Abstract
Undoubtedly, Industry 4.0 in the energy sector improves the conditions for automation, generation and distribution of energy, increasing the rate of electric vehicle manufacturing in recent years. As a result, more grid-connected charging infrastructures are being installed, whose charging stations (CSs) can follow standardized architectures, such as the one proposed by the open charge point protocol (OCPP). The most recent version of this protocol is v.2.0.1, which includes new security measures at device and communication level to cover those security issues identified in previous versions. Therefore, this paper analyzes OCPP-v2.0.1 to determine whether the new functions may still be susceptible to specific cyber and physical threats, and especially when CSs may be connected to microgrids. To formalize the study, we first adapted the well-known threat analysis methodology, STRIDE, to identify and classify threats in terms of control and energy, and subsequently we combine it with DREAD for risk assessment. The analyses indicate that, although OCPP-v2.0.1 has evolved, potential security risks still remain, requiring greater protection in the future.
Similar content being viewed by others
1 Introduction
Governments and institutions are supporting the electric vehicle (EV) market since they are aware of the environmental advantages of this mode of transport. Due to the limitations of the battery capacity, EV owners are expected to charge their vehicles in multiple locations (including their home, workplace or with public infrastructure) [1]. The research community is analyzing in depth where to place and how to operate EV charging stations (CSs), as uncontrolled charging of these vehicles poses a technological challenge for smart grids [2]. From these studies, it is recommended that future power systems must incorporate advanced control algorithms to ensure reliability, safety and security while coping with the relevant changes affecting the grid.
Guaranteeing reliability, safety and security in power systems with high power levels and an increasing number of assets (e.g., EVs) is becoming complex. Current research efforts propose dividing the power system into smaller interconnected units, known as microgrids (MGs) in order to simplify the control and to make it more robust. In the context of Industry 4.0, an MG employs advanced information technologies, communication networks, protocols and sophisticated information processing to monitor and control power generation, distribution and consumption processes in more efficient and robust way [3]. To do so, it is necessary to optimize the management of electrical, communication and control elements, which are tightly coupled resulting in cyber-physical MGs. As a cyber-physical system (CPS), an MG is susceptible to cyber-attacks which may compromise its performance, maintainability and integrity. Specifically, an attacker can maliciously exploit its components and interdependence to damage the MG, degrade its performance and even interfere with the external power network. In fact, the MG’s voltage and frequency stability, power balance and dispatch are highly dependent on secure and healthy cyber-systems to ensure that the MG assets are controlled correctly [4].
Previous works have already studied the vulnerabilities of MGs focusing on some of their components. For example, some studies have already identified the threats to voltage source converters and their controls [5, 6]. However, there are still many security issues to consider in the MGs. Due to the impact of EVs on MGs and the stress their charging may generate, numerous research works conclude that the Charging Infrastructure (CI) could provoke high risks with a high probability, as they are easily accessible for the public [7, 8]. Consequently, it is necessary to study the new CIs required in the future from a cybersecurity point of view. Academia and industry have already identified vulnerabilities in the communication between the EV and the CS, the EV operator interfaces, the Internet and the maintenance interface of the CS [9], but a deeper analysis is fundamental to consider the communication and information processing done by these elements in the context of Industry 4.0.
In this paper, we identify the threats and risks posed to EV public CSs in MGs corresponding to the new generation of Industry 4.0, including those risks related to the communication infrastructure, Information Technologies (ITs) involved in the control and the MG power assets. Due to its popularity, we assume that CSs use the Open Charge Point Protocol (OCPP) for the Charging Transactions (CTs). Specifically, we analyze OCPP-v2.0.1 [10], which includes new functions not analyzed and covered in its previous versions [11]. Some of these functions are: device management, improved transaction handling, support for ISO 15118 (related to incorporate the communication between the EV and the CS) [12, 13], display and messaging support, smart charging functions and even new security functions compared to OCPP-v1.6 [14] that need to be assessed with respect to possible security and safety risks. To identify these risks, we use a common risk management approach for the analysis, extending it according to the methodology also applied in [15]. Namely, we study the threats using a formal method to detect how attackers can compromise both control and energy assets. In this sense, we adapted the STRIDE methodology to contemplate two relevant aspects: (i) the inclusion of energy hazards and (ii) the combined use of STRIDE with the DREAD assessment model to deepen the analysis process by contemplating possible risks [16].
STRIDE is a simple method, originally conceived to classify threats according to the aim of the attack in software (SW) developments [17]. Specifically, the STRIDE model identifies six categories of threat: Spoofing, Tampering, Repudiation, Information disclosure, Denial of service and Elevation of privilege (defining the acronym for STRIDE). Some recent works have already applied the STRIDE methodology in monitoring systems and in cyber-physical energy systems, but mainly focus their approaches on the consequences of the control processes [18, 19]. Since MGs have both SW and energy system components, we also apply the STRIDE model to comprise energy-specific threats as also considered in [20]. This related work includes a recent survey on security issues in OCPP. The main difference between our work and that of [20] lies in the level of study and depth of the OCPP-v2.0.1 protocol by computing risks through two well-known risk management methodologies, STRIDE+DREAD. The comprehensive view that we get with this combination of methodologies even allows us to identify which types of threats require greater attention in the future, especially now with the new technological currents of Industry 4.0 spreading within the sector.
Regarding the combined use of STRIDE + DREAD, it is important to note that DREAD classifies security threats according to five characteristics: Damage, Reproducibility, Exploitability, Affected Users and Discoverability (which defines the acronym DREAD). Thus, our research aims to combine both approaches (STRIDE+DREAD) to evaluate a set of risks in control (c) and energy (e) assets, referring this combination to as STRIDE-DREAD\(^{\tiny {\mathrm {c+e}}}\) (henceforth SD\(^{\tiny {\mathrm {c+e}}}\)). This grouping facilitates us to later provide a set of countermeasures, considering the particularities of the MG in the context of Industry 4.0. Therefore, the main contributions of this work are:
-
Adaptation of the threat analysis method STRIDE to a system with control and energy assets. In particular, we consider a scenario with public EV Charging Infrastructure (EVCI) and a MG-based control. In the context of Industry 4.0, we extract a specific taxonomy of threats related to the OCPP protocol, v2.0.1, demonstrating the susceptibility of the protocol to multiple types of attacks.
-
Combination of methodologies STRIDE + DREAD to determine the level of severity of each attack on control and energy assets.
-
Identification of a set of mitigation actions, prioritizing each action according to the analysis made by SD\(^{\tiny {\mathrm {c+e}}}\) to reduce possible consequences and impact.
The paper is structured as follows: Sect. 2 proposes a formal architecture of the MG components, highlighting the role of CSs and their control. Section 3 presents SD\(^{\tiny {\mathrm {c+e}}}\) for EVCIs, describing how we apply the extended STRIDE methodology together with the DREAD model for threat assessment. Section 4 analyzes the influence of mitigation solutions, while Sect. 5 outlines the conclusions and future work.
2 Architecture and stakeholders
A MG is a local power system formed by Distributed Energy Resources (DERs) and based on multiple stakeholders: suppliers, customers (as EVs), technical operators and engineers [21, 22]. The implementation of a MG involves considering one of the following three main operational approaches: (i) to operate as an independent power system during its lifetime; (ii) to be fully connected to another power system and use it to complement energy from local DERs and storage systems; and (iii) to switch from the isolated and connected modes in order to rely on the external power system when local resources cannot satisfy local demand. In the next subsections, we first analyze the architecture of a MG with EVs considering these three operational modes. Then, we will describe the role of the stakeholders for the aforementioned operational conditions.
