Abstract
We consider a natural generalization of Jackson and Wolinsky’s (J Econ Theory 71:44–74, 1996) connections model where the quality or strength of a link depends on the amount invested in it and is determined by a non-decreasing function of that amount. The information that the nodes receive through the network is the revenue from investments in links. We prove that in this most general version of the connections model, the only possibly non-empty efficient networks, in the sense of maximizing the aggregate profit, are still the all-encompassing star and the complete network, with the sole and rare exception of a highly particular case where there is a draw between the all-encompassing star, the complete network and a whole range of a particular type of nested split graph structures intermediate between them.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Jackson and Wolinsky (1996) introduce a connections model of network formation where nodes invest in links with other players in order to receive valuable information. Each node embodies a piece of information of worth v for any other node if it is received intact. However, connection through a link is not perfect as it involves a certain friction or decay, i.e., only a fraction \(\delta \) (\(0<\delta <1\)) of the information transmitted through a link reaches the other node. The formation of each link requires an investment of a fixed amount c by each of the two nodes involved. A noteworthy result is that in this setting the only efficient architectures, that is, the only ones that can maximize the aggregate payoff or net value of the network, i.e., the sum of the information received by all players minus the total cost of the network, are the all-encompassing star, the complete network or the empty network, depending on the configuration of values of the two parameters, \(\delta \) and c. The same occurs in the non-cooperative version of this model in Bala and Goyal (2000), where links can be formed unilaterally.
The question arises of whether this result is robust to more general settings.Footnote 1 The proof of this result is straightforward, but it is unclear whether it is dependent on the simplicity of the link-formation technology in the model: only one type of link of fixed strength and fixed cost. To answer this question, we address in this paper the question of efficiency in a natural generalization of Jackson and Wolinsky’s connections model, by assuming that the quality or strength of a link, i.e., the fidelity level of the transmission through it, is never perfect, but depends on the amount invested in it. A link-formation technology determines the quality of the resulting link as a function of investment. Formally, a technology is a non-decreasing function whose range is [0, 1), i.e., an increase in investment in a link cannot decrease its strength, but however much is invested in a link transmission is never perfect. The revenue from investments in links is the information that the nodes receive through the network. We prove that even in this general setting, virtually, whatever the technology, the only possibly efficient networks are the empty network, the all-encompassing star and the complete network.
Olaizola and Valenciano (2019) prove constructively that, under rather general conditions for models extending the connections model of Jackson and Wolinsky (1996) and for any link-formation technology, any network with positive net value is dominated by a weighted nested split graph network (NSG-network) of particular type called dominant nested split graph network (DNSG-network).Footnote 2 The generalized connections model considered here meets those conditions, so that result applies to the current model and provides the basic point of support for the result obtained. As any network is dominated by a connected DNSG-network, the strategy of the proof consists of showing that any network of this type other than the complete network and the all-encompassing star, which are both particular cases of connected DNSG-networks, is strictly dominated by one of them, by a complete network or by an all-encompassing star. In fact, we prove that this is so with one rare exception, that of a highly particular case of a “supertie” where there is a tie between the all-encompassing star, the complete network and a whole range of a particular type of nested split graph structures intermediate between them. Nevertheless, we show that by adding the requirement of minimizing the total cost of the network renders this exception impossible.
The rest of the paper is organized as follows. Section 2 introduces basic notation and terminology. Section 3 introduces the generalized connections model. Section 4 addresses the question of efficiency and characterizes efficient networks. Section 5 deals with the issues of existence and uniqueness of efficient networks and the rarity of a supertie. Section 6 briefly reviews some related literature, and Sect. 7 gives some concluding comments emphasizing the results obtained and pointing out some lines of further research. Proofs are relegated to “Appendix.”
2 Preliminaries
An undirected weighted graph consists of a set of nodes\( N=\{1,2,\ldots ,n\}\) with \(n\ge 3\) and a set of links specified by a symmetric adjacency matrix\(g=(g_{ij})_{i,j\in N}\), with \(g_{ij}\in [0,1)\) and \(g_{ii}=0\). An undirected weighted graph g can also be represented by a map \(g:N_{2}\rightarrow [0,1)\), where \(N_{2}\) denotes the set of all subsets of N with cardinality 2. In what follows, \( {\underline{ij}}\) stands for \(\{i,j\}\) and \(g_{{\underline{ij}}}\) for \( g(\{i,j\}) \) for any \(\{i,j\}\in N_{2}\). When the codomain of g is \( \{0,1\}\) instead of [0, 1), i.e., \(g_{{\underline{ij}}}\) only takes the values 0 or 1, we say that g is non-weighted and it can be specified as a set of links \(S\subseteq N_{2}\). In particular, the non-weighted underlying graph\(S_{g}\) of a weighted graph g is \( S_{g}:=\{{\underline{ij}}\in N_{2}:g_{{\underline{ij}}}>0\}\). When \(g_{ {\underline{ij}}}>0\) we say that a link of weight\(g_{{\underline{ij}}}\) connects i and j. \(N^{d}(i,g):=\{j\in N:g_{{\underline{ij}}}>0\}\) denotes the set of neighbors of node i, and its cardinality, \(\left| N^{d}(i,g)\right| \), is the degree of node i. Note that \(i\notin N^{d}(i,g)\). N(i, g) denotes the set of nodes connected to i by a path, i.e., a sequence of distinct nodes s.t. every two consecutive nodes are connected by a link. The length of a path is the number of links that it contains, i.e., the number of nodes minus 1. A graph is connected if any two nodes are connected by a path. A component of a graph is a maximal connected subgraph.
Undirected graphs, weighted or not, underlie a variety of situations where actual links mean some sort of reciprocal connection or relationship. Such structures are commonly referred to as networks. Behind a network there is always a graph as a highly salient feature, so we transfer the notions introduced so far for graphs to networks and refer the new ones directly to networks.
The empty network is the one for which \(g_{{\underline{ij}}}=0\) for all \({\underline{ij}}\in N_{2}\). A complete network is one where \(g_{ {\underline{ij}}}>0\) for all \({\underline{ij}}\in N_{2}\).Footnote 3 An all-encompassing star consists of a network with \(n-1\) links in which one node (the center) is connected to each of the remaining nodes by a link. One important class of networks is that of those whose underlying graph is a “nested split graph.”These networks exhibit a strict hierarchical structure where nodes can be ranked by their number of neighbors.
Definition 1
A nested split graph (NSG) is an undirected (weighted or not) graph g such that
A nested split graph network (NSG-network for brief) is a network whose underlying graph is nested split. In terms of the adjacency matrix, such graphs have a simple structure. It is a symmetric matrix such that for a certain numbering of the nodes, each row consists of a sequence of nonzero entries (apart from those in the main diagonal) followed by zeros, and the number of nonzero entries in each row is no greater than that in the preceding row. Such a numbering of the nodes is a ranking numbering . In what follows, nodes are always assumed to be numbered like this in NSG-networks. Nodes in an NSG-network are partitioned in NSG-classes, each containing the nodes with the same number of neighbors. Isolated nodes, i.e., with no neighbors, form the trivial class, which plays no relevant role.
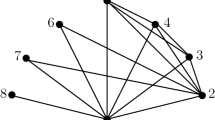
Example 1
Figure 1 shows the adjacency matrix of a 12-node NSG-network with 6 NSG-classes: \(K_{1}=\{1,2\}\) with 11 neighbors, \(K_{2}=\{3\}\) with 8 neighbors, \(K_{3}=\{4\}\) with 5 neighbors, \(K_{4}=\{5,6\}\) with 4 neighbors, \(K_{5}=\{7,8,9\}\) with 3 neighbors, \(K_{6}=\{10,11,12\}\) with 2 neighbors.
3 A generalized connections model
In Jackson and Wolinsky’s (1996) connections model, all links have the same strength \({\overline{\delta }}\) (\(0<{\overline{\delta }}<1\)), and the formation of a link requires an investment of a fixed amount \({\overline{c}}>0\) by each of the two nodes involved. Thus, the question of an efficient investment (in the sense of maximizing the aggregate payoff) by the node players is equivalent to the question of an efficient investment by a planner making use of a technology that requires an investment of at least \(2 {\overline{c}}\) in a link for the link actually to form. Such a technology can be formalized as a map \(\delta : {\mathbb {R}} _{+}\rightarrow [0,1)\) s.t. if \(c\ge 0\) is the amount invested in a link, \(\delta (c)\) is the strength of the resulting link and is given by
We consider the natural generalization of Jackson and Wolinsky’s connections model that results from replacing the discrete technology in that model (1) by any link-formation technology that meets the following definition:
Definition 2
A link-formation technology is a non-decreasing map \( \delta : {\mathbb {R}} _{+}\rightarrow [0,1)\) s.t. \(\delta (0)=0\).
