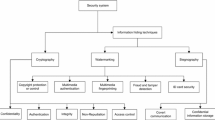
Abstract
Image encryption techniques play a significant role in multimedia applications to secure and authenticate digital images. This paper presents a comprehensive study of various image encryption techniques. This paper covers the most significant developments in meta-heuristic based image encryption techniques. The various attacks and performance measures related to image encryption techniques have also been studied. The existing techniques are analyzed with respect to differential, statistical, and key analyses. The main goal of this paper is to give a broad perspective on characteristics of image encryption techniques. The paper concludes by discussing significant advancements in the field of image encryption and highlighting future challenges.














Similar content being viewed by others
References
Ghebleh M, Kanso A, Noura H (2014) An image encryption scheme based on irregularly decimated chaotic maps. Signal Process Image Commun 29(5):618–627
Sivakumar T, Venkatesan R (2015) A novel image encryption using calligraphy based scan method and random number. KSII Trans Internet Inf Syst 9(6):2317–2337
Forouzan BA, Mukhopadhyay D (2011) Cryptography and network security (Sie). McGraw-Hill Education, New York
Bi N, Sun Q, Huang D, Yang Z, Huang J (2007) Robust image watermarking based on multiband wavelets and empirical mode decomposition. IEEE Trans Image Process 16(8):1956–1966
Li XW, Kim ST (2013) Optical 3D watermark based digital image watermarking for telemedicine. Opt Lasers Eng 51(12):1310–1320
Belazi A, El-Latif AAA, Belghith S (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process 128:155–170
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Zhao G, Chen G, Fang J, Xu G (2011) Block cipher design: generalized single-use-algorithm based on chaos. Tsinghua Sci Technol 16(2):194–206
El-Samie FEA, Ahmed HEH, Elashry IF, Shahieen MH, Faragallah OS, El-Rabaie E-SM, Alshebeili SA (2013) Image encryption: a communication perspective. CRC Press, Boca Raton
Chai X, Gan Z, Yang K, Chen Y, Liu X (2017) An image encryption algorithm based on the memristive hyperchaotic system, cellular automata and DNA sequence operations. Signal Process Image Commun 52:6–19
Zhang W, Wong K-W, Yu H, Zhu Z-L (2013) An image encryption scheme using reverse 2-dimensional chaotic map and dependent diffusion. Commun Nonlinear Sci Numer Simul 18(8):2066–2080
El-Latif AAA, Niu X (2013) A hybrid chaotic system and cyclic elliptic curve for image encryption. AEU Int J Electron Commun 67(2):136–143
Li XW, Cho SJ, Kim ST (2014) A 3D image encryption technique using computer-generated integral imaging and cellular automata transform. Opt Int J Light Electron Opt 125(13):2983–2990
Mehra I, Nishchal NK (2015) Optical asymmetric image encryption using gyrator wavelet transform. Opt Commun 354:344–352
Rawat N, Kim B, Kumar R (2016) Fast digital image encryption based on compressive sensing using structurally random matrices and arnold transform technique. Optik Int J Light Electron Opt 127(4):2282–2286
Abbas NA (2016) Image encryption based on independent component analysis and Arnolds cat map. Egypt Inform J 17(1):139–146
Cao X, Wei X, Guo R, Wang C (2017) No embedding: a novel image cryptosystem for meaningful encryption. J Vis Commun Image Represent 44:236–249
Zhang Y, Xu B, Zhou N (2017) A novel image compression–encryption hybrid algorithm based on the analysis sparse representation. Opt Commun 392:223–233
Khan M, Shah T (2014) A novel statistical analysis of chaotic S-box in image encryption. 3D Res 5(3):1–8
Gu G, Ling J (2014) A fast image encryption method by using chaotic 3D cat maps. Optik Int J Light Electron Opt 125(17):4700–4705
Huang X, Ye G (2014) An efficient self-adaptive model for chaotic image encryption algorithm. Commun Nonlinear Sci Numer Simul 19(12):4094–4104
Ono A, Kohda T (2007) Solvable three-dimensional rational chaotic map defined by Jacobian elliptic functions. Int J Bifurc Chaos 17(10):3645–3650
