Abstract
Recently, the twin field quantum key distribution (TF-QKD) protocols have been investigated extensively. In particular, an efficient protocol for TF-QKD with sending or not sending the coherent state has been given in. Here in this paper, we present results of practical sending-or-not-sending (SNS) twin field quantum key distribution. In real-life implementations, we need consider the following three requirements, a few different intensities rather than infinite number of different intensities, a phase slice of appropriate size rather than infinitely small size and the statistical fluctuations. We first show the decoy-state method with only a few different intensities and a phase slice of appropriate size. We then give a statistical fluctuation analysis for the decoy-state method. Numerical simulation shows that, the performance of our method is comparable to the asymptotic case for which the key size is large enough. Our method can beat the PLOB bound on secret key capacity. Our results show that practical implementations of the SNS quantum key distribution can be both secure and efficient.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) allows two parties, Alice and Bob, to share unconditional secret keys based on the laws of quantum physics1,2,3,4,5,6, even in the presence of an eavesdropper, Eve. However, in real-life implementations of QKD, its practical security is still questionable due to the device imperfections, such as the imperfect source7,8,9 and detectors. Fortunately, by using the decoy-state method10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25, it has been shown that the unconditional security of QKD can still be assured with an imperfect single-photon source. To avoid the detector side channel attacks, the measurement-device-independent QKD (MDI-QKD) was proposed26,27. The decoy-state MDI-QKD can remove all detector side-channel attacks with imperfect single-photon sources28,29,30,31,32,33.
With the developments10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44 in both theory and experiment, QKD is more and more hoped to be extensively applied in practice, though there are barriers for doing so. Among them, the transmission loss of photons for long distance QKD has become the major obstacle in practical implementations. Very recently, a milestone breakthrough was made under the name of twin-field quantum key distribution (TF-QKD)45 for long distance QKD with a key rate scales in square root of channel transmittance. To offer the information-theoretic-security, a number of upgraded variants were then proposed1,46,47,48. In particular, an efficient protocol for TF-QKD with sending or not sending the coherent state has been given in ref.1. In the sending-or-not-sending (SNS) protocol1, Alice and Bob do not take post selection for the bits in Z basis (signal pulses) and hence the traditional calculation formulas directly apply. Also, it is fault tolerant to misalignment errors in the long distance single-photon interference.
In practice, we need consider the situations with a few different intensities rather than infinite number of different intensities, a phase slice of appropriate size and the statistical fluctuations. It should be interesting to see whether the advantage in the twin-field QKD still holds with these conditions in practice. In this paper, we proceed further and analyse the performance of the SNS TF-QKD under the above real-life assumptions and we show that the advantage in distance and key rate still holds..
First, we reveal the decoy-state method with only a few different intensities and a phase slice of appropriate size to estimate the lower bound of the yield and the upper bound of the phase-flip error rate for the single-photon state. Furthermore, we also need to consider the statistical fluctuations. In order to improve the results, the instances for basis unmatched are also used to estimate the lower bound of the yield for the single-photon state, such as in Eq. (1).
Results
The decoy-state method with a few different intensities and a phase slice of appropriate size
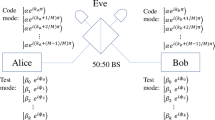
In the four-intensity decoy-state SNS protocol, Alice and Bob randomly choose the X-window (decoy pulses) and Z-window (signal pulses) to send or not to send a phase-randomized coherent pulse to an untrusted party, Charlie, who is expected to perform interference measurement. The protocol is detailed below.
-
1.
Alice and Bob repeat Steps 2–3, N times. All the public announcements by the legitimate users Alice and Bob are done over an authenticated channel.
-
2.
Alice and Bob randomly choose X-window and Z-window with probabilities pX and 1−pX respectively. Alice (Bob) prepares and sends the decoy pulses in her (his) X-window. Explicitly she (he) randomly choose one of three sources \({\rho }_{{\alpha }_{i}}\) with probability pi for i = 0, 1, 2, where \({\rho }_{{\alpha }_{0}}=\mathrm{|0}\rangle \langle \mathrm{0|}\) is the vacuum source, \({\rho }_{{\alpha }_{1}}\) and \({\rho }_{{\alpha }_{2}}\) are two phase-randomized coherent sources with intensity μ1 and μ2 (μ1 < μ2) respectively. In Z-window, Alice (Bob) puts down a bit value 1 and prepares and sends the phase-randomized coherent state \({\rho }_{{\alpha }_{z}}\) with probability pz, or puts down a bit value 0 and sends nothing else, i.e., sends the vacuum pulse with probability 1−pz.