2.1 Architecture
In [23, 24], the authors present the fundamental components of a MG, which mainly consists of three layers: (i) physical layer containing electrical devices; (ii) communication layer; and (iii) cyber layer. A set of ITs runs in these three layers, and they are responsible for controlling operations through the different processing and decision-making techniques of a Central Control System (CCS). These ITs must converge with existing Operational Technologies (OTs), introducing the benefits of Industry 4.0 (better automation, autonomy, access and control) into EVCIs [25]. This CCS is able to manage the control signals from the controllers and actuators in order to optimize energy production levels and the MG stability. The installation of the Energy Management System (EMS) is within the CCS. Its main purpose is to monitor, control and optimize the performance of the MG operations. It performs a set of control functions to maintain safety, reliability, economy, resilience, sustainability and efficiency in the system [26]. Another main component of the CCS is the CS Management System (CSMS), which is responsible for efficiently managing the collection transactions requested by end users in all its CSs (usually deployed in public places). A communication network composed of various wireless and wired network devices, communication infrastructures and industrial communication protocols allows the data flows collected by the sensors and the transmission of the operations sent by the CCS. OCPP corresponds to an open application protocol that establishes communication between the CSs and the CSMS, and even the EMS [10].
The architecture that we follow in this paper aims to model an advanced EVCI in an MG operating with an electricity market where users pay for electricity consumption to charge their EVs. In this architecture, users can reserve power at a predetermined CS connector, and the connection may be initiated automatically, with no manual intervention. The system can, therefore, activate a connector and start to charge the EV battery. This request is managed in two ways, depending on the scenario implemented. The first allows the user to start a CT via a mobile, web application or a payment terminal/system (using a credit/debit card or a parking ticket), where the CSMS manages the transaction request. To do so, the CSMS is responsible for authenticating the user and sending the transaction operation to the corresponding CS. The second way to request CTs allows the user to authenticate himself/herself using the authentication resources of the CSs and the resources supported by the OCPP protocol, such as an RFID tag, button (no authentication required), PIN, EV certificate or unique token. The CS forwards the request to the CSMS which accepts or denies the user’s request and authorizes the CS to start the CT. Note that the CS is also able to handle the request without previously communicating with the CSMS if it is in offline mode. In the following sections, we will discuss these authentication modes in more detail.
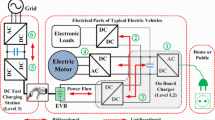
As can be seen in Fig. 1, the architecture counts with a set of distributed CSs that operate and communicate with the CSMS, included in the CCS, via the specialized OCPP protocol, which provides a secure interaction with users and EVs as controllable loads. In addition, the MG powers the CSs and the CCS control and manage the CSs. Each CS relies on different SW and hardware (HW) modules, which enable intelligent operability and secure communication between the internal devices. These modules have been classified into two parts: communication assets and the controller. In the communication part, it is possible to find (i) the OCPP communication, where the OCPP client is able to connect to the OCPP server in the CSMS, but also (ii) different ways to connect with the end user such as Bluetooth Low Energy (BLE) advertisements or Near-Field Communication (NFC) to display the nearby CSs to the user. Thanks to the communication elements, the user can visualize the status of the connectors and send a new request to the CSMS. On the other hand, the controller part of the CS contains three main components. The first component constitutes telemetry elements working as “sensors”. These sensors are devoted to collecting information on the electrical state of the CS, temperature and other measures of energy consumption per CS. In this case, the “smart meters” are electronic devices with the capacity to compute information records such as consumption of electric energy, voltage levels, current and power factor. These devices are responsible for metering the total energy consumed in each CT, in order to facilitate user billing in the CSMS and real-time control demand in the EMS. The last main components of the controller part are the EV Supply Equipments (EVSEs), which include actuators in charge of activating/deactivating the connection and communication with the EVs.
2.2 Stakeholders
The CSMS is in charge of sending regularly the energy consumption and reserve data of all CSs to the EMS. Subsequently, this information is processed and analyzed by the EMS to monitor and control the DERs according to the energy consumption and demand in the MG. Since EVs are controllable loads within the MG, the EMS would be responsible for monitoring the loads and their safe storage and for supplying power to the CS connectors when needed. These functionalities are largely controlled by the OCPP protocol [10], corresponding to the smart charging functional block. This functional block describes all the functionality that enables the CS operator (or indirectly a third party, like the EMS) to influence the charging current/power of a CT, or set limits on the amount of power/current of a CS that can be supplied to an EV. It is feasible to negotiate these current and power limits in the CSs during the CTs with the EVs
through a bidirectional communication standard ISO 15118 [12, 13]. Moreover, OCPP offers the possibility to use a local controller, which is deployed between the CSMS (or the EMS) and any number of CSs creating a local group. It is located close to the CSs (and may even be wired to the CSs), and works so that the CSMS and the EMS are not aware if the CS is connecting to it directly, or via the local controller.
In addition to the users requesting CTs from the CSMS or directly from the CS with their EVs connected to the CS connectors, there are other possible parties involved in a CS-based MG, as shown in Fig. 1. For example, the MG may adapt the power levels of the CIs as a consequence of a relevant growth of controllable/uncontrollable loads. If at certain hours these customers demand high energy from DERs, this may have repercussions for the current/power charging limits of the CSs. Other involved stakeholders are (i) the manufacturers of the firmware installed in each CS; (ii) the operators who have full access to the DERs; and (iii) the CS Operators (CSOs), who have the possibility to interact by performing OCPP operations and configurations on the system through the CSMS or directly on the CSs. Moreover, OCCP-v2.0.1 incorporates two new actors: (i) law enforcement personal, who could stop any ongoing transaction via a Master Pass ID (e.g., a Master Pass RFID tag) with the intention of disconnecting any EV that has to be towed away; and (ii) Certificate Authorities (CAs), which have the function of validating and signing certificates generated by the CSMS. Finally, IT administrators can have access to the CSMS and EMS processes and configuration variables, as well as having full access to databases, containing telemetry values, control data or security configurations/data. We subsequently consider all these actors as possible malicious agents in the threat analysis presented in the following sections.
With the incorporation of new ITs, multiple communications infrastructures and the wide set of actors, it is essential to consider the diverse security risks posed by the new generation of MGs. As can be seen from the architecture, the OCPP protocol bears a major responsibility in the communication processes between the CSMS and CSs, and between the EMS and CSs. In [11], the same cybersecurity issues were already discussed, but focused on OCPP-v1.6. Now, OCPP has upgraded its version to v2.0.1, which includes new security functionalities such as device management using certificates x.509, support for ISO 15118, secure firmware updates and encrypted communication via Transport Layer Security (TLS). But even so, a security analysis is still necessary to identify the new security issues in this new version of OCPP. For that reason, the following sections aim to extract a set of threats that may be found in OCPP-enabled CSs, considering STRIDE + DREAD.
STRIDE + DREAD methodology based on 6 steps, recommended by [16]
3 SD\(^{\tiny {\mathrm {c+e}}}\): threat model and analysis
To identify vulnerabilities and threats, we apply the STRIDE threat model proposed by Microsoft [27, 28].
3.1 Main STRIDE phases and related work
As stated above, STRIDE classifies the threats into six categories (cf. Table 1). This model is widely used due to its straightforward methodology, which is simple and easy to apply, where threats are analyzed and identified manually in each of the system components [29]. For example, in work [17], the STRIDE methodology is applied for CPS-based applications using five steps; while work in [15] applies one more step (see also Fig. 2) in order to assess the effect of the threats for cyber-enabled ships and establish mitigation actions. Considering the mentioned six-step approach [16], we then apply it to provide a more complete picture of threats and risks associated with CIs in a MG.