The interpretation is clear: If c is the amount invested in a link to connect two nodes, \(\delta (c)\) is the level of fidelity of the transmission of information through it. More precisely, \(\delta (c)\) is the fraction of information flowing through the link that remains intact.Footnote 4 Flow occurs only through links invested in (\(\delta (0)=0\)), an increase in the investment in a link cannot decrease its strength, but perfect fidelity in transmission between different nodes is never reached (\(\delta (c)<1\)).
Thus, if nodes in a set \(N=\{1,2,\ldots ,n\}\) can be connected by links according to a link-formation technology \(\delta \), a link-investment vector is an \(n(n-1)/2\)-vector, \(\underline{{\mathbf {c}}}=(c_{{\underline{ij}}})_{ {\underline{ij}}\in N_{2}}\), where \(c_{{\underline{ij}}}\ge 0\) denotes the investment in link \({\underline{ij}}\in N_{2}\) through which the fidelity level is \(\delta (c_{{\underline{ij}}})\).Footnote 5 Investing \(c>0\) in a link determines its strength, \(\delta (c)\), so when \(\delta (c)>0\) we often refer to such a link as a c-link. Thus, investment \(\underline{{\mathbf {c}}}\) yields network \(g^{\underline{{\mathbf {c}}}}\), namely
For link-investment vector \(\underline{{\mathbf {c}}}=(c_{{\underline{ij}}})_{{\underline{ij}}\in N_{2}}\), a node i thus receives the fraction from another node’s worth v that reaches i through the best possible route in the weighted network \(g^{\underline{{\mathbf {c}}}}\), as in Jackson and Wolinsky (1996). Let \({\mathcal {P}}_{ij}(g^{\underline{{\mathbf {c}}}})\) denote the set of paths in \(g^{\underline{{\mathbf {c}}}}\) connecting i and j. For a path \(p\in {\mathcal {P}}_{ij}(g^{\underline{{\mathbf {c}}}})\), let \(\delta (p)\) denote the resulting fidelity level determined by the product of the fidelity levels through each link in that path, i.e., if \( p=ii_{2}i_{3}\ldots i_{k}j\), \(\delta (p)=\delta (c_{\underline{ii_{2}}})\delta (c_{\underline{i_{2}i_{3}}})\ldots \delta (c_{\underline{i_{k}j}})\). Thus, i values information originating from j that arrives via p by \(v\delta (p). \) If information is routed via the best possible route from j to i, then i’s valuation of the information originating from \(j\ne i\) is
and i’s overall revenue from \(g^{\underline{{\mathbf {c}}}}\) is
For all \(i,j\in N,i\ne j,\) let \({\overline{p}}_{ij}\) denote an optimal path connecting them, i.e., such that \(\delta ({\overline{p}} _{ij})=\max _{p\in {\mathcal {P}}_{ij}(g^{\underline{{\mathbf {c}}}})}\delta (p);\) that is
The netvalue of the network resulting from a link-investment vector \(\underline{{\mathbf {c}}}=(c_{{\underline{ij}} })_{{\underline{ij}}\in N_{2}}\) is the aggregate payoff, i.e., the total value of the information received by the nodes minus the total cost of the network:
4 Efficiency
Let \(\underline{{\mathbf {c}}}\) and \(\underline{{\mathbf {c}}}^{\prime }\) be two link-investment vectors and \(v(g^{\underline{{\mathbf {c}}}})\) and \(v(g^{ \underline{{\mathbf {c}}}^{\prime }})\) as defined by (3): \(g^{ \underline{{\mathbf {c}}}}\)dominates\(g^{\underline{{\mathbf {c}}} ^{\prime }}\) (or \(\underline{{\mathbf {c}}}\) dominates \(\underline{{\mathbf {c}}} ^{\prime }\)) if \(v(g^{\underline{{\mathbf {c}}}})\ge v(g^{\underline{{\mathbf {c}} }^{\prime }})\), and \(g^{\underline{{\mathbf {c}}}}\)strictly dominates \(g^{\underline{{\mathbf {c}}}^{\prime }}\) (or \(\underline{{\mathbf {c}}}\)strictly dominates \(\underline{{\mathbf {c}}}^{\prime }\)) if \(v(g^{ \underline{{\mathbf {c}}}})>v(g^{\underline{{\mathbf {c}}}^{\prime }})\). Network \( g^{\underline{{\mathbf {c}}}}\) (or link-investment vector \(\underline{{\mathbf {c}} }\)) is said to be efficient if it dominates any other.
Efficiency can be seen as a desirable outcome when links are formed in a decentralized context by node players who invest in links. Alternatively, efficiency can be seen as the goal of a planner investing in links with the objective of maximizing social welfare, i.e., the aggregate revenue received by the nodes minus the total cost of the network.
Olaizola and Valenciano (2019) prove constructively that under rather general conditions, within a wide class of extensions of the connections model of Jackson and Wolinsky (1996) and for any link-formation technology, any network with a positive net value is dominated by a particular type of weighted NSG-network. Such dominantNSG-networks show certain features in addition to those specified in Definition 1. Like any undirected graph, a weighted NSG-network g is completely specified by the triangular matrix above the main diagonal of 0-entries of its adjacency matrix, \(T(g)=(g_{ij})_{i<j}\). Formally, this leads to the following definition:
Definition 3
A dominant nested split graph network (DNSG-network) is a connected weighted NSG-network g such that, for a ranking numbering of the nodes, in T(g): (i) each row (of entries to the right of the main diagonal of the adjacency matrix) consists of a rightward non-decreasing sequence of positive entries followed by zeros; (ii) all positive entries in the first row are greater than or equal to any other entries; and (iii) from the second row down on, nonzero entries in the same column form a non-decreasing sequence.
Thus, a DNSG-network consists of an all-encompassing central star centered at node 1 formed by the strongest links (i.e., first row and column of the adjacency matrix) plus some additional links between spoke nodes of that star (i.e., remaining nonzero entries on the northwest of the adjacency matrix) according to the pattern specified in Definition 3. As an example, Fig. 2 shows an adjacency matrix that follows this pattern.Footnote 6
In order to make the paper basically self-contained, we briefly review the family of connections models considered in Olaizola and Valenciano (2019). As in the current model, a link-formation technology (as per Definition 2) rules the formation of costly weighted links among a set of nodes, each of them endowed with value v. The value that one node receives from another is what it receives through the strongest path connecting them, and what it receives through a path is a fraction of v proportional to the “strength” of their connection through that path. Olaizola and Valenciano (2019) make the following assumptions about the “strength” of the connection of any two nodes in a weighted network through a path: (i) the strength of a link is its weight; (ii) the strength of the connection of i with j is the same as that of j with i; (iii) the strength of the connection through a path is non-decreasing w.r.t. the increase of the strength of its links; (iv) the strength of the connection through a path is not stronger than the connection of any two nodes in it through the subpath. Then, the net value that a weighted network generates is the sum of the value received by all the nodes minus the total cost of the network.Footnote 7
It is straightforward to check that the model described in Sect. 3 satisfies all these conditions, under which the dominance of weighted DNSG-networks is established in Olaizola and Valenciano (2019). We omit the very easy detailed checking here to avoid a trivial digression. On the other hand, the constructive proof of the result in Olaizola and Valenciano (2019) consists of an algorithm that generates a DNSG-network that dominates the initial network by rearranging the links of any network whose net value is positive, perhaps disposing of some of them. The procedure consists basically of forming a star with the strongest links and adding the weakest of the remaining available links at each stage only if adding it improves the connection of the two worst connected nodes in the network. It is proved that the resulting DNSG-network dominates the initial network. Nevertheless, that network may include superfluous links between spoke nodes of the initial star that can be eliminated without decreasing the net value of the network. In this case, a simple procedure enables to refine the result and produce a DNSG-network that dominates the initial network and contains no superfluous links connecting spoke nodes of the initial star. That is, the elimination of any link would cause a decrease in the net value of the network.Footnote 8
Therefore, the result applies, and we have the following:
Proposition 1
If the net value is given by (3), for any investment \( \underline{{\mathbf {c}}}\), network \(g^{\underline{{\mathbf {c}}}}\), given by (2), is dominated either by the empty network or by a connected DNSG-network where no link connecting spoke nodes of the central star can be eliminated without decreasing the net value of the network.
This is the starting point for the proof of the main result in this paper, which requires several steps. Before proceeding with it, we give the outline of the proof: Given that any network with a positive net value is dominated by a connected DNSG-network, Definition 3 specifies a particular type of NSG-structure among which an efficient network is to be found if efficient non-empty networks do actually exist. Thus, the strategy of the proof consists of showing that any DNSG-network other than a complete network and an all-encompassing star is strictly dominated by one of them.Footnote 9 To that end, Proposition 1 is first refined by narrowing the class of dominant connected DNSG-networks among which an efficient network is to be found if a non-empty efficient network actually exists. We show that attention can be constrained to the subclass of simpleDNSG-networks (Propositions 2 and 2’), among which only those exhibiting two particular architectures can be efficient (Proposition 3 and Corollary 1). Propositions 4 and 5 establish necessary conditions for a complete network and an all-encompassing star to be efficient. (Both are particular, extreme cases of the two especial architectures obtained in Corollary 1.) Proposition 6 establishes that unless a rare condition holds, only an all-encompassing star or a complete network among the two particular architectures obtained in Corollary 1 can be efficient. Then, the result is finally established: The only possible architectures of a non-empty efficient network are the complete network and the all-encompassing star network, unless a rare condition holds (Theorem 1).
