Abstract
Nowadays, the Internet of things (IoT), which connect to larger, internet-connected devices, is exponentially increased, and is used across the globe [1]. Integration of such a device into networks to provide advanced and intelligent services has to Protect user privacy against cyber-attacks. Attackers exploit vulnerable end sensors and devices supporting IoT data transmission to gain unauthorized system privileges and access to information and connected resources.
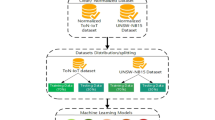
This paper investigates how malware attack, especially ransomware attack, exploits IoT devices. Moreover, we deeply review different Machine learning solutions that provide IoT security precisely on a ransomware attack. We focused on How Machine learning solutions detect malicious incidents, such as a ransomware attack on IoT-connected networks. The authors perform all the experiments in this study using a benchmark dataset from the GitHub repository. We used Random Forest (RF) and Decision Tree (DT) Classifier algorithm to evaluate the performance comparison. Finally, we propose a machine learning detection model with better performance and accuracy.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Segal, B.: Introduction to IoT Devices and Products, 19 Apr 2021. https://telnyx.com/resources/iot-devices. Accessed 21 Nov 2021
Gartner 2022. https://www.gartner.com/en/information-technology/glossary/internet-of-things. Accessed 22 Jan 2022
McClelland, C.: Leverege, 16 Oct 2016. https://www.leverege.com/blogpost/iot-explained-how-does-an-iot-system-actually-work. Accessed 02 Feb 2022
Sestino, A., Prete, M.I., Piper, L., Guidob, G.: Internet of things and big data as enablers for business digitalization strategies, Technovation, vol. 98, no. Elsevier Public Health Emergency Collection (2020)
Jovanovic, B.: Internet of things statistics for 2022 - taking things apart 2022. https://dataprot.net/statistics/iot-statistics/#
World economic forum, 2022. [Online]. Available: https://www.weforum.org/agenda/2022/05/how-digital-solutions-can-reduce-global-emissions/. [Accessed 11 02 2022]
McKinsey & Company, Artificial intelligence the next digital frontier? (2017). https://www.mckinsey.com/~/media/mckinsey/industries/advanced%20electronics/. Accessed 15 Feb 2022
Irshad, M.: A systematic review of information security frameworks on the internet of things (IoT). In: 18th International Conference on High Performance Computing and Communications, Sydney (2016)
Donostia, G.: The effects of consumers’ information security behavior and information privacy concerns on usage of IoT technology. In: Proceedings of the XX International Conference on Human Computer Interaction, 2019, Spain (2019)
Software AG, Machine learning (ML) for IoT, (2022). https://www.softwareag.com/en_corporate/resources/what-is/machine-learning.html. Accessed 02 Feb 2022
Dinga, L., Wang, Z., Wang, X., DongWud.: Security information transmission algorithms for IoT based on cloud computing. Comput. Commun. 155, 32–39 (2020)
Thuraisingham, B.: The role of artificial intelligence and cyber security for social media. In: 2020 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), New Orleans, LA, USA (2020)
Géron, A.: (2019). https://www.oreilly.com/library/view/hands-on-machine-learning/9781492032632/. Accessed 22 Jan 2022
ReportLinker, Global mobile data traffic market to reach 220.8 million terabytes per month by the year 2026, 14 Jan 2022. https://www.globenewswire.com/news-release/2022/01/14/2367194/0/en/Global-Mobile-Data-Traffic-Market-to-Reach-220-8-Million-Terabytes-per-Month-by-the-Year-2026.html. Accessed 05 Feb 2022
Sjouwerman, S.: KnowBe4 2021. https://blog.knowbe4.com/ransomware-attack-volume-increases-by-18-percent. Accessed 22 Jan 2022
Azmoodeh, A., et al.: Detecting crypto-ransomware in IoT networks based on energy consumption footprint. J. Ambient Intell. Humanized Comput. 9, 1141–1152 (2018)
I Yaqoob 2017 The rise of ransomware and emerging security challenges in the internet of things Comput. Netw. 129 2 444 458
Zahra, A., Shah, M.A.: IoT based ransomware growth rate evaluation and detection using command and control blacklisting. In: Huddersfield, UK, Huddersfield, UK (2017)
Wani, A., Sathiya, R.: Ransomware protection in IoT using software defined networking. Int. J. Electr. Comput. Eng. 10(3), 3166–3175 (2020)
Su, J., Vasconcellos, D.V., Prasad, S., Sgandurra, D., Feng, Y., Sakurai, K.: Lightweight classification of IoT malware based on image recognition. In: IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan (2018)
Gantenbein, K.: ExtraHop, 13 Nov 2020. https://www.extrahop.com/company/blog/2020/ransomware-explanation-and-prevention/. Accessed 02 Feb 2022
Beaman, C., Barkworth, A., Akande, T.D., Hakak, S., Khan, M.K.: Ransomware: recent advances, analysis, challenges and future research directions Comput. Secur. 111 102490 (2021)
Wang, B., Dou, Y., Sang, Y., Zhang, Y., Huang, J.: Towards a hybrid IoT honeypot for capturing and analyzing malware. In: ICC 2020 - 2020 IEEE International Conference on Communications (ICC), Dublin, Ireland (2020)
Cohesity, The Essential Guide to Modern Data Management, Cohesity, Inc, San Jose (2021)
Radečić, D.: Google Colab: How does it compare to a GPU-enabled laptop? 30 Apr 2020. https://towardsdatascience.com/google-colab-how-does-it-compare-to-a-gpu-enabled-laptop-851c1e0a2ca9. Accessed 25 Jan 2022
Kimmell, J.C., Abdelsalam, M., Gupta, M.: Analyzing machine learning approaches for online malware detection in cloud. In: 2021 IEEE International Conference on Smart Computing (SMARTCOMP), Irvine, CA, USA (2021)
MindTools, Decision Trees (2022). https://www.mindtools.com/dectree.html. Accessed 01 Jan 2022
Szczerbicki, E.: Decision tree classifier, ScienceDirect (2008). https://www.sciencedirect.com/topics/computer-science/decision-tree-classifier. Accessed 22 Apr 2022
Brownlee, J.: https://machinelearningmastery.com/confusion-matrix-machine-learning/#:~:text=Contact-,What%20is%20a%20Confusion%20Matrix%20in%20Machine%20Learning,-by%20Jason%20Brownlee. 15 Aug 2020. https://machinelearningmastery.com/confusion-matrix-machine-learning/. Accessed 26 Jan 2022
Géron, A.: Hands-on machine learning with Scikit-Learn, Keras & TensorFlow. In: Concepts, Tools, and Techniques to Build Intelligent Systems, O’Reilly Media, Inc., p. 92 (2019)
Dhingra, M., Jain, M., Jadon, R.S.: Role of artificial intelligence in enterprise information security: a review. In: 2016 Fourth International Conference on Parallel, Distributed and Grid Computing (PDGC) (2016)
Dhamija, P.: Role of artificial intelligence in operations environment: a review and bibliometric analysis. TQM J. (2020)
Acknowledgment
ARLIS (Applied Research Lab for Intelligence and Security) Grant supports this research work.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 Springer Nature Switzerland AG
About this paper
Cite this paper
Zewdie, T.G., Girma, A., Cotae, P. (2022). Ransomware Attