Abstract
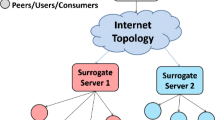
In Peer-to-Peer (P2P) network systems, content (object) delivery between nodes is often required. One way to study such a distributed system is by defining games, which involve selfish nodes that make strategic choices on replicating content in their local limited memory (cache) or accessing content from other nodes for a cost. These Selfish Replication games have been introduced in Chun et al. (2004) for nodes that do not have any capacity limits, leaving the capacitated problem, i.e. Capacitated Selfish Replication (CSR) games, open. In this work, we first form the model of the CSR games, for which we perform a Nash equilibria analysis. In particular, we focus on hierarchical networks, given their extensive use to model communication costs of content delivery in P2P systems. We present an exact polynomial-time algorithm for any hierarchical network, under two constraints on the utility functions: 1) “Nearer is better”, i.e. the closest the content is to the node the less its access cost is, and 2) “Independence of irrelevant alternatives”, i.e. aggregation of individual node preferences. This generalization represents a vast class of utilities and more interestingly allows each of the nodes to have simultaneously completely different functional forms of utility functions. In this general framework, we present CSR games results on arbitrary networks and outline the boundary between intractability and effective computability in terms of the network structure, object preferences, and the total number of objects. Moreover, we prove that the problem of equilibria existence becomes NP-hard for general CSR games. By adding some constraints in the number of objects and their preferences, we show that the equilibrium can be found in polynomial time. Finally, we introduce the fractional version of CSR games (F-CSR) to represent content distribution. We prove that equilibrium exists for every F-CSR game, but it is PPAD-complete.





Similar content being viewed by others
Notes
not to be confused with “fictitious play” [24] which involves learning
We let each node be both descendant and ancestor of itself.
We define a total preorder as a binary relation that satisfies reflexivity, transitivity, and totality. By totality we mean that for any i, j, k, either j ≥ik or k ≥ij.
A strict weak order is a strict partial order >, i.e. a transitive relation that is irreflexive, in which the “neither a > b nor b > a” relation is transitive. Strict weak orders and total preorders are widely used in the field of microeconomics.
References
Ahmadyan, S.N., Etesami, S.R., Poor, H.V.: A random tree search algorithm for Nash equilibrium in capacitated selfish replication games. In: IEEE 55th conference on decision and control (CDC), pp 4439–4444. https://doi.org/10.1109/CDC.2016.7798943 (2016)
Angel, E., Bampis, E., Pollatos, G.G., Zissimopoulos, V.: Optimal data placement on networks with constant number of clients. Theoretical Computer Science (2013)
Arrow, K.: Social choice and individual values. Yale University Press (1951)
Baev, I.D., Rajaraman, R., Swamy, C.: Approximation Algorithms for Data Placement Problems. SIAM J. Comput. 38(4), 1411–1429 (2008)
Byers, J.W., Luby, M., Mitzenmacher, M., Rege, A.: A digital fountain approach to reliable distribution of bulk data. In: SIGCOMM ’98, pp 56–67 (1998)
Chen, X., Deng, X., Teng, S.H.: Settling the complexity of computing two-player Nash equilibria. Journal of the ACM (JACM), 56(3) (2009)
Chen, Y., Katz, R.H., Kubiatowicz, J.D.: Scan: A dynamic, scalable, and efficient content distribution network. In: Mattern, F., Naghshineh, M. (eds.) Pervasive computing, pp 282–296. Springer, Berlin (2002)
Chun, B.G., Chaudhuri, K., Wee, H., Barreno, M., Papadimitriou, C.H., Kubiatowicz, J.: Selfish caching in distributed systems: A game-theoretic analysis. In: ACM symposium on principles of distributed computing (PODC), pp 21–30 (2004)
Dabek, F., Kaashoek, M.F., Karger, D., Morris, R., Stoica, I.: Wide-area cooperative storage with cfs. In: Proceedings of the 8th ACM symposium on operating systems principles, SOSP ’01. https://doi.org/10.1145/502034.502054, pp 202–215. ACM, New York (2001)
