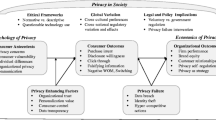
Abstract
The increased use of the internet and information technology to enable online transactions, distribute information and customer reviews through ecommerce and social networking sites, online advertising, and data mining is both creating efficiencies and challenging our privacy. This paper highlights the growing fear that current federal and state laws in the United States are not adequate to protect the privacy of the data collected while we process electronic transactions or browse the internet for information. The notion of efficiency and cost-benefit are used to justify a certain level of privacy loss, thus treating privacy as a commodity to be transacted rather than a right to be defended. To address developing concerns about personal privacy invasions, we discuss the role and limits that both government regulation and self-regulation play in protecting our privacy.

Similar content being viewed by others
References
Lepore, J. (2013, June). Privacy in an age of publicity. http://www.newyorker.com/reporting/2013/06/24/130624fa_fact_lepore?currentPage=all. Accessed 15 Mar 2015.
Halbert, T., & Ingulli, E. (2014). Law and ethics in the business environment (Legal Studies in Business). Stamford: Cengage Learning.
Smith, H. J., Dinev, T., & Xu, H. (2011). Information privacy research: An interdisciplinary review. MIS Quarterly, 35(4), 989–1016.
Culnan, M. J., & Bies, R. J. (2003). Consumer privacy: Balancing economic and justice considerations. Journal of Social Issues, 59(2), 323–342.
Li, Y. (2012). Theories in online information privacy research: A critical review and an integrated framework. Decision Support Systems, 54(1), 471–481.
Arrow, K. J., Chenery, H. B., Minhas, B. S., & Solow, R. M. (1961). Capital-labor substitution and economic efficiency. The Review of Economics and Statistics, 43, 225–250.
Harold, O. (1993). The measurement of productive efficiency: Techniques and applications—Techniques and applications. Oxford: Oxford University Press.
Arrow, K. J. (1973). Social responsibility and economic efficiency. Public Policy, 21(3), 303–317.
Westin, A. F. (2003). Social and political dimensions of privacy. Journal of Social Issues, 59(2), 431–453.
Sheng, H., Nah, F. F.-H., & Siau, K. (2008). An experimental study on ubiquitous commerce adoption: Impact of personalization and privacy concerns. Journal of the Association for Information Systems, 9(6), 15.
Xu, H., Luo, X. R., Carroll, J. M., & Rosson, M. B. (2011). The personalization privacy paradox: An exploratory study of decision making process for location-aware marketing. Decision Support Systems, 51(1), 42–52.
Page, T. (2013). Conservation and economic efficiency: An approach to materials policy. London: Routledge.
Unger, D. J. (2013, October). Energy efficiency: How the internet can lower your electric bill. http://www.csmonitor.com/Environment/2013/1006/Energy-efficiency-How-the-Internet-can-lower-your-electric-bill/(page)/2. Accessed 15 Mar 2015.
Unknown. (2014). How green is the internet? https://www.google.com/green/efficiency/industry-collaboration/. Accessed 15 Mar 2015.
Taylor, D. G., Davis, D. F., & Jillapalli, R. (2009). Privacy concern and online personalization: The moderating effects of information control and compensation. Electronic Commerce Research, 9(3), 203–223.
Earp, J. B., & Baumer, D. (2003). Innovative web use to learn about consumer behavior and online privacy. Communications of the ACM, 46(4), 81–83.
Taddicken, M. (2014). The ‘Privacy Paradox’ in the social web: the impact of privacy concerns, individual characteristics, and the perceived social relevance on different forms of self-disclosure. Journal of Computer-Mediated Communication, 19(2), 248–273.
Case. (2012). Pneus Touchette Distribution inc. c. Pneus Chartrand inc. - 2012 QCCS 3241 (CanLII) - Quebec, Canada. http://www.canlii.org/fr/qc/qccs/doc/2012/2012qccs3241/2012qccs3241.html. Accessed 1 Mar 2015.
Case. (2012). Images Turbo inc. c. Marquis - 2012 QCCS 4386 - Quebec, Canada. http://www.canlii.org/fr/qc/qccs/doc/2012/2012qccs4386/2012qccs4386.pdf. Accessed 1 Mar 2015.
Ren, Y., Cheng, F., Peng, Z., Huang, X., & Song, W. (2011). A privacy policy conflict detection method for multi-owner privacy data protection. Electronic Commerce Research, 11(1), 103–121. doi:10.1007/s10660-010-9067-8.
Landau, S. (2013). Making sense from Snowden. IEEE Security & Privacy Magazine, 4, 54–63.
MPR. (2013). Conflict between privacy rights and security is nothing new. http://www.mprnews.org/story/2013/06/18/daily-circuit-government-surveillance. Accessed 15 Mar 2015.
Robbin, J. E. (1980). Geodemographics: The new magic. Campaigns and Elections, 1(1), 106–125.
Marwick, A. E. (2014, January). How your data are being deeply mined. http://www.nybooks.com/articles/archives/2014/jan/09/how-your-data-are-being-deeply-mined/. Accessed 15 Mar 2015.
Lohr, S. (2014, May). New curbs sought on the personal data industry. http://www.nytimes.com/2014/05/28/technology/ftc-urges-legislation-to-shed-more-light-on-data-collection.html?hpw&rref=busines&_r=0. Accessed 15 Mar 2015.
Berendt, B., Günther, O., & Spiekermann, S. (2005). Privacy in e-commerce: Stated preferences vs. actual behavior. Communications of the ACM, 48(4), 101–106.
Henderson, S. C., & Snyder, C. A. (1999). Personal information privacy: Implications for MIS managers. Information & Management, 36(4), 213–220.
Kleinberg, J. (2006). The world at your fingertips. Nature, 440(7082), 279–280.
