Abstract
We present a generic construction of an insider secure signcryption scheme with non-interactive non-repudiation. Our construction uses as building blocks a signature scheme, a key encapsulation mechanism (KEM), a keyed hash function, a symmetric encryption scheme, and a pseudo-random function. We show that our construction is insider secure in the dynamic multi-user model, without resorting the random oracle or the key registration model. Our generic scheme provides also non-interactive non-repudiation.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
References
An, J.H., Rabin, T.: Security for signcryption: the two-user model. In: Dent, A., Zheng, Y. (eds.) Practical Signcryption, pp. 21–42. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-540-89411-7_2
Arriaga, A., Barbosa, M., Farshim, P.: On the joint security of signature and encryption schemes under randomness reuse: efficiency and security amplification. In: Bao, F., Samarati, P., Zhou, J. (eds.) ACNS 2012. LNCS, vol. 7341, pp. 206–223. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-31284-7_13
Badertscher, C., Banfi, F., Maurer, U.: A constructive perspective on signcryption security. In: Catalano, D., De Prisco, R. (eds.) SCN 2018. LNCS, vol. 11035, pp. 102–120. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-98113-0_6
Baek, J., Steinfeld, R.: Security for signcryption: the multi-user model. In: Dent, A., Zheng, Y. (eds.) Practical Signcryption, pp. 43–53. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-540-89411-7_3
Baek, J., Steinfeld, R., Zheng, Y.: Formal proofs for the security of signcryption. J. Cryptol. 20(2), 203–235 (2007)
Barnes, R., Bhargavan, K., Lipp, B., Wood, C.: RFC 9180: Hybrid public key encryption (2022)
Bao, F., Deng, R.H.: A signcryption scheme with signature directly verifiable by public key. In: Imai, H., Zheng, Y. (eds.) PKC 1998. LNCS, vol. 1431, pp. 55–59. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054014
Bjørstad, T.E., Dent, A.W.: Building better signcryption schemes with tag-KEMs. In: Yung, M., Dodis, Y., Kiayias, A., Malkin, T. (eds.) PKC 2006. LNCS, vol. 3958, pp. 491–507. Springer, Heidelberg (2006). https://doi.org/10.1007/11745853_32
Boneh, D., Shoup, V.: A graduate course in applied cryptography. Draft 0.6 (2023). https://toc.cryptobook.us/
Chiba, D., Matsuda, T., Schuldt, J.C.N., Matsuura, K.: Efficient generic constructions of signcryption with insider security in the multi-user setting. In: Lopez, J., Tsudik, G. (eds.) ACNS 2011. LNCS, vol. 6715, pp. 220–237. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-21554-4_13
Ducklin, P.: Serious security: google finds fake but trusted SSL certificates for its domains, made in France. Naked Security-Award-Winning Computer Security, News, Opinion, Advice and Research from SOPHOS, pp. 09–12 (2013)
Fan, J., Zheng, Y., Tang, X.: Signcryption with non-interactive non-repudiation without random oracles. In: Gavrilova, M.L., Tan, C.J.K., Moreno, E.D. (eds.) Transactions on Computational Science X. LNCS, vol. 6340, pp. 202–230. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-17499-5_9
Fisher, D.: Final Report on DigiNotar Hack Shows Total Compromise of CA Servers. Threatpost, 10/31/12. https://threatpost.com/final-report-diginotar-hack-shows-total-compromise-ca-servers-103112/77170/
Kakvi, S.A., Kiltz, E.: Optimal security proofs for full domain hash, revisited. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 537–553. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_32
Kelsey, J., Chang, S.J., Perlner, R.: SHA-3 derived functions: cSHAKE, KMAC, TupleHash, and ParallelHash. NIST Special Publication, vol. 800, p. 185 (2016)
Krawczyk, H., Bellare, M., Canetti, R.: RFC2104: HMAC: Keyed-hashing for message authentication (1997)
Krovetz, T. (Ed.): RFC 4418: UMAC: Message Authentication Code using Universal Hashing (2006)
Malone-Lee, J.: Signcryption with non-interactive non-repudiation. Des. Codes Cryptogr. 37(1), 81–109 (2005)
Matsuda, T., Matsuura, K., Schuldt, J.C.N.: Efficient constructions of signcryption schemes and signcryption composability. In: Roy, B., Sendrier, N. (eds.) INDOCRYPT 2009. LNCS, vol. 5922, pp. 321–342. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-10628-6_22
Ngarenon, T., Sarr, A.P.: A Computational Diffie-Hellman based Insider Secure Signcryption with Non Interactive Non Repudiation (full version) (2022). https://hal.science/hal-03628351/document
Ngarenon, T., Sarr, A.P.: A computational Diffie-Hellman based insider secure signcryption with non-interactive non-repudiation. In: Rushi Kumar, B., Ponnusamy, S., Giri, D., Thuraisingham, B., Clifton, C.W., Carminati, B. (eds.) ICMC 2022. Springer Proceedings in Mathematics & Statistics, vol. 415. Springer, Cham (2023). https://doi.org/10.1007/978-981-19-9307-7_8
Sarr, A.P., Seye, P.B., Ngarenon, T.: A practical and insider secure signcryption with non-interactive non-repudiation. In: Carlet, C., Guilley, S., Nitaj, A., Souidi, E.M. (eds.) C2SI 2019. LNCS, vol. 11445, pp. 409–429. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-16458-4_24
Tan, C.H.: Signcryption scheme in multi-user setting without random oracles. In: Matsuura, K., Fujisaki, E. (eds.) IWSEC 2008. LNCS, vol. 5312, pp. 64–82. Springer, Heidelberg (2008). https://doi.org/10.1007/978-3-540-89598-5_5
Zheng, Y.: Digital signcryption or how to achieve cost(signature & encryption) \(\ll \) cost(signature) + cost(encryption). In: Kaliski, B.S. (ed.) CRYPTO 1997. LNCS, vol. 1294, pp. 165–179. Springer, Heidelberg (1997). https://doi.org/10.1007/BFb0052234
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Proof of Lemma 1
A Proof of Lemma 1
Let \(\mathcal {A}\) be an adversary playing Game 1. We build an adversary \(\mathcal {B}\) against the collision (with identical prefix) resistance of \(\textsf{H}\) a follows.