The following result refines Proposition 1 and enables us to confine our attention to a simpler class of DNSG-networks.
Proposition 2
For any efficient connected DNSG-network with a positive net value and no superfluous links, there is another connected DNSG-network, \( g^{\underline{{\mathbf {c}}}}\), with the same underlying graph, no superfluous links and the same net value satisfying the following conditions, where \( {\widehat{c}}\) is any value in \(\arg \max _{c>0}(2v\delta (c)-c)\):
-
(i)
For all \(i,j\ne 1\) s.t. \(c_{{\underline{ij}}}\ne 0:c_{ {\underline{ij}}}={\widehat{c}}\).
-
(ii)
For all j\(\ne 1\) in the NSG-class of node 1 (i.e., with \(n-1\) neighbors\():c_{{\underline{1j}}}={\widehat{c}}\).
-
(iii)
For all \(i,j\ne 1:\)\(c_{{\underline{1i}}}\le c_{{\underline{1j}}}\) if and only if \(\left| N^{d}(i;g^{\underline{{\mathbf {c}}} })\right| \ge \left| N^{d}(j;g^{\underline{{\mathbf {c}}}})\right| \).
Proposition 2 refines Proposition 1 by specifying a class of DNSG-networks, among which an efficient DNSG-network is to be found for any technology for which a non-empty efficient network actually exists. Given that all links not involving central node 1 and those connecting node 1 with nodes with as many neighbors as node 1 in an efficient DNSG -network are only used by the two nodes that each of them connects, they must all maximize \(2v\delta (c)-c\). Therefore, all such links can be replaced by \({\widehat{c}}\)-links, with \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) without altering the net value of the network. Note that for such links to exist for a technology \(\delta \) it is necessary that \(2v\delta (c)-c>0\) holds for some c, but this is not sufficient, and nor they need to be unique if they do exist. Links of the central star connecting its center with spoke nodes with different numbers of neighbors must receive different investments, and the greater the number of neighbors the smaller the investment. By contrast, those connecting its center with spoke nodes with the same number of neighbors are proved either to necessarily receive the same investment (when they are not neighbors) or to be replaceable by links of the same strength without altering the net value.
Therefore, any efficient connected DNSG-network with a positive net value has the same net value as a simpler connected DNSG-network that satisfies the conditions in Proposition 2, which motivates the following definition:
Definition 4
A simple DNSG-network is a connected DNSG-network with no superfluous links such that: (i) all links connecting pairs of nodes other than 1 and all those connecting node 1 with nodes with \(n-1\) neighbors receive the same investment \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c);\) (ii) links of node 1 with nodes that belong to the same NSG-class (i.e., with the same number of neighbors) receive the same investment, and the smaller the number of neighbors the greater the investment is.
In terms of investments, the pattern of the link-investment matrix of a simpleDNSG-network is represented in Fig. 3 for an NSG-network with an underlying graph identical to that of Example 1, where there are 6 NSG-classes, \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) and \({\widehat{c}}<c_{2}<c_{3}<c_{4}<c_{5}<c_{6}\).
In the seminal papers of Jackson and Wolinsky (1996) and Bala and Goyal (2000), the complete network and the all-encompassing star emerge as efficient structures. Note that simple DNSG-networks include complete networks (all entries \(>0\), except those in the main diagonal) and all-encompassing stars (nonzero entries in the first row and column and no more nonzero entries) as extreme cases. Note also that in a simple complete network all pairs of nodes are connected by links of the same strength \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\), and in a simple all-encompassing star network all links are of the same strength.
Proposition 2 can thus be reformulated like this:
Proposition 2’
(Proposition 2 reformulated) If \( g^{\underline{{\mathbf {c}}}}\) is an efficient connected DNSG-network with a positive net value and no superfluous links, then there is a simple DNSG-network \(g^{\underline{{\mathbf {c}}}^{\prime }}\) with the same underlying graph and the same net value.
As a corollary of the following proposition shows, it is possible to further constrain attention to the only two particular types of simple DNSG-network (other than the complete network and the all-encompassing star) that can be efficient.
Proposition 3
If \(g^{\underline{{\mathbf {c}}}}\) is an efficient simple DNSG-network with a positive net value, then \(g^{\underline{{\mathbf {c}}}}\) has links of at most two different strengths.
Notice that given the precise structure of simple DNSG-networks, the only ones with all links of the same strength are the complete network (all pairs of nodes connected by \({\widehat{c}}\)-links for some \({\widehat{c}} \in \arg \max _{c>0}(2v\delta (c)-c)\)) and the all-encompassing star of links of the same strength. For those with only two levels of investment in their links, one level must be \({\widehat{c}}\) (connecting some of the spoke nodes). But then there must be other links of greater strength. This leaves only two types of simple DNSG-networks which only have two levels of investment in their links \(c_{1}={\widehat{c}}\) and \(c_{2}>{\widehat{c}}\), all of which are members of the family specified by the following definition, which also assigns a notation to them which is used to conclude the proof of the main theorem.
Definition 5
If \(1\le k\le n\), \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) and \(g^{ \underline{{\mathbf {c}}}_{k}^{**}}\) are defined in terms of the triangular matrix\(\ (c_{ij})_{i<j}\) associated with the investments \( \underline{{\mathbf {c}}}_{k}^{*}\) and \(\underline{{\mathbf {c}}}_{k}^{**}\) given by
where \(c_{2}>{\widehat{c}}\).
If \(k=1\), \(g^{\underline{{\mathbf {c}}}_{1}^{*}}=g^{\underline{{\mathbf {c}}} _{1}^{**}}\) is an all-encompassing star, while if \(k=n\), \(g^{ \underline{{\mathbf {c}}}_{n}^{*}}=g^{\underline{{\mathbf {c}}}_{n}^{**}}\) is a complete network of \({\widehat{c}}\)-links. If \(1<k<n\), \(g^{\underline{ {\mathbf {c}}}_{k}^{*}}\) is a simple DNSG-network with three NSG-classes of cardinality \(\#K_{1}=1\) with \(n-1\) neighbors, \( \#K_{2}=k-1\) with \(k-1\) neighbors and \(\#K_{3}=n-k\) with 1 neighbor (Fig. 4a), unless\(k=2\), because \(g^{\underline{{\mathbf {c}} }_{2}^{*}}\) is a non simple star as it is formed by one \( {\widehat{c}}\)-link and \(n-1\)\(c_{2}\)-links. By contrast, \(g^{\underline{ {\mathbf {c}}}_{k}^{**}}\) is a simple DNSG-network with two NSG-classes of cardinalities \(\#K_{1}=k\) with \(n-1\) neighbors and \( \#K_{2}=n-k\), with k neighbors (Fig. 4b), unless\(k=n-1\), because \(g^{\underline{{\mathbf {c}}}_{n-1}^{**}}\) is a non simple complete network as it is formed by \({\widehat{c}}\)-links and only one \(c_{2}\)-link.Footnote 10
Note that for any of these structures to be efficient a necessary condition is \(2v\delta ({\widehat{c}})-{\widehat{c}}\le 2v\delta (c_{2})^{2},\) i.e.,
Thus, Proposition 3 yields the following:
Corollary 1
The only possibly efficient simple DNSG-networks are \(g^{ \underline{{\mathbf {c}}}_{k}^{*}}\)\((k\ne 2)\) and \(g^{\underline{{\mathbf {c}}}_{k}^{**}}\)\((k\ne n-1)\) for some k\((1\le k\le n)\).
The following propositions establish necessary conditions for the efficiency of a complete network and an all-encompassing star network.
Proposition 4
For a complete network \(g^{\underline{{\mathbf {c}}}}\) to be efficient, the following conditions are necessary:
-
(i)
For all \({\underline{ij}}\in N_{2}\), \(c_{{\underline{ij}}}\in \arg \max _{c>0}(2v\delta (c)-c)>0\).
-
(ii)
For all \({\underline{ij}}\in N_{2},\) and all \(k\ne i,j:\)\( 2v\delta (c_{{\underline{ki}}})\delta (c_{{\underline{kj}}})\le 2v\delta (c_{ {\underline{ij}}})-c_{{\underline{ij}}}\).
Proposition 5
For an all-encompassing star network to be efficient, the following conditions are necessary:
-
(i)
All links receive the same investment \(c_{n}^{*}\) s.t.
$$\begin{aligned} c_{n}^{*}\in \arg \max _{c>0}(2v\delta (c)+(n-2)v\delta (c)^{2}-c). \end{aligned}$$(5) -
(ii)
Additionally, if \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)>0\),
$$\begin{aligned} 2v\delta (c_{n}^{*})^{2}\ge 2v\delta ({\widehat{c}})-{\widehat{c}}, \end{aligned}$$(6)for all \(c>0\).