-
3.
Charlie measures the incoming signals and records which detector clicks. When the quantum communication is over, he publicly announces all the information about the detection event. The situation when one and only one detector (detector 0 or detector 1) makes a count is denoted as an effective event. Alice and Bob collect all the data with effective events and discard all the others.
-
4.
Alice and Bob announce the basis information (X-window or Z-window) firstly. Then they announce the bit values and phase information corresponding to the effective events when Alice or Bob choose X-window. With these information, Alice and Bob obtain the observable Njk(j, k = 0, 1, 2, z) being the number of instances when Alice and Bob send state \({\rho }_{{\alpha }_{j}}\) and \({\rho }_{{\alpha }_{k}}\) respectively. Correspondingly, the lowercases njk are used to denote the number of effective events. The yields can be defined as Sjk = njk/Njk. Explicitly, we have N11, N22 and Nzz are the number of instances when Alice and Bob send state \({\rho }_{{\alpha }_{1}}\), \({\rho }_{{\alpha }_{2}}\) and \({\rho }_{{\alpha }_{z}}\) respectively. Furthermore, In order to improve the results, the instances for basis unmatched are also considered and
$$\begin{array}{rcl}{N}_{00} & = & {p}_{0}^{2}{N}_{X}+2{p}_{0}\mathrm{(1}-{p}_{z}){N}_{XZ},\\ {N}_{01} & = & {N}_{10}={p}_{0}{p}_{1}{N}_{X}+\mathrm{(1}-{p}_{z}){p}_{1}{N}_{XZ},\\ {N}_{02} & = & {N}_{20}={p}_{0}{p}_{2}{N}_{X}+\mathrm{(1}-{p}_{z}){p}_{2}{N}_{XZ},\end{array}$$(1)where p0 = 1−p1−p2 is the probability to send a vacuum pulse in X-window, \({N}_{X}={p}_{X}^{2}N\) is the number of instances when both Alice and Bob choose X-window and NXZ = pX(1−pX)N is the number of instances when Alice chooses X-window and Bob chooses Z-window.
-
5.
Define two sets \({C}_{{{\rm{\Delta }}}^{+}}\) and \({C}_{{{\rm{\Delta }}}^{-}}\) that contain the instances when both Alice and Bob send \({\rho }_{{\alpha }_{1}}\) in X-window with the phase information θA and θB falling into the slice |θA−θB| ≤ Δ/2 and |θA−θB−π| ≤ Δ/2 respectively. The number of instances in \({C}_{{{\rm{\Delta }}}^{\pm }}\) are \({N}_{11}^{{{\rm{\Delta }}}^{\pm }}=\frac{{\rm{\Delta }}}{2\pi }{N}_{11}\). The number of effective events corresponding to \({C}_{{{\rm{\Delta }}}^{\pm }}\) are denoted by \({n}_{11}^{{{\rm{\Delta }}}_{0}^{\pm }}\) and \({n}_{11}^{{{\rm{\Delta }}}_{1}^{\pm }}\) for detector 0 and detector 1 respectively.
-
6.
With these observables, Alice and Bob can estimate the lower bound of n1 and the upper bound of \({e}_{1}^{ph}\) by using the decoy-state methods shown below. Then the post-processing can be performed and the final key length is
where Nf is the number of final bits, n1 is the number of effective events caused by single-photon states in Z-basis when Alice decides sending while Bob decides not sending or Alice decides not sending while Bob decides sending, \({e}_{1}^{ph}\) is the phase-flip error rate for instances of n1, \(H(p)=-\,p{\mathrm{log}}_{2}(p)-\mathrm{(1}-p){\mathrm{log}}_{2}\mathrm{(1}-p)\) is the binary entropy function, f is the correction efficiency, nt is the number of effective events when both Alice and Bob choose Z-window and EZ is the corresponding bit-flip error rate.
Alternatively, we also have the equivalent formula for key rate per time window as shown in the section Methods.
