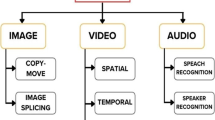
Abstract
The popularity of internet usage has resulted in the exponential growth of data in one form or the other. The exhaustive use of massive amount of artistic and communicative multimedia for several purposes has resulted in a need to develop tools and techniques to handle such multimedia in a secure and privacy-preserved manner. The legitimacy, ownership and authentication of such datasets are important as it can have a significant effect on the lives of human beings and organizations as a whole. With the advancement of technology, there exists an ocean of freely available software that can be used to create fake and tampered data without being detected by the normal visual perceptions resulting in dangerous consequences. Today, issues like copyright, ownership and legitimacy are imperative when we deal with multimedia data. This has made multimedia tampering detection an important area for research. Many techniques are being developed to identify different types of tampering in multimedia. This paper aims to present the state-of-the-art about multimedia tampering detection tools and techniques. Furthermore, it provides a comprehensive survey of the current researches in the area of multimedia tampering detection and related technologies.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
T. Liu, Z.D. Qiu, The survey of digital watermarking-based image authentication techniques, in 2002 6th International Conference on Signal Processing, vol. 2 (IEEE, 2002), pp. 1556–1559)
P. Yin, H.H. Yu, Classification of video tampering methods and countermeasures using digital watermarking, in Multimedia Systems and Applications IV, vol. 4518 (International Society for Optics and Photonics, 2001), pp. 239–247)
H.H. Yu, D. Kundur, C.-Y. Lin, Spies, Thieves, and Lies: The Battle for Multimedia in the Digital Era, Visions and Views Editor: Nevenka Dimitrova Phillips Research, 1070-986X/01/$10.00 © 2001 IEEE
MMGD0101, Introduction To Multimedia Chap. 2 Multimedia Systems, http://www.ftms.edu.my/images/Document/MMGD0101%20-%20Introduction%20to%20Multimedia/MMGD0101%20chapter%202.pdf
Digital Image Characteristics, http://www.sprawls.org/resources/DICHAR/index.htm
Significant Characteristics of Audio Files https://wiki.archivematica.org/Significant_characteristics_of_audio_files
G. Voyatzis, I. Pitas, The use of watermarks in the protection of digital multimedia products. Proc. IEEE 87(7), 1197–1207 (1999)
V. Amanipour, S. Ghaemmaghami, Video-Tampering Detection and Content Reconstruction via Self-Embedding. IEEE Trans. Instrum. Meas. 67(3), 505–515 (2018)
T. Mahmood, Z. Mehmood, M. Shah, T. Saba, A robust technique for copy-move forgery detection and localization in digital images via stationary wavelet and discrete cosine transform. J. Vis. Commun. Image Represent. 53, 202–214 (2018)
M. Fatema, V. Maheshkar, S. Maheshkar, G. Agarwal, Tamper detection using fragile image watermarking based on chaotic system. in International Conference on Wireless Intelligent and Distributed Environment for Communication (Springer, Cham, 2018), pp. 1–11
M. Zakariah, M.K. Khan, H. Malik, Digital multimedia audio forensics: past, present and future. Multimed. Tools Appl. 77(1), 1009–1040 (2018)
V. Thirunavukkarasu, J.S. Kumar, G.S. Chae, J. Kishorkumar, Non-intrusive forensic detection method using DSWT with reduced feature set for copy-move image tampering. Wirel. Pers. Commun. 98(4), 3039–3057 (2018)
H. Chen, Y. Wo, G. Han, Multi-granularity geometrically robust video hashing for tampering detection. Multimed. Tools Appl. 77(5), 5303–5321 (2018)
B. Bayar, M.C. Stamm, Constrained convolutional neural networks: a new approach towards general purpose image manipulation detection. IEEE Trans. Inform. Forensics Secur. (2018)
A.M. Sundaram, C. Nandini, ASRD: algorithm for spliced region detection in digital image forensics, in Computer Science On-line Conference (Springer, Cham, 2017), pp. 87–95
P.M.G.I. Reis, J.P.C.L. da Costa, R.K. Miranda, G. Del Galdo, ESPRIT-hilbert-based audio tampering detection With SVM classifier for forensic analysis via electrical network frequency. IEEE Trans. Inform. Forensics Secur. 12(4), 853–864 (2017)
A. Alahmadi, M. Hussain, H. Aboalsamh, G. Muhammad, G. Bebis, H. Mathkour, Passive detection of image forgery using DCT and local binary pattern. Signal, Image Video Process. 11(1), 81–88 (2017)
B.B. Haghighi, A.H. Taherinia, A. Harati, TRLH: fragile and blind dual watermarking for image tamper detection and self-recovery based on lifting wavelet transform and halftoning technique. J. Vis. Commun. Image Represent. (2017)
Y.C. Hu, K.K.R. Choo, W.L. Chen, Tamper detection and image recovery for BTC-compressed images. Multimed. Tools Appl. 76(14), 15435–15463 (2017)
A. Baumy, M. Abdalla, N.F. Soiliman, F.E.A. El-Samie, Efficient implementation of pre-processing techniquesfor image forgery detection, in Japan-Africa Conference on Electronics, Communications and Computers (JAC-ECC) (IEEE, 2017), pp 53–56
F. Arab, S.M. Abdullah, S.Z.M. Hashim, A.A. Manaf, M. Zamani, A robust video watermarking technique for the tamper detection of surveillance systems. Multimed. Tools Appl. 75(18), 10855–10885 (2016)
C.P. Yan, C.M. Pun, X.C. Yuan, Multi-scale image hashing using adaptive local feature extraction for robust tampering detection. Signal Process. 121, 1–16 (2016)
K. Sitara, B.M. Mehtre, Digital video tampering detection: an overview of passive techniques. Digit. Investig. 18, 8–22 (2016)
W.C. Hu, W.H. Chen, D.Y. Huang, C.Y. Yang, Effective image forgery detection of tampered foreground or background image based on image watermarking and alpha mattes. Multimed. Tools Appl. 75(6), 3495–3516 (2016)
http://papers.nips.cc/paper/6672-unsupervised-image-to-image-translation-networks.pdf
A.S. Jackson, A. Bulat, V. Argyriou, G. Tzimiropoulos, Large pose 3D face reconstruction from a single image via direct volumetric CNN regression, in Proceedings of the IEEE International Conference on Computer Vision (2017), pp. 1031–1039
https://29a.ch/2015/08/16/forensically-photo-forensics-for-the-web
M. Barni, M.C. Stamm, B. Tondi, Adversarial multimedia forensics: overview and challenges ahead, in 2018 26th European Signal Processing Conference (EUSIPCO) (Rome, 2018), pp. 962–966
K.N. Sowmya, H.R. Chennamma, A survey on video forgery detection. Int. J. Comput. Eng. Appl. 9(2), 17–27 (2015)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Tripathi, G., Abdul Ahad, M., Ali Haq, Z. (2020). Multimedia Tampering Detection: A Comprehensive Review of Available Techniques and Solutions. In: Jain, L., Virvou, M., Piuri, V., Balas, V. (eds) Advances in Bioinformatics, Multimedia, and Electronics Circuits and Signals. Advances in Intelligent Systems and Computing, vol 1064. Springer, Singapore. https://doi.org/10.1007/978-981-15-0339-9_18
Download citation
DOI: https://doi.org/10.1007/978-981-15-0339-9_18
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-0338-2
Online ISBN: 978-981-15-0339-9
eBook Packages: EngineeringEngineering (R0)