-
1)
\(\mathcal {B}\) receives
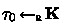 from its challenger and sends \(\tau _0\) to \(\mathcal {A}\).
from its challenger and sends \(\tau _0\) to \(\mathcal {A}\). -
2)
When \(\mathcal {B}\) receives \((p_0, m_0, s_0)\) from \(\mathcal {A}\), it chooses
 and computes \(\tau ''_0\leftarrow \textsf{Prf}(\tau ', m_0)\), \(\hat{m}_0\leftarrow \textsf{H}(\tau _0, (p_0, \tau , \tau ', \tau '', s_0))\) and sends \(\hat{m}_0\) to \(\mathcal {A}\).
and computes \(\tau ''_0\leftarrow \textsf{Prf}(\tau ', m_0)\), \(\hat{m}_0\leftarrow \textsf{H}(\tau _0, (p_0, \tau , \tau ', \tau '', s_0))\) and sends \(\hat{m}_0\) to \(\mathcal {A}\). -
3)
When \(\mathcal {A}\) outputs \((\tau ^*, \tau '^*)\) such that \(\hat{m}_0=\hat{m}^*_0\leftarrow \textsf{H}(\tau _0, (p_0, \tau ^*, \tau '^*, \tau ''^*, s_0))\) wherein \(\tau ''^*\leftarrow \textsf{Prf}(\tau '^*, m_0)\), if \((\tau , \tau ')\ne (\tau ^*, \tau '^*)\) then \(\mathcal {B}\) outputs \((s, s')\) wherein \(s=(p_0, \tau , \tau ', \tau '', s_0)\) and \(s'=(p_0, \tau ^*, \tau '^*, \tau ''^*, s_0)\) as messages with identical prefix \(p_0\) and colliding hashes under \(\tau _0\).
Let \(\textsf{bad}\) be the event: the chosen pair \((\tau , \tau ')\) is such that for all \((\bar{\tau }, \bar{\tau }')\ne (\tau , \tau ')\), \(\hat{m}_0\ne \textsf{H}(\tau _0, (p_0, \bar{\tau }, \bar{\tau }', \bar{\tau }'', s_0))\), i. e. there is no other pair \((\bar{\tau }, \bar{\tau }')\in \textbf{K}^2\) such that \(\textsf{H}(\tau _0, (p_0, \bar{\tau }, \bar{\tau }', \bar{\tau }'', s_0)) =\textsf{H}(\tau _0, (p_0, \tau , \tau ', \tau '', s_0))\). It holds that
If \(\textsf{Succ}_{\mathcal {A}, \textsf{H}}\) denotes the event \(\mathcal {A}\) succeeds in Game 1,
Now let \(\textsf{Eq}\) be the event \((\tau , \tau ')=(\tau ^*, \tau '^*)\).
Now, as if \(\textsf{Succ}_{\mathcal {A}, \textsf{H}}\wedge \lnot \textsf{bad}\) occurs, there at least one \((\tau ^*, \tau '^*)\ne (\tau , \tau ')\) such that \(\hat{m}_0=\hat{m}^*_0\leftarrow \textsf{H}(\tau _0, (p_0, \tau ^*, \tau '^*, \tau ''^*, s_0))\), and \(\mathcal {A}\) has no information about \((\tau , \tau ')\) besides \(\hat{m}_0\), it holds that
Hence
And, whenever \(\textsf{Succ}_{\mathcal {A}, \textsf{H}}\wedge \lnot \textsf{bad}\wedge \lnot \textsf{Eq}\) occurs \(\mathcal {B}\) outputs \(s, s'\) with identical prefix such that \(\textsf{H}(\tau _0,s)=\textsf{H}(\tau _0, s')\). \(\square \)
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Togde, N., Sarr, A.P. (2024). An Efficient Generic Insider Secure Signcryption with Non-Interactive Non-Repudiation. In: Regazzoni, F., Mazumdar, B., Parameswaran, S. (eds) Security, Privacy, and Applied Cryptography Engineering. SPACE 2023. Lecture Notes in Computer Science, vol 14412. Springer, Cham. https://doi.org/10.1007/978-3-031-51583-5_8
Download citation
DOI: https://doi.org/10.1007/978-3-031-51583-5_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-51582-8
Online ISBN: 978-3-031-51583-5
eBook Packages: Computer ScienceComputer Science (R0)


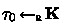 from its challenger and sends
from its challenger and sends  and computes
and computes