Danzig, P.: Netcache architecture and deployment. Comput. Netw. ISDN Syst. 30(22-23), 2081–2091 (1998). https://doi.org/10.1016/S0169-7552(98)00250-5
Daskalakis, C., Goldberg, P.W., Papadimitriou, C.H.: The complexity of computing a Nash equilibrium. STOC ACM, 71–78 (2006)
Devanur, N.R., Garg, N., Khandekar, R., Pandit, V., Saberi, A., Vazirani, V.V.: Price of anarchy, locality gap, and a network service provider game. In: WINE, pp 1046–1055 (2005)
Douceur, J.R., Wattenhofer, R.P.: Large-scale simulation of replica placement algorithms for a serverless distributed file system. In: MASCOTS 2001 proceedings 9th international symposium on modeling, analysis and simulation of computer and telecommunication systems, pp. 311–319. https://doi.org/10.1109/MASCOT.2001.948882 (2001)
Etesami, S.R., Basar, T.: Pure Nash equilibrium in capacitated selfish replication (CSR) game. arXiv:1404.3442 (2014)
Etesami, S.R., Basar, T.: Approximation algorithm for the binary-preference capacitated selfish replication game and a tight bound on its price of anarchy. arXiv:1506.04047v2 (2016)
Etesami, S.R., Basar, T.: Pure Nash equilibrium in a capacitated resource allocation game with binary preferences. arXiv:1404.3442v3(2016)
Etesami, S.R., Basar, T.: Pure Nash equilibrium in a capacitated selfish resource allocation game. IEEE Transactions on Control of Network Systems PP(99), 1–1 (2016)
Etesami, S.R., Başar, T.: Network games, pp 1–46. Springer International Publishing, Cham (2017). https://doi.org/10.1007/978-3-319-27335-8_10-1
Etesami, S.R., Başar, T.: An approximation algorithm and price of anarchy for the binary-preference capacitated selfish replication game. In: 54th IEEE conference on decision and control (CDC), pp. 3568–3573. https://doi.org/10.1109/CDC.2015.7402771 (2015)
Etesami, S.R., Başar, T.: Price of anarchy and an approximation algorithm for the binary-preference capacitated selfish replication game. Automatica 76(Supplement C), 153–163 (2017). https://doi.org/10.1016/j.automatica.2016.10.002
Fabrikant, A., Luthra, A., Maneva, E., Papadimitriou, C.H., Shenker, S.: On a Network Creation Game. In: PODC ’03: Proceedings of the 22nd annual symposium on principles of distributed computing. https://doi.org/10.1145/872035.872088, pp 347–351. ACM Press, New York (2003)
Fan, L., Cao, P., Almeida, J., Broder, A.Z.: Summary cache: A scalable wide-area web cache sharing protocol. In: Proceedings of the ACM SIGCOMM ’98 conference on applications, technologies, architectures, and protocols for computer communication, SIGCOMM ’98. https://doi.org/10.1145/285237.285287, pp 254–265. ACM, New York (1998)
Feldman, M., Chuang, J.: Overcoming free-riding behavior in peer-to-peer systems. ACM Sigecom Exchanges 5(4), 41–50 (2005)
Fudenberg, D., Levine, D.: The theory of learning in games. MIT Press (1998)
Garces-Erice, L., Biersack, E.W., Felber, P.A., Ross, K.W., Urvoy-Keller, G.: Hierarchical peer-to-peer systems. Parallel Process. Lett. 13 (04), 643–657 (2003). https://doi.org/10.1142/S0129626403001574
Garey, M., Johnson, D.: Computers and intractability. Freeman Press (1979)
Goemans, M.X., Li, L., Mirrokni, V.S., Thottan, M.: Market sharing games applied to content distribution in ad hoc networks. IEEE J. Sel. Areas Commun. 24 (5), 1020–1033 (2006). https://doi.org/10.1109/JSAC.2006.872884
Goemans, M.X., Li, L., Mirrokni, V.S., Thottan, M.: Market sharing games applied to content distribution in Ad Hoc networks. IEEE J. Sel. Areas Commun. 24(5), 1020–1033 (2006)
Gopalakrishnan, R., Kanoulas, D., Karuturi, N., Pandu Rangan, C., Rajaraman, R., Sundaram, R.: Cache me if you can: Capacitated selfish replication games. In: Latin American symposium on theoretical informatics (LATIN), vol. 7256, pp. 420-432 (2012)
Gribble, S.D., Halevy, A.Y., Ives, Z.G., Rodrig, M., Suciu, D.: What can database do for peer-to-peer?. In: WebDB workshop on databases and the web (2001)
Hu, X., Gong, J.: PhD forum: Not so cooperative caching. In: 21st IEEE international conference on network protocols (ICNP), pp. 1–3. https://doi.org/10.1109/ICNP.2013.6733656 (2013)