In the above, for conciseness, we have omitted those mismatching time windows in a real protocol. For example, when Alice commits to a decoy window and Bob commits to a signal window. Although the events of these windows cannot be used for the final key distillation, the data for heralded events from these time windows can be used in the decoy-state analysis. The bit value encoding is defined by Alice or Bob’s decision on sending or not-sending in a signal window. As shown in ref.1, we can relate the bit values with local ancillary states in the virtual protocol. Clearly, there isn’t any definition confusion47 in the SNS protocol1.
A tricky point in the SNS protocol is that the traditional decoy-state method can still work. In this protocol, the random phase information of Z-windows are never announced therefore we can regard pulses of Z-basis as classical mixture of different photon number states properly. Note that, very importantly, the random phase information in Z windows can never been announced because otherwise, the elementary concepts such as the number of single-photon counts are illy defined. But, as shown in details in ref.1, the random phase information in X-windows can be post announced. Because we only want to verify the phase-flip error rate of Z windows. The phase-flip rate of Z windows is an objective fact, once it is verified, it is there. The post announced phase information does not change this objective facts because no matter how Eve takes action with the post announced information, the action is just Eve’s local action which can not make a difference to anything detectable to Alice and Bob.
Numerical simulation
In this section, we present some results of the numerical simulation. In order to show the efficiency of our method, without any loss of generality, we focus on the symmetric case where the two channel transmissions from Alice to Charlie and from Bob to Charlie are equal. We also assume that Charlie’s detectors are identical, i.e., they have the same dark count rates and detection efficiencies, and their detection efficiencies do not depend on the incoming signals. The results for the asymmetric case will be considered in the coming work. We shall estimate what values would be probably observed in the normal cases by the linear models as previously. The values of the experimental parameters used in the simulations are listed in Table 1.
We optimize all parameters, pX, p1, p2 pz, μ1, μ2, μz and Δ by the method of full optimization. The results of optimized key rate with different N by four-inensity decoy-state method and the result with theoretical PLOB bound49 are shown in Fig. 1. In it, we use the red solid line to denote the asymptotic results with infinite number of pulses. The optimal key rate with N = 1014, N = 1013 and N = 1012 are shown by the blue dotted line, the green dash-dot line and the black dashed line respectively. The result with theoretical PLOB bound is plotted by the thick magenta solid line. The numerical simulations show that the finite-size SNS protocol can overcome the PLOB bound. In Fig. 2, we plot the final key rates by the four-intensity and the three-intensity decoy-state methods with N = 1012. We can see that the optimal key rates for the three-intensity decoy-state method is nearly equal to the results for the four-intensity decoy-state method when we are aim for practically useable key-rates (such as 10−6 per-pulse). In Fig. 3, we plot the optimal value of Δ for different distances with N = 1012 by four-inensity decoy-state method. With this, we know that the optimal value of Δ are changed with different communication distance between Alice and Bob. The optimal value of Δ monotonically increases, to reduce the impact of statistical fluctuations, until it reaches a peak where the optimal key rate becomes decreasing dramatically and the error rate has a greater impact on the key rate than the statistical fluctuation.
Optimal key rate (bits per pulse) as a function of the distance by 4-inensity decoy-state method. The asymptotic result is shown in the red solid line. The blue dotted line, the green dash-dot line and the black dashed line are the results with N = 1014, N = 1013 and N = 1012, respectively. The solid magenta thick line illustrates the PLOB bound.
Also, according to the observed data there36, we use a linear loss model to estimate the actual loss in the experiment for 404 km of ultralow-loss optical fiber (0.16 dB/km). Assuming the same device parameters (pd = 7.2 × 10−8, ηd = 0.5525, f = 1.16, ε = 10−10, ea = 2% and N = 6.0 × 1014), we make the optimization by using our SNS protocol with the four-intensity decoy-state method shown above. We obtain a final key rate of 141 bit per second (bps), which is more than 4.4 × 105 times higher than the reported experimental result, 3.2 × 10−4 bps. Similarly, assuming the same device parameters (pd = 4.0 × 10−11, ηd = 0.5, f = 1.1, ε = 5.0 × 10−11, ea = 2% and N = 2.178 × 1014) for 421 km of ultralow-loss optical fiber (0.17 dB/km) in ref.50, we obtain a final key rate of 2.62 × 103 bit per second (bps), which is more than 1.05 × 104 times higher than the reported experimental result, 0.25 bps.
