Abstract
In this paper, the security of linear optics cloning machine-enhanced passive state preparation continuous-variable quantum key distribution is investigated. The employment of passive state preparation eliminates the strict requirements on electro-optical modulators, while an appropriately tuned linear optics cloning machine can compensate the preparation noise introduced in passive state preparation and improve the system performance. The expression of the composable secret key rate in the finite-size regime of the proposed scheme is obtained. Simulation results demonstrate that the proposed scheme can effectively enhance the secret key rate and increase the maximum secure transmission distance.








Similar content being viewed by others
Data availability
Data will be made available on reasonable request.
References
Huang, P., Huang, J.Z., Zhang, Z.S., Zeng, G.H.: Quantum key distribution using basis encoding of Gaussian-modulated coherent states. Phys. Rev. A 97(4), 042311 (2018)
Leverrier, A., García-Patrón, R., Renner, R., Cerf, N.J.: Security of continuous-variable quantum key distribution against general attacks. Phys. Rev. Lett. 110(3), 030502 (2013)
Leverrier, A.: Composable security proof for continuous-variable quantum key distribution with coherent states. Phys. Rev. Lett. 114(7), 070501 (2015)
Leverrier, A.: Security of continuous-variable quantum key distribution via a Gaussian de Finetti reduction. Phys. Rev. Lett. 118(20), 200501 (2017)
Jouguet, P., Kunz-Jacques, S., Leverrier, A., Grangier, P., Diamanti, E.: Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photon 7, 378–381 (2013)
Jain, N., et al.: Practical continuous-variable quantum key distribution with composable security. Nat. Commun. 13, 4740 (2022)
Frédéric, G., Philippe, G.: Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002)
Leverrier, A., Philippe, G.: Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 102, 180504 (2009)
Qi, B., Evans, P.G., Grice, W.P.: Passive state preparation in the Gaussian-modulated coherent-states quantum key distribution. Phys. Rev. A 97, 012317 (2018)
Qi, B., Gunther, H., Evans, P.G., Williams, B.P., Camacho, R.M., Peters, N.A.: Experimental passive state preparation for continuous variable quantum communications. Phys. Rev. Appl. 13, 054065 (2020)
Huang, P., Wang, T., Chen, R., Wang, P., Zhou, Y.M., Zeng, G.H.: Experimental continuous-variable quantum key distribution using a thermal source. New J. Phys. 23, 113028 (2021)
Wu, X.D., Wang, Y.J., Guo, Y., Zhong, H., Huang, D.: Passive continuous-variable quantum key distribution using a locally generated local oscillator. Phys. Rev. A 103, 032604 (2021)
Fossier, S., Diamanti, E., Debuisschert, T., Tualle-Brouri, R., Grangier, P.: improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B At. Mol. Opt. Phys. 42, 114014 (2009)
Guo, Y., Lv, G., Zeng, G.H.: Balancing continuous-variable quantum key distribution with source-tunable linear optics cloning machine. Quantum Inf. Process. 14, 4323–4338 (2015)
Wu, X.D., Liao, Q., Huang, D., Wu, X.H., Guo, Y.: Balancing four-state continuous-variable quantum key distribution with linear optics cloning machine. Chin. Phys. B 26, 110304 (2017)
Zhang, H., Mao, Y., Huang, D., Guo, Y., Wu, X.D., Zhang, L.: Finite-size analysis of eight-state continuous-variable quantum key distribution with the linear optics cloning machine. Chin. Phys. B 27, 090307 (2018)
Yang, F.L., Qiu, D.W.: Thermal states quantum cryptography with linear optics cloning machine. Quantum Inf. Process. 19, 99 (2020)
Andersen, U.L., Josse, V., Leuchs, G.: Unconditional quantum cloning of coherent states with linear optics. Phys. Rev. Lett. 94, 240503 (2005)
Dong, Y.L., Zou, X.B., Guo, G.C.: Local and nonlocal cloning of coherent states with known phases using linear optics. Phys. Rev. A 77, 034304 (2008)
Fan, H., Wang, Y.N., Jing, L., Yue, J.D., Shi, H.D., Zhang, Y.L., Mu, L.Z.: Quantum cloning machines and the applications. Phys. Rep. 544(3), 241–322 (2014)
García-Patrón, R.: Quantum information with optical continuous variables: from bell tests to key distribution. Universite Libre De Bruxelles, Brussels (2007)
Huang, D., Huang, P., Lin, D.K., Zeng, G.H.: Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 6, 19201 (2016)
Liu, W.B., et al.: Homodyne detection quadrature phase shift keying continuous-variable quantum key distribution with high excess noise tolerance. PRX Quantum 2, 040334 (2021)