Hu, X.Y., Gong, J.: Study on the theoretical framework of not so cooperative caching. J. Internet Technol. 15(3), 351–362 (2014). https://doi.org/10.6138/JIT.2014.15.3.04
Iyer, S., Rowstron, A.I.T., Druschel, P.: Squirrel: a decentralized peer-to-peer web cache. In: PODC (2002)
Jain, K., Vazirani, V.V.: Primal-dual approximation algorithms for metric facility location and k-median problems. In: 40th annual symposium on foundations of computer science (Cat. No.99CB37039), pp. 2–13. https://doi.org/10.1109/SFFCS.1999.814571(1999)
Jamin, S., Jin, C., Jin, Y., Raz, D., Shavitt, Y., Zhang, L.: On the placement of internet instrumentation. In: Proceedings IEEE INFOCOM 2000. Conference on computer communications. 19th annual joint conference of the ieee computer and communications societies (Cat. No.00CH37064), vol. 1, pp. 295-304. https://doi.org/10.1109/INFCOM.2000.832199 (2000)
Jamin, S., Jin, C., Kurc, A.R., Raz, D., Shavitt, Y.: Constrained mirror placement on the internet. In: Proceedings IEEE INFOCOM 2001. Conference on computer communications. 20th annual joint conference of the ieee computer and communications society (Cat. No.01CH37213), vol. 1, pp. 31–40. https://doi.org/10.1109/INFCOM.2001.916684 (2001)
Johnson, D.S., Papadimitriou, C.H., Yannakakis, M.: How Easy is Local Search? J. Comput. Syst. Sci. 37(1), 79–100 (1988)
Karger, D., Lehman, E., Leighton, T., Panigrahy, R., Levine, M., Lewin, D.: Consistent hashing and random trees: Distributed caching protocols for relieving hot spots on the world wide web. In: Proceedings of the 29th annual ACM symposium on theory of computing (STOC), pp. 654–663 (1997)
Kintali, S., Poplawski, L.J., Rajaraman, R., Sundaram, R., Teng, S.H.: Reducibility among fractional stability problems. Proceedings of the 50th annual IEEE symposium on foundations of computer science (FOCS) (2009)
Ko, B.J., Rubenstein, D.: Distributed self-stabilizing placement of replicated resources in emerging networks. IEEE/ACM Trans. Netw. 13(3), 476–487 (2005). https://doi.org/10.1109/TNET.2005.850196
Korupolu, M., Plaxton, C.G., Rajaraman, R.: Placement algorithms for hierarchical cooperative caching. J. Algorithms 38, 260–302 (2001)
Korupolu, M.R., Dahlin, M.: Coordinated placement and replacement for large-scale distributed caches. IEEE Trans. Knowl. Data Eng. 14(6), 1317–1329 (2002)
Koutsoupias, E., Papadimitriou, C.: Worst-case equilibria. In: STACS, pp. 404–413 (1999)
Kubiatowicz, J., Bindel, D., Chen, Y., Czerwinski, S., Eaton, P., Geels, D., Gummadi, R., Rhea, S., Weatherspoon, H., Weimer, W., Wells, C., Zhao, B.: Oceanstore: An architecture for global-scale persistent storage. ACM SIGPLAN Not. 35(11), 190–201 (2000). https://doi.org/10.1145/356989.357007
Laoutaris, N., Smaragdakis, G., Bestavros, A., Stavrakakis, I.: Mistreatment in distributed caching groups: Causes and implications. In: INFOCOM (2006)
Laoutaris, N., Telelis, O., Zissimopoulos, V., Stavrakakis, I.: Distributed selfish replication. IEEE Trans. Parallel Distrib. Syst. 17(12), 1401–1413 (2006)
Laoutaris, N., Smaragdakis, G., Oikonomou, K., Stavrakakis, I., Bestavros, A.: Distributed placement of service facilities in large-scale networks. In: INFOCOM, pp. 2144–2152 (2007)
Leff, A., Wolf, J.L., Yu, P.S.: Replication algorithms in a remote caching architecture. IEEE Trans. Parallel Distrib. Syst. 4(11), 1185–1204 (1993)
Li, B., Golin, M.J., Italiano, G.F., Deng, X., Sohraby, K.: On the optimal placement of web proxies in the internet. In: IEEE INFOCOM ’99. Conference on computer communications. Proceedings. 18th annual joint conference of the IEEE computer and communications societies. The future is now (Cat. No.99CH36320), vol. 3, pp. 1282–1290. https://doi.org/10.1109/INFCOM.1999.752146 (1999)
Mahdian, M., Ye, Y., Zhang, J.: Improved approximation algorithms for metric facility location problems. In: Jansen, K, Leonardi, S, Vazirani, V (eds.) Approximation algorithms for combinatorial optimization, pp 229–242. Springer, Berlin (2002)
McCuaig, W., Robertson, N., Seymour, P.D., Thomas, R.: Permanents, Pfaffian orientations, and even directed circuits. In: STOC, pp. 402–405 (1997)
