Abstract
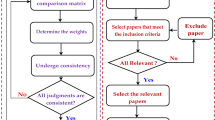
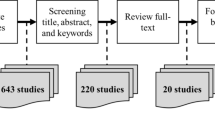
We have presented a review of the challenges facing business PM. These challenges are categorized into three challenges: (1) between business and IT, difficulty of deriving IT goals from business goals challenges; (2) security issues on business PM challenges; and (3) managing customer power, the rapidly changing business environment and business process (BP) challenges. Also, it presents the limitations of existing business PM frameworks. For example, in the first challenge, the existing literature is limited because they fail to capture the real business environment. Also, it is hard for IT analysts to understand BPs. In the second challenges, the existing methods of IS development fail to successfully integrate security during all development process stages and only deal with specific security requirements, goals and constraints. In the third challenges, no research has been conducted in the area of separating customers into different priority groups to provide services according to their required delivery time, payment history and feedback. Finally, we outline possible further research directions in the business PM domain. A systematic literature review method was used. Our review reports on academic publications on business PM challenges over the 13 years from 2000 to 2012. There are 31 journals as well as the IEEE and ACM databases being searched to identify relevant papers. Our systematic literature review results in that there are 53 journal papers as being the most relevant to our topic. In conclusion, it is not easy to create a good business PM. However, the research have to pay much attention on the area of creating successful business PM by creating secure business PM, manage customer power and create business PM where IT goals can be easily derived from business goals.






Similar content being viewed by others
References
Aburub, F., Odeh, M., & Beeson, I. (2007). Modelling non-functional requirements of business processes. Information and Software Technology, 49(12), 1162–1171.
Aguilarsaven, R. (2004). Business process modelling: Review and framework. International Journal of Production Economics, 90(2), 129–149.
Alexopoulos, E., & Theodoulidis, B. (2003). The generic information business model. International Journal of Information Management, 23(4), 323–336.
Alghathbar, K. (2007). Validating the enforcement of access control policies and separation of duty principle in requirement engineering. Information and Software Technology, 49(2), 142–157.
Aghathbar, K., & Wijesekera, D. (2003). AuthUML: a three-phased framework to analyze access control specifications in use cases. In Proceedings of the Workshop on Formal Methods in Security Engineering (FMSE) Washington, DC: ACM Press.
Alotaibi, Y., & Liu, F. (2012a). A new framework to model a secure e-commerce system. International Journal of Social and Human Sciences, 6(6), 162–168.
Alotaibi, Y., & Liu, F. (2012b). How to model a secure information system (IS): A case study. International Journal of Information and Education Technology, 2(2), 94–102.
Alotaibi, Y. & Liu, F. (2012c). Business process modelling towards derivation of information technology goals. In: 45th Hawaii international conference on system science (HICSS) (pp. 4307–4315). 4–7 January 2012. Maui, Hawaii, US.
Alotaibi, Y., & Liu, F. (2013a). Average waiting time of customers in a new queue system with different classes. Business Process Management Journal, 19(1), 146–168.
Alotaibi, Y., & Liu, F. (2013b). Queuing system for different classes of customers. International Journal of Business Information Systems, 13(4), 418–434.
Alotaibi, Y. & Liu, F. (2013c). Business process modelling towards derive and implement IT goals. In 8th IEEE conference on industrial electronics and applications (ICIEA 2013) 19–21 June 2013, Melbourne, Australia.
Alotaibi, Y. & Liu, F. (2014a). A novel secure business process modelling approach and its impact on business performance. Information Sciences. doi:10.1016/j.ins.2014.02.088.
Alotaibi, Y., & Liu, F. (2014b). An empirical study of a novel managing customer power model and business performance in the mobile service industry. Business Process Management Journal. (accepted).
Alotaibi, Y., & Liu, F. (2014c). Business process modelling framework derive and implement IT goals: A case study. International Journal of Industrial and Systems Engineering. (accepted).
Amaral, C. S. T., Rozenfeld, H., Costa, J. M. H., Magon, M. D. F. D. A., & Mascarenhas, Y. M. (2011). Improvement of radiology services based on the process management approach. European Journal of Radiology, 78(3), 377–383.
