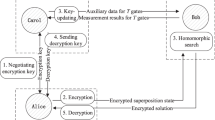
Abstract
As a promising emerging technology, quantum homomorphic encryption (QHE) attracts considerable attention in the domain of cloud computing. However, as the homomorphic evaluation for non-Clifford gate generates an undesired error, efficient QHE scheme for any quantum circuit still faces a serious challenge. In this paper, we propose a two-round QHE scheme based on matrix decomposition, which can be used to eliminate the error and obtain the decryption matrix non-interactively. Through the circuit synthesis method, the decryption matrix can be decomposed into a quantum circuit to complete the decryption. In order to reduce the decryption overhead for Client, an extra round of evaluation is used to perform the decryption circuit by Server. We prove that the scheme is compact and information-theoretically secure. In addition, we apply the QHE scheme to ciphertext retrieval and complete a ciphertext retrieval experiment on IBM Qiskit. The retrieval scheme is efficient even if the evaluated circuit contains any number of non-Clifford gates.










Similar content being viewed by others
Data Availability
The data that support the findings of this study are available from the corresponding author upon reasonable request.
References
Gentry, C.: A fully homomorphic encryption scheme. PhD thesis, Stanford University (2009)
Gentry, C.: Fully homomorphic encryption using ideal lattices. In: ACM, pp. 169–178 (2009)
Brakerski, Z., Vaikuntanathan, V.: Efficient fully homomorphic encryption from (standard) lwe. In: IEEE Symposium on Foundations of Computer Science (2011)
Peter, W.S.: Algorithms for quantum computation: Discrete log and factoring. In: Proceedings of Annual Symposium on the Foundations of Computer Science IEEE Computer Society Press Los Alamitos Ca, pp. 124–134 (1994)
Liang, M.: Symmetric quantum fully homomorphic encryption with perfect security. Quantum Inf. Process. 12(12), 3675–3687 (1999)
Wang, Y., She, K., Luo, Q., et al.: Symmetric weak ternary quantum homomorphic encryption schemes. Mod. Phys. Lett. B 30(7), 1650076 (2016)
Song, L.X., Zhou, D.Y., Wen, A.J.: Design and simulation of d dimensional (t, n) threshold quantum homomorphic encryption algorithm. Acta Electron. Sin. 48(5), 8 (2020)
Childs, A.M.: Secure assisted quantum computation. Quantum Inf. Comput. 5(6), 456–466 (2005)
Broadbent, A.: Delegating private quantum computations. Can J. Phys. 93(9), 410–413 (2015)
Yu, L., Ca, P.D., Fitzsimons, J.F.: Limitations on information-theoretically-secure quantum homomorphic encryption. Phys. Rev. A 90(5), 050303 (2014)
Newman, M., Shi, Y.: Limitations on transversal computation through quantum homomorphic encryption. Quantum Inf. Comput. 18(11), 927–948 (2017)
Lai, C.Y., Chung, K.M.: On statistically-secure quantum homomorphic encryption. Quantum Inf. Comput. 18(9), 0785–0794 (2018)
Broadbent, A., Jeffery, S.: Quantum homomorphic encryption for circuits of low t-gate complexity. Crypto 2015(9216), 609–629 (2014)
Liang, M.: Teleportation-based quantum homomorphic encryption scheme with quasi-compactness and perfect security. Quantum Inf. Process. 19(1), 28 (2019)
Wang, S.L., Shang, T., Liu, J.W.: Non-interactive quantum homomorphic encryption scheme based on the rotation operator. Sci. China-Phys. Mech. Astron. 53(4), 240311 (2023)
Wang, C., Zhou, R.G.: Secure multi-party convex hull protocol based on quantum homomorphic encryption. Quantum Inf. Process. 22(1), 24–32 (2022)
Xu, G., Yun, F., Chen, X.B., et al.: Secure multi-party quantum summation based on quantum homomorphic encryption. Intelligent Autom. Soft Comput. 34(1), 531–541 (2022)
Chen, G., Wang, Y., Jian, L., et al.: Quantum identity authentication protocol based on flexible quantum homomorphic encryption with qubit rotation. J. Appl. Phys. 133(6), 064402 (2023)
Sun, X.Q., Wang, T., Sun, Z.W., et al.: An efficient quantum somewhat homomorphic symmetric searchable encryption. Int. J. Theor. Phys. 56(4), 1335–1345 (2017)
Zhou, Q., Lu, S.: Quantum search on encrypted data based on quantum homomorphic encryption. Sci. Rep. 10(1), 5135 (2017)
Gong, C.Q., Du, J., Dong, Z.Y., et al.: Grover algorithm-based quantum homomorphic encryption ciphertext retrieval scheme in quantum cloud computing. Quantum Inf. Process. 19(3), 105 (2020)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: The 28th Annual ACM Symposium on the Theory of Computing, pp. 212–219 (1996)
Niemann, P., Wille, R., Drechsler, R.: Efficient synthesis of quantum circuits implementing clifford group operations. In: Design Automation Conference, pp. 483–488 (2014)
Boykin, P.O., Roychowdhury, V.: Optimal encryption of quantum bits. Phys. Rev. A 67(4), 645–648 (2003)
Gottesman, D.: The heisenberg representation of quantum computers. In: Proceedings of the XXII International Colloquium on Group Theoretical Methods in Physics, pp. 32–43 (1998)
Broadbent, A., Kazmi, R.A.: Constructions for quantum indistinguishability obfuscation. In: LATINCRYPT 2021, pp. 24–43 (2021)
Acknowledgements
This project was supported by the National Natural Science Foundation of China(No. 61971021), the Key Research and Development Project of Hebei Province (No. 22340701D) and the Universities Innovation Foundation of China-Beichuang Teaching Assistant Project (No. 2021BCA0200) for valuable helps.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Shang, T., Wang, S., Jiang, Y. et al. Two-round quantum homomorphic encryption scheme based on matrix decomposition. Quantum Inf Process 22, 422 (2023). https://doi.org/10.1007/s11128-023-04173-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-023-04173-0