013.09.001
Du X, Li Y, Zhou S et al (2022) ATS-LIA: A lightweight mutual authentication based on adaptive trust strategy in flying ad-hoc networks. Peer-to-Peer Netw Appl. https://doi.org/10.1007/s12083-022-01330-7
P. J. Werbos (2019) The new ai: Basic concepts, and urgent risks and opportunities in the internet of things,” in Artificial Intelligence in the Age of NeuralNetworks and Brain Computing. Elsevier, pp. 161-190. https://doi.org/10.1016/B978-0-12-815480-9.00008-6
Din U, Guizani M, Kim B-S, Hassan S, Khan MK (2018) Trust management techniques for the internet of things: a survey. IEEE Access. https://doi.org/10.1109/ACCESS.2018.2880838
Sfar R, Natalizio E, Challal Y, Chtourou Z (2018) A roadmap for security challenges in the internet of things. Digital Commun Netw 4(2):118–137. https://doi.org/10.1016/j.dcan.2017.04.003
Bao, F, Chen I-R (2012) Dynamic trust management for internet of things applications. In: Proceedings of the 2012 international workshop on Selfaware internet of things. ACM. https://doi.org/10.1145/2378023.2378025
Nitti M, Girau R, Atzori L (2014) Trustworthiness management in the social internet of things. IEEE Trans Knowl Data Eng 26(5):1253–1266. https://doi.org/10.1109/TKDE.2013.105
Mendoza CV, Kleinschmidt JH (2015) Mitigating on-off attacks in the internet of things using a distributed trust management scheme. Int J Distrib Sens Netw 11(11):859731. https://doi.org/10.1155/2015/859731
Son H, Kang N, Gwak B, Lee D (2017) An adaptive iot trust estimation scheme combining interaction history and stereotypical reputation. In: Consumer Communications & Networking Conference (CCNC), 14th IEEE Annual. IEEE 2017:349–352. https://doi.org/10.1109/CCNC.2017.7983132
Zhang L, Zou Y, Wang W et al (2021) Resource allocation and trust computing for blockchain-enabled edge computing system - ScienceDirect[J]. Comput Secur. https://doi.org/10.1016/j.cose.2021.102249
Semal B, Markantonakis K, Akram RNA, certificateless group authenticated key agreement protocol for secure communication in untrusted UAV networks[C]. (2018) IEEE/AIAA 37th Digital Avionics Systems Conference (DASC). IEEE 2018:1–8. https://doi.org/10.1109/DASC.2018.8569730
Tan Y, Wang J, Liu J et al (2022) Blockchain-Assisted Distributed and Lightweight Authentication Service for Industrial Unmanned Aerial Vehicles[J]. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2022.3142251
Acknowledgements
This work was supported by The National Natural Science Foundation of China (62176088), the Special Project for Key R &D and the Promotion of Science, Technology Department of Henan Province (222102210272, 222102210007, 222102210062, and 232102211009), the Key Technology Research and Development Project of Henan Province under Grant (222102210055), the Postgraduate Education Reform and Quality Improvement Project of Henan Province under Grant (YJS2022JD26), the Major Science and Technology Projects of Henan Province, and the Major Public Welfare Projects of Henan Province (201300210400), Kaifeng Science and Technology Development Plan (2201010).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Du, X., Tao, S., Yuan, K. et al. A blockchain authentication scheme for UAV-aided fog computing. Complex Intell. Syst. 10, 1689–1702 (2024). https://doi.org/10.1007/s40747-023-01232-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40747-023-01232-y