Chen G, Zhang D, Chen Q, Zhou D (2012) The characteristic of different chaotic sequences for compressive sensing. In: 2012 5th international congress on image and signal processing (CISP). IEEE, pp 1475–1479
Umamageswari A, Suresh G (2013) Security in medical image communication with Arnold’s cat map method and reversible watermarking. In: 2013 international conference on circuits, power and computing technologies (ICCPCT). IEEE, pp 1116–1121
Salleh M, Ibrahim S, Isnin IF (2003) Enhanced chaotic imageencryption algorithm based on Baker’s map. In: Proceedings of the 2003 international symposium on circuits and systems, 2003. ISCAS’03, vol 2. IEEE, pp II–II
Hu H, Liu L, Ding N (2013) Pseudorandom sequence generator based on the chen chaotic system. Comput Phys Commun 184(3):765–768
Chattopadhyay D, Mandal M, Nandi D (2011) Symmetric key chaotic image encryption using circle map. Indian J Sci Technol 4(5):593–599
Shastry MC, Nagaraj N, Vaidya PG (2006) The b-exponential map: a generalization of the logistic map, and its applications ingenerating pseudo-random numbers. ArXiv preprint arXiv:cs/0607069
Gao T, Chen Z (2008) A new image encryption algorithm based on hyper-chaos. Phys Lett A 372(4):394–400
Wei-Bin C, Xin Z (2009) Image encryption algorithm based on Henon chaotic system. In: International conference on image analysis and signal processing, 2009. IASP 2009. IEEE, pp 94–97
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24(9):926–934
Zhen W, Xia H, Yu-Xia L, Xiao-Na S (2013) A new image encryption algorithm based on the fractional-order hyperchaotic Lorenz system. Chin Phys B 22(1):010504
Kadir A, Hamdulla A, Guo W-Q (2014) Color image encryption using skew tent map and hyper chaotic system of 6th-order CNN. Optik Int J Light Electron Opt 125(5):1671–1675
Enayatifar R, Sadaei HJ, Abdullah AH, Lee M, Isnin IF (2015) A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt Lasers Eng 71:33–41
Hamza R, Titouna F (2016) A novel sensitive image encryption algorithm based on the Zaslavsky chaotic map. Inf Secur J Glob Perspect 25(4–6):162–179
Behnia S, Akhshani A, Mahmodi H, Akhavan A (2008) A novel algorithm for image encryption based on mixture of chaotic maps. Chaos Solitons Fractals 35(2):408–419
Ye G (2010) Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recognit Lett 31(5):347–354
Li C, Lin D, Lü J (2017) Cryptanalyzing an image-scrambling encryption algorithm of pixel bits. IEEE MultiMed 24(3):64–71
Zhu Z-L, Zhang W, Wong K-W, Yu H (2011) A chaos-based symmetric image encryption scheme using a bit-level permutation. Inf Sci 181(6):1171–1186
Zhang Y-Q, Wang X-Y (2014) Analysis and improvement of a chaos-based symmetric image encryption scheme using a bit-level permutation. Nonlinear Dyn 77(3):687–698
Li C (2016) Cracking a hierarchical chaotic image encryption algorithm based on permutation. Signal Process 118:203–210
Mirzaei O, Yaghoobi M, Irani H (2012) A new image encryption method: parallel sub-image encryption with hyper chaos. Nonlinear Dyn 67(1):557–566
Kanso A, Ghebleh M (2012) A novel image encryption algorithm based on a 3D chaotic map. Commun Nonlinear Sci Numer Simul 17(7):2943–2959
Wang X-Y, Wang T, Xu D-H, Chen F (2014) A selective image encryption based on couple spatial chaotic systems. Int J Mod Phys B 28(06):1450023
Zhang Y-Q, Wang X-Y (2014) A symmetric image encryption algorithm based on mixed linear-nonlinear coupled map lattice. Inf Sci 273:329–351
Wang X-Y, Gu S-X, Zhang Y-Q (2015) Novel image encryption algorithm based on cycle shift and chaotic system. Opt Lasers Eng 68:126–134
Liu W, Sun K, Zhu C (2016) A fast image encryption algorithm based on chaotic map. Opt Lasers Eng 84:26–36
Wang X, Wang Q, Zhang Y (2015) A fast image algorithm based on rows and columns switch. Nonlinear Dyn 79(2):1141–1149
Farajallah M, El Assad S, Deforges O (2016) Fast and secure chaos-based cryptosystem for images. Int J Bifurc Chaos 26(02):1650021