Note that, in general, under the minimal assumptions made on the technology, the existence of an optimal complete network or an optimal star network is not guaranteed, as the set \(\arg \max _{c>0}(2v\delta (c)-c)\) may be empty. The same may occur for the \(\arg \max \)-set where \(c_{n}^{*}\) is taken according to (5). Moreover, even if it does exist, uniqueness is not guaranteed as these sets may not be singletons.Footnote 11 There may be various efficient complete networks that combine different link-investments in \(\arg \max _{c>0}(2v\delta (c)-c)\). The highly special case may even occur in which
for some \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) and some \( c_{n}^{*}\) satisfying (5). In this case, there is a supertie: The complete network and the all-encompassing star and a whole range of particular intermediate DNSG-structures (\(g^{\underline{{\mathbf {c}}}_{k}^{**}}\), \(k=1,2,\ldots ,n\), in fact) may be efficient as is presently shown. In fact, it turns out that unless this very special coincidence occurs the only possible non-empty efficient simple DNSG-networks are the complete network and the all-encompassing star as the following proposition shows.
Proposition 6
The only possibly efficient simple DNSG-networks are the complete network and the all-encompassing star network, except if (7) holds for some \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) and some \(c_{n}^{*}\) s.t. (5). If (7) holds for a technology \(\delta \), all \(g^{\underline{ {\mathbf {c}}}_{k}^{**}}\)\((k\ne n-1)\) are efficient if their same net value is positive.
The last part of Proposition 6 is clear. If (7) holds for a technology \(\delta \), the three equal terms in (7) are the contributions to the net value of \(g^{\underline{{\mathbf {c}}} _{k}^{**}}\)\((k=1,2,\ldots ,n)\) of the connection of different pairs of nodes, namely \(2v\delta ({\widehat{c}})-{\widehat{c}}\) for those connected by \( {\widehat{c}}\)-links, \(2v\delta (c_{n}^{*})-c_{n}^{*}\) for those connected by \(c_{n}^{*}\)-links and \(2v\delta (c_{n}^{*})^{2}\) for those indirectly connected through the central star, i.e., \(k+1,\ldots ,n\) (Fig. 4b).
We now proceed to put together the steps set out so far, so as to prove the main result:
Theorem 1
The only possible efficient networks are the empty network, a complete network and an all-encompassing star network, unless (7) holds for any \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) and any \( c_{n}^{*}\) such that (5).
As we have seen, the \(\arg \max \)-sets from which \({\widehat{c}}\) and \(c^{*}\) are picked may not be singletons. This means that efficient networks that yield the same net value may have different costs. This difference may be particularly important for a planner. This suggests the possibility of strengthening the notion of efficient network by adding the condition of minimizing the cost of the network.
Theorem 1 can then be adapted as follows:
Theorem 2
The only possible efficient networks of minimal cost are the empty network, the complete network of minimum cost, i.e., with
and an all-encompassing star network of minimum cost, i.e., with
5 Existence, uniqueness and rarity of the supertie
In this section, we examine the issues of the existence and uniqueness of efficient networks, along with the rarity of the occurrence of the supertie.
5.1 Existence
In order to be as general as possible, the only assumptions made here about the technology are that links are costly and their conductivity non-decreasing with investment. As a result, we obtain only necessary conditions for an investment/network to be efficient. Nevertheless, there may not actually be any efficient networks, as the following trivial example shows.
Example 2
Consider a variant of the seminal model of Jackson and Wolinsky (1996), where the available technology is given by:
where \({\overline{c}}>0\), \(0<{\overline{\delta }}<1\) and \(2v{\overline{\delta }}-2 {\overline{c}}>0\). That is, the only difference is that \(\delta (2{\overline{c}} )=0\) instead of \({\overline{\delta }}.\) In this case, a complete network cannot be efficient for an obvious reason: \(\max _{c>0}(2v\delta (c)-c))\) does not exist. The same goes for the star.
Obviously, the continuity of \(\delta \) suffices to guarantee the existence of an optimal star and an optimal complete network, and consequently the existence of an efficient non-empty network if \( \max _{c>0}(2v\delta (c)-c)>0\) or \(\max _{c>0}(2v\delta (c)+(n-2)v\delta (c)^{2}-c)>0.\)
As for efficiency along with minimal cost, continuity of \(\delta \) also ensures the compactness of the \(\arg \max \)-sets in (8) and (9), and consequently, \({\widehat{c}}\) and \(c_{n}^{*}\) are well-defined by (8) and (9).
5.2 Uniqueness
Nevertheless, even assuming continuity, the uniqueness (up to a permutation of the labels of the nodes) of an efficient network is not guaranteed as both \(\arg \max \)-sets may contain more than one value. An optimal complete network is unique only if \(\arg \max _{c>0}(2v\delta (c)-c)\) is a singleton, and this is certain if \(\delta \) is strictly concave as well as continuous, but concavity does not suffice to guarantee it, as the following example shows:
Example 3
Consider the following 3-parametric family of technologies, piecewise linear and concave (no strictly):
where parameters \({\widehat{c}}_{\min }\), \(c^{*}\) and k are s.t. \(0< {\widehat{c}}_{\min }<c^{*}<2v-k\) and \(k<2v\). Figure 5 shows the graph of a technology in this family.
A technology in the family of Example 3
It is easy to check that for any technology in this family the following holds
Therefore, any complete network where any pair of nodes are connected by links of strength within the interval \([{\widehat{c}}_{\min },c^{*}]\) is optimal. Whether the complete network or all-encompassing stars are efficient depends on \(k\lessgtr 2v\delta (c^{*})^{2}\), and a supertie occurs if \(k=2v\delta (c^{*})^{2}\).
An optimal all-encompassing star is unique (up to the identity of the central node) only if \(\arg \max _{c>0}(2v\delta (c)+(n-2)v\delta (c)^{2}-c)\) is a singleton, and this is certain if \(\delta \) is continuous and in addition \(2v\delta (c)+(n-2)v\delta (c)^{2}-c\) is strictly concave, which is certain if both\(\delta (c)\) and \(\delta (c)^{2}\) are strictly concave.
Efficiency along with minimal cost of a complete network or a star network implies its uniqueness. Thus, continuity is sufficient to guarantee uniqueness unless, in addition to a supertie, the cost of the optimal star and complete also coincide, i.e., \(c_{n}^{*}=\frac{n}{2}{\widehat{c}}\) holds.
5.3 Rarity of a supertie
As for the occurrence of a supertie (7), it should be noticed that it is not just a tie between the net values optimal complete networks and optimal all-encompassing stars. The following example illustrates the possibility and rarity of the supertie.
Example 4
Consider the following biparametric family of technologies piecewise linear and continuous, perhaps the simplest that can be thought of:
where parameters v, \({\overline{c}}\) and \({\overline{\delta }}\) are s.t. \(0< {\overline{c}}<2v{\overline{\delta }}\). (Otherwise, a link that only connects two nodes is not worth its cost.) The conductivity/strength of a link increases linearly up to a saturation point at \(({\overline{c}},{\overline{\delta }})\), i.e., at cost \({\overline{c}}\) and saturation level \({\overline{\delta }}\), beyond which it remains constant no matter how much is invested in the link. Figure 6 represents \(\delta (c)\), \(2v\delta (c)\) and c.