Anthony Byrd, T., Lewis, B. R., & Bryan, R. W. (2006). The leveraging influence of strategic alignment on IT investment: An empirical examination. Information & Management, 43(3), 308–321.
Aversano, L., Grasso, C., & Tortorella, M. (2012). A literature review of business/IT alignment strategies. Procedia Technology, 5, 462–474.
Basin, D., Clavel, M., Doser, J., & Egea, M. (2009). Automated analysis of security-design models. Information and Software Technology, 51(5), 815–831.
Becker, J., Rosemann, M., & Uthmann, C. V. (2000). Guidelines of business process modeling. Business process management: Models techniques and empirical studies. Berlin: Springer.
Benbya, H., & Mckelvey, B. (2006). Using coevolutionary and complexity theories to improve IS alignment: A multi-level approach. Journal of Information Technology, 21(4), 284–298.
Box, S., & Platts, K. (2005). Business process management: establishing and maintaining project alignment. Business Process Management Journal, 11(4), 370–387.
Bradley, R. V., Pratt, R. M. E., Byrd, T. A., Outlay, C. N., & Wynn, D. E, Jr. (2012). Enterprise architecture, IT effectiveness and the mediating role of IT alignment in US hospitals. Information Systems Journal, 22(2), 97–127.
Burn, J. M., & Szeto, C. (2000). A comparison of the views of business and IT management on success factors for strategic alignment. Information & Management, 37(4), 197–216.
Capozucca, A., & Guelfi, N. (2010). Modelling dependable collaborative time-constrained business processes. Enterprise Information Systems, 4(2), 153–214.
Chan, Y. E., & Reich, B. H. (2007). IT alignment: An annotated bibliography. Journal of Information Technology, 22(4), 316–396.
Chen, L. (2010). Business-IT alignment maturity of companies in China. Information & Management, 47(1), 9–16.
Chung, L. & Nixon, B. A. (1995). Dealing with non-functional requirements: Three experimental studies of a process-oriented approach. In Proceedings of the 17th international conference on Software engineering (ICSE) 23–30 April 1995. Seattle, Washington, USA: ACM.
Cohen, J. F., & Toleman, M. (2006). The IS-business relationship and its implications for performance: An empirical study of South African and Australian organizations. International Journal of Information Management, 26(6), 457–468.
Cragg, P., King, M., & Hussin, H. (2002). IT alignment and firm performance in small manufacturing firms. The Journal of Strategic Information Systems, 11(2), 109–132.
Croteau, A.-M., & Raymond, L. (2004). Performance outcomes of strategic and IT competencies alignment\({\dagger }\). Journal of Information Technology, 19(3), 178–190.
Curtis, B., Kellner, M. I., & Over, J. (1992). Process modeling. Communications ACM, 35(9), 75–90.
D’aubeterre, F., Singh, R., & Iyer, L. (2008). Secure activity resource coordination: Empirical evidence of enhanced security awareness in designing secure business processes. European Journal of Information Systems, 17(5), 528–542.
Davenport, T. H. (1993). Process innovation: Reengineering work through information technology. Boston: Mass.
Davenport, T. H. & Short, J. E. (1990). The new industrial engineering: Information technology and business process redesign. Sloan Management Review, 31(4), 11–27.
Dobson, G., & Sainathan, A. (2011). On the impact of analyzing customer information and prioritizing in a service system. Decision Support Systems, 51(4), 875–883.
Duran, S., Liu, T., Simchilevi, D., & Swann, J. (2008). Policies utilizing tactical inventory for service-differentiated customers. Operations Research Letters, 36(2), 259–264.
El-Attar, M. (2012a). A framework for improving quality in misuse case models. Business Process Management Journal, 18(2), 168–196.
El-Attar, M. (2012b). Towards developing consistent misuse case models. Journal of Systems and Software, 85(2), 323–339.
Eracar, Y. A. & Kokar, M. M. (2012). Using UML and OCL for representing multiobjective combinatorial optimization problems. Journal of Intelligent Manufacturing. doi:10.1007/s10845-012-0705-y.
Eriksson, H.-E., & Penker, M. (2000). Business modeling with UML: Business patterns at work. Chichester, New York: Wiley.
Frank, K. C., Zhang, R. Q., & Duenyas, I. (2003). Optimal policies for inventory systems with priority demand classes. Operations Research, 51(6), 993–1002.