Chen E, Min L, Chen G (2017) Discrete chaotic systems with one-line equilibria and their application to image encryption. Int J Bifurc Chaos 27(03):1750046
Hua Z, Zhou Y (2017) Design of image cipher using block-based scrambling and image filtering. Inf Sci 396:97–113
Pak C, Huang L (2017) A new color image encryption using combination of the 1D chaotic map. Signal Process 138:129–137
Li Y, Wang C, Chen H (2017) A hyper-chaos-based image encryption algorithm using pixel-level permutation and bit-level permutation. Opt Lasers Eng 90:238–246
Gao H, Zhang Y, Liang S, Li D (2006) A new chaotic algorithm for image encryption. Chaos Solitons Fractals 29(2):393–399
Wang Y, Wong K-W, Liao X, Chen G (2011) A new chaos-based fast image encryption algorithm. Appl Soft Comput 11(1):514–522
Chen J-X, Zhu Z-L, Fu C, Yu H (2015) Optical image encryption scheme using 3-D chaotic map based joint image scrambling and random encoding in gyrator domains. Opt Commun 341:263–270
Zhou N, Pan S, Cheng S, Zhou Z (2016) Image compression–encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt Laser Technol 82:121–133
Wu X, Wang D, Kurths J, Kan H (2016) A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inf Sci 349:137–153
Zhang Q, Liu L, Wei X (2014) Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEU Int J Electron Commun 68(3):186–192
Li X, Wang L, Yan Y, Liu P (2016) An improvement color image encryption algorithm based on DNA operations and real and complex chaotic systems. Optik Int J Light Electron Opt 127(5):2558–2565
Wu X, Kan H, Kurths J (2015) A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl Soft Comput 37:24–39
Kumar M, Iqbal A, Kumar P (2016) A new RGB image encryption algorithm based on DNA encoding and elliptic curve Diffie–Hellman cryptography. Signal Process 125:187–202
Yuan Wang X, Li Zhang H, Mei Bao X (2016) Color image encryption scheme using CML and DNA sequence operations. Biosystems 144:18–26
Mondal B, Mandal T (2017) A light weight secure image encryption scheme based on chaos DNA computing. J King Saud Univ Comput Inf Sci 29(4):499–504
Wang X, Luan D (2013) A novel image encryption algorithm using chaos and reversible cellular automata. Commun Nonlinear Sci Numer Simul 18(11):3075–3085
Li X, Xiao D, Wang Q-H (2018) Error-free holographic frames encryption with CA pixel-permutation encoding algorithm. Opt Lasers Eng 100:200–207
Wang X, Luan D (2013) A novel image encryption algorithm using chaos and reversible cellular automata. Commun Nonlinear Sci Numer Simul 18(11):3075–3085
Bakhshandeh A, Eslami Z (2013) An authenticated image encryption scheme based on chaotic maps and memory cellular automata. Opt Lasers Eng 51(6):665–673
Ping P, Xu F, Wang Z-J (2014) Image encryption based on non-affine and balanced cellular automata. Signal Process 105:419–429
Mohamed FK (2014) A parallel block-based encryption schema for digital images using reversible cellular automata. Eng Sci Technol Int J 17(2):85–94
Enayatifar R, Sadaei HJ, Abdullah AH, Lee M, Isnin IF (2015) A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt Lasers Eng 71:33–41
Yang Y-G, Tian J, Lei H, Zhou Y-H, Shi W-M (2016) Novel quantum image encryption using one-dimensional quantum cellular automata. Inf Sci 345:257–270
Li X, Li C, Lee I-K (2016) Chaotic image encryption using pseudo-random masks and pixel mapping. Signal Process 125:48–63
Niyat AY, Moattar MH, Torshiz MN (2017) Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt Lasers Eng 90:225–237
Enayatifar R, Abdullah AH, Isnin IF (2014) Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Opt Lasers Eng 56:83–93
Souici I, Seridi H, Akdag H (2011) Images encryption by the use of evolutionary algorithms. Analog Integr Circuits Signal Process 69(1):49–58
Abdullah AH, Enayatifar R, Lee M (2012) A hybrid genetic algorithm and chaotic function model for image encryption. AEU Int J Electron Commun 66(10):806–816