For the sake of clarity, the operation of the adapted methodology is described as follows. Step 1 consists in decomposing the system into logical or structural components. These can be internal or external processes or assets that interact and communicate with the system. Subsequently, a Data Flow Diagram (DFD) is plotted (Step 2) for each of the components, in order to visualize the functionalities inside and outside the system. Each DFD shows four standard symbols: (i) External Entity (EE), (ii) Data Flow (DF), (iii) Process (P) and (iv) Data Store (DS). This subdivision facilitates the manual process of identifying and analyzing STRIDE threats (Step 3) in each asset of the DFD (STRIDE-per-asset) and in each interaction between assets (STRIDE-per-interaction). Once threats on control and energy assets are identified, the system vulnerabilities are detected manually (Step 4) by analyzing the possible causes and sources of the identified threats. After this, potential threats must be evaluated according to certain established criteria, in order to prioritize and mitigate their effects. This evaluation process coincides with Step 5 through the DREAD model proposed by Microsoft in [16]. DREAD prioritizes threats, managed by STRIDE, by simply calculating the risk that their effects may have in terms of damage, reproducibility, exploitability, affected users and discovery (cf. Table 2). With this information, it is now possible to more appropriately select mitigation strategies (Step 6) according to each threat score and risk prioritization.
With respect to the state of the art, STRIDE is one of the most widely used threat models in energy applications and CPSs. Khan et al apply it to identify threats in a real synchrophasor-based synchronous islanding testbed [17], while Orellana et al and Yampolskiy et al adapt STRIDE and security tactics for designing secure CPS architectures in [30, 31], respectively. There are other related works that combine STRIDE with other existing methodologies to (i) calculate risks using DREAD [15] or according to likelihood and impact [32, 33] and (ii) to detect and mitigate attacks through neural networks [34]. Also, other threat models have been used for CPSs, such as STPA-sec, HAZOP, OCTAVE, PASTA, Abuser stories, Attack Trees, T-MAP and CORAS [17, 29]. It is also possible to classify threats using the Adversarial Tactics, Techniques, and Common Knowledge (ATT &CK) framework developed by MITRE Corporation in [35]. Related to this framework, Zografopoulos et al provide an overview of the security of cyber-physical energy systems using the MITRE ATT &CK for Industrial Control System (ICS) repository [19]. There are also authors that manages the threats considering the specific CPS scenarios [11, 22, 36,37,38]. In [36], Atlantic and Ra describe two types of threats to the security of plug-in EVs: Vehicle-to-Grid (V2G) physical threats (V2GP) and V2G communication threats (V2GC), and propose several mitigation strategies. In [37], Antoun et al present a security assessment of the EVCI by analyzing cyber threats to home and public charging systems. Likewise, [11, 22] identify the threats and key security properties of the OCPP-v1.6 protocol in power systems. With a perspective of the impact on the power system, Sayed et al analyze some vulnerabilities of the protocols involved in the management of public charging infrastructures [8]. This includes the identification of vulnerabilities in the IEC protocols, the firmware, the ISO 15118 and the OCPPv\(-\)1.6. The analysis is performed without a risk assessment methodology, is based on simulating the variation of the active and reactive power of loads (associated to EVs) and evaluating the impact on the grid stability and performance. The authors propose monitoring the electrical performance of the CSs and the reactive power and the harmonic distortion of the grid as feasible countermeasures.
In [39], a penetration test considering three attack scenarios (erroneous data, long values and user interface manipulation) is performed for OCPP-v1.6, while the papers [20, 38] include in their study the OCPP-v2.0.1 protocol. Indeed, in [38], a general vulnerability and mitigation analysis on domestic CSs is also provided according to some of the current protocols and standards, including OCPP-v2.0.1. However, the analysis is at a very high level, covering the fundamental differences with the previous version and several security challenges and recommendations. In [20], a recent survey about security issues and countermeasures in the OCPP protocol is found, stressing the main affected assets (EV, EVSE, CS, EMS, CSMS, data or grid). These three last studies differ from ours in the way in which OCPP is evaluated. Our work focuses on providing a comprehensive threat analysis of OCPP-v2.0.1, following the traditional STRIDE + DREAD methodology and enumerating a set of countermeasures.
To summarize, Table 3 shows a comparison of the frameworks and approaches used in the related work on CPS, and particularly on CS infrastructures. As the table shows, some related research work focus on threats to CIs such as [11, 22, 32, 33, 36, 37], but only some of them consider threats to the OCPP communication protocol such as [11, 20, 22, 37, 39]. From the table, we also highlight that none of the related work applies a STRIDE + DREAD-based threat and risk assessment model for specific CIs integrating OCPP. It is also true that reference [15] contemplates this combination of methodologies, but only focused for CPSs deployed on ships and not for power applications. Therefore, this paper introduces SD\(^{\tiny {\mathrm {c+e}}}\) for energy scenarios. This new approach analyzes both cyber threats in control processes (c) and energy threats (e) caused in power system environments; thus, covering cyber, physical and energy assets. This also provides a clear understanding of the vulnerability impact of each component using DREAD for the assessment and helps to ensure the security of the power system. These threats will be discussed in detail in the following section.
3.2 Main threats and vulnerabilities
Observing Fig. 2, the first action to perform within the SD\(^{\tiny {\mathrm {c+e}}}\) model would be to identify the main assets of the application scenario such as control, communication, HW and SW components, and power. Based on these assets, it is possible to classify them according to their functions, and subsequently into EE, DF, DS and P. Table 4 shows this characteristic, contemplating additionally those main assets illustrated in Fig. 1. After this, the second step requires plotting the DFDs to see the potential relationships between assets. But since the data flows and relationships between these elements can easily be derived from Fig. 1, this step is omitted from the paper.
To continue with SD\(^{\tiny {\mathrm {c+e}}}\), we analyze the phases established by Step 3 and Step 4 of Fig. 2, both focused on the identification and analysis of vulnerabilities. Each type of asset is susceptible to various threats specific to the STRIDE model, as shown in Table 5 and detailed in [17]. This methodology states that before analyzing the threats and vulnerabilities, it is necessary to first extract a list of possible consequences that may affect the system. For that reason, Table 6 establishes a set of possible Threat Consequences (TCs) associated with EVCIs deployed in MGs. Each of these TCs is associated with a pre-determined code and may result in greater or lesser impact on a part of the system or on the overall system (I-1, I-2, I-3 and I-4). This type of analysis allows us to later manage the risks in the DREAD model and rating according to threats.
From Table 6, we determine that all TCs have an impact on the economy of the MG system owners or their customers, due to (i) energy losses, (ii) inability to meet energy demand at the CS, or (iii) possible fraud in energy consumption. For example, through information disclosure (TC-4), attackers could first intend to leak sensitive information (such as configurations, SW codes, user consumption data, etc.) to subsequently corrupt the reputation of the organization or carry out other subsequent attacks against the control or distribution of energy. TC-1 and TC-8 also present high risk consequences, which lead to a lack of control and deconfiguration of the MG, thereby destabilizing the energy load parameters and even causing overloads, blackouts, physical damage to DER and CS equipment and possible human injuries. Likewise, TC-9 also has a high impact on the system, since this TC refers to the possibility of an unnatural or massive reversion of energy to the MG. In turn, this may affect the stability of electrical components, which could be overloaded and damaged, leading to energy losses and economic costs. For clarity, all these threats are further described in the following sections, but classified according to the STRIDE category set out in [27], and analyzed taking into account the main OCPP-v2.0.1 features. To provide a preview of these features, Tables 7, 8, 9 and 10 detail the main functionalities of the protocol. For instance, Table 7 shows the main differences related to security issues of v2.0.1 [10] with respect to v1.6 [14]. Similarly, Table 8 outlines the three possible security profiles according to the OCPP client–server model: (i) “Unsecured Transport with Basic Authentication” (with the “Identity” and “BasicAuthPassword” Configuration Variables (CVs)), which does not include encryption and is recommended only in secure networks, such as a Virtual Private Network (VPN); (ii) “TLS with Basic Authentication” where the CSMS authenticates itself using a TLS server certificate, while the CSs are authenticated using “HTTP Basic Authentication”; and (iii) “TLS with Client Side Certificates”, where both the CSMS and CSs authenticate themselves using certificates. Meanwhile, Table 9 summarizes the OCPP Use Cases (UCs), grouped by functional blocks, and Table 10 lists the CVs that are susceptible to attack if they are disclosed or tampered with. For reasons of space, only a subset of UCs and CVs, mainly susceptible to STRIDE threats, have been collected and are identified in more detail in the following subsections.