Note that
Whether the optimal all-encompassing star \(g^{*}\) or any optimal complete network \(g^{\triangle }\) is efficient depends on their net values. The net value of an optimal complete network \(g^{\triangle }\) is
while that of an optimal star is
From this, it follows easily that
Thus, on the boundary \(2v{\overline{\delta }}(1-\overline{\delta })={\overline{c}}\) separating the regions where only the complete network or the all-encompassing star is efficient, a supertie occurs, i.e., \(2v{\widehat{\delta }}-{\widehat{c}}=2v\overline{\delta }-{\overline{c}}=2v\delta ^{*}-c^{*}=2v\overline{\delta }^{2}\). Figure 7 shows (for \(v=1,n=10\)) the regions of values of the two parameters, \({\overline{c}}\) and \({\overline{\delta }}\), separated by thick lines, where the efficient network for the corresponding technology is the complete network, the star or the empty network. For technologies in this family whose saturation \(({\overline{c}}, {\overline{\delta }})\) occurs within region I, the efficient networks are complete; for those whose saturation occurs within region II, the efficient networks are all-encompassing stars, while for those whose saturation occurs within region III, the only efficient network is the empty one.Footnote 12
6 Related literature
Since the seminal papers of Jackson and Wolinsky (1996) and Bala and Goyal (2000), there has been a growing branch of economic literature that draws up models of network formation. In this brief review, we concentrate preferentially on publications stemming from or in the wake of these models, where agents derive utility from their direct and indirect connections by investing in links, and focus on those most closely related to the model studied in this paper.Footnote 13
Nested split graph networks were first brought into network economics by König et al. (2014). Olaizola and Valenciano (2019), establishing the dominance of NSG-networks in a very general connections model, lay the groundwork for the results obtained in this paper. Bloch and Dutta (2009) introduce endogenous link strength in a connections model, opening up an interesting line of research. Their paper was in fact the one that most inspired our work. Bloch and Dutta replace Jackson and Wolinsky’s discrete technology by a function that determines the strength of a link as a function of the players’ investments in it. They assume that a unit of resource limits the players’ investments and that technology is an additively separable and convex function, i.e., they assume non-decreasing returns to investment. We instead only assume technology to be a non-decreasing function and no budget constraint, hence the different results. Bloch and Dutta prove that the star is the only stable architecture and the only efficient one. Deroian (2009) adopts a similar approach, but in directed communication, i.e., links are directed. As in Bloch and Dutta (2009), in equilibrium agents concentrate their investment on a single link. He establishes that the complete wheel is the unique efficient architecture and the unique Nash architecture. So (2016), like Bloch and Dutta (2009), assumes that a unit of resource limits the investment of every player and that the strength of a link is an additively separable function of the investments in it of the players that it connects, but unlike Bloch and Dutta, Chiu Ki So assumes concavity instead of convexity, i.e., that the strength of a link connecting i and j where i invests \(x_{i}^{j}\) and j invests \(x_{j}^{i}\) is \( \phi (x_{i}^{j})+\phi (x_{j}^{i})\), with \(\phi \) increasing and strictly concave, while in our model the strength is \(\phi (x_{i}^{j}+x_{j}^{i})\) with \(\phi \) just non-decreasing. She obtains sufficient conditions for the symmetric complete network to dominate all star networks, but no characterization is provided.Footnote 14 She also establishes sufficient conditions for the symmetric star and the complete network to be Nash stable.
Other, less closely related models with endogenous link strength are the following. Cabrales et al. (2011) provide a model where players choose an aggregate level of socialization effort which is distributed across all possible bilateral interactions in proportion to the partner’s socialization effort; Feri and Meléndez-Jiménez’s (2013) provide a dynamic model, where the choice of whom to link and a coordination game determines the strength of the links. Harmsen-van Hout et al. (2013) provide a model where individuals derive social value from direct connections and informational value from direct and indirect connections, but the more links an individual sustains the weaker they are. In Boucher (2015), individuals with a limited budget derive utility from “self-investment” and from direct connections, assuming the utility of a direct link to be a convex function of the investments of the two players involved, whose distance also enters as an argument their utility. Also in Salonen (2015), Baumann (2019) and Griffith (2019), individuals with limited resources derive utility from self-investment and from direct connections, but assuming the utility of a link to be a strictly concave function of the investments of the two players. Ding (2019) considers a CES (constant elasticity of substitution) link-formation technology that nests unilateral and bilateral network formation.
7 Concluding comments
It is worth emphasizing the generality and naturalness of the extension of Jackson and Wolinsky’s (1996) connections model studied, where the two parameters—cost and decay level—fixed exogenously in Jackson and Wolinsky’s model are replaced by a function, i.e., a technology that relates the investment in a link and its strength.
As it turns out, still in broad general terms as far as technology is concerned, in connections models à la Jackson–Wolinsky complete networks and all-encompassing star networks continue to be the only possibly non-empty efficient networks unless a rare coincidence occurs. Even the exception of a supertie in this more general model is very rare. Moreover, if the notion of efficiency is strengthened by requiring minimal cost, only complete networks and all-encompassing star networks can possibly satisfy this requirement. The outcome of a laborious proof confirms the great robustness of the result obtained by Jackson and Wolinsky (1996) for the simplest technology, where only one type of link, with fixed strength and fixed cost, is feasible. This adds new insight, substantially increasing the scope of the connections model introducing endogenous link strength.
It is worth noting the crucial role of the result (and its proof) obtained in Olaizola and Valenciano (2019) in the laborious proof of Theorem 1: The first step in its proof (Proposition 1) is a corollary of that result, and the final steps for the proof of the theorem are based on the algorithm at the basis of the proof in Olaizola and Valenciano (2019). The proof then takes advantage of the sharp structure of DNSG-networks, among which one is sure to be efficient if a non-empty efficient network exists (Proposition 1), to corner the actual candidates step by step. Each step narrows the set of candidate networks. It is also worth remarking that the result on efficiency in the “unifying” model in Olaizola and Valenciano (2018), whose proof was extremely lengthy, is now a direct corollary of Theorem 1 in this work.
An easy strengthening of Theorem 1 is worth mentioning. The model considered here assumes that revenue and investments occur simultaneously, so as long as the net value is positive a network is feasible. In other words, the planner has unlimited credit and there are no budget constraints. This may seem unrealistic and begs question of efficiency under a budget constraint. As commented, Olaizola and Valenciano (2019) provide an algorithm that rearranges the available links (i.e., those forming the network) in a more efficient way, perhaps disposing of some of them, and yields a connected DNSG-network whose net value is at least as high as that of the original network. Therefore, if a network is feasible under a given budget, this rearranging procedure can be applied without increasing the cost. This means that the result in Olaizola and Valenciano (2019) applies, i.e., any network feasible for a budget is dominated by a DNSG-network which is also feasible for the budget. Moreover, Theorem 1 extends to the case when the planner has a limited budget. To see why, note that if \(\delta \) is the available technology and b the budget, this is equivalent in practical terms to no budget and a technology \(\delta _{b}\) given by
An natural line of further work is to address the question of stability, i.e., Nash equilibrium or pairwise stability, in a decentralized context where node players can invest in links and a technology in the general sense considered here, possibly satisfying further regularity conditions, determines the strength of each link. That will be the goal of a separate paper
Notes
König et al. (2014) contains an interesting study of the topological properties of nested split graph networks.
Note that there is only one non-weighted complete network, but there are infinite complete weighted networks.
Nevertheless, the strength of a link admits other interpretations, such as the “strength of a tie,”i.e., the intensity of a personal relationship (Granovetter 1973). A link can also be a means for the flow of other goods, but we give preference here to the interpretation in terms of information.
A link-investment vector \(\underline{{\mathbf {c}}}=(c_{{\underline{ij}}})_{ {\underline{ij}}\in N_{2}}\) can also and below often will be seen as a symmetric matrix \({\mathbf {c}}=(c_{ij})_{i,j\in N}\), with \(c_{ij}=c_{ji}=c_{ {\underline{ij}}}\) for all \(i,j\in N\).
In what follows, we always assume that nodes in a DNSG-network are numbered according to a ranking numbering for which the conditions in Definition 3 hold.
In fact, the result in Olaizola and Valenciano (2019) also covers two other cases: when only nodes at a given or smaller distance are received and when only nodes with which the strength of the connection is above a threshold level are received.
In the formulation of the result Olaizola and Valenciano (2019), only the structure of DNSG-network is emphasized, but this refining procedure is commented in the concluding remarks of that paper.
In fact, as we show later, with the sole, rare exception of a highly particular case where there is a tie between an optimal all-encompassing star, an optimal complete network and a whole range of “intermediate” NSG-structures between them.
It is noteworthy that once again the same types of structure emerge in the final steps to prove this result as in the lengthy proof under much more restrictive conditions in the unifying model of Olaizola and Valenciano (2018) without using Proposition 1, and indeed using it as in Olaizola and Valenciano (2019).
The questions of existence and uniqueness are dealt with in the next section.
Note the coincidence of Fig. 10 with the regions of values of the parameters where these structures are efficient in Jackson and Wolinsky’s (1996) discrete biparametric model. This is not surprising, given that in the current family of non-discrete technologies it holds that \({\widehat{c}}= {\overline{c}}=c^{*}\).
As Chiu Ki So rightly acknowledges in “Introduction”: “A complete characterization of efficient and stable networks for concave technologies seems analytically formidable.”
In fact, any choice of nodes in \(K_{p-1}\) and \(K_{p}\) would do. The only reason for this particular choice is to preserve the conditions in Definition 3 for the same numbering of the nodes after either of the modifications considered.
Note that 0-entries not in the main diagonal correspond to pairs of nodes indirectly connected through the star. In Fig. 4, 0-entries in the main diagonal are in bold (\({\mathbf {0}}\)).