Sreelaja N, Pai GV (2012) Stream cipher for binary image encryption using ant colony optimization based key generation. Appl Soft Comput 12(9):2879–2895
Enayatifar R, Abdullah AH, Lee M (2013) A weighted discrete imperialist competitive algorithm (WDICA) combined with chaotic map for image encryption. Opt Lasers Eng 51(9):1066–1077
Talarposhti KM, Jamei MK (2016) A secure image encryption method based on dynamic harmony search (DHS) combined with chaotic map. Opt Lasers Eng 81:21–34
Behnia S, Akhavan A, Akhshani A, Samsudin A (2013) Image encryption based on the Jacobian elliptic maps. J Syst Softw 86(9):2429–2438
Nagaraj S, Raju G, Rao KK (2015) Image encryption using elliptic curve cryptograhy and matrix. Procedia Comput Sci 48:276–281
Liu H, Wang X, Kadir A (2013) Color image encryption using Choquet fuzzy integral and hyper chaotic system. Opt Int J Light Electron Opt 124(18):3527–3533
Seyedzadeh SM, Norouzi B, Mirzakuchaki S (2014) RGB color image encryption based on Choquet fuzzy integral. J Syst Softw 97:128–139
Chen H, Du X, Liu Z, Yang C (2013) Color image encryption based on the affine transform and gyrator transform. Opt Lasers Eng 51(6):768–775
Singh N, Sinha A (2009) Gyrator transform-based optical image encryption, using chaos. Opt Lasers Eng 47(5):539–546
Wang Q, Guo Q, Lei L, Zhou J (2013) Linear exchanging operation and random phase encoding in gyrator transform domain for double image encryption. Opt Int J Light Electron Opt 124(24):6707–6712
Wang Q, Guo Q, Lei L (2014) Multiple-image encryption system using cascaded phase mask encoding and a modified Gerchberg–Saxton algorithm in gyrator domain. Opt Commun 320:12–21
Abuturab MR (2015) An asymmetric single-channel color image encryption based on hartley transform and gyrator transform. Opt Lasers Eng 69:49–57
Chen J-X, Zhu Z-L, Fu C, Zhang L-B, Yu H (2015) Analysis and improvement of a double-image encryption scheme using pixel scrambling technique in gyrator domains. Opt Lasers Eng 66:1–9
Yao L, Yuan C, Qiang J, Feng S, Nie S (2017) An asymmetric color image encryption method by using deduced gyrator transform. Opt Lasers Eng 89:72–79
Wang Y-Y, Wang Y-R, Wang Y, Li H-J, Sun W-J (2007) Optical image encryption based on binary Fourier transform computer-generated hologram and pixel scrambling technology. Opt Lasers Eng 45(7):761–765
Guo Q, Liu Z, Liu S (2010) Color image encryption by using arnold and discrete fractional random transforms in ihs space. Opt Lasers Eng 48(12):1174–1181
Li Y, Zhang F, Li Y, Tao R (2015) Asymmetric multiple-image encryption based on the cascaded fractional Fourier transform. Opt Lasers Eng 72:18–25
Li X-W, Lee I-K (2015) Modified computational integral imaging-based double image encryption using fractional Fourier transform. Opt Lasers Eng 66:112–121
Ran Q, Yuan L, Zhao T (2015) Image encryption based on nonseparable fractional Fourier transform and chaotic map. Opt Commun 348:43–49
Zhao H, Liu J, Jia J, Zhu N, Xie J, Wang Y (2013) Multiple-image encryption based on position multiplexing of Fresnel phase. Opt Commun 286:85–90
Wang Q, Guo Q, Lei L, Zhou J (2014) Single-beam image encryption using spatially separated ciphertexts based on interference principle in the Fresnel domain. Opt Commun 333:151–158
Wang Y, Quan C, Tay C (2014) Nonlinear multiple-image encryption based on mixture retrieval algorithm in Fresnel domain. Opt Commun 330:91–98
Wang Y, Quan C, Tay C (2015) Optical color image encryption without information disclosure using phase-truncated Fresnel transform and a random amplitude mask. Opt Commun 344:147–155
Luo Y, Du M, Liu J (2015) A symmetrical image encryption scheme in wavelet and time domain. Commun Nonlinear Sci Numer Simul 20(2):447–460
Kanso A, Ghebleh M (2017) An algorithm for encryption of secret images into meaningful images. Opt Lasers Eng 90:196–208
Lima JB, Madeiro F, Sales F (2015) Encryption of medical images based on the cosine number transform. Signal Process Image Commun 35:1–8