Discussion
In real setups of QKD, the practical situations with a few different intensities rather than infinite number of different intensities, a phase slice of appropriate size rather than infinitely small size and the statistical fluctuations must be considered. We first present the decoy-state method with a few different intensities and a phase slice of appropriate size. Then we show that the SNS protocol is a highly practical scheme even when the statistical fluctuations are considered. Numerical simulation shows that, the finite-size SNS protocol can exceed the PLOB bound. Our results show that practical implementations of the SNS TF-QKD can be both secure and efficient.
Methods
Decoy-state method analysis
In the protocol, Alice and Bob prepare and send the coherent pulses with randomized phase. The traditional formulas of decoy-state method can be applied directly. The coherent state whose phase is selected uniformly at random can be regard as a mixture of photon number states
where μj = |αj|2 is the intensity of the coherent state |αj〉. Then the state when Alice decides not sending and Bob decides to send \({\rho }_{{\alpha }_{k}}\) is \({\rho }_{{\alpha }_{0}{\alpha }_{k}}={e}^{-{\mu }_{k}}{\sum }_{n=0}^{\infty }\,{\mu }_{k}^{n}/n\mathrm{!|0}n\rangle \langle 0n|\). With these convex forms, the lower bound of the yield of the state \({\rho }_{{z}_{01}}=\mathrm{|01}\rangle \langle \mathrm{01|}\) can be written into the following form30
where S0k are the yield of the sources \({\rho }_{{\alpha }_{0}{\alpha }_{k}}\) for k = 1, 2, S00 is the yield when both Alice and Bob send the vacuum state. Similarly, the lower bound of the yield of the state \({\rho }_{{z}_{10}}=\mathrm{|10}\rangle \langle \mathrm{10|}\) can be written as
where Sj0 are the yield of the sources \({\rho }_{{\alpha }_{j}{\alpha }_{0}}\) for j = 1, 2. With Eqs (4) and (5), the lower bound of the yield of single-photon state in Z-basis, i.e., the state \({\rho }_{1}^{Z}=\frac{1}{2}({\rho }_{{z}_{01}}+{\rho }_{{z}_{10}})\), has the following form
Note: Replacing the source ρ2 used in Eqs (4–6) with the source ρz, we obtain the other lower bound of \({s}_{1}^{Z}\). With this replacement, source ρ2 is not used actually, then the four-intensity decoy-state method can be simplified to a three-intensity decoy-state method by taking p2 = 0. On the one hand, the three-intensity decoy-state method can be carried out easily in experiment. On the other hand, interested more in terms of practical key-rates instead of achieving the longest distance QKD possible (such as 10−6 per-pulse), the key rate of the three-intensity decoy-state method is only a little lower than (less than one percent for the cases discussed in the numerical simulation) the results for the four-intensity decoy-state method.
In the rest of this section, we show the formula to estimate the upper bound of \({e}_{1}^{ph}\) in Eq. (2) with the observable. The state of pulse pair when Alice sends the coherent state \(|{\alpha }_{1}^{A}=\sqrt{{\mu }_{1}}{e}^{i{\theta }_{A}}\rangle \) and Bob sends the coherent state \(|{\alpha }_{1}^{B}=\sqrt{{\mu }_{1}}{e}^{i{\theta }_{B}}\rangle \) is
Similarly, we also have
In Eqs (7) and (8), the n-photon twin-field state \(|{\psi }_{n}^{{\delta }^{\pm }}\rangle \) is defined as follows
where δ = θA−θB. For the state in set \({C}_{{{\rm{\Delta }}}^{+}}\), the phase is selected uniformly at random in the slice with |θA−θB| ≤ Δ/2. Equivalently, in set \({C}_{{{\rm{\Delta }}}^{+}}\), the phase θB chosen by Bob in \(|{\alpha }_{1}^{A}\rangle |{\alpha }_{1}^{B}\rangle \) can be regarded as uniformly distributed in [0, 2π) and the phase θA chosen by Alice satisfies the condition |δ| ≤ Δ/2. For any fixed value δ, we have
Similarly, we also have
Considering the single-photon twin-field states in \({C}_{{\rm{\Delta }}}={C}_{{{\rm{\Delta }}}^{+}}\cup {C}_{{{\rm{\Delta }}}^{-}}\) for a fixed δ, we have