3.2.1 Spoofing
Any impersonation involves first illicitly obtaining the security credentials or identity (ID) of legitimate users to (i) gain unauthorized access to CS resources (TC-5) or (ii) commit other subsequent attacks such as energy fraud (TC-7). If, additionally, we explore the capabilities of OCPP-v2.0.1 to authenticate users in the system, we note that in the authorization UCs (C functional block), it collects the different authentication methods in a previous phase, before authorizing the user to start the transaction in the CS. These authentication phases are still susceptible to impersonation threats such as: (i) RFID tag cloning/theft as also mentioned in [11, 20, 38]; (ii) physical theft of the credit/debit card or the parking ticket; (iii) disclosure or brute-force attack of a PIN-code; and (iv) disclosure of the security credentials through malware infection in personal devices if CT requests are via a web or mobile application.
The CCS is another vulnerable access point in the CI analyzed. If an attacker succeeds in spoofing the central system and he/she is capable of gaining access to resources, then he/she may be capable of disabling, manipulating and eavesdropping the communication with CSs (TC-[2–9]), and even controlling EMS operations (TC-1 and TC-10). Another way to attack communication channels from the CCS to CSs is to conduct a Man-in-the-Middle (MitM). An attacker first needs to impersonate the legitimate CSMS through one or several UCs of the OCPP itself; especially, when a CS connects or migrates to a new malicious CSMS (UCs B01 and B10). Once the CSMS has been spoofed, the attacker may be able to remotely start and stop transactions—if this option is enabled (“AuthorizeRemoteStart” CV)—in order to deny service to CSs (TC-3). If, addition, the OCPP configuration enables the CV options “SmartChargingEnabled”, “SmartChargingAvailable” and “ExternalControlSignalsEnabled”, then it is likely that an attacker can impersonate an external entity, such as an external EMS, to connect to legitimate CSs. Consequently, a spoofed EMS might alter energy profiles and limit the amount of current/power of CSs, in order to destabilize energy resources (TC-3, TC-8, TC-10) or consume at a higher power than is permitted (TC-7—according to the new and corrupted charging profiles).
CSs are also susceptible to attacks due to their high exposure in public areas [20]. Attackers may steal the ID of a victim CS in different ways. For example, (i) by tampering the CS device and extracting its ID through the OCPP CVs related to “Identity” and “BasicAuthPassword”; (ii) by stealing the credentials of the client TLS certificate through a physical access to the CS (only if security profile 3 is used and the private key is stored in plain text); (iii) by injecting logic bombs such as spyware or rootkits; and (iv) by stealing or tampering the new password through the A01 UC (see Table 9). A spoofed CS allows the attacker to leak sensitive information managed by the CS itself (e.g., telemetry values, users’ IDs, credentials, parameters) and the CSMS (e.g., OCPP transactions), corrupting TC-4. This threat may even favor other subsequent attacks, such as the unauthorized use of the CS and its connectors for charging (TC-5), or change the CS parameters (TC-8 or TC-9). Moreover, legal stakeholders may also stop any OCPP transaction if they use a Master Pass. This Master Pass consists in a unique token (e.g., a master RFID tag) used by law enforcement personnel to stop any (or all) ongoing transactions—e.g., to stop any ongoing transaction when an EV has to be towed away. If this Master Pass is theft or cloned, attackers may gain access to these critical operations and could deny service or the charging to users (TC-3 and TC-7).
3.2.2 Tampering
This threat refers to the attacker’s capacity to violate the integrity of OCPP communication messages, databases or process of a CS. The first and most obvious way to attack the OCPP protocol is to physically or remotely access the OCPP client module of a CS in order to manipulate its CVs. Table 10 shows a set of CVs that can be manipulated (except for “Identity” and “BasicAuthPassword” which are read-only) to cause either a DoS (e.g., by decreasing the heartbeat interval) or to gain unauthorized access to the system (e.g., by activating “OfflineTxForUnknownIdEnabled” to access as a “legitimate” user when the CS is in offline mode due to a previous DoS attack). Another way to attack is through a MitM [11, 20]. OCPP messages may be manipulated from different standpoints. For example, attackers might: (i) change the “meterValues” variable during a transaction (JO2 UC) to mislead the CSMS about the total amount of energy consumed in a transaction, causing fraud (TC-7); (ii) modifying a charging profile (K01 UC) to consume at higher power and desynchronize energy parameters (TC-8); or (iii) alter the tariff and cost messages during a transaction (I02 UC) to cheat the end user about the total cost—making the victim pay more or less than expected (TC-7). To avoid this situation, TLS-based peer-to-peer protection could help encrypt such transactions. In this way, an attacker would first need to overcome this issue considering the TLS weaknesses against MitM threats [11, 40].
Finally, energy-related threats have to be taken into account in MG systems. Attackers can manipulate DERs for the purpose of misconfiguring installations in order to extract energy from renewable energy sources, for example, by modifying the inclination of photovoltaic panels or turbine blades, leading to energy inefficiency (TC-1, TC-8). As a consequence, storage systems may be overused, causing their performance to degrade prematurely (TC-10). In addition, if the attacker varies the control set-points associated with voltage or frequency regulations, the electrical signal in the MG bus would be unable to comply with international restrictions on voltage levels and/or operational frequency. This may cause electrical damage to the CS components and even some computational problems (the frequency of the electrical signal may cause some timing problems in the micro-processors). Smart meters, such as phasor measurements, may also provide wrong measurements, which may lead to incorrect control commands. These attacks may render the CS unable to meet the energy demand of the users, thereby causing an impact on the real health of the power assets that make up the MG. Any misconfiguration of the MG may even interfere with the external power system, provoking further consequences.
3.2.3 Repudiation
Traditional repudiation attacks are triggered when a malicious entity claims not to have performed an action that it did in fact perform, and the victim entity is unable to verify the truth of the claim. To avoid this problem, the system should contemplate the use of digital signatures to ensure the provenance of the actions.
Thanks to the ISO 15118, CSs can manage digital signatures with information related to metering in the EV part. Unlike OCPP-v1.6, the new version also manages signed meter values when CSs need metering information exchange to the CSMS (in OCPP security profiles 2 and 3). However, OCPP does not force to the use of digital signatures, what repudiation attacks may arise. For example, malicious customers may lie about the real metering values in the transactions as stated in [11]. Also, if messages between the CSMS and CSs, and between the EMS and CSs are not properly audited, when an error occurs in a CS due to poor control of energy and charging profiles, the system may not determine the responsible entity (e.g., the EMS or other external EMSs), or even the origin of the error. Therefore, it is essential to use secure communications under digital signature schemes to ensure accountability, traceability and authentication.
3.2.4 Information disclosure
Adversaries may exploit security breaches to steal sensitive information (TC-4) and gain more detailed knowledge of the system, in order to subsequently prepare more elaborated attacks. In CS, it is possible to lead this type of attack not only at communication level but also in a compromised CS (e.g., through a physical attack or a physical manipulation during the installation/maintenance tasks), corrupting databases, registers and logs. From these information assets, it is possible to extract or derive user IDs, security credentials, telemetry data, energy consumption and cumulative power data, and vulnerabilities inherent in the CS firmware − even if many of these are encrypted [41].
To launch a MitM attack on the OCPP security profiles (as also shown in Table 8), the attacker must gain access to the private network. To do so, if TLS (especially when the version is lower than 1.3) is applied (security profiles 2 and 3), then the attacker must obtain the shared session key through the already discovered vulnerabilities such as protocol downgrades, connection renegotiation and session resumption. The work in [40] reflects these weaknesses, which compiles a list of vulnerabilities found in the SSL/TLS protocols, while the work [11] states several examples of threats in the TLS-based OCPP-v1.6. Other data flows that may be threatened are charging requests to the CSMS via the web or mobile app, or directly to the CS via technologies such as BLE, NFC and RFID [42, 43]. A MitM in these communications could leak sensitive user information (e.g., IDs) to later impersonate him/her [44].