Wu, X.D., Wang, Y.J., Li, S., Zhang, W., Huang, D., Guo, Y.: Security analysis of passive measurement-device-independent continuous-variable quantum key distribution with almost no public communication. Quantum Inf. Process. 18, 372 (2019)
Zhang, M.Q., Huang, P., Wang, P., Wei, S.R., Zeng, G.H.: Experimental free-space continuous-variable quantum key distribution with thermal source. Opt. Lett. 48, 1184–1187 (2023)
Leverrier, A., Frédéric, G., Philippe, G.: Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 81, 062343 (2010)
Stefano, P.: Limits and security of free-space quantum communications. Phys. Rev. Research 3, 013279 (2021)
Acknowledgements
The work is supported in part by the Natural Science Foundation of China (No. 62361009) and in part by the Guizhou Provincial Science and Technology Projects (No. ZK[2021]304).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection, and analysis were performed by YH. The first draft of the manuscript was written by YH and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflicts of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
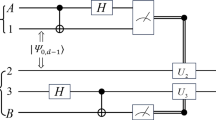
Appendix: The detailed derivation of \(I\left( {A:B} \right)\) and \(S\left( {B:E} \right)\) in PSP-LOCM CVQKD
Appendix: The detailed derivation of \(I\left( {A:B} \right)\) and \(S\left( {B:E} \right)\) in PSP-LOCM CVQKD
Given the covariance matrix \(\gamma_{{AB\varepsilon_{{{\text{PE}}}} }}\) in Eq. (22), the classical mutual information \(I\left( {A:B} \right)\) can be expressed as
On the other hand, \(S\left( {B:E} \right)\) can be given by
where \(S\left( \bullet \right)\) denotes the von Neumann entropy, \(S\left( { \bullet \left| B \right.} \right)\) denotes the conditional von Neumann entropy on Bob’s measurements, and \(B\) indicates Bob's measurement results. On the one hand, to maximize the information available, Eve can purify the system \(EAB_{1}\), it follows that \(S\left( E \right) = S\left( {AB} \right)\). On the other hand, Bob also can purify the system AEFG, one can get \(S\left( {E|B} \right) = S\left( {AFG|B} \right)\). The above equation can be rewritten as
It can be noted that \(S\left( {AB} \right)\) is determined by the covariance matrix \(\gamma_{AB}\) and \(S\left( {AFG|B} \right)\) is determined by the covariance matrix \(\gamma_{AFGB}\). \(\gamma_{AB}\) is described by
where \(G\left( x \right) = \left( {x + 1} \right)\log_{2} \left( {x + 1} \right) - x\log_{2} x\) is the von Neumann entropy of the thermal field state [3, 4] and \(\lambda_{i}\) is the i-th symplectic eigenvalue. The expressions of \(\lambda_{1 - 2}\) read
where \(A = \det \gamma_{A} + \det \gamma_{B} + \det \sigma_{AB}\) and \(B = \det \gamma_{AB}\). For \(\lambda_{3 - 5}\), it is first necessary to derive \(\gamma_{AFG}^{{x_{B} }}\) which can be expressed as
where \(\left( \bullet \right)^{ - 1}\) represents the inverse of a matrix. \(\gamma_{AFG}^{{x_{B} }}\) is the system after Bob's measurement, which is obtained by projecting the measurement of the whole system on the mode B2. Besides, the whole system can be described by the covariance matrix \(\gamma_{{AFGB_{2} }}\), whose expression is
where \(\Omega\) presents the beam splitter transformation, and contents \(\Omega = I_{A} \oplus \Omega_{{{\text{BF}}_{0} }}^{{{\text{BS}}}} \oplus I_{G}\) with \(I_{A} = I_{G} = \left( {\begin{array}{*{20}c} 1 & 0 \\ 0 & 1 \\ \end{array} } \right)\). Moreover, \(\Omega_{{{\text{BF}}_{0} }}^{{{\text{BS}}}}\) can be given by
The matrix of additional LOCM tunable noise effects is
Fortunately, after the above intricate calculations, \(\gamma_{AFG}^{{x_{B} }}\) can be presented by the following equation
The elements in the matrix of Eq. (35) can be expressed as
Then, it is straightforward to calculate \(\lambda_{3 - 5}\)
where \(C = \frac{{A\chi_{{{\text{LOCM}}}}^{2} + B + 1 + 2\chi_{{{\text{LOCM}}}} \left( {V\sqrt B + T\left( {V + \chi_{{{\text{line}}}} } \right) + 2T\sqrt {V^{2} - 1} } \right)}}{{\left[ {T\left( {V + \chi_{{{\text{tot}}}} } \right)} \right]^{2} }}\) and \(D = \left[ {\frac{{V + \sqrt B \chi_{{{\text{LOCM}}}} }}{{T\left( {V + \chi_{{{\text{tot}}}} } \right)}}} \right]^{2}\). Hence, \(S\left( {B:E} \right)\) can be derived from \(S\left( {AFG|B} \right) = \sum\limits_{i = 3}^{5} {G\left( {\frac{{\lambda_{i} - 1}}{2}} \right)}\).
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
He, Y., Wang, T. Security analysis of linear optics cloning machine-enhanced passive state preparation continuous-variable quantum key distribution. Quantum Inf Process 23, 135 (2024). https://doi.org/10.1007/s11128-024-04344-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-024-04344-7