So we know that the single-photon states in set CΔ and in Z-basis have the same density matrices. The probability to emit a single-photon pulse from CΔ is \({q}_{1}=2{\mu }_{1}{e}^{-2{\mu }_{1}}\). With this relations, we know that the bit-flip error rate of single-photon state in set CΔ is equal to the phase-flip error rate \({e}_{1}^{ph}\) asymptotically. The bit-flip error yield for all instances in set CΔ is
where Tk, k = Δ, Δ+, Δ− is the proportion of wrong effective events in Ck, e.g. in \({N}_{11}^{k}\). Attribute all the error to the single-photon state and the vacuum state, the upper bound of phase-flip error rate \({e}_{1}^{ph}\) can be estimated by
where \({\underline{s}}_{1}^{Z}\) is the lower bound of \({s}_{1}^{Z}\) given in Eq. (6). Then the final key rate of per pulse can be calculated with
where R is the final key rate, \({a}_{1}={\mu }_{z}{e}^{-{\mu }_{z}}\) is the probability to emit a single-photon state from source ρz, s1 is the yield of the single-photon state in Z-window when one party from Alice and Bob decides to send a signal states, \({e}_{1}^{ph}\) is the phase-flip error rate for those instance of s1, SZ and EZ are the yield and bit-flip error rate for instances when both Alice and Bob choose Z-window.
Statistical fluctuation analysis
In the real protocol with finite data size, in order to extract the secure final key, we have to consider the effect of statistical fluctuations. To obtain the lower bound value for s1 and the upper bound value for \({e}_{1}^{ph}\) in the real protocol with finite N, one can implement the idea of ref.25, i.e., treating the averaged yield. Accordingly, define 〈S〉 as the mean value of yield S. Note that even though Sjk(j, k = 0, 1, 2, z) are known values directly observed in the experiment, the mean values 〈Sjk〉 are not. However, given the observed values Sjk and the corresponding number of pulse pairs, the confidence lower and upper limits of 〈Sjk〉 can be calculated.
In order to obtain a tighter lower bound of \(\langle {s}_{1}^{Z}\rangle \), we need introduce the following two yields
Replacing the observed yields with their mean values in Eqs (6) and (15), we can formulate the lower bound of \(\langle {s}_{1}^{Z}\rangle \) and the upper bound of \(\langle {e}_{1}^{ph}\rangle \) respectively. Explicitly, we have
and
with
for \({\mathscr{U}}=S,\,T\) and k = 00, 1, 2 and Δ. By using the multiplicative form of the Chernoff bound29,33, with a fixed failure probability ε, we can give an interval of 〈Sk〉 with the observable Sk, \([{\underline{S}}_{k},\,{\bar{S}}_{k}]\), which can bound the value of 〈Sk〉 with a probability of at least 1−ε. Explicitly, with the function \({f}_{\delta }(x,\,y)=[-\,\mathrm{ln}(y\mathrm{/2)}+\sqrt{{(\mathrm{ln}(y\mathrm{/2))}}^{2}-8\,\mathrm{ln}(y\mathrm{/2)}x}]/\mathrm{(2}x)\), we have δ00 = fδ(N00S00, ε), δj = fδ((N0j + Nj0)Sj,ε), j = 1, 2 and \({\delta }_{{\rm{\Delta }}}={f}_{\delta }(({N}_{11}^{{{\rm{\Delta }}}^{+}}+{N}_{11}^{{{\rm{\Delta }}}^{-}}){T}_{{\rm{\Delta }}},\,\varepsilon )\).
With the mean values \(\langle {\underline{s}}_{1}^{Z}\rangle \) and \(\langle {\bar{e}}_{1}^{ph}\rangle \) defined in Eqs (19) and (20), the lower bound of the yield \({\underline{s}}_{1}\) and the upper bound of the phase-flip error rata \({\bar{e}}_{1}^{ph}\) corresponding to s1 in Eq. (16) can be estimated by29,33
where \({\delta }_{1}^{c}={f}_{\delta }({a}_{1}{N}_{zz}^{c}\langle {\underline{s}}_{1}^{Z}\rangle ,\,\varepsilon )\) and \({\delta }_{1}^{\text{'}c}={f}_{\delta }({a}_{1}{N}_{zz}^{c}{\underline{s}}_{1}\langle {\bar{e}}_{1}^{ph}\rangle ,\,\varepsilon )\) with \({N}_{zz}^{c}=2{p}_{z}\mathrm{(1}-{p}_{z}){N}_{zz}\) and \({a}_{1}={\mu }_{z}{e}^{-{\mu }_{z}}\) being the probability to emit a single-photon state from source ρz.