Wu J, Guo F, Liang Y, Zhou N (2014) Triple color images encryption algorithm based on scrambling and the reality-preserving fractional discrete cosine transform. Opt Int J Light Electron Opt 125(16):4474–4479
Yaru L, Jianhua W (2015) New image encryption combining fractional DCT via polynomial interpolation with dependent scrambling and diffusion. J China Univ Posts Telecommun 22(5):1–9
Li X-W, Wang Q-H, Kim S-T, Lee I-K (2016) Encrypting 2D/3D image using improved lensless integral imaging in Fresnel domain. Opt Commun 381:260–270
Candes EJ, Wakin MB (2008) An introduction to compressive sampling. IEEE Signal Process Mag 25(2):21–30
Zhang Y, Zhang LY, Zhou J, Liu L, Chen F, He X (2016) A review of compressive sensing in information security field. IEEE Access 4:2507–2519
Zhang Y, Zhou J, Chen F, Zhang LY, Wong K-W, He X, Xiao D (2016) Embedding cryptographic features in compressive sensing. Neurocomputing 205:472–480
Lu P, Xu Z, Lu X, Liu X (2013) Digital image information encryption based on compressive sensing and double random-phase encoding technique. Opt Int J Light Electron Opt 124(16):2514–2518
Zhou N, Zhang A, Wu J, Pei D, Yang Y (2014) Novel hybrid image compression–encryption algorithm based on compressive sensing. Opt Int J Light Electron Opt 125(18):5075–5080
Zhou N, Li H, Wang D, Pan S, Zhou Z (2015) Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt Commun 343:10–21
Zhou N, Yang J, Tan C, Pan S, Zhou Z (2015) Double-image encryption scheme combining DWT-based compressive sensing with discrete fractional random transform. Opt Commun 354:112–121
Zhou N, Pan S, Cheng S, Zhou Z (2016) Image compression-encryption scheme based on hyper-chaotic system and 2D compressive sensing. Opt Laser Technol 82:121–133
Leihong Z, Zilan P, Luying W, Xiuhua M (2016) High-performance compression and double cryptography based on compressive ghost imaging with the fast Fourier transform. Opt Lasers Eng 86:329–337
Li XW, Cho SJ, Kim ST (2014) High security and robust optical image encryption approach based on computer-generated integral imaging pickup and iterative back-projection techniques. Opt Lasers Eng 55:162–182
Li S-L, Wang Q-H, Xiong Z-L, Deng H, Ji C-C (2014) Multiple orthographic frustum combing for real-time computer-generated integral imaging system. J Display Technol 10(8):704–709
Li XW, Cho SJ, Kim ST (2014) A 3D image encryption technique using computer-generated integral imaging and cellular automata transform. Opt Int J Light Electron Opt 125(13):2983–2990
Xing Y, Wang Q-H, Xiong Z-L, Deng H (2016) Encrypting three-dimensional information system based on integral imaging and multiple chaotic maps. Opt Eng 55(2):023107
Wang Q, Wei M, Chen X, Miao Z (2018) Joint encryption and compression of 3D images based on tensor compressive sensing with non-autonomous 3D chaotic system. Multimed Tools Appl 77(2):1715–1734
Qin Y, Gong Q (2014) Multiple-image encryption in an interference-based scheme by lateral shift multiplexing. Opt Commun 315:220–225
Ding X, Chen G (2014) Optical color image encryption using position multiplexing technique based on phase truncation operation. Opt Laser Technol 57:110–118
Wang X, Dai C, Chen J (2014) Optical image encryption via reverse engineering of a modified amplitude-phase retrieval-based attack. Opt Commun 328:67–72
Chen L, Liu J, Wen J, Gao X, Mao H, Shi X, Qu Q (2015) A new optical image encryption method based on multi-beams interference and vector composition. Opt Laser Technol 69:80–86
Chen L, Liu J, Wen J, Mao H, Ge F, Zhao D (2015) Pseudo color image encryption based on three-beams interference principle and common vector composition. Opt Commun 338:110–116
Deng X, Wen W (2015) Optical multiple-image encryption based on fully phase encoding and interference. Opt Int J Light Electron Opt 126(21):3210–3214
Zhao T, Ran Q, Yuan L, Chi Y, Ma J (2015) Image encryption using fingerprint as key based on phase retrieval algorithm and public key cryptography. Opt Lasers Eng 72:12–17