3.2.5 Denial of service
This threat disables the availability of system services and may cause significant disruption and damage. This also means that if an attacker performs a DoS, for example, on the communication with the authentication server, end users will not be able to request CTs, interrupting the real energy charge in their EVs (TC-2, TC-3 and TC-6). On the other hand, if the aim of the attack is to interfere with OCPP transactions (e.g., through an on-path attacks such as black holes, selective forwarding or gray holes, or replays [11, 20]) or deny access to the database of the CSMS or EMS, this can have even a greater impact by causing loss of control of the DERs and CSs (TC-1, TC-2, TC-3 and TC-6).
As mentioned above, the OCPP protocol may be manipulated in order to deny service to CSs or the CSMS. For example, a malicious CSMS or an attacker with a Master Pass may stop other users’ transactions or even disable the availability of CSs (F03, C16 and G04 UCs). In addition, if the attacker changes the datetime parameter (“DateTime” CV) of a CS with respect to the CSMS, it would lead to a desynchronization, and, therefore, reserve transactions would not start and stop at the corresponding time. Thus, the duration of any OCPP transaction related to the starting of a charging would not either correspond to the date-time parameter of the CSMS. Attackers may carry out a similar attack with users’ IDs to exploit H01 UC and make massive reservations of EVSEs with a high expiration date. This disables other legitimate users from having the ability to reserve and use these reserved connectors by the adversaries. Moreover, if an attacker carry out a DoS in the communication channel between the CSMS and the CS to force the CSs enter into offline mode, the attacker may take advantage of the offline authorization modes (C13 and C15 UCs) to gain access the CS, as also noted in [11]. Attackers may achieve this purpose through jamming, flooding, replay or massive sending of OCPP heartbeats in short periods of time.
As for energy assets, attackers may be able to alter the EMS, the storage systems or the communication between them so that the storage system is deliberately perturbed. The storage system may, e.g., be blocked to users while the market price is high, i.e., when it is usually recommended to extract energy from the storage system. Moreover, DERs are connected to the MG bus through power converters, whose operation is generally regulated through digital controllers. If attackers gain malicious access to the control and alter the activation signals of the converters or incorporate delays in them, it may cause both the power converters and the energy source itself to operate with electrical magnitudes (voltage, current and/or power) that exceed the maximum allowed. This could result in damage to electrical components or even breakage (TC-2). This vulnerability is also present in electrical storage systems. Controllable loads (EVs or others) carry out their load according to an established criterion, and a control is performed to evaluate the suitability of the load. Access to the data on which these criteria are based may result in a failure to connect loads to the grid. In the case of EVs, their charging/discharging process would not be carried out. For example, adversaries may alter economic data and cause this impact (in an electricity market-oriented scenario), or may also intentionally change data related to grid support services. On the other hand, if an attacker modifies the operating set-points of the generators and loads—decided by the EMS to ensure that the grid operates correctly in terms of voltage and frequency—the MG could become unstable and, as a result, totally or partially inoperative (TC-8, TC-10).
As highlighted in [11], DoS against power flows may also arise. In V2G networks, where the CI is equipped to enable bidirectional power transfer, attackers may execute sophisticated attacks. They could prepare several synchronized attack vectors on different CSs connected to the same power transformer at peak demand hours (interval of highest demand in grid connection and use of CSs). The aim is to extract power from the EV batteries, revert power on a massive scale and cause significant local blackouts or damage to electrical equipment (TC-9) in the MG or the external power system. For instance, energy storage systems, loads connected to the MG (e.g., other EVs) or the converter to connect to the power grid may seriously be affected.
3.2.6 Elevation of privilege
There are two ways to connect to OCPP-based CIs: (i) as a user through a website, mobile application or directly with the CS, where the only functionalities are to reserve the connector of a nearby CS in order to charge his/her EV battery; and (ii) as a CSO via the CCS, with control and configuration functionalities over the CSMS and EMS. To gain unauthorized access by one of these two means, attackers start by finding weak points through which they may first penetrate the network. They then attempt to escalate privileges to gain further permissions or access other sensitive systems.
In addition, there are two types of privilege escalation: horizontal and vertical. In the horizontal mode, an attacker expands his/her privileges by accessing the data of other accounts at the same level. For example, an attacker could leak a legitimate user’s security credential and get unauthorized access to the victim’s account to make charging requests with the victim user’s account. In contrast, in vertical mode, an attacker can obtain such an access through an existing but compromised user account. The attacker starts from a less privileged account until he/she gains the permissions of an IT/OT administrator. This situation would correspond to one where the adversary, without permissions, is able to manipulate and add his/her ID to the local authentication list (C13 UC) in order to later elevate his/her privileges as a legitimate user. Alternatively, an attacker with user permissions could tamper with “MasterPassGroupId” CV and add his/her ID (like a “legitimate” stakeholder) to get the Master Pass permissions. In either case, and as an “authorized” user within the system, he/she could exploit further UCs; e.g., to reserve power in an unauthorized manner (TC-5), or take advantage of the Master Pass to stop any ongoing transaction (TC-1-3, TC-8).
The three methods to authorize a user when the CS is in offline mode in OCPP (corresponding to C functional block of Table 9) are (some already analyzed previously in [11]): (i) authorization cache, (ii) local authorization list and (iii) unknown offline authorization. The former maintains a record of IDs that the CSMS has successfully authorized previously. An adversary could manipulate this cache to add a record with a malicious ID and force the offline mode (with a subsequent DoS to the CSMS) to achieve unauthorized use of the CS. The local authorization list has a list of IDs, which is periodically synchronized with the list of the CSMS (D01 UC). A malicious CSMS or MitM could send a tampered list with invalid IDs and then force the offline mode to use these invalid IDs, gaining unauthorized access to the CS. Finally, if the unknown offline authorization option is enabled, a CS allows automatic authorization of any unknown ID that is not necessarily in the local authorization list or authorization cache. In this case, an attacker must first enable the “OfflineTxForUnknownIdEnabled” CV to TRUE; and under this situation the attacker may take advantage of this modality to cause fraud. He/she may request unauthorized CTs using an invalid ID when the CS is offline (C15 UC).
On the other hand, if an advanced adversary manages to elevate its privileges and gain access to the EMS or CSMS in a stealthy manner, it could lead to greater consequences. Some of them have been mentioned above: (i) inability to configure the MG (TC-1); (ii) disclosure of configuration data and system status (TC-4); (iii) altering consumption data with the aim of economic fraud (TC-7); or (iv) even desynchronizing system parameters (TC-8), putting physical equipment and human lives at risk. CPSs, such as CS infrastructures, increase the number of vulnerabilities due to: (i) the growing complexity of Industry 4.0 communication technologies, combining wired and wireless networks; (ii) their high exposure to external networks, where the CCS commonly contacts external links over the Internet; (iii) increasingly extensive inter-network communications, increasing the number of DERs and smart meters to take advantage of local renewable energy generation and demand management; and (iv) the inheritance of vulnerabilities in established or growing tools, such as the TLS and OCPP communication protocols [45].
Table 11 summarizes all the threat consequences found in each STRIDE threat in a CSs-based MG. In addition, we can observe that T and D threats have a direct impact on the generation and distribution of energy by the MG and therefore pose a higher risk to the system. In the following section, we will evaluate each of the STRIDE threats on (c) and (e) using the DREAD model and then propose a list of countermeasures.
