Abstract
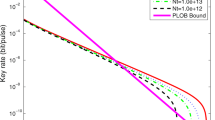
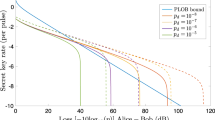
Twin-field quantum key distribution (TF-QKD) is a new extraordinary QKD protocol, which can overcome the fundamental rate-distance limit without quantum repeaters. Moreover, its variant, the sending-or-not-sending twin-field quantum key distribution (SNS-QKD) protocol, can both tolerate large misalignment error and have a higher key rate; however, the light source is assumed to be the trusted one in the original SNS protocol. In this paper, we propose a more practical SNS-QKD protocol with plug-and-play architecture, named \( P \& P\) SNS-QKD protocol. We present the framework of \( P \& P\) SNS-QKD protocol and analyze the tight bound of its key rate with the four-intensity decoy-state method. The proposed protocol can avoid the careful adjustments, and the control of the system and the numerical simulations results show that the proposed protocol has a close key generation rate to that of the original SNS-QKD. Besides, the proposed protocol still maintains a high tolerance for misalignment errors even if the source is unknown and untrusted.






Similar content being viewed by others
References
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050–2056 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48(3), 351–406 (2001)
Bennett, C.H., Brassard, G.: Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers Systems and Signal Processing, pp. 175-C179 (1984)
Lo, H.K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012)
Ma, X., Razavi, M.: Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 86(6), 062319 (2012)
Wang, X.B.: Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 87(1), 012320 (2013)
Zhou, Y.H., Yu, Z.W., Wang, X.B.: Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A 93(4), 042324 (2016)
Li, Z., Zhang, Y.C., Xu, F., Peng, X., Guo, H.: Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 89(5), 052301 (2014)
Sasaki, T., Yamamoto, Y., Koashi, M.: Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509(7501), 475–478 (2014)
Wang, L., Zhao, S.: Round-robin differential-phase-shift quantum key distribution with heralded pair-coherent sources. Quantum Inf. Process. 16, 100 (2017)
Pirandola, S., Laurenza, R., Ottaviani, C., Banchi, L.: Fundamental limits of repeaterless quantum communications. Nat. Commun. 8(1), 1–15 (2017)
Takeoka, M., Guha, S., Wilde, M.M.: Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 5(1), 1–7 (2014)
Lucamarini, M., Yuan, Z.L., Dynes, J.F., Shields, A.J.: Overcoming the rate-distance limit of quantum key distribution without quantum repeaters. Nature 557(7705), 400–403 (2018)
Minder, M., et al.: Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 13(5), 334–338 (2019)
Wang, X.B., Yu, Z.W., Hu, X.L.: Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 98(6), 062323 (2018)
Ma, X., Zeng, P., Zhou, H.: Phase-matching quantum key distribution. Phys. Rev. X 8(3), 031043 (2018)
Lin, J., Ltkenhaus, N.: Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 98(4), 042332 (2018)
Cui, C., Yin, Z.Q., Wang, R., Chen, W., Wang, S., Guo, G.C., Han, Z.F.: Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 11(3), 034053 (2019)
Curty, M., Azuma, K., Lo, H.K.: Simple security proof of twin-field type quantum key distribution protocol. npj Quantum Inf. 5(1), 1–6 (2019)
Grasselli, F., Curty, M.: Practical decoy-state method for twin-field quantum key distribution. New J. Phys. 21(7), 073001 (2019)
Hu, X.L., Jiang, C., Yu, Z.W., Wang, X.B.: Sending-or-not-sending twin-field protocol for quantum key distribution with asymmetric source parameters. Phys. Rev. A 100(6), 062337 (2019)
Liu, Y., Yu, Z.W., Zhang, W., Guan, J.Y., Chen, J.P., Zhang, C., Chen, T.Y.: Experimental twin-field quantum key distribution through sending or not sending. Phys. Rev. Lett. 123(10), 100505 (2019)
Yu, Z.W., Hu, X.L., Jiang, C., Xu, H., Wang, X.B.: Sending-or-not-sending twin-field quantum key distribution in practice. Sci. Rep. 9(1), 1–8 (2019)