References
Bala V, Goyal S (2000) A non-cooperative model of network formation. Econometrica 68:1181–1229
Baumann L (2019) A model of weighted network formation (unpublished working paper)
Bloch F, Dutta B (2009) Communication networks with endogenous link strength. Games Econ Behav 66:39–56
Boucher V (2015) Structural homophily. Int Econ Rev 56(1):235–264
Bramoullé Y, Galeotti A, Rogers BW (eds) (2015) The Oxford handbook on the economics of networks. Oxford University Press, Oxford
Cabrales A, Calvó-Armengol A, Zenou Y (2011) Social interactions and spillovers. Games Econ Behav 72:339–360
Deroian F (2009) Endogenous link strength in directed communication networks. Math Soc Sci 57:110–116
Ding S (2019) The formation of links and the formation of networks (unpublished working paper)
Feri F, Meléndez M (2013) Coordination in evolving networks with endogenous decay. J Evolut Econ 23:955–1000
Goyal S (2007) Connections. An introduction to the economics of networks. Princeton University Press, Princeton
Granovetter MS (1973) The strength of weak ties. Am J Sociol 78(6):1360–1380
Griffith A (2019) A continuous model of strong a weak ties (unpublished working paper)
Harmsen-van Hout MJW, Herings PJ-J, Dellaert BGC (2013) Communication network formation with link specificity and value transferability. Eur J Oper Res 229:199–211
Jackson M (2008) Social and economic networks. Princeton University Press, London
Jackson M, Wolinsky A (1996) A strategic model of social and economic networks. J Econ Theory 71:44–74
König MD, Tessone CJ, Zenou Y (2014) Nestedness in networks: a theoretical model and some applications. Theor Econ 9:695–752
Olaizola N, Valenciano F (2018) A unifying model of strategic network formation. Int J Game Theory 47:1033–1063
Olaizola N, Valenciano F (2019) Dominance of weighted nested split graph networks in connections models. Int J Game Theory. https://doi.org/10.1007/s00182-019-00676-2 (forthcoming)
Salonen H (2015) Reciprocal equilibria in link formation games. Czech Econ Rev 9(2015):169–183
So CK (2016) Network formation with endogenous link strength and decreasing returns to investment. Games MDPI Open Access J 7(4):1–9
Vega-Redondo F (2007) Complex social networks. Econometric Society Monographs. Cambridge University Press, Cambridge
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they do not have conflict of interests.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
We thank the editor and two anonymous referees for their comments. This research is supported by the Spanish Ministerio de Economía y Competitividad under Projects ECO2015-66027-P and ECO2015-67519-P (MINECO/FEDER). Both authors also receive Basque Government Departamento de Educación, Política Lingüística y Cultura funding for Grupos Consolidados IT1367-19. N. Olaizola, F. Valenciano: BRiDGE Group (http://www.bridgebilbao.es).
Appendix
Appendix
1.1 Proposition 2
Proof
Let \(g^{\underline{{\mathbf {c}}}}\) be an efficient connected DNSG-network where nodes are numbered so that Definition 3 holds, with a positive net value and no superfluous links.
(i): Let i and j be two nodes, \(i,j\ne 1\), directly connected, i.e., \(c_{{\underline{ij}}}>0.\) Given the DNSG-structure of \(g^{ \underline{{\mathbf {c}}}}\), the strongest links are those that form the all-encompassing star centered at node 1 that connects any two nodes other than node 1 by two-link paths. Therefore, link \({\underline{ij}}\) cannot be a necessary part of the optimal path connecting any other pair of nodes in \( g^{\underline{{\mathbf {c}}}}\). In other words, link \({\underline{ij}}\) can only be part of one optimal path, the one-link path connecting i and j. Then, given that the link is only useful for i and j to see each other, for investment \(\underline{{\mathbf {c}}}\) to be efficient \(c_{{\underline{ij}}}\) must maximize \(2v\delta (c)-c\), that is, \(c_{{\underline{ij}}}\in \)\(\arg \max _{c>0}(2v\delta (c)-c)\). Then, all such links can be replaced by \( {\widehat{c}}\)-links, where \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\), to obtain a DNSG-network with the same underlying graph, the same net value, which is consequently also efficient and has no superfluous links.
(ii): Now assume that node j\(\ne 1\) belongs to the NSG-class \(K_{1}\) of node 1, i.e., j has \(n-1\) neighbors. All nodes in \( K_{1} \) are directly connected with all other nodes, so links connecting 1 with other nodes in \(K_{1}\) are not used by any indirect connection. That is, link \({\underline{1j}}\) is only used by 1 and j to see each other. Therefore, \(c_{{\underline{1j}}}\in \)\(\arg \max _{c>0}(2v\delta (c)-c)\). Then, all such links can also be replaced by \({\widehat{c}}\)-links to obtain a DNSG-network with the same net value and no superfluous links.
(iii): In view of (i) and (ii), it is possible to replace all links connecting pairs of nodes other than 1 and those connecting node 1 with nodes with as many neighbors as node 1 by \( {\widehat{c}}\)-links for a fixed \({\widehat{c}}\in \arg \max _{c>0}(2v\delta (c)-c)\) to form a network with the same underlying graph, the same net value and no superfluous links. Let \(g^{\underline{{\mathbf {c}}}}\) (with \(\underline{ {\mathbf {c}}}\) so updated) be such a network and \(i,j\ne 1.\) If \(\left| N^{d}(i;g^{\underline{{\mathbf {c}}}})\right| >\left| N^{d}(j;g^{ \underline{{\mathbf {c}}}})\right| ,\) the DNSG-structure of \(g^{ \underline{{\mathbf {c}}}}\) implies that \(\delta (c_{{\underline{1i}}})\le \delta (c_{{\underline{1j}}}).\) We show that the inequality must be strict. Assume \(k\in N^{d}(i;g^{\underline{{\mathbf {c}}}})\setminus N^{d}(j;g^{ \underline{{\mathbf {c}}}})\), i.e., \(c_{{\underline{ik}}}={\widehat{c}}>0\) and \(c_{ {\underline{jk}}}=0.\) Then, \(2v\delta ({\widehat{c}})-{\widehat{c}}>2v\delta (c_{ {\underline{1i}}})\delta (c_{{\underline{1k}}})\) (otherwise the \({\widehat{c}}\)-link connecting i and k would be superfluous) and if \(\delta (c_{ {\underline{1i}}})=\delta (c_{{\underline{1j}}})\), then \(2v\delta ({\widehat{c}})- {\widehat{c}}>2v\delta (c_{{\underline{1j}}})\delta (c_{{\underline{1k}}})\) too. That is, by connecting j and k by a \({\widehat{c}}\)-link the net value of the network would increase. Therefore, it must be \(\delta (c_{{\underline{1i}} })<\delta (c_{{\underline{1j}}})\), which implies \(c_{{\underline{1i}}}<c_{ {\underline{1j}}}.\)
Thus, nodes with fewer neighbors are connected through stronger links with the center. We show now that nodes with the same number of neighbors are either connected with the center by links of the same strength or by links that can be replaced by links of the same strength without changing the net value. Let \(i,j\ne 1\) be two nodes with the same number of neighbors, \(\left| N^{d}(i;g^{\underline{{\mathbf {c}}} })\right| =\left| N^{d}(j;g^{\underline{{\mathbf {c}}}})\right| \), and let \({\overline{c}}=c_{{\underline{1i}}}\) and \({\overline{c}}^{\prime }=c_{ {\underline{1j}}}.\) Let \(\underline{{\mathbf {c}}}^{\prime }\) and \(\underline{ {\mathbf {c}}}^{\prime \prime }\) be the investments that result from changing one link in \(\underline{{\mathbf {c}}}\): link \({\underline{1j}}\) for \(\underline{ {\mathbf {c}}}\rightarrow \underline{{\mathbf {c}}}^{\prime }\), and link \( {\underline{1i}}\) for \(\underline{{\mathbf {c}}}\rightarrow \underline{{\mathbf {c}} }^{\prime \prime }\), defined by
It follows that if i and j are not neighbors, the changes in the contribution to the net value from \(g^{\underline{{\mathbf {c}}}}\) to \(g^{ \underline{{\mathbf {c}}}^{\prime }}\) and from \(g^{\underline{{\mathbf {c}}}}\) to \( g^{\underline{{\mathbf {c}}}^{\prime \prime }}\) are of equal absolute value and opposite sign or zero for any pair of nodes but for i and j, namely
because for \(g^{\underline{{\mathbf {c}}}}\) to be efficient both differences must be \(\ge 0\). Therefore, adding up the two inequalities we have
which implies \(\delta ({\overline{c}})-\delta ({\overline{c}}^{\prime })=0\), i.e., \(\delta (c_{{\underline{1i}}})=\delta (c_{{\underline{1j}}}),\) which, by \( g^{\underline{{\mathbf {c}}}}\) efficiency, implies \(c_{{\underline{1i}}}=c_{ {\underline{1j}}}\).