3.3 DREAD model for threat assessment
DREAD provides a mnemonic for the classification of security risks using five categories: Damage, Reproducibility, Exploitability, Affected users and Discoverability. Table 2 (in Sect. 3) details the evaluation procedure and description of each of the DREAD categories. There are different quantitative evaluation methods for this model. In this case, we have followed a variant of the procedure proposed by Microsoft [16]. We evaluate each STRIDE threat in each component with respect to each DREAD category with a value from 1 to 10, where 1 is a low impact and 10 a high-risk threat. After this, we make a weighted average for each STRIDE threat, thus obtaining a numerical value that indicates the level of risk in the system as a whole. In addition, in order to provide a qualitative risk analysis, we establish a list of criteria that relate the evaluations to the rating values. The qualitative risk analysis is based on experience. In this case, we have classified the risk levels as high, medium and low following the criteria proposed by Kavallieratos and Katsikas in [15]. These criteria are also defined in Table 12.
In order to assess the risk, we consider the threats classified in Table 11 (cf. Section 3.2). For each of these threats, each of the criteria established by DREAD are scored manually with a score from 1 to 10. In this case, the risks are analyzed in terms of the impact and consequences on CSs, leaving aside other related infrastructures, such as the MG, to reduce the scope. Moreover, Table 13 reflects the results of this assessment analysis, where T and D (which directly affect energy) correspond to the highest risk threats in CIs. This table also shows how a tampering or DoS leads to major impacts on the system (high risk in Damage and Affected users criteria) and could also be executed by adversaries without detailed security or network knowledge (high risk in Reproducibility, Exploitability and Discoverability criteria). This analysis coincides with the preservation of integrity and availability requirements that are essential in any ICS, and which correspond to T and D in the STRIDE model (cf. Table 1).
On the other hand, S and E threats present a medium level of risk, except for two that are high risk (“CS spoofing” and “OCPP CVs”). As the previous cases, a spoofing or elevation of privileges could have major consequences for the organization, such as fraud, unauthorized access, inefficient operations or energy destabilization. However, for these threats, adversaries require greater cybersecurity expertise (low risk in Exploitability criterion) and, in addition, the threats could be partially/fully covered by appropriate defense measures (low risk in Discoverability criterion), such as security policies, identity management, principle of least privilege, etc. In contrast, R and I threats present the lowest risk. R is easily addressed through the use of digital signature and I is also controlled with the correct use of TLS or VPNs. Note that these measures are already addressed in the OCPP-v2.0.1 protocol with security profiles 2 and 3, strongly affecting the Discoverability criterion of the DREAD model. Other significant DREAD criteria, which influence the low risk assessment of these threats, are Damage and Affected users.
Overall, threats directly related to CSs present a high level of risk, mainly due to their high exposure to the public. The fact that CSs are generally deployed in open environments makes them more prone to physical attacks, whether natural or intentional. Reproducibility, Exploitability and Discoverability criteria of the DREAD evaluation model are highly affected in these threats. Table 13 clarifies that “CS spoofing”, “OCPP CVs” (the variables are stored in the CS) and “DoS to the CS” are the threats with the highest risk in each of the corresponding STRIDE categories.
4 Recommendations for mitigation
This section explores a set of recommendations to address the threats discussed in the previous section, and especially those related to D and T together with those presenting high and medium risk (\(\ge \) 5.0) in Table 13.
4.1 Priority recommendations for risks [8.0, 10.0]
As stated in the previous section, the most potential threats are those related to “DoS to CS”, manipulation of “OCPP CVs” and “CS spoofing”. These three threats require OCPP transaction-level protection and especially for A01 UC. For this protection, it is advisable to force the use of mutual authentication via TLS using certificates in the CS and CSMS (security profile 3 in OCPP-v2.0.1). Although this action avoids any disclosure or manipulation of identification variables (such as Identity and BasicAuthPassword), the TLS version also influences the protection process, where it is also recommended to apply TLSv1.3 or related protocols such as IPSec. On the other hand, as CSs are generally deployed in open and public environments, TLS certificates (included private keys stored in plain text) may also be easily manipulated through a physical access. In these circumstances, it is necessary to foresee a surveillance plan (e.g., installation of cameras), as well as the deployment of CSs enabled with shock-resistant casings and SW-based anti-tampering solutions to prevent not only access to keys and certificates, but also illicit modifications [20].
Any DoS also has a significant social and economic impact, so it is essential to activate redundant mechanisms that facilitate not only the permanent connection to the CSMS, but also the authentication and authorization of legitimate users. To do this, it is essential to (i) address mainly redundant architectures in terms of communication and services, such as the use of proxies around the CSs (or in the local controllers), and to (ii) periodically update the list of users (with unique IDs) who have permissions to charge their EVs. In this way, it is possible to facilitate the authorization of legitimate operations with the CSMS when stations lose connection with the central system. Likewise, the official authorities, owners of the Master Pass, must follow training programs to avoid denials of service, caused by themselves or by others who may have stolen the Master Pass. One way to detect these unfortunate situations, caused mainly by lack of knowledge or training, would be through reputation mechanisms capable of identifying irregular behavior at the user level (lack of interest or knowledge), but also through mechanisms that enhance data traceability to identify at any time the use and misuse of the Master Pass. In this case, we highlight the capacities of some disruptive technologies like blockchain since it guarantees data immutability, traceability, auditability and accountability [46, 47].
Malware (in a CS, the CSMS or the EMS) is another threat that can cause DoS. It can be detected by checking the integrity of each SW component. This type of verification is also critical to deal with manipulations to OCPP CVs (B05 UC). Not only encryption schemes are useful to prevent direct access to their content, but also the traditional use of Message Authentication Message (MAC) functions and hash functions (e.g., SHA-256/SHA-512) can be useful. The latter can even help the CS to (i) not only verify the integrity of each variable, but also to (ii) manage digital signatures for each OCPP transaction, ensuring authentication, non-repudiation and accountability. In other words, any action performed in the CS, including those performed after authentication in offline mode (C13 and C15 UCs), could be logged and linked. This also means that each entity (including the device/process or a transaction) within the organization has to have a unique ID to link operations and actions.
Specific mechanisms for HW and SW diagnostics and advanced detection, supported by dynamic event management systems like the Security Information and Event Management (SIEM) systems in the CSMS, could also facilitate local and global monitoring of all these potential threats and enable the system to make timely decisions [48]. These mechanisms usually rely on Machine Learning (ML) algorithms to predict any deviation in the normal status of control components and their behavior [49]. Depending on the capabilities of the devices that integrate them, the selection of the model can vary. The authors of the work [50] determine that decision trees, fuzzy logic, rules, statistics and clustering may be good candidates for detecting anomalies in very limited devices. Moreover, SW agents and additional (current, voltage, phasor and power) sensors acting as inspectors can be integrated as part of a distributed or collaborative detection system [20, 49] to extend the input data for these techniques, and ensure greater accuracy in detection processes. The goal could be, for example, to identify if there is an illogical physical correspondence that may affect the actual availability of the CS, and may be strong evidence of a possible attack or accidental threat. In this sense, reputation measures at device level can also be a good approach to estimate when maintenance actions should be launched and plans should be reviewed accordingly.
4.2 Priority recommendations for risks [5.0, 8.0]
As can be seen in Table 14, most of the countermeasures are transversal to all UCs—those marked in the table with the symbol R−, including those countermeasures considered of medium risk. From the table, we also note that access control should follow solutions that prevent offline authentication modes. This requires maintaining the connection to the CSMS using, for example, redundant mechanisms as mentioned above, and validating any connection with external entities, via TLS with certificates and digital signature in each transaction. On the other hand, continuous maintenance and certification of energy components (DERs and storage systems) is also relevant to guarantee the availability of minimum services to the end user. In this sense, anomaly-based detection mechanisms and diagnostics with support in blockchain networks for traceability of anomalies can also be incorporated to predict variations in the behavior of critical components (e.g., caused by failures or by malicious CSOs—related to the N03-N06 UCs). This information can even feed to other analytics of the EMS to, for example, (i) favor the smart charging procedures and their profiles (related to K UCs), or (ii) optimize existing resources in the EMS. The latter is relevant for managing MG controller set-points; increasing run-time may mean that this power system is not scalable. Instead of this centralized approach, an alternative could be the implementation of distributed control algorithms. Coordinated and distributed control algorithms make use of the information sent by the immediate neighbors in the MG topology and incorporate them into the optimization sub-problem to reach the optimum solution with an iterative process [51]. For instance, several CSs may exchange data related to their current operation, which may help the local controllers to decide their best set-point. In this way, the data integrity weaknesses that the control algorithm must withstand are limited to a smaller area.