Wang Y, Quan C, Tay C (2016) Asymmetric optical image encryption based on an improved amplitude-phase retrieval algorithm. Opt Lasers Eng 78:8–16
Chen W (2016) Optical multiple-image encryption using three-dimensional space. IEEE Photonics J 8(2):1–8
Li C, Luo G, Li C (2018) A parallel image encryption algorithm based on chaotic Duffing oscillators. Multimed Tools Appl 77(15):19193–19208
Chai X, Gan Z, Zhang M (2017) A fast chaos-based image encryption scheme with a novel plain image-related swapping block permutation and block diffusion. Multimed Tools Appl 76(14):15561–15585
Zhang Y, Tang Y (2017) A plaintext-related image encryption algorithm based on chaos. Multimed Tools Appl 77:1–23
Huang X, Ye G (2018) An image encryption algorithm based on irregular wave representation. Multimed Tools Appl 77(2):2611–2628
Chai X, Yang K, Gan Z (2017) A new chaos-based image encryption algorithm with dynamic key selection mechanisms. Multimed Tools Appl 76(7):9907–9927
Chai X (2017) An image encryption algorithm based on bit level brownian motion and new chaotic systems. Multimed Tools Appl 76(1):1159–1175
Mollaeefar M, Sharif A, Nazari M (2017) A novel encryption scheme for colored image based on high level chaotic maps. Multimed Tools Appl 76(1):607–629
Tang Z, Wang F, Zhang X (2017) Image encryption based on random projection partition and chaotic system. Multimed Tools Appl 76(6):8257–8283
Liu L, Miao S (2017) An image encryption algorithm based on baker map with varying parameter. Multimed Tools Appl 76(15):16511–16527
Zhu J, Yang X, Meng X, Wang Y, Yin Y, Sun X, Dong G (2018) Optical image encryption scheme with multiple light paths based on compressive ghost imaging. J Mod Opt 65(3):306–313
Wu J, Zhang M, Zhou N (2017) Image encryption scheme based on random fractional discrete cosine transform and dependent scrambling and diffusion. J Mod Opt 64(4):334–346
Li H, Wang Y (2008) Double-image encryption by iterative phase retrieval algorithm in fractional Fourier domain. J Mod Opt 55(21):3601–3609
Wang X, Teng L, Qin X (2012) A novel colour image encryption algorithm based on chaos. Signal Process 92(4):1101–1108
Norouzi B, Mirzakuchaki S (2017) An image encryption algorithm based on DNA sequence operations and cellular neural network. Multimed Tools Appl 76(11):13681–13701
Liang Y, Liu G, Zhou N, Wu J (2015) Image encryption combining multiple generating sequences controlled fractional DCT with dependent scrambling and diffusion. J Mod Opt 62(4):251–264
Zhang Y (2018) The image encryption algorithm based on chaos and DNA computing. Multimed Tools Appl 77:1–27
Liu X, Mei W, Du H (2014) Optical image encryption based on compressive sensing and chaos in the fractional Fourier domain. J Mod Opt 61(19):1570–1577
Chen T, Zhang M, Wu J, Yuen C, Tong Y (2016) Image encryption and compression based on kronecker compressed sensing and elementary cellular automata scrambling. Opt Laser Technol 84:118–133
Souyah A, Faraoun KM (2016) An image encryption scheme combining chaos-memory cellular automata and weighted histogram. Nonlinear Dyn 86(1):639–653
Niyat AY, Moattar MH, Torshiz MN (2017) Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt Lasers Eng 90:225–237
Wang Y, Zhao Y, Zhou Q, Lin Z (2018) Image encryption using partitioned cellular automata. Neurocomputing 275:1318–1332
Hanis S, Amutha R (2017) Double image compression and encryption scheme using logistic mapped convolution and cellular automata. Multimed Tools Appl 77:1–16
Jeyaram B, Raghavan R et al (2016) New cellular automata-based image cryptosystem and a novel non-parametric pixel randomness test. Secur Commun Netw 9(16):3365–3377
Murugan B, Gounder N, Gounden A, Manohar S (2016) A hybrid image encryption algorithm using chaos and Conway’s game-of-life cellular automata. Secur Commun Netw 9(7):634–651
Ahmad M, Alam MZ, Umayya Z, Khan S, Ahmad F (2018) An image encryption approach using particle swarm optimization and chaotic map. Int J Inf Technol 10:1–9