Gartner Group. (2009). Meeting the Challenge: The 2009 CIO Agenda. EXP Premier Report, January 2009. Gartner Inc.: Connecticut, Stamford.
Gerber, T., Theorin, A. & Johnsson, C. (2013). Towards a seamless integration between process modeling descriptions at business and production levels: work in progress. Journal of Intelligent Manufacturing.
Giorgini, P., Massacci, F., Mylopoulos, J., & Zannone, N. (2006). Requirements engineering for trust management: model, methodology, and reasoning. International Journal of Information Security, 5(4), 257–274.
Goluch, G., Ekelhart, A., Fenz, S., Jakoubi, S., Tjoa, S. & Muck, T. (2008). Integration of an ontological information security concept in risk-aware business process management. In Proceedings of the 41st annual Hawaii international conference on system sciences (p. 377). 7–10 January 2008.
Grant, G. G. (2003). Strategic alignment and enterprise systems implementation: The case of Metalco. Journal of Information Technology, 18(3), 159–175.
Green, P., & Rosemann, M. (2000). Integrated process modeling: An ontological evaluation. Information Systems, 25(2), 73–87.
Gritzalis, D., & Lambrinoudakis, C. (2004). A security architecture for interconnecting health information systems. International Journal of Medical Informatics, 73(3), 305–309.
Gruhn, V., & Laue, R. (2007). What business process modelers can learn from programmers. Science of Computer Programming, 65(1), 4–13.
Guha, S., Grover, V., Kettinger, W. J., & Teng, J. T. C. (1997). Business process change and organizational performance: Exploring an antecedent model. Journal of Management Information Systems, 14(1), 119–154.
Gutierrez, A., Oozco, J., & Serrano, A. (2009). Factors affecting IT and business alignment: A comparative study in SMEs and large organizations. Journal of Enterprise Information Management, 22(2), 197–211.
Hammer, M. (1990). Reengineering work: Don’t automate, obliterate. Harvard Business Review, 68(4), 104–112.
Hammer, M., & Champy, J. (1993). Reengineering the corporation a manifesto for business revolution. New York: harper business.
Henderson, J. C., & Venkatraman, H. (1999). Strategic alignment: Leveraging information technology for transforming organizations. IBM Systems Journal, 38(3), 472–484.
Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: A framework for security policy compliance in organizations. European Journal of Information Systems, 18(2), 106–125.
Hill, J. B., Sinur, J., Flint, D., & Melenovsky, M. J. (2006). Gartner’s position on business process management. Business issues. Connecticut: Gartner Inc.
Hung, R. Y.-Y. (2006). Business process management as competitive advantage: A review and empirical study. Total Quality Management & Business Excellence, 17(1), 21–40.
Hvolby, H.-H., & Trienekens, J. H. (2010). Challenges in business systems integration. Computers in Industry, 61(9), 808–812.
Indulska, M., Recker, J., Rosemann, M., & Green, P. F. (2009). Process modeling: current issues and future challenges. In Conference on Advanced Information Systems Engineering (CAiSE 2009), Lecture Notes in Computer Science (pp. 501–514). Springer: Amsterdam, The Netherlands.
Iyer, L., D’aubeterre, F., & Singh, R. (2008). A semantic approach to secure collaborative inter-organizational eBusiness processes (SSCIOBP). Journal of the Association for Information Systems, 9(3), 233–269.
Jin, T., Wang, J., La Rosa, M., Ter Hofstede, A., & Wen, L. (2013). Efficient querying of large process model repositories. Computers in Industry, 64(1), 41–49.
Jürjens, J. (2001). Towards development of secure systems using UMLsec fundamental approaches to software engineering. In Proceedings of 4th international conference joint european conferences on theory and practice of software (ETAPS 2001), April 2–6, 2001 (pp. 187–200). Genova, Italy.
Kesari, M., Chang, S. & Seddon, P. B. (2003). A content-analytic study of the advantages and disadvantages of process modelling. In 14th Australasian conference on information systems (ACIS). Perth, Australia.
Khaiata, M., & Zualkernan, I. A. (2009). A simple instrument to measure IT-business alignment maturity. Information Systems Management, 26(2), 138–152.