Last but not least, it is necessary to protect any OCPP data, either during its transfer (related to the B06a dn B08 UCs) or its storage in the CS, CSMS or the EMS. As indicated above, not only TLS or IPSec should be part of the future EVCI designs, but also cryptography primitives should be part of the encryption processes of any sensitive data in the CS, the CSMS and the EMS. Depending of the data volume and the analytic models applied, privacy-enhancing technologies should be contemplated to protect user privacy [11]. In general, CCS systems, and especially CSMS and EMS, manage multiple types of data (e.g., consumption per zone) whose access can help attackers infer private information, even if it is encrypted [41]. In addition, attackers can also deduce users’ routine patterns by observing how frequently the CSs are used. Thus, more research remains to be done on techniques that (i) intensify the randomness of resource usage and device location within the infrastructure and (ii) obfuscate the OCPP transactions to protect real consumption.
4.3 Other essential recommendations
To complement the detection processes identified in the previous section, both CSs and CSMSs must be able to automatically estimate and manage potential risks [48]. This means that the consequences of malicious interactions of (trusted) third parties, lack of physical and logical protection and lack of testing on critical resources can be prevented by dynamically calculating potential risks. For proper governance, it is also mandatory to comply with regulatory frameworks, establish security controls and follow current strategic and organizational procedures according to current standards. Through these standards, it is possible to harmonize and incorporate new approaches (whether on the CS side, the CSMS or the EMS) complying with international and national regulatory schemes, and especially those related to the energy sector.
As mentioned above, any record can be considered a good practice that benefits the operation of other systems (e.g., SIEMs) and the governance of an organization. Through these records, it is possible to derivate security breaches by verifying the compliance with regulatory frameworks and plans. For example, updating of CS firmware is often a priority requirement within maintenance plans, and should be carried out with care, first verifying the CSMS certificate (source of the download) and firmware signature (as recommended in L01 UC instead of L02). As is evident, these solutions, and others mentioned throughout this paper, can demand high computational and storage resources to enrich analysis processes and improve decision making, impacting (in some way) the operational processes of each CS. Charging stations are often equipped with limited cyber-physical elements [50] which forces the scientific community to continue researching on solutions that are based on effective and lightweight approaches in order not to clash with operational requirements.
5 Conclusions and future work
This work comprises a risk assessment analysis with application to charging infrastructures connected to MGs under the control of the OCPP-v2.0.1 protocol. The analysis, based on the combination of the traditional methodologies STRIDE + DREAD and denoted in this work as SD\(^{\tiny {\mathrm {c+e}}}\)—c, control and e, energy—has proven to be a feasible tool for classifying and prioritizing threats. The results indicate that tampering and denial of service pose the greatest risks, which in turn confirms that integrity and availability requirements in critical systems are essential to ensure control of operations and availability of minimal services, such as energy. We also believe that SD\(^{\tiny {\mathrm {c+e}}}\) can be applied to other critical systems where energy and computing elements are jointly managed, giving a broad and useful perspective of vulnerabilities and threats to be faced. As a complement to this study, the paper also adds a set of recommendations for mitigation, established according to the risk analysis of SD\(^{\tiny {\mathrm {c+e}}}\) and priorities.
As future work, we intend to extend the study to contemplate new charging scenarios, such as bidirectional charging networks (V2G) and wireless charging. These types of scenarios present new threats, electronics, control and power flows, which have not yet been analyzed in the literature.
Availability of data and materials
Not applicable.
Code availability
Not applicable.
References
Lee, J.H., Chakraborty, D., Hardman, S.J., Tal, G.: Exploring electric vehicle charging patterns: mixed usage of charging infrastructure. Transp. Res. Part D Transp. Environ. 79, 102249 (2020)
Sadeghian, O., Oshnoei, A., Mohammadi-ivatloo, B., Vahidinasab, V., Anvari-Moghaddam, A.: A comprehensive review on electric vehicles smart charging: solutions, strategies, technologies, and challenges. J. Energy Storage 54, 105241 (2022)
Faheem, M., Shah, S., Butt, R., Raza, B., Anwar, M., Ashraf, M., Ngadi, M., Gungor, V.: Smart grid communication and information technologies in the perspective of industry 4.0. Oppor. Chall. Comput. Sci. Rev. 30, 1–30 (2018)
Wang, C., Zhang, T., Luo, F., Li, F., Liu, Y.: Impacts of cyber system on microgrid operational reliability. IEEE Trans. Smart Grid 10(1), 105–115 (2019)
Sahoo, S., Dragicevic, T., Blaabjerg, F.: Cyber security in control of grid-tied power electronic converters-challenges and vulnerabilities. IEEE J. Emerg. Sel. Top. Power Electron. 9, 5326–5340 (2019)
Liu, Y., Li, Y., Wang, Y., Zhang, X., Gooi, H.B., Xin, H.: Robust and resilient distributed optimal frequency control for microgrids against cyber attacks. IEEE Trans. Ind. Inform. 18, 375–386 (2021)
Chen, C., Xiao, L., Duan, S.D., Chen, J.: Cooperative optimization of electric vehicles in microgrids considering across-time-and-space energy transmission. IEEE Trans. Ind. Electron. 66(2), 1532–1542 (2019)
Sayed, M.A., Atallah, R., Assi, C., Debbabi, M.: Electric vehicle attack impact on power grid operation. Int. J. Electr. Power Energy Syst. 137, 107784 (2022)
Johnson, J., Berg, T., Anderson, B., Wright, B.: Review of electric vehicle charger cybersecurity vulnerabilities, potential impacts, and defenses. Energies 15(11), 3931 (2022)
Open Charge Alliance: Open charge point protocol 2.0.1 (2020). https://www.openchargealliance.org/protocols/ocpp-201/
Alcaraz, C., Lopez, J., Wolthusen, S.: OCPP protocol: security threats and challenges. IEEE Trans. Smart Grid 8(5), 2452–2459 (2017)
ISO 15118-1:2019: Road vehicles—vehicle to grid communication interface-part 1: general information and use-case definition (2019). https://www.iso.org/standard/69113.html
ISO 15118-2:2014: Road vehicles—vehicle-to-grid communication interface—part 2: network and application protocol requirements (2014). https://www.iso.org/standard/55366.html
Open Charge Alliance: Open charge point protocol 1.6 (2015). https://www.openchargealliance.org/protocols/ocpp-16/
Kavallieratos, G., Katsikas, S.: Managing cyber security risks of the cyber-enabled ship. J. Mar. Sci. Eng. 8(10), 1–19 (2020)
Threat modeling for drivers—windows drivers | Microsoft Docs (2021). https://docs.microsoft.com/en-us/windows-hardware/drivers//driversecurity/threat-modeling-for-drivers