With the lower bound of s1 and the upper bound of \({e}_{1}^{ph}\) in Eq. (22), the final key rate can be calculated with Eq. (16).
References
Wang, X.-B., Yu, Z.-W. & Hu, X.-L. Twin-field quantum key distribution with large misalignment error. Physical Review A 98, 062323 (2018).
Bennett, C. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, 175–179 (1984).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Reviews of modern physics 74, 145 (2002).
Gisin, N. & Thew, R. Quantum communication. Nature photonics 1, 165 (2007).
Dušek, M., Lütkenhaus, N. & Hendrych, M. Quantum cryptography. Progress in Optics 49, 381–454 (2006).
Scarani, V. et al. The security of practical quantum key distribution. Reviews of modern physics 81, 1301 (2009).
Brassard, G., Lütkenhaus, N., Mor, T. & Sanders, B. C. Limitations on practical quantum cryptography. Physical Review Letters 85, 1330 (2000).
Lütkenhaus, N. Security against individual attacks for realistic quantum key distribution. Physical Review A 61, 052304 (2000).
Lütkenhaus, N. & Jahma, M. Quantum key distribution with realistic states: photon-number statistics in the photon-number splitting attack. New Journal of Physics 4, 44 (2002).
Inamori, H., Lütkenhaus, N. & Mayers, D. Unconditional security of practical quantum key distribution. The European Physical Journal D 41, 599 (2007).
Gottesman, D., Lo, H.-K., Lutkenhaus, N. & Preskill, J. Security of quantum key distribution with imperfect devices. In Information Theory, 2004. ISIT 2004. Proceedings. International Symposium on, 136 (IEEE, 2004).
Hwang, W.-Y. Quantum key distribution with high loss: toward global secure communication. Physical Review Letters 91, 057901 (2003).
Wang, X.-B. Beating the photon-number-splitting attack in practical quantum cryptography. Physical review letters 94, 230503 (2005).
Lo, H.-K., Ma, X. & Chen, K. Decoy state quantum key distribution. Physical review letters 94, 230504 (2005).
Adachi, Y., Yamamoto, T., Koashi, M. & Imoto, N. Simple and efficient quantum key distribution with parametric down-conversion. Physical review letters 99, 180503 (2007).
Hayashi, M. Practical evaluation of security for quantum key distribution. Physical Review A 74, 022307 (2006).
Hayashi, M. Upper bounds of eavesdropper’s performances in finite-length code with the decoy method. Physical Review A 76, 012329 (2007).
Rosenberg, D. et al. Long-distance decoy-state quantum key distribution in optical fiber. Physical review letters 98, 010503 (2007).
Schmitt-Manderbach, T. et al. Experimental demonstration of free-space decoy-state quantum key distribution over 144 km. Physical Review Letters 98, 010504 (2007).
Peng, C.-Z. et al. Experimental long-distance decoy-state quantum key distribution based on polarization encoding. Physical review letters 98, 010505 (2007).
Yuan, Z., Sharpe, A. & Shields, A. Unconditionally secure one-way quantum key distribution using decoy pulses. Applied physics letters 90, 011118 (2007).
Wang, X.-B., Peng, C.-Z., Zhang, J., Yang, L. & Pan, J.-W. General theory of decoy-state quantum cryptography with source errors. Physical Review A 77, 042311 (2008).
Hu, J.-Z. & Wang, X.-B. Reexamination of the decoy-state quantum key distribution with an unstable source. Physical Review A 82, 012331 (2010).
Wang, X.-B., Hiroshima, T., Tomita, A. & Hayashi, M. Quantum information with gaussian states. Physics reports 448, 1–111 (2007).
Wang, X.-B., Yang, L., Peng, C.-Z. & Pan, J.-W. Decoy-state quantum key distribution with both source errors and statistical fluctuations. New Journal of Physics 11, 075006 (2009).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Physical review letters 108, 130502 (2012).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Physical review letters 108, 130503 (2012).