Kim, Y.-G. (1995). Process modeling for BPR: event-process chain approach. In 16th international conference on information systems (ICIS). Amsterdam, Netherlands.
Ko, R. K. L., Lee, S. S. G., & Lee, E. W. (2009). Business process management (BPM) standards: A survey. Business Process Management Journal, 15(5), 744–791.
Kokolakis, S. A., Demopoulos, A. J., & Kiountouzis, E. A. (2000). The use of business process modelling in information systems security analysis and design. Information Management & Computer Security, 8(3), 107–116.
Kueng, P., Kawalek, P. & Bichler, P. (1996). How to compose an Object-Oriented Business Process Model? In Brinkkemper, S. et al. (Eds.), Method Engineering, Proceedings of the IFIP WG8.1/WG8.2 working conference. Atlanta, GA.
Lee, R. G., & Dale, B. G. (1998). Business process management: A review and evaluation. Business Process Management Journal, 4(3), 214–225.
Lepmets, M., Mcbride, T., & Ras, E. (2012). Goal alignment in process improvement. Journal of Systems and Software, 85(6), 1440–1452.
Li, N., Grosof, B. N., & Feigenbaum, J. (2003). Delegation logic: A logic-based approach to distributed authorization. ACM Transactions on Information and System Security, 6(1), 128–171.
Lindsay, A. (2003). Business processes-attempts to find a definition. Information and Software Technology, 45(15), 1015–1019.
Liu, L., Yu, E. & Mylopoulos, J. (2003). Security and privacy requirements analysis within a social setting. In Proceedings of 11th IEEE international requirements, engineering conference (pp. 151–161). 8–12 September 2003.
Lodderstedt, T., Basin, D., & Doser, J. (2002). SecureUML: A UML-based modeling language for model-driven security. In Proceedings of the 5th international conference on the unified modeling language, 2002 (pp. 426–441). Berlin/Heidelberg: Springer.
Lodhi, A., Koppen, V., & Saake, G. (2011). Business Process Modeling: Active Research Areas and Challenges. http://wwwiti.cs.unimagdeburg.de/iti_db/publikationen/ps/auto/AzVkGsTR1002.pdf.
Luftman, J. (2000). Assessing business-IT alignment maturity. Communications of the Association for Information Systems, 4(14), 1–50.
Luftman, J. (2003). Assessing It/business alignment. Information Systems Management, 20(4), 9–15.
Mahdavi, I., Mohebbi, S., Zandakbari, M., Cho, N., & Mahdavi-Amiri, N. (2009). Agent-based web service for the design of a dynamic coordination mechanism in supply networks. Journal of Intelligent Manufacturing, 20(6), 727–749.
Mana, A., Montenegro, J. A., Rudolph, C. & Vivas, J. L. (2003). A business process-driven approach to security engineering. In Proceedings of 14th international workshop on database and expert systems applications (pp. 477–481). 1–5 September 2003.
Matulevicius, R., Mayer, N. & Heymans, P. (2008). Alignment of misuse cases with security risk management. In Proceedings of the third international conference on availability, reliability and security (ARES 08) (pp. 1397–1404). 4–7 March 2008.
Mayer, N., Dubois, E., & Rifaut, A. (2007). Requirements engineering for improving business/IT alignment in security risk management methods enterprise interoperability II. London: Springer.
Mayer, N., Dubois, E., Matulevicius, R. & Heymans, P. (2008). Towards a Measurement Framework for Security Risk Management. Modeling Security Workshop (MODSEC’08). In Conjunction with the 11th international conference on model driven engineering languages and systems (MODELS’08). Toulouse, France.
Mcdermott, J. & Fox, C. (1999). Using Abuse Case Models for Security Requirements Analysis. Proceedings of the 15th Annual Computer Security Applications Conference. IEEE Computer, Society. 55–64.
Mili, H., Jaoude, G. B., Lefebvre, É., Tremblay, G., Petrenko, A., & Boussaidi, G. E. (2010). Business process modeling languages: Sorting Through the alphabet soup. ACM Computing Surveys, 43(1), 4–56.
Millet, P.-A., Schmitt, P., & Botta-Genoulaz, V. (2009). The SCOR model for the alignment of business processes and information systems. Enterprise Information Systems, 3(4), 393–407.