Khan, R., McLaughlin, K., Laverty, D., Sezer, S.: Stride-based threat modeling for cyber-physical systems. In: 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), pp. 1–6 (2017)
Tseng, T.W., Wu, C.T., Lai, F.: Threat analysis for wearable health devices and environment monitoring internet of things integration system. IEEE Access 7, 144983–144994 (2019)
Zografopoulos, I., Ospina, J., Liu, X., Konstantinou, C.: Cyber-physical energy systems security: threat modeling, risk assessment, resources, metrics, and case studies. IEEE Access 9, 29775–29818 (2021). https://doi.org/10.1109/ACCESS.2021.3058403
Garofalaki, Z., Kosmanos, D., Moschoyiannis, S., Kallergis, D., Douligeris, C.: Electric vehicle charging: a survey on the security issues and challenges of the open charge point protocol (OCPP). IEEE Commun. Surv. Tutor. 24(3), 1504–1533 (2022)
Li, G., Wu, D., Hu, J., Li, Y., Hossain, M.S., Ghoneim, A.: HELOS: heterogeneous load scheduling for electric vehicle-integrated microgrids. IEEE Trans. Veh. Technol. 66(7), 5785–5796 (2017)
Rubio, J.E., Alcaraz, C., Lopez, J.: Addressing security in OCPP: protection against man-in-the-middle attacks. In: 2018 9th IFIP International Conference on New Technologies, Mobility and Security, NTMS 2018—Proceedings, 2018-January, pp. 1–5 (2018)
Sen, S., Kumar, V.: Microgrid control: a comprehensive survey. Annu. Rev. Control 45, 118–151 (2018)
Priyadharshini, N., Gomathy, S., Sabarimuthu, M.: WITHDRAWN: a review on microgrid architecture, cyber security threats and standards. Mater. Today Proc. (2020). https://doi.org/10.1016/j.matpr.2020.10.622
Alcaraz, C., Lopez, J., Wolthusen, S.: Policy enforcement system for secure interoperable control in distributed smart grid systems. J. Netw. Comput. Appl. 59, 301–314 (2016)
Nejabatkhah, F., Li, Y.W.: Cyber-security of smart microgrids: a survey. Energies 14, 27 (2020)
Microsoft: STRIDE chart microsoft security (2021). https://www.microsoft.com/security/blog/2007/09/11/stride-chart/
Microsoft: Uncover security design flaws using the STRIDE approach (2019). https://learn.microsoft.com/en-us/archive/msdn-magazine/2006/november/uncover-security-design-flaws-using-the-stride-approach
Hussain, S., Kamal, A., Ahmad, S., Rasool, G., Iqbal, S.: Threat modeling methodologies: a survey. Sci. Int. (Lahore) 26(4), 1607–1609 (2014)
Orellana, C., Villegas, M.M., Astudillo, H.: Mitigating security threats through the use of security tactics to design secure cyber-physical systems (CPS). ACM Int. Conf. Proc. Ser. 2, 109–115 (2019)
Yampolskiy, M., Horvath, P., Koutsoukos, X.D., Xue, Y., Sztipanovits, J.: Systematic analysis of cyber-attacks on CPS-evaluating applicability of DFD-based approach. In: Proceedings—2012 5th International Symposium on Resilient Control Systems, ISRCS 2012, pp. 55–62 (2012)
Lightman, S., Brewer, T.: Symposium on Federally Funded Research on Cybersecurity of Electric Vehicle Supply Equipment (EVSE) (2020)
Jouvray, C., Pellischek, G., Tiguercha, M.: Impact of a smart grid to the electric vehicle ecosystem from a privacy and security perspective. World Electr. Veh. J. 6(4), 1115–1124 (2013)
Girdhar, M., Hong, J., Lee, H., Song, T.J.: Hidden Markov models based anomaly correlations for the cyber-physical security of EV charging stations. IEEE Trans. Smart Grid 13(5), 3903–3914 (2021)
Shao, G.: MITRE ATT &CK. ATT &CK v12 (015-2022). https://attack.mitre.org
Atlantic, F., Ra, B.: The PEV security challenges to the smart grid: analysis of threats and a mitigation strategies. In: 2013 International Conference on Connected Vehicles and Expo (ICCVE), pp. 300–305 (2013)
Antoun, J., Kabir, M.E., Moussa, B., Atallah, R., Assi, C.: A detailed security assessment of the EV charging ecosystem. IEEE Netw. 34(3), 200–207 (2020)
Pourmirza, Z., Walker, S.: Electric vehicle charging station: cyber security challenges and perspective. In: 2021 9th IEEE International Conference on Smart Energy Grid Engineering, SEGE 2021, pp. 111–116 (2021)
Gebauer, L., Trsek, H., Lukas, G.: 2022 IEEE 27th International Conference on Emerging Technologies and Factory Automation (ETFA), pp. 1–4 (2022). https://doi.org/10.1109/ETFA52439.2022.9921430
Satapathy, A., Livingston, J.: A comprehensive survey on SSL/TLS and their vulnerabilities. Int. J. Comput. Appl. 153(5), 31–38 (2016)
Jegorova, M., Kaul, C., Mayor, C., O’Neil, A.Q., Weir, A., Murray-Smith, R., Tsaftaris, S.A.: Survey: leakage and privacy at inference time (2021). arXiv preprint arXiv:2107.01614
Albahar, M., Haataja, K., Toivanen, P., Albahar, M.A.: Bluetooth MITM vulnerabilities: a literature review, novel attack scenarios, novel countermeasures, and lessons learned. Int. J. Inf. Technol. Secur. 4(2018), 25–49 (2016)
Akter, S., Chakraborty, T., Khan, T.A., Chellappan, S., Al Islam, A.A.: Can you get into the middle of near field communication? In: Proceedings—Conference on Local Computer Networks, LCN, pp. 365–373 (2017)
Zhang, Y., Weng, J., Dey, R., Fu, X.: Bluetooth low energy (BLE) security and privacy. Encycl. Wirel. Netw. 2, 123–134 (2020)
Li, Z., Shahidehpour, M., Aminifar, F.: Cybersecurity in distributed power systems. Proc. IEEE 105(7), 1367–1388 (2017)
Mollah, M.B., Zhao, J., Niyato, D., Lam, K.Y., Zhang, X., Ghias, A.M.Y.M., Koh, L.H., Yang, L.: Blockchain for future smart grid: a comprehensive survey. IEEE Internet Things J. 8(1), 18–43 (2021)
Zhuang, P., Zamir, T., Liang, H.: Blockchain for cybersecurity in smart grid: a comprehensive survey. IEEE Trans. Ind. Inform. 17(1), 3–19 (2021)
Fischer-Hübner, S., Alcaraz, C., Ferreira, A., Fernandez-Gago, C., Lopez, J., Markatos, E., Islami, L., Akil, M.: Stakeholder perspectives and requirements on cybersecurity in Europe. J. Inf. Secur. Appl. 61, 102916 (2021)
Cumplido, J., Alcaraz, C., Lopez, J.: Collaborative anomaly detection system for charging stations. Comput. Secur. ESORICS 2022, 716–736 (2022)
Alcaraz, C., Cazorla, L., Fernandez, G.: Context-awareness using anomaly-based detectors for smart grid domains. In: 9th International Conference on Risks and Security of Internet and Systems, vol. 8924, pp. 17–34 (2015)
Guo, Y., Gao, H., Wu, Q.: Distributed cooperative voltage control of wind farms based on consensus protocol. Int. J. Electr. Power Energy Syst. 104, 593–602 (2019)
Acknowledgements
This work has been supported by the “Smart and Secure EV Urban Lab II” through the Second Own Plan of Smart-Campus of the Universidad de Malaga and partially funded by the Spanish Ministerio de Ciencia e Innovacion (MICINN) by project PID2019-110531-RA-I00 from the “Proyectos de I+D+i - RTI Tipo A” programme and by the SecureEdge project also funded by the Spanish Ministerio de Ciencia e Innovacion (AEI/10.13039/501100011033/) under Grant PID2019-110565RB-I00.
Funding
Funding for open access publishing: Universidad Málaga/CBUA.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Alcaraz, C., Cumplido, J. & Trivin̄o, A. OCPP in the spotlight: threats and countermeasures for electric vehicle charging infrastructures 4.0. Int. J. Inf. Secur. 22, 1395–1421 (2023). https://doi.org/10.1007/s10207-023-00698-8
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-023-00698-8