Gan Z, Chai X, Yuan K, Lu Y (2017) A novel image encryption algorithm based on LFT based s-boxes and chaos. Multimed Tools Appl 77:1–25
Deng J, Zhao S, Wang Y, Wang L, Wang H, Sha H (2017) Image compression-encryption scheme combining 2D compressive sensing with discrete fractional random transform. Multimed Tools Appl 76(7):10097–10117
Krishnamoorthi R, Murali P (2017) A selective image encryption based on square-wave shuffling with orthogonal polynomials transformation suitable for mobile devices. Multimed Tools Appl 76(1):1217–1246
Ahmad J, Khan MA, Hwang S, Khan JS (2017) A compression sensing and noise-tolerant image encryption scheme based on chaotic maps and orthogonal matrices. Neural Comput Appl 28(1):953–967
Wang X, He G (2011) Cryptanalysis on a novel image encryption method based on total shuffling scheme. Opt Commun 284(24):5804–5807
Zhang G, Liu Q (2011) A novel image encryption method based on total shuffling scheme. Opt Commun 284(12):2775–2780
Wen W (2016) Security analysis of a color image encryption scheme based on skew tent map and hyper chaotic system of 6th-order CNN against chosen-plaintext attack. Multimed Tools Appl 75(6):3553–3560
Murillo-Escobar M, Cruz-Hernandez C, Abundiz-Perez F, Lopez-Gutierrez R, Del Campo OA (2015) A RGB image encryption algorithm based on total plain image characteristics and chaos. Signal Process 109:119–131
Fan H, Li M, Liu D, An K (2017) Cryptanalysis of a plaintext-related chaotic RGB image encryption scheme using total plain image characteristics. Multimed Tools Appl 77:1–25
Zeng L, Liu R, Zhang LY, Liu Y, Wong K-W (2016) Cryptanalyzing an image encryption algorithm based on scrambling and veginere cipher. Multimed Tools Appl 75(10):5439–5453
Li S, Zhao Y, Qu B et al (2013) Image scrambling based on chaotic sequences and veginère cipher. Multimed Tools Appl 66(3):573–588
Su X, Li W, Hu H (2017) Cryptanalysis of a chaos-based image encryption scheme combining DNA coding and entropy. Multimed Tools Appl 76(12):14021–14033
Zhen P, Zhao G, Min L, Jin X (2016) Chaos-based image encryption scheme combining DNA coding and entropy. Multimed Tools Appl 75(11):6303–6319
Zhang X, Nie W, Ma Y, Tian Q (2017) Cryptanalysis and improvement of an image encryption algorithm based on hyper-chaotic system and dynamic s-box. Multimed Tools Appl 76(14):15641–15659
Liu Y, Tong X, Ma J (2016) Image encryption algorithm based on hyper-chaotic system and dynamic s-box. Multimed Tools Appl 75(13):7739–7759
Norouzi B, Mirzakuchaki S (2017) Breaking a novel image encryption scheme based on an improper fractional order chaotic system. Multimed Tools Appl 76(2):1817–1826
Zhao J, Wang S, Chang Y, Li X (2015) A novel image encryption scheme based on an improper fractional-order chaotic system. Nonlinear Dyn 80(4):1721–1729
Peng H, Tian Y, Kurths J, Li L, Yang Y, Wang D (2017) Secure and energy-efficient data transmission system based on chaotic compressive sensing in body-to-body networks. IEEE Trans Biomed Circuits Syst 11:558–573
Cao W, Zhou Y, Chen CP, Xia L (2017) Medical image encryption using edge maps. Signal Process 132:96–109
Hua Z, Yi S, Zhou Y (2018) Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Signal Process 144:134–144
Sajjad M, Muhammad K, Baik SW, Rho S, Jan Z, Yeo S-S, Mehmood I (2017) Mobile-cloud assisted framework for selective encryption of medical images with steganography for resource-constrained devices. Multimed Tools Appl 76(3):3519–3536
Xu L, Gou X, Li Z, Li J (2017) A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt Lasers Eng 91:41–52
Praveenkumar P, Devi NK, Ravichandran D, Avila J, Thenmozhi K, Rayappan JBB, Amirtharajan R (2017) Transreceiving of encrypted medical image—a cognitive approach. Multimed Tools Appl 77:1–26
Ismail SM, Said LA, Radwan AG, Madian AH, Abu-Elyazeed MF (2018) Generalized double-humped logistic map-based medical image encryption. J Adv Res 10:85–98
Li S, Li C, Chen G, Bourbakis NG, Lo KT (2008) A general quantitative cryptanalysis of permutation-only multimedia ciphers against plaintext attacks. Signal Process Image Commun 23(3):212–223
