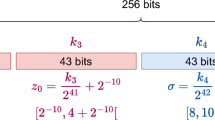
Abstract
The security of digital information is one of the significant problems of the existing world. In this work, we have proposed a dual-layer information hiding mechanism. We have utilized 3-Cell Cellular Neural Network (CNN) system to generate a pseudorandom number generator to fulfill diffusion requirements of a cryptosystem, and then utilizing highly non-linear substitution boxes (S-boxes) to complete the confusion process of cryptosystem design. The encrypted data are the hide in the cover image, the data hiding process comprises three steps, generation of transform matrix from the cover image, embedding matrix from transform matrix and secret encrypted image and the last step is to obtain a stego image. Less computational complexity without affecting the strength of the security scheme is the need of the day. Due to the simplicity and computational efficiency of the diffusion process of a 3-cell cellular neural network, the confusion created by predefined S-boxes, and the data hiding scheme effectively reduces the time for encryption and data hiding. The proposed scheme has been tested using state-of-the-art key performance indicators including information theory-based analysis, Histogram based analysis, analysis based on pixels difference, correlation-based measurements, and distance-based analysis. the results of this analysis show the efficiency and effectiveness of the proposed system.








Similar content being viewed by others
Data availability
The data set (s) supporting the conclusions of this article is (are) included within the article.
References
Alanazi, Ammar S (2021) A dual layer secure data encryption and hiding scheme for color images using the three-dimensional chaotic map and lah transformation. IEEE Access 9:26583–26592
Alghafis A, Firdousi F, Khan M, Batool SI, Amin M (2020) An efficient image encryption sheme based on chaotic and Deoxyribonucleic acid sequencing,. Math Comput Simul 177:441–466
Alghafis A, Waseem HM, Khan M et al (2020) A novel digital contents privacy scheme based on quantum harmonic oscillator and schrodinger paradox. Wireless Netw. https://doi.org/10.1007/s11276-020-02363-7
Khan M, Khan L, Hazzazi MM, Jamal SS, Hussain I (2022) Image encryption scheme for multi-focus images for visual sensors network. Multimed Tools Appl 81(12):16353–16370
Ali KM, Khan M (2019) A new construction of confusion component of block ciphers. Multimed Tools Appl 78:32585–32604
Arena P, Caponetto R, Fortuna L, Porto D (1998) Bifurcation and chaos in noninteger order cellular neural networks. Int J Bifurcat Chaos 8(7):1527–1539
Arshad U, Khan M, Shaukat S, Amin M, Shah T (2020) An efficient image privacy scheme based on nonlinear chaotic system and linear canonical transformation. Phys A: Stat Mech Appl 546:123458
Batool SI, Shah T, Khan M (2014) A color image watermarking scheme based on affine transformation and S 4 permutation. Neural Comput Appl 25(7):2037–2045
Farah MAB, Farah A, Farah T (2020) An image encryption scheme based on a new hybrid chaotic map and optimized substitution box,. Nonlinear Dyn 99:3041–3064
Gan Z, Chai X, Zhang M, Lu Y (2018) A double color image encryption scheme based on three dimensional Brownian motion. Multimed Tools Appl 77:27919–27953
He Y, Zhang YQ, Wang XY (2020) A new image encryption algorithem based on two dimensional spatiotemporal chaotic system. Neural Comput Appl 32:247–260
Jamal SS, Shah T, Farwa S, Khan MU (2019) A new technique of frequency domain watermarking based on a local ring. Wirel Netw 25(4):1491–1503
Jamal SS, Farwa S, Alkhaldi AIH, Aslam M, Gondal MAG (2019) A robust steganographic technique based on improved chaotic-range systems. Chin J Phys 61:301–309
Kaur M, Kumar V (2020) A comprehensive review on image encryption techniques. Arch Comput Methods Eng 15–43:27
Kaur M, Kumar V (2020) A comprehensive review on image encryption techniques. Arch Comput Methods Eng 43:15–27
Khan M, Shah T (2014) A construction of novel chaos base nonlinear component of block cipher. Nonlinear Dyn 76:377–382
Khan M, Masood F (2019) A novel chaotic image encryption technique based on multiple discrete dynamical maps. Multimed Tools Appl 358:26203–26222
Khan M, Jamal SS, Waqas UA (2020) A novel combination of information hiding and confidentiality scheme. Multimed Tools Appl 79:30983–31005
Khan S, Han L, Lu H, Butt KK, Bachira G, Khan NU (2019) A new hybrid image encryption algorithm based on 2D-CA, FSM-DNA rule generator, and FSBI. IEEE Access 7:81333–81350
Khan S, Han L, Lu H, Butt KK, Bachira G, Khan NU (2019) A new hybrid image encryption algorithm based on 2D-CA, FSM-DNA rule generator, and FSBI. IEEE Access 7:81333–81350
Malik A, Wang H, Chen T, Yang T, Khan AN, Wu H, ... Hu Y (2019) Reversible data hiding in homomorphically encrypted image using interpolation technique. J Inf Secur Appl 48:102374
Marvel L, Boncelet C, Retter CT (2020) Spread spectrum image steganography,. IEEE Trans Image Process 8(8):1075–1083
Norouzi B, Mirzakuchaki S (2017) An image encryption algorithem based on DNA sequence operations and cellular neural network,. Multimed Tools Appl 76:13681–13701
Özkaynak F (2020) On the effect of chaotic system in performance characteristics of chaos based s-box designs. Phys A: Stat Mech Appl 550:124072
Özkaynak F, Özer AB (2010) A method for designing strong S-Boxes based on chaotic Lorenz system. Phys Lett A 374(36):3733–3738
Khan LS, Hazzazi MM, Khan M, Jamal SS (2021) A novel image encryption based on rossler map diffusion and particle swarm optimization generated highly non-linear substitution boxes. Chin J Phys 72:558–574
Seyedzadeh SM, Norouzi B, Mirzakuchaki S (2015) A novel color image encryption algorithm based on spatial permutation and quantum chaotic map. Nonlinear Dyn 81:511–529
Wua HT, Cheung Ym, Yang Z, Tang S (2019) A high-capacity reversible data hiding method for homomorphic encrypted images. Elsevier: J Vis Commun Image R 62:87–96
Younas I, Khan M (2018) A new efficient digital image encryption based on inverse left almost semi group and Lorenz chaotic system. Entropy 20(12):913
Yu C, Li J, Li X, Ren X, Gupta BB (2017) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77:4585–4608
Zhang Q, Guo L, Wei X (2013) A novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Optik - Int J Light Electron Optics 124(18):3596–3600
Zhang LY, Hu X, Liu Y, Wong K-W (2017) A chaotic image encryption scheme owning temp-value feedback. Commun Nonlinear Sci Numer Simul 19(10):3653–3659
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
There is no conflict of interest among the authors regarding the publication of this article.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Said, L., Alanazi, A.S. & Khan, M. A novel dual-layer security scheme based on 3-cell cellular neural network encryption and data hiding scheme for color images. Multimed Tools Appl 82, 6127–6145 (2023). https://doi.org/10.1007/s11042-022-13621-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-13621-5