Chen, J.P., Zhang, C., Liu, Y., Jiang, C., Zhang, W., Hu, X.L., Li, M.J.: Sending-or-Not-Sending with Independent Lasers: Secure Twin-Field Quantum Key Distribution over 509 km. Phys. Rev. Lett. 124(7), 070501 (2020)
Jiang, C., Yu, Z.W., Hu, X.L., Wang, X.B.: Unconditional security of sending or not sending twin-field quantum key distribution with finite pulses. Phys. Rev. Appl. 12(2), 024061 (2019)
Zhou, X.Y., Zhang, C.H., Zhang, C.M., Wang, Q.: Asymmetric sending or not sending twin-field quantum key distribution in practice. Phys. Rev. A 99(6), 062316 (2019)
Zhang, C.H., Zhang, C.M., Wang, Q.: Twin-field quantum key distribution with modified coherent states. Opt. lett. 44(6), 1468–1471 (2019)
Qiao, Y., Chen, Z., Zhang, Y., Xu, B., Guo, H.: Sending-or-not-sending twin-field quantum key distribution with light source monitoring. Entropy 22(1), 36 (2020)
Chen, G., Wang, L., Li, W., Zhao, Y., Zhao, S.M., Gruska, J.: Multiple-pulse phase-matching quantum key distribution. Quantum Inf. Process. 19(11), 1–16 (2020)
Yu, Y., Wang, L., Zhao, S., Mao, Q.: Decoy-state phase-matching quantum key distribution with source errors. Opt. Express 29(2), 2227–2243 (2021)
Lu, F.Y., Yin, Z.Q., et al.: Practical issues of twin-field quantum key distribution. New J. Phys. 21(12), 123030 (2019)
Teng, J., Lu, F.Y., Yin, Z.Q., Fan-Yuan, G.J., Wang, R., Wang, S., Han, Z.F.: Twin-field quantum key distribution with passive-decoy state. New J. Phys. 22(10), 103017 (2020)
Muller, A., Herzog, T., Huttner, B., Tittel, W., Zbinden, H., Gisin, N.: Plug and play systems for quantum cryptography. Appl. Phys. Lett. 70(7), 793–795 (1997)
Stucki, D., Gisin, N., Guinnard, O., Ribordy, G., Zbinden, H.: Quantum key distribution over 67 km with a plug&play system. New J. Phys. 4(1), 41 (2002)
Zhao, Y., Qi, B., Lo, H.K.: Quantum key distribution with an unknown and untrusted source. Phys. Rev. A 77(5), 052327 (2008)
Xu, F.H.: Measurement-device-independent quantum communication with an untrusted source. Phys. Rev. A 92(1), 012333 (2015)
Mao, Q.P., Wang, L., Zhao, S.M.: Plug-and-play round-robin differential phase-shift quantum key distribution. Sci. Rep. 7(1), 1–8 (2017)
Wang, X.B., Yang, L., Peng, C.Z., Pan, J.W.: Decoy-state quantum key distribution with both source errors and statistical fluctuations. New J. Phys. 11(7), 075006 (2009)
Gisin, N., Fasel, S., Kraus, B., Zbinden, H., Ribordy, G.: Trojan-horse attacks on quantum-key-distribution systems. Phys. Rev. A 73(2), 022320 (2006)
Fung, C.H.F., Qi, B., Tamaki, K., Lo, H.K.: Phase-remapping attack in practical quantum-key-distribution systems. Phys. Rev. A 75(3), 032314 (2007)
Sajeed, S., Radchenko, I., Kaiser, S., Bourgoin, J.P., Pappa, A., Monat, L., Makarov, V.: Attacks exploiting deviation of mean photon number in quantum key distribution and coin tossing. Phys. Rev. A 91(3), 032326 (2015)
Guo, H., Li, Z.Y., Peng, X.: Quantum Cryptography. National Defense Industry Press, Beijing (2016).. (( ( (in Chinese))))
Lütkenhaus, N.: Security against individual attacks for realistic quantum key distribution. Phys. Rev. A 61(5), 052304 (2000)
Brassard, G., Lütkenhaus, N., Mor, T., Sanders, B.C.: Limitations on practical quantum cryptography. Phys. Rev. Lett. 85(6), 1330 (2000)
Zhao, Y., Qi, B., Lo, H.K., Qian, L.: Security analysis of an untrusted source for quantum key distribution: passive approach. New J. Phys. 12(2), 023024 (2010)
Acknowledgements
The work is supported by the National Natural Science Foundation of China (61871234), the Postgraduate Research & Practice Innovation Program of Jiangsu Province (SJCX19-0251), and the open research fund of Key Lab of Broadband Wireless Communication and Sensor Network Technology (Nanjing University of Posts and Telecommunications), Ministry of Education (JZNY202104).
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Xue, K., Zhao, S., Mao, Q. et al. Plug-and-play sending-or-not-sending twin-field quantum key distribution. Quantum Inf Process 20, 320 (2021). https://doi.org/10.1007/s11128-021-03259-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-021-03259-x