Abstract
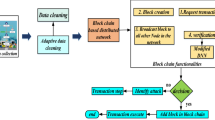
Internet of Things (IoT) is playing a vital role in the smart infrastructure environment. The IoT vendors are delivering their products in the market without any concern about the security of the devices, so it is an open number of security issues on the IoT devices and data. Security threats are growing high because existing techniques measures are inadequate; two of the most significant concerns in IoT are security and privacy. Due to the IoT devices limited CPU, storage, and energy resources, existing security architectures are unable to provide the key safety requirements, so deep learning and blockchain algorithms are used. These IoT devices give accurate results from heavy complex datasets. Furthermore, blockchain and deep learning model are very familiar to give secured devices to IoT. This proposed model is window blockchain (WBC). In proof-of-work, it leverages past (n − 1) hash to construct the next hash with minimal change; because of this quick block analysis time, we can easily prevent IoT devices from the attackers. WBC’s performance is evaluated using an actual data stream generated by one of the analyzed smart infrastructure devices. Another method using deep learning hybrid algorithms for LSTM networks with whale optimization algorithm is a new schema optimization technique that mimics humpback whales’ intelligent bubble-net fishing activity. It is an easy, powerful, and predator probabilistic optimization algorithm that can avoid local optima and find global optimal answer. The findings indicate that the proposed window blockchain model improves security and reduces memory utilization this employing limited resources. In the Whale +LSTM (WLSTM), a large number of the dataset were gathered using a real-time scenario using OMNET++IoT plugins, and a Python API is created to insert various malicious activity through networks. The proposed WLSTM model output of 99% has been tested and related to other deep learning utilizing benchmark datasets such as CIDDC-001, UNSWN15, and KDD datasets, as well as actual datasets; the prediction of unknown threats is used to tackle the computation complexity in big networks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Zhihan Lv, Bin Hu: Infrastructure monitoring and operation for smart cities based on IoT system. IEEE Trans. Indust. Inf. 16(3). https://doi.org/10.1109/TII.2019.2913535 (2020)
Mukherjee, A., Chakraborty, N.: Whale optimization algorithm: an implementation to design low-pass FIR filter. IEEE [IPACT2017]. https://doi.org/10.1109/IPACT.2017.8244929
Dorri, A., Kanhere, S.S.: LSB: a lightweight scalable blockchain for IoT security and anonymity. J. Parallel Distrib. Comp. https://doi.org/10.1016/j.jpdc.2019.08.005.
Khraisat, A., Alazab, A.: A critical review of intrusion detection systems in the internet of things: techniques, deployment strategy, validation strategy, attacks, public datasets and challenges. Cybersecurity. https://doi.org/10.1186/s42400-021-00077-7 (2021)
Vinayakumar, R., Alazab, M.: A visualized botnet detection system based deep learning for the internet of things networks of smart cities. IEEE Trans. Indust. Appl. https://doi.org/10.1109/TIA.2020.2971952 (2020)
Monikaroopak, Tian, G.Y.: An intrusion detection system against DDos attacks in IoT networks. IEEE. https://doi.org/10.1109/CCWC47524.2020.9031206 (2020)
Su, T., Sun, H.: Bat: deep learning methods on network intrusion detection using NSL-KDD dataset. IEEE. https://doi.org/10.1109/ACCESS.2020.2972627 (2020)
Tanzir Mehedi, S.K., Shamim, A.A.M.: Blockchain—Based security management of IoT infrastructure with ethereum transactions. Springer. https://doi.org/10.1007/s42044-019-00044-z (2019)
Liang, W., Huang, W.: Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet Things J. Doi: https://doi.org/10.1109/JIOT.2020.2974281 (2019)
Ly, V., Nguyen, Q.U.: Deep transfer learning for IoT attack detection. doi: https://doi.org/10.1109/ACCESS.2020.3000476 June 18, 2020
Manimurugan, S., Almutairi, S.: Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE. doi: https://doi.org/10.1109/ACCESS.2020.2986013 (2020)
Ning, G.-Y., Cao, D.-Q.: Improved whale optimization algorithm for solving constrained optimization problems. Hindawi vol. https://doi.org/10.1155/2021/8832251 (2021)
Patidar, S., Singh Bains, I.: Web security in IoT networks using deep learning model. IEEE Xplore. doi: https://doi.org/10.1109/ICSSIT48917.2020.9214114 (2020)
Soleimanian Gharehchopogh, F., Gholizadeh, H.: A comprehensive survey: whale optimization algorithm and its applications. https://doi.org/10.1016/j.swevo.2019.03.004 (2019)
Beltagy, I., Peters, M.E.: Longformer: the long-document transformer. https://github.com/allenai/longformer (2020)
Jiang, F., Fu, Y.: Deep learning based multi-channel intelligent attack detection for data security. IEEE Trans. Sustain. Comp. 5(2). doi: https://doi.org/10.1109/TSUSC.2018.2793284 (2020)
Boukhalfa, A., Abdellaoui, A.: LSTM Deep Learning Method for Network Intrusion Detection System, vol. 10, no. 3 (2020)
Otoum, S., Kantarci, B.: On the feasibility of deep learning in sensor network intrusion detection. IEEE Netw. Lett. 1(2). doi: https://doi.org/10.1109/LNET.2019.2901792 (2019)
Reyna, A., Martín, C.: On blockchain and its integration with IoT. Challenges Opportunities. https://doi.org/10.1016/j.future.2018.05.046 (2018)
Waheed, N., He, X.: Security and privacy in IoT using machine learning and blockchain: threats and countermeasures. ACM Comput. Surv. 53(3), (2020)
Riyanto, R.A.: Discretizing whale optimization algorithm to optimize a long short-term memory. IEEE. doi: https://doi.org/10.1109/ICOIACT50329.2020.9331972 (2020)
Sun, X., Jin Gao, X.: The research on application of sliding window LS_SVM in the batch process. doi: https://doi.org/10.1109/ACC.2013.6579852 (2013)
Rana, N., Latiff, M.S.: Whale optimization algorithm: a systematic review of contemporary applications, modifications and developments. https://doi.org/10.1007/s00521-020-04849-z (2020)
Fu, J., Qiao, S.: A study on the optimization of Blockchain Hashing algorithm based on PRCA. https://doi.org/10.1155/2020/8876317 (2020)
Sultan, M.A.M.: IoT Security Issues via Blockchain: A Review Paper. doi: https://doi.org/10.1145/3320154.3320163
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Janani, K., Ramamoorthy, S. (2022). Integrated Smart IoT Infrastructure Management Using Window Blockchain and Whale LSTM Approaches. In: Goar, V., Kuri, M., Kumar, R., Senjyu, T. (eds) Advances in Information Communication Technology and Computing. Lecture Notes in Networks and Systems, vol 392. Springer, Singapore. https://doi.org/10.1007/978-981-19-0619-0_10
Download citation
DOI: https://doi.org/10.1007/978-981-19-0619-0_10
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-0618-3
Online ISBN: 978-981-19-0619-0
eBook Packages: EngineeringEngineering (R0)