Mouratidis, H., & Jurjens, J. (2010). From goal-driven security requirements engineering to secure design. International Journal of Intelligent Systems, 25(8), 813–840.
Neubauer, T. (2009). An empirical study about the status of business process management. Business Process Management Journal, 15(2), 166–183.
Newkirk, H. E., Lederer, A. L., & Johnson, A. M. (2008). Rapid business and IT change: Drivers for strategic information systems planning? European Journal of Information Systems, 17(3), 198–218.
Nickels, D. W., & Janz, B. D. (2010). Organizational culture: Another piece of the IT-business alignment puzzle. Journal of Information Technology Management, XXI(3), 1–14.
Pereira Klen, A., Rabelo, R., Ferreira, A., & Spinosa, L. (2001). Managing distributed business processes in the virtual enterprise. Journal of Intelligent Manufacturing, 12(2), 185–197.
Piccoli, G., & Lloyd, R. (2010). Strategic impacts of IT-enabled consumer power: Insight from Internet distribution in the U.S. lodging industry. Information & Management, 47(8), 333–340.
Pla, A., Gay, P., Meléndez, J. & López, B. (2012). Petri net-based process monitoring: a workflow management system for process modelling and monitoring. Journal of Intelligent Manufacturing, 23(5), 1–16.
Ramirez, R., Melville, N., & Lawler, E. (2010). Information technology infrastructure, organizational process redesign, and business value: An empirical analysis. Decision Support Systems, 49(4), 417–429.
Recker, J., Safrudin, N., & Rosemann, M. (2012). How novices design business processes. Information Systems, 37(6), 557–573.
Reijers, H. A., & Mendling, J. (2011). A study into the factors that influence the understandability of business process models. IEEE Transactions on Systems, Man and Cybernetics, Part A: Systems and Humans, 41(3), 449–462.
Risdiyono, & Koomsap, P. (2011). Design by customer: Concept and applications. Journal of Intelligent Manufacturing, 24(2), 295–311.
Rodríguez, A., Fernndez-Medina, E., & Piattini, M. (2007a). A BPMN extension for the modeling of security requirements in business processes. IEICE Transactions on Information and Systems, 90(4), 745–752.
Rodríguez, A., Fernndez-Medina, E. & Piattini, M. (2007b). M-BPSec: a method for security requirement elicitation from a UML 2.0 business process specification. In Proceedings of the 2007 conference on advances in conceptual modeling: Foundations and applications. Auckland, New Zealand: Springer.
Rodríguez, A., Fernández-medina, E., Trujillo, J., & Piattini, M. (2011). Secure business process model specification through a UML 2.0 activity diagram profile. Decision Support Systems, 51(3), 446–465.
Rodríguez, A., Guzmán, I. G.-R. D., Fernández-Medina, E., & Piattini, M. (2010). Semi-formal transformation of secure business processes into analysis class and use case models: An MDA approach. Information and Software Technology, 52(9), 945–971.
Rohrig, S. & Ag, S. S. (2002). Using process models to analyze health care security requirements. In International Conference Advances in Infrastructure for e-Business, e-Education, e-Science, and e-Medicine on the Internet. Italy.
Rosemann, M. (2006a). Potential pitfalls of process modeling: Part A. Business Process Management Journal, 12(2), 249–254.
Rosemann, M. (2006b). Potential pitfalls of process modeling: Part B. Business Process Management Journal, 12(3), 377–384.
Ryan, G., & Valverde, M. (2006). Waiting in line for online services: A qualitative study of the user’s perspective. Information Systems Journal, 16(2), 181–211.
Santos Rocha, R. D., & Fantinato, M. (2013). The use of software product lines for business process management: A systematic literature review. Information and Software Technology, 55(8), 1355–1373.
Schwarz, M., & Daduna, H. (2006). Queueing systems with inventory management with random lead times and with backordering. Mathematical Methods of Operations Research, 64(3), 383–414.
Sentanin, O. F., Santos, F. C. A., & Jabbour, C. J. C. (2008). Business process management in a Brazilian public research centre. Business Process Management Journal, 14(4), 483–496.
Shim, S. J., & Kumar, A. (2010). Simulation for emergency care process reengineering in hospitals. Business Process Management Journal, 16(5), 795–805.
