Abstract
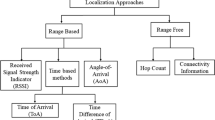
A heterogeneous wireless sensor network attacked by jamming is analyzed as a two-player non-cooperative game chance constrained problem, the utility function is based on the signal interference plus noise ratio at the receiver. In view of the problem’s stochasticity, second order cone programming is used to solve the game problem. Our preliminary numerical results show that the communication distance between network elements must be taken into account at the time of establishing the design requirements of any reliable application against jamming attacks. Furthermore, it is established that the receiver’s sensitivity level is a central parameter for changing the frequency used for the power transmission initially selected by the nodes.

Similar content being viewed by others
References
Sakthidharan, G. R., & Chitra, S. (2012). A survey on wireless sensor network: An applications perspective. IEEE international conference on computer communication and informatics (ICCCI).
Chen, X., Makki, K., Yen, K., & Pissinou, N. (2009). Sensor network security: A survey. IEEE Communications Surveys and Tutorials, 11(2), 52–73.
Mpitziopoulos, A., Gavalas, D., Konstantopoulos, C., & Pantziou, G. (2009). A survey on jamming attacks and countermeasures in WSNs. IEEE Communications Surveys and Tutorials, 11(4), 42–56.
Xu, W., Trappe, W., Zhang, Y., & Wood, T. (2005). The feasibility of launching and detecting jamming attacks in wireless networks. Urbana-Champaign: ACM MobiHoc.
Barron, (2008). Game theory: An introduction. New Jersey: Wiley Series in Operations Research and Management Science.
Chen, L., & Leneutre, J. (2011). Fight jamming with jamming—A game theoric analysis of jamming attack in wireless networks and defense strategy. Computer Networks, 55, 2259–2270.
Altman, E., Avrachenkov, K., & Garnaev, A. (2011). Jamming in wireless networks under uncertainty. Mobile Networks Applications, 16(2), 246–254.
Xu x., Gao, K., Zheng, X., & T. Zhao. (2012). A zero-sum game theoretic framework for jamming detection and avoidance in wireless sensor networks. IEEE international conference on computer science and information processing (CSIP) (pp. 265–270).
Ponukumati, D., & Gao, F. (2012). Robust coordinated downlink beamforming for multicell-cognitive radio networks with probabilistic constraints. IEEE signal processing for comunications sysmposium.
Ma, S., & Sun, D. (2013). Chance constrained robust beamforming in cognitive radio networks. IEEE Communications Letters, 17(1), 67–70.
Tse, D., & Viswanath, P. (2005). Fundamental of wireless communication. Cambridge: Cambridge University Press.
Charnes, A., Kirby, M. J. L., & Raike, W. M. (1968). Zero–zero chance-constrained games. Theory of Probability and Its Applications, 13, 628–646.
Charnes, A., Kirby, M. J. L., & Raike, W. M. (1968). Chance-constrained games with partially controllable strategies. Operations Research, 16, 142–149.
Blau, R. A. (1974). Random-payoff two-person zero-sum games. Operations Research, 22(6), 1243–1251.
Kosuch, S., & Lisser, A. (2010). Upper bounds for the 0–1 stochastic knapsack problem and a B&B algorithm. Annals of Operations Research, 176(1), 77–93.
Lobo, M., & Vandenberghe, L. (1998). Applications of second-order cone programming. Linear Algebra and Its Applications, 284(1–3), 193–228.
Lu, W.-S. (2009). Use SeDuMi to solve LP, SDP and SOCP problems: Remarks and examples. Greater Victoria: Dept. of Electrical and Computer Engineering, University of Victoria.
Sturm, J. (1999). Using SeDuMi 1.02, a MATLAB toolbox for optimization over symmetric cones. Optimization Methods and Software, 11–12, 625–653.
Acknowledgments
This work was supported by National Commission for Scientific and Technological research (CONICYT) of Chile, No. 74120035/2012 and the University of Santiago of Chile.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Cordero, C.V., Lisser, A. Jamming Attacks Reliable Prevention in a Clustered Wireless Sensor Network. Wireless Pers Commun 85, 925–936 (2015). https://doi.org/10.1007/s11277-015-2817-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2817-0