Wang, X.-B. Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Physical Review A 87, 012320 (2013).
Curty, M. et al. Finite-key analysis for measurement-device-independent quantum key distribution. Nature communications 5, 3732 (2014).
Yu, Z.-W., Zhou, Y.-H. & Wang, X.-B. Three-intensity decoy-state method for measurement-device-independent quantum key distribution. Physical Review A 88, 062339 (2013).
Xu, F., Xu, H. & Lo, H.-K. Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Physical Review A 89, 052333 (2014).
Yu, Z.-W., Zhou, Y.-H. & Wang, X.-B. Statistical fluctuation analysis for measurement-device-independent quantum key distribution with three-intensity decoy-state method. Physical Review A 91, 032318 (2015).
Zhou, Y.-H., Yu, Z.-W. & Wang, X.-B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Physical Review A 93, 042324 (2016).
Comandar, L. et al. Quantum key distribution without detector vulnerabilities using optically seeded lasers. Nature Photonics 10, 312 (2016).
Wang, C. et al. Measurement-device-independent quantum key distribution robust against environmental disturbances. Optica 4, 1016–1023 (2017).
Yin, H.-L. et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Physical review letters 117, 190501 (2016).
Koashi, M. Simple security proof of quantum key distribution based on complementarity. New Journal of Physics 11, 045018 (2009).
Sasaki, T., Yamamoto, Y. & Koashi, M. Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509, 475 (2014).
Chau, H. Quantum key distribution using qudits that each encode one bit of raw key. Physical Review A 92, 062324 (2015).
Azuma, K., Tamaki, K. & Munro, W. J. All-photonic intercity quantum key distribution. Nature communications 6, 10171 (2015).
Takesue, H., Sasaki, T., Tamaki, K. & Koashi, M. Experimental quantum key distribution without monitoring signal disturbance. Nature Photonics 9, 827 (2015).
Roberts, G. et al. Experimental measurement-device-independent quantum digital signatures. Nature Communications 8, 1098 (2017).
Liao, S.-K. et al. Satellite-to-ground quantum key distribution. Nature 549, 43 (2017).
Liao, S.-K. et al. Satellite-relayed intercontinental quantum network. Physical review letters 120, 030501 (2018).
Lucamarini, M., Yuan, Z., Dynes, J. & Shields, A. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 557, 400 (2018).
Tamaki, K., Lo, H. -K., Wang, W. & Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv preprint arXiv:1805.05511 (2018).
Ma, X., Zeng, P. & Zhou, H. Phase-matching quantum key distribution. Physical Review X 8, 031043 (2018).
Cui, C. et al. Phase-matching quantum key distribution without phase post-selection. arXiv preprint arXiv:1807.02334 (2018).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nature communications 8, 15043 (2017).
Boaron, A. et al. Secure quantum key distribution over 421 km of optical fiber. Physical review letters 121, 190502 (2018).
Acknowledgements
We acknowledge the financial support in part by Ministration of Science and Technology of China through The National Key Research and Development Program of China grant No. 2017YFA0303901; National Natural Science Foundation of China grant No. 11474182, 11774198 and U1738142.
Author information
Authors and Affiliations
Contributions
X.B.W. and Z.W.Y. proposed this work. X.L.H., C.J. and H.X. did the calculations and drew the figures. Z.W.Y. and X.L.H. wrote the manuscript.
Corresponding author
Ethics declarations
Competing Interests
The authors declare no competing interests.
Additional information
Publisher’s note: Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this license, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Yu, ZW., Hu, XL., Jiang, C. et al. Sending-or-not-sending twin-field quantum key distribution in practice. Sci Rep 9, 3080 (2019). https://doi.org/10.1038/s41598-019-39225-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-019-39225-y
- Springer Nature Limited
This article is cited by
-
Parameter optimization in decoy-state phase-matching quantum key distribution
Quantum Information Processing (2023)
-
2×N twin-field quantum key distribution network configuration based on polarization, wavelength, and time division multiplexing
npj Quantum Information (2022)
-
Twin-field quantum key distribution over 830-km fibre
Nature Photonics (2022)
-
More optimal relativistic quantum key distribution
Scientific Reports (2022)
-
Coherent phase transfer for real-world twin-field quantum key distribution
Nature Communications (2022)