Silva, A. R., & Rosemann, M. (2012). Processpedia: An ecological environment for BPM stakeholders’ collaboration. Business Process Management Journal, 18(1), 20–42.
Silva, L., Figueroa, B. E., & González-Reinhart, J. (2007). Interpreting IS alignment: A multiple case study in professional organizations. Information and Organization, 17(4), 232–265.
Silvius, G., Smit, J., & Driessen, H. (2010). The relationship between organizational culture and the alignment of business and IT. In Proceedings of the sixteenth Americas conference on information systems (AMCIS), (pp. 1–14) 12–15 August, 2010. Peru: Lima.
Sindre, G., & Opdahl, A. L. (2005). Eliciting security requirements with misuse cases. Requirements Engineering, 10(1), 34–44.
Siponen, M., Bskerville, R., & Hikka, J. (2006). A design theory for secure information systems design methods. Journal of the Association for Information Systems, 7(8), 568–592.
Stahl, B. C., Doherty, N. F., & Shaw, M. (2012). Information security policies in the UK healthcare sector: A critical evaluation. Information Systems Journal, 22(1), 77–94.
Strembeck, M., & Mendling, J. (2011). Modeling process-related RBAC models with extended UML activity models. Information and Software Technology, 53(5), 456–483.
Synstar. (2004). The Pressure Point Index: V. Synstar.
Taylor, A. (2000, January). IT projects: Sink or Swim. Computer Bulletin
Tempelmeier, H. (2006). Supply chain inventory optimization with two customer classes in discrete time. European Journal of Operational Research, 174(1), 600–621.
Tosic, V. (2006). The 5 C challenges of business-driven IT management and the 5 A approaches to addressing them. In: The first IEEE/IFIP international workshop on business-driven IT management, BDIM’06 (pp. 11–18). 07 April 2006.
Trkman, P. (2010). The critical success factors of business process management. International Journal of Information Management, 30(2), 125–134.
Tsalgatidou, A., & Junginger, S. (1995). Modelling in the re-engineering process. SIGOIS Bulletin, 16(1), 17–24.
Turetken, O., & Demirors, O. (2011). Plural: A decentralized business process modeling method. Information & Management, 48(6), 235–247.
van-der-AALST, W. M. P. (2003). Don’t go with the flow: Web services composition standards exposed. IEEE Intelligent Systems, 18(1), 72–76.
van-der-Aalst, W. M. P. (2004). Busienss process management: A personal view. Business Process Management Journal, 10(2), 5.
Villaseñor Herrera, V., Vidales Ramos, A., & Martínez Lastra, J. L. (2011). An agent-based system for orchestration support of web service-enabled devices in discrete manufacturing systems. Journal of Intelligent Manufacturing, 23(6), 2681–2702.
Watanabe, K., Mikoshiba, S., Tateyama, T., & Shimomura, Y. (2011). Service process simulation for integrated service evaluation. Journal of Intelligent Manufacturing, 23(4), 1379–1388.
Weske, M., van-der-Aalst, W. M. P., & Verbeek, H. M. W. (2004). Advances in business process management. Data & Knowledge Engineering, 50(1), 1–8.
Wijnhoven, F., Spil, T., Stegwee, R., & Fa, R. T. A. (2006). Post-merger IT integration strategies: An IT alignment perspective. The Journal of Strategic Information Systems, 15(1), 5–28.
Willcoxson, L., & Chatham, R. (2004). Progress in the IT/business relationship: A longitudinal assessment. Journal of Information Technology, 19(1), 71–80.
Wolter, C., Menzel, M., Schaad, A., Miseldine, P., & Meinel, C. (2009). Model-driven business process security requirement specification. Journal of Systems Architecture, 55(4), 211–223.
Yao, Y., & Zhang, J. (2012). Pricing for shipping services of online retailers: Analytical and empirical approaches. Decision Support Systems, 53(2), 368–380.
Zhao, N., & Lian, Z. (2011). A queueing-inventory system with two classes of customers. International Journal of Production Economics, 129(1), 225–231.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Alotaibi, Y. Business process modelling challenges and solutions: a literature review. J Intell Manuf 27, 701–723 (2016). https://doi.org/10.1007/s10845-014-0917-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10845-014-0917-4