Finally, if i and jare neighbors the changes in the contribution to the net value from \(g^{\underline{{\mathbf {c}}}}\) to \(g^{ \underline{{\mathbf {c}}}^{\prime }}\) and from \(g^{\underline{{\mathbf {c}}}}\) to \( g^{\underline{{\mathbf {c}}}^{\prime \prime }}\) are of equal absolute value and opposite signs or zero for any pair of nodes, i.e.,
which, as both \(v(g^{\underline{{\mathbf {c}}}})-v(g^{\underline{{\mathbf {c}}} ^{\prime }})\) and \(v(g^{\underline{{\mathbf {c}}}})-v(g^{\underline{{\mathbf {c}}} ^{\prime \prime }})\) are \(\ge 0\), implies \(v(g^{\underline{{\mathbf {c}}} })=v(g^{\underline{{\mathbf {c}}}^{\prime }})=v(g^{\underline{{\mathbf {c}}} ^{\prime \prime }})\). From this, it follows that
where \(K=\sum _{k<l\le n}\delta (c_{{\underline{1l}}})\), if \(k-1\) is the number of neighbors of both i and j. In general, this \(\arg \max \)-set may not be a singleton, but if all links connecting the center with nodes in the same NSG-class as i and j are replaced by \({\overline{c}}\)-links the net value will remain the same.
Finally, given that the new network has been formed by replacing all existing links between spoke nodes of the central star in the initial one (none of them superfluous) by \({\widehat{c}}\)-links, and each of the links forming the central star has been either left unchanged or replaced by a link that does not alter the net value, in the resulting network the underlying graph is the same and no link is superfluous. \(\square \)
1.2 Proposition 3
Proof
Assume that \(\underline{{\mathbf {c}}}\) is an efficient investment vector such that \(g^{\underline{{\mathbf {c}}}}\) is a simple DNSG-network, with \( p\ge 2\)NSG-classes \(K_{1},K_{2},\ldots ,K_{p-1},K_{p}\). We show that the central star of \(g^{\underline{{\mathbf {c}}}}\) can have links of at most two different strengths: \({\widehat{c}}\) and \(c_{2}\). Assume that there are links of three different strengths in the central star. Then, at least two of them must have strengths greater than \({\widehat{c}}\). This must be so for classes \(K_{p-1}\) and \(K_{p}\), with investments \(c_{p-1}<c_{p}\). Let \(j:=\max K_{p-1}\) (and consequently \(j+1=\min K_{p}\)), and compare the net value of \(g^{\underline{{\mathbf {c}}}}\) with the net value of the two networks, \(g^{\underline{{\mathbf {c}}}^{\prime }}\) and \(g^{\underline{\mathbf {c }}^{\prime \prime }}\), that result from each of the following two modifications of \(\underline{{\mathbf {c}}}\) (Fig. 8) denoted by \( \underline{{\mathbf {c}}}^{\prime }\) and \(\underline{{\mathbf {c}}}^{\prime \prime }\) respectively:Footnote 15
- (a):
-
\({\mathbf {c}}\rightarrow {\mathbf {c}}^{\prime }:\) Invest \(c_{p}\) in link \( {\underline{1j}}\) instead of \(c_{p-1}\), delete the \({\widehat{c}}\)-links connecting j with nodes in \(N^{d}(j,g^{\underline{{\mathbf {c}}}}){\setminus } N^{d}(j+1,g^{\underline{{\mathbf {c}}}})\) and let all other link-investments remain unchanged.
- (b):
-
\({\mathbf {c}}\rightarrow {\mathbf {c}}^{\prime \prime }:\) Invest \(c_{p-1}\) in link \(\underline{1,j+1}\) instead of \(c_{p}\), connect \(j+1\) with nodes in \( N^{d}(j,g^{\underline{{\mathbf {c}}}}){\setminus } N^{d}(j+1,g^{\underline{{\mathbf {c}}}})\) by \({\widehat{c}}\)-links, and let all other link-investments remain unchanged.
Figure 8 represents columns j and \(j+1\) of the investment matrix corresponding to \(g^{\underline{{\mathbf {c}}}}\) (center), \(g^{\underline{ {\mathbf {c}}}^{\prime }}\) (left) and \(g^{\underline{{\mathbf {c}}}^{\prime \prime }}\) (right). Note that \({\mathbf {c}}\rightarrow {\mathbf {c}}^{\prime }\) modifies only the j-column and row, while \({\mathbf {c}}\rightarrow {\mathbf {c}}^{\prime \prime }\) modifies only the \((j+1)\)-column and row. A comparison of the impact of either modification on the net value generated by the connection of any pair of nodes entry by entry yields the following.Footnote 16 The impact in both cases is either the same (when there is no impact), or the same but with opposite signs (entries framed), but in only one case for each (entries marked as \(0^{*}\) in Fig. 8).
The change in contribution by the indirect connection between j and \(j+1\) differs. In the first case, it is \(2v(\delta (c_{p-1})\delta (c_{p})-\delta (c_{p})^{2})\), while in the second it is \(2v(\delta (c_{p-1})\delta (c_{p})-\delta (c_{p-1})^{2}).\) This means that for \(v(g^{\underline{{\mathbf {c}}}})\) to be efficient the following must hold:
and summing up these inequalities, we obtain \(-(\delta (c_{p})-\delta (c_{p-1}))^{2}\ge 0\), which is a contradiction as we assume \(c_{p-1}<c_{p}\) and \(\delta (c_{p})>\delta (c_{p-1})\). \(\square \)
1.3 Proposition 4
Proof
(i) This follows from the fact that in an efficient complete network any link is only used by the two nodes that it connects.
(ii) Otherwise, if \(2v\delta (c_{{\underline{ki}}})\delta (c_{ {\underline{kj}}})>2v\delta (c_{{\underline{ij}}})-c_{{\underline{ij}}}\), the net value of the network would increase if link \({\underline{ij}}\) were deleted. \(\square \)
1.4 Proposition 5
Proof
(i) An all-encompassing star is an NSG-network with two NSG-classes: a singleton, the center and all other nodes with only one neighbor. There are no links between spoke nodes, so any two spoke nodes in that NSG-class are not neighbors. Therefore, the last part of the proof of Proposition 2(iii) adapts to the case of an efficient all-encompassing star and yields that all spoke nodes are connected with the center by links that receive the same investment, say, \(c_{n}^{*}\). The net value of an all-encompassing star of \(c_{n}^{*}\)-links, \(g^{ \underline{{\mathbf {c}}}}\), is:
Thus, for this star to be efficient \(c_{n}^{*}\) must maximize \(2v\delta (c)+(n-2)v\delta (c)^{2}-c.\) Hence, (5).
(ii) Otherwise, if \(2v\delta (c_{n}^{*})^{2}<2v\delta ( {\widehat{c}})-{\widehat{c}}\), the net value of the network would increase if two spoke nodes were connected with a \({\widehat{c}}\)-link. \(\square \)
1.5 Proposition 6
Proof
By Corollary 1, the only possibly efficient simple DNSG-networks are \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) (\(k\ne 2\)) or \(g^{\underline{ {\mathbf {c}}}_{k}^{**}}\) (\(k\ne n-1\)) for some \(k=1,2,\ldots ,n\). We first discuss \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) (Fig. 4a) and prove that the only efficient \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) must be complete (\(g^{\underline{{\mathbf {c}}}_{n}^{*}}\)) or an all-encompassing star (\(g^{\underline{{\mathbf {c}}}_{1}^{*}}\)). To that end, compare the net value of \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) (\( 2<k<n\) ) with the net values of the two networks, \(g^{\underline{{\mathbf {c}}} _{k-1}^{*}}\) and \(g^{\underline{{\mathbf {c}}}_{k+1}^{*}}\), that result from each of the following two modifications of \(\underline{{\mathbf {c}}} _{k}^{*}\) (Fig. 9):
- (a):
-
\({\mathbf {c}}_{k}^{*}\rightarrow {\mathbf {c}}_{k-1}^{*}:\) Invest \( c_{2}\) in link \({\underline{1k}}\) instead of \({\widehat{c}}\), delete the \( {\widehat{c}}\)-links connecting k with other nodes in \(K_{2}\) and let all other link-investments be unchanged.
- (b):
-
\({\mathbf {c}}_{k}^{*}\rightarrow {\mathbf {c}}_{k+1}^{*}:\) Invest \( {\widehat{c}}\) in link \(\underline{1,k+1}\) instead of \(c_{2}\), connect \(k+1\) with all the other nodes in \(K_{2}\) by \({\widehat{c}}\)-links and let all other link-investments be unchanged.
Then, we have
and therefore:
If \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) is efficient, \(2v\delta ( {\widehat{c}})-{\widehat{c}}\le \delta ({\widehat{c}})\delta (c_{2})\) must hold. (Otherwise, the net value of the network would increase if a node in \(K_{1}\) and a node in \(K_{2}\) were connected by a \({\widehat{c}}\)-link.) Then,
In other words,
or equivalently
which contradicts the efficiency of \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\) . This leaves the all-encompassing star \(g^{\underline{{\mathbf {c}}}_{1}^{*}}\) and the complete network \(g^{\underline{{\mathbf {c}}}_{n}^{*}}\) as the only possibly efficient simple DNSG-networks of type \(g^{ \underline{{\mathbf {c}}}_{k}^{*}}\).