Li C, Lo KT (2011) Optimal quantitative cryptanalysis of permutation-only multimediaciphers against plaintext attacks. Signal Process 91(4):949–954
Li Y, Song B, Cao R, Zhang Y, Qin H (2016) Image encryption based on compressive sensing and scrambled index for secure multimedia transmission. ACM Trans Multimed Comput Commun Appl (TOMM) 12(4s):62
Huang X, Ye G, Chai H, Xie O (2015) Compression and encryption for remote sensing image using chaotic system. Secur Commun Netw 8(18):3659–3666
Xiang T, Hu J, Sun J (2015) Outsourcing chaotic selective image encryption to the cloud with steganography. Digit Signal Process 43:28–37
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(11):2594–2608
Jin X, Guo K, Song C, Li X, Zhao G, Luo J, Li Y, Chen Y, Liu Y, Wang H (2016) Private video foreground extraction through chaotic mapping based encryption in the cloud. In: International conference on multimedia modeling. Springer, pp 562–573
Xia Z, Xiong NN, Vasilakos AV, Sun X (2017) EPCBIR: an efficient and privacy-preserving content-based image retrieval scheme in cloud computing. Inf Sci 387:195–204
Cui H, Yuan X, Wang C (2017) Harnessing encrypted data in cloud for secure and efficient mobile image sharing. IEEE Trans Mobile Comput 16(5):1315–1329
Zou Q, Wang J, Ye J, Shen J, Chen X (2017) Efficient and secure encrypted image search in mobile cloud computing. Soft Comput 21(11):2959–2969
El-Bakary EM, El-Rabaie E-SM, Zahran O, El-Samie FEA (2017) Drpe encryption with chaotic interleaving for video communication. Wirel Pers Commun 97(1):1373–1384
Long M, Peng F, Li H (2017) Separable reversible data hiding and encryption for HEVC video. J Real-Time Image Processing:1–12
Su Y, Tang C, Chen X, Li B, Xu W, Lei Z (2017) Cascaded Fresnel holographic image encryption scheme based on a constrained optimization algorithm and Henon map. Opt Lasers Eng 88:20–27
Sallam AI, El-Rabaie E-SM, Faragallah OS (2017) Efficient HEVC selective stream encryption using chaotic logistic map. Multimed Syst 24:1–19
Khlif N, Masmoudi A, Kammoun F, Masmoudi N (2018) Secure chaotic dual encryption scheme for H.264/AVC video conferencing protection. IET Image Process 12(1):42–52
Wang W, Peng D, Wang H, Sharif H, Chen H-H (2007) Energy-constrained quality optimization for secure image transmission in wireless sensor networks. Adv Multimed. https://doi.org/10.1155/2007/25187
Wang W, Peng D, Wang H, Sharif H (2009) An adaptive approach for image encryption and secure transmission over multirate wireless sensor networks. Wirel Commun Mobile Comput 9(3):383–393
Wang W, Hempel M, Peng D, Wang H, Sharif H, Chen H-H (2010) On energy efficient encryption for video streaming in wireless sensor networks. IEEE Trans Multimed 12(5):417–426
Khan MA, Ahmad J, Javaid Q, Saqib NA (2017) An efficient and secure partial image encryption for wireless multimedia sensor networks using discrete wavelet transform, chaotic maps and substitution box. J Mod Opt 64(5):531–540
Chen R-J, Sun Y-L, He D (2012) Video encryption based on generalized cat mapping and H. 264. Internet Things Technol 1:017
Muhammad K, Hamza R, Ahmad J, Lloret J, Wang HHG, Baik SW (2018) Secure surveillance framework for IoT systems using probabilistic image encryption. IEEE Trans Ind Inform 14(8):3679–3689
Nagy G, Seth S, Einspahr K (1987) Decoding substitution ciphers by means of word matching with application to OCR. IEEE Trans Pattern Anal Mach Intell PAMI–9(5):710–715
Handley JC, Buckley RR (2005) Selective encryption of mixed raster content layers, Oct. 11 2005. US Patent 6,954,532
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest.
Rights and permissions
About this article
Cite this article
Kaur, M., Kumar, V. A Comprehensive Review on Image Encryption Techniques. Arch Computat Methods Eng 27, 15–43 (2020). https://doi.org/10.1007/s11831-018-9298-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11831-018-9298-8