Miller, C. C. (2014, May). It’s not as simple as asking to ‘Be Forgotten’ by google. http://www.nytimes.com/2014/05/27/upshot/its-not-as-simple-as-asking-to-be-forgotten-by-google.html?hpw&rref=&_r=1. Accessed 15 Mar 2015.
Antoniou, G., & Batten, L. (2011). E-commerce: Protecting purchaser privacy to enforce trust. Electronic Commerce Research, 11(4), 421–456. doi:10.1007/s10660-011-9083-3.
Bowie, N. E., & Jamal, K. (2006). Privacy rights on the internet: self-regulation or government regulation? Business Ethics Quarterly, 16, 323–342.
Hahn, R. W., & Layne-Farrar, A. (2002). The benefits and costs of online privacy legislation. Administrative Law Review, 54, 85–171.
Ashworth, L., & Free, C. (2006). Marketing dataveillance and digital privacy: Using theories of justice to understand consumers’ online privacy concerns. Journal of Business Ethics, 67(2), 107–123.
Dwyer, C., Hiltz, S., & Passerini, K. (2007). Trust and privacy concern within social networking sites: A comparison of Facebook and MySpace: Proceedings of AMCIS 2007 (p. 339).
Raji, F., Miri, A., Jazi, M. D., & Malek, B. (2011). Online social network with flexible and dynamic privacy policies: CSI International Symposium on Computer Science and Software Engineering (CSSE), 2011 (pp. 135–142). IEEE.
Saltz, J. (2014, January). Art at arm’s length: A history of the selfie. http://www.vulture.com/2014/01/history-of-the-selfie.html. Accessed 15 Mar 2015.
Palmer, D. E. (2005). Pop-ups, cookies, and spam: Toward a deeper analysis of the ethical significance of Internet marketing practices. Journal of Business Ethics, 58(1–3), 271–280.
Kakutani, M. (2014, May). Snowden’s story, behind the scenes. http://www.nytimes.com/2014/05/13/books/no-place-to-hide-by-glenn-greenwald.html?_r=1. Accessed 15 Mar 2015.
Whitman, J. Q. (2004). The two western cultures of privacy: Dignity versus liberty. Yale Law Journal, 113(6), 1151–1221.
Preibusch, S., Kübler, D., & Beresford, A. R. (2013). Price versus privacy: An experiment into the competitive advantage of collecting less personal information. Electronic Commerce Research, 13(4), 423–455. doi:10.1007/s10660-013-9130-3. Accessed 15 Mar 2015.
Case. (1965). Griswold versus Connecticut, 381 U.S. 479 - US Supreme Court. http://laws.findlaw.com/us/381/479.html.
Case. (1967). Katz versus US, 389 U.S. 347 - US Supreme Court. https://supreme.justia.com/cases/federal/us/389/347/case.html. Accessed 15 Mar 2015.
Craig, B. (2013). Cyberlaw: The law of the internet and information technology. Prentice Hall: Pearson Education Inc.
DOJ. (1966). What is FOIA. http://www.foia.gov/about.html. Accessed 15 Mar 2015.
Schultz, B. S. (1999). Electronic money, internet commerce, and the right to financial privacy: A call for new federal guidelines. University of Cincinnati Law Review 67, 779, 791–792.
Hirsh, D. D. (2011). The law and policy of online privacy: Regulation, self-regulation, or co-regulation. The Seattle University Law Review, 439, 457–458.
Case. (2010). Young versus Facebook, Inc - U.S. Dist. - (N.D.Cal. Oct. 25, 2010). https://scholar.google.com/scholar_case?case=14196698777849520612&q=Young+v.+Facebook&hl=en&as_sdt=2,5&as_ylo=2011. Accessed 15 Mar 2015.
Case. (2010). FenF, LLC versus Healio Health, Inc. - U.S. Dist. https://scholar.google.com/scholar_case?case=9276471333322576008&q=FenF,+LLC+v.+Healio+Health,+Inc&hl=en&as_sdt=6,33&as_vis=1. Accessed 15 Mar 2015.
Case. (1976). United States versus Miller - 425 U.S. 435, 443 - US Supreme Court. http://caselaw.lp.findlaw.com/scripts/getcase.pl?court=US&vol=425&invol=435. Accessed 15 Mar 2015.
Case. (2010). Courtright versus Madigan - Civil No. 09-CV-208-JPG WL 3713654 (S.D.Ill. Nov. 4, 2009). https://scholar.google.com/scholar_case?case=7495388096977244675&q=Courtright+v.+Madigan&hl=en&as_sdt=6,33&as_vis=1. Accessed 15 Mar 2015.
Kang, C. (2011, April). Kerry, McCain offer bill to protect web users’ privacy rights, p. 203.
Case. (2006). United States versus Schuster - 467 F.3d 614, 616 (7th Cir. 2006). https://casetext.com/case/us-v-schuster-4. Accessed 15 Mar 2015.
BCP. (2009). The CAN-SPAM act: A compliance guide for business - the federal trade commission. http://business.ftc.gov/documents/bus61-can-spam-act-compliance-guide-business/. Accessed 15 Mar 2015.
Cate, F. H. (2008). Government data mining: The need for a legal framework. Harvard Civil Rights-Civil Liberties Law Review (CR-CL), 43, 435–438.
Smith, M. (2014). Targeted: How technology is revolutionizing advertising and the way companies reach consumers. New York: AMACOM Div American Mgmt Assn.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Walsh, D., Parisi, J.M. & Passerini, K. Privacy as a right or as a commodity in the online world: the limits of regulatory reform and self-regulation. Electron Commer Res 17, 185–203 (2017). https://doi.org/10.1007/s10660-015-9187-2
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10660-015-9187-2