Mettu, R.R., Plaxton, C.G.: The online median problem. In: Proceedings of the 41st annual symposium on foundations of computer science. FOCS ’00, p 339. IEEE Computer Society, Washington (2000)
Nisan, N., Roughgarden, T., Tardos, É., Vazirani VV: Algorithmic game theory. Cambridge University Press, Cambridge (2007)
Osborne, M.J., Rubinstein, A.: A course in game theory. MIT Press (1994)
Pacifici, V.: Resource allocation in operator-owned content delivery systems. KTH School of Electrical Engineering, PhD thesis (2016)
Papadimitriou, C.H.: On the complexity of the parity argument and other inefficient proofs of existence. JCSS 48(3), 498–532 (1994)
Pollatos, G.G., Telelis, O., Zissimopoulos, V.: On the social cost of distributed selfish content replication. In: Networking, pp. 195–206 (2008)
Qiu, L., Padmanabhan, V.N., Voelker, G.M.: On the placement of web server replicas. In: Proceedings IEEE INFOCOM 2001. Conference on computer communications. 20th annual joint conference of the IEEE computer and communications society (Cat. No.01CH37213), vol. 3, pp. 1587-1596. https://doi.org/10.1109/INFCOM.2001.916655 (2001)
Rabin, M.: Efficient dispersal of information for security, load balancing and fault tolerance. J. ACM 36, 335–348 (1989)
Rabinovich, M., Rabinovich, I., Rajaraman, R., Aggarwal, A.: A dynamic object replication and migration protocol for an internet hosting service. In: Proceedings. 19th IEEE international conference on distributed computing systems (Cat. No.99CB37003), pp. 101–113. https://doi.org/10.1109/ICDCS.1999.776511 (1999)
Robertson, N., Seymour, P.D., Thomas, R.: Permanents, Pfaffian orientations, and even directed circuits. Annals of Mathematics, pp. 929–975 (1999)
Rosenwein, M.B.: Discrete location theory. In: Mirchandani, P.B., Francis, R.L. (eds.) . Networks 24(2):124–125 https://doi.org/10.1002/net.3230240212, p 555. Wiley, New York (1990)
Rowstron, A., Druschel, P.: Storage management and caching in past, a large-scale, persistent peer-to-peer storage utility. In: Proceedings of the 18th ACM symposium on operating systems principles, SOSP ’01. https://doi.org/10.1145/502034.502053, pp 188–201. ACM, New York (2001)
Saito, Y., Karamanolis, C., Karlsson, M., Mahalingam, M.: Taming aggressive replication in the pangaea wide-area file system. SIGOPS Oper. Syst. Rev. 36(SI), 15–30 (2002). https://doi.org/10.1145/844128.844131
Schrijver, A.: Combinatorial optimization (3 Vol.) Springer-Verlag, Berlin (2003)
Shokrollahi, A.: Raptor codes. In: IEEE Trans Inf Theory, pp. 2551–2567 (2006)
Tang, X., Chanson, S.T.: Coordinated en-route web caching. IEEE Trans. Comput. 51(6), 595–607 (2002). https://doi.org/10.1109/TC.2002.1009146
Tewari, R., Dahlin, M., Vin, H.M., Kay, J.S.: Design Considerations for Distributed Caching on the Internet. In: ICDCS, pp 273–284 (1999)
Tsaknakis, H., Spirakis, P.G., Kanoulas, D.: Performance evaluation of a descent algorithm for bi-matrix games. In: Internet and network economics, 4th international workshop, WINE 2008, Shanghai, China, December 17-20, 2008. Proceedings, pp 222–230. https://doi.org/10.1007/978-3-540-92185-1_29 (2008)
Vetta, A.: Nash equilibria in competitive societies, with applications to facility location traffic routing and auctions. In: FOCS (2002)
Wolfson, O., Jajodia, S., Huang, Y.: An Adaptive Data Replication Algorithm. ACM Trans. Database Syst. 22, 255–314 (1997)
Younger, D.H.: Graphs with interlinked directed circuits. In: Proceedings of midwestern symposium on circuit theory, vol. 2, pp. XVI2.1–XVI2.7 (1973)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Gopalakrishnan and Karuturi were partially supported by a generous gift from Northeastern University alumnus Madhav Anand. This work was also partially supported by NSF grants CCF-0635119 and CNS-0915985. A preliminary version of this work appeared in LATIN 2012 [29].
Rights and permissions
About this article
Cite this article
Gopalakrishnan, R., Kanoulas, D., Karuturi, N.N. et al. Cache Me if You Can: Capacitated Selfish Replication Games in Networks. Theory Comput Syst 64, 272–310 (2020). https://doi.org/10.1007/s00224-019-09939-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00224-019-09939-7