We now discuss a network of the second type, \(g^{\underline{{\mathbf {c}}} _{k}^{**}}\) with \(1<k<n-2\) (Fig. 4b). Compare the net value of \( g^{\underline{{\mathbf {c}}}_{k}^{**}}\) with the net value of the two networks, \(g^{\underline{{\mathbf {c}}}_{k-1}^{**}}\) and \(g^{\underline{{\mathbf {c}}}_{k+1}^{**}}\), that result from each of the following two modifications of \(\underline{{\mathbf {c}}}_{k}^{**}\) denoted by \(\underline{{\mathbf {c}}}_{k-1}^{**}\) and \(\underline{{\mathbf {c}}} _{k+1}^{**}\), respectively (Fig. 10):
- (a):
-
\({\mathbf {c}}_{k}^{**}\rightarrow {\mathbf {c}}_{k-1}^{**}:\) Invest \(c_{2}\) in link \({\underline{1k}}\) instead of \({\widehat{c}}\), delete the \({\widehat{c}}\)-links connecting k with nodes in \(K_{2}\), and let all other link-investments be unchanged.
- (b):
-
\({\mathbf {c}}_{k}^{**}\rightarrow {\mathbf {c}}_{k+1}^{**}:\) Invest \({\widehat{c}}\) in link \(\underline{1,k+1}\) instead of \(c_{2}\), connect \(k+1\) with the other \(n-k-1\) nodes in \(K_{2}\) by \({\widehat{c}}\)-links, and let all other link-investments be unchanged.
Then, we have
and therefore:
If \(g^{\underline{{\mathbf {c}}}_{k}^{**}}\) is efficient, \(2v\delta ( {\widehat{c}})-{\widehat{c}}\le \delta (c_{2})^{2}\) must hold. (Otherwise, the net value of the network would increase if any two nodes in \(K_{2}\) were connected by a \({\widehat{c}}\)-link.) Then, necessarily
If \(2v\delta ({\widehat{c}})-{\widehat{c}}-2v\delta (c_{2})^{2}<0,\) then it follows that
which contradicts the efficiency of \(g^{\underline{{\mathbf {c}}}_{k}^{**}}\) and leaves the all-encompassing star \(g^{\underline{{\mathbf {c}}} _{1}^{**}}\) and the complete network \(g^{\underline{{\mathbf {c}}} _{n}^{**}}\) as the only possibly efficient simple DNSG -networks of type \(g^{\underline{{\mathbf {c}}}_{k}^{*}}\).
Otherwise, if \(2v\delta ({\widehat{c}})-{\widehat{c}}-2v\delta (c_{2})^{2}=0\), then
which implies that \(g^{\underline{{\mathbf {c}}}_{k}^{**}}\) can only be efficient if \(v(g^{\underline{{\mathbf {c}}}_{k}^{**}})-v(g^{\underline{ {\mathbf {c}}}_{k-1}^{**}})=v(g^{\underline{{\mathbf {c}}}_{k}^{**}})-v(g^{\underline{{\mathbf {c}}}_{k+1}^{**}})=0.\) In other words, in the sequence from \(g^{\underline{{\mathbf {c}}}_{1}^{**}}\) to \(g^{ \underline{{\mathbf {c}}}_{n-1}^{**}}\) the increase (decrease) in net value is the same for any two consecutive structures. From this, it also follows that \(g^{\underline{{\mathbf {c}}}_{k}^{**}}\) is strictly dominated either by \(g^{\underline{{\mathbf {c}}}_{1}^{**}}\) or by \(g^{ \underline{{\mathbf {c}}}_{n-1}^{**}}\), unless all these differences are 0. But this is only possible if, in addition to \(2v\delta ({\widehat{c}} )-{\widehat{c}}-2v\delta (c_{2})^{2}=0,\) it holds that \(2v\delta ({\widehat{c}} )-{\widehat{c}}=2v\delta (c_{2})-c_{2}.\) That is,
In this case, \(v(g^{\underline{{\mathbf {c}}}_{1}^{**}})=v(g^{\underline{ {\mathbf {c}}}_{2}^{**}})=\cdots =v(g^{\underline{{\mathbf {c}}}_{n}^{**}})\), and they are all strictly dominated either by the optimal complete or by the optimal all-encompassing star, unless these happen to be \(g^{\underline{{\mathbf {c}}}_{1}^{**}}\) and \(g^{ \underline{{\mathbf {c}}}_{n}^{**}},\) in which case \(c_{2}=c_{n}^{*} \) and (11) becomes (7). In this very special case, the complete network, the all-encompassing star and all intermediate\(g^{\underline{{\mathbf {c}}}_{k}^{**}}\) with \( c_{2}=c_{n}^{*}\) are efficient if their net value is positive. \(\square \)
1.6 Theorem 1
Proof
Let g be an efficient network with a positive value. Let \(g_{\mathrm{D }}\) be the dominant NSG-network with no superfluous links that the algorithm at the basis of the result in Olaizola and Valenciano (2019) produces from g s.t. \(v(g)\le v(g_{{\mathrm{D}}})\). Given that g is efficient, \(v(g)=v(g_{{\mathrm{D}}})\) and \(g_{{\mathrm{D}}}\) must also be efficient. Moreover, by Proposition 2’, \(v(g)=v(g_{{\mathrm{D}}})=v(g_{{\mathrm{RD}}})\), where \(g_{{\mathrm{RD}}}\) is a simpleDNSG-network with the same underlying graph as \(g_{{\mathrm{D}}}\) and necessarily efficient too. Thus, by Corollary 1 and Proposition 6, unless (7) holds, \(g_{{\mathrm{RD}}}\) (and \(g_{{\mathrm{D}}}\) which has the same underlying graph) must be either complete or an all-encompassing star. But this is only possible if gitself is complete or an all-encompassing star; otherwise, the algorithm could not yield a DNSG-network with such an underlying graph and the same net value. This is obvious if \(g_{{\mathrm{D}}}\) and \(g_{{\mathrm{RD}}}\) are complete. If \(g_{{\mathrm{D}}}\) and \(g_{{\mathrm{RD}}}\) are all-encompassing stars, then \(g_{{\mathrm{D}} }=g_{{\mathrm{RD}}}\), and they must consist of \(n-1\)\(c^{*}\)-links for some \(c^{*}\) s.t. (5). Thus, g must have at least \(n-1\)\(c^{*}\)-links, which arranged as a star maximize the net value achievable with those links. If g has more links, as \(v(g)=v(g_{{\mathrm{D}}})\), some of them must be superfluous and therefore discarded in the transition from g to \(g_{{\mathrm{D}}}\). But this is not possible. If two spoke nodes of a star of \(c^{*}\)-links are connected by a c-link, for this link to be superfluous it must hold
but efficiency of g implies that in the expression above “\(\le \)” must be “\(=\).”Thus, we have
In this case, it is immediate to check that a complete network of \({\widehat{c}} \)-links yields a greater net value than a star of \(c^{*}\)-links unless\(2v\delta (c^{*})-c^{*}=2v\delta ({\widehat{c}})-{\widehat{c}}.\) But this along with (12) means that there is a supertie. Thus, g has no superfluous links and must be an all-encompassing star. \(\square \)
1.7 Theorem 2
Proof
In view of Theorem 1 and Propositions 4 and 5, it is clear that the only complete network that can be efficient and minimize the cost is the one with \({\widehat{c}}\)-links, with \({\widehat{c}}\) given by (8), and the only all-encompassing star that can be efficient and minimize the cost is one with \(c_{n}^{*}\)-links, with \(c_{n}^{*}\) given by (9).
In the case of a supertie, i.e., if (7) holds for \( {\widehat{c}}\) given by (8), and \(c_{n}^{*}\) given by ( 9), then, as shown in Proposition 6, all \(g^{\underline{ {\mathbf {c}}}_{k}^{**}}\)\((1\le k\le n)\) are efficient if their same net value is positive. Nevertheless, their costs are different because
for \(1\le k<n\), and those differences are decreasing with k. In particular,
If all these differences are negative (or, equivalently, \(cost(\underline{ {\mathbf {c}}}_{2}^{**})-cost(\underline{{\mathbf {c}}}_{1}^{**})=(n-1){\widehat{c}}-c_{n}^{*}<0\)), then the cheapest is the complete network \(\underline{{\mathbf {c}}}_{n}^{**}\). Otherwise, these differences form a decreasing sequence of positive terms followed by negative terms, i.e., for some \(1<k<n,\)
In this case,
that is, the minimal cost is achieved either by \(\underline{{\mathbf {c}}} _{1}^{**}\) (an optimal all-encompassing star) or by \(\underline{ {\mathbf {c}}}_{n}^{**}\) (the optimal complete). \(\square \)
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Olaizola, N., Valenciano, F. Characterization of efficient networks in a generalized connections model with endogenous link strength. SERIEs 11, 341–367 (2020). https://doi.org/10.1007/s13209-020-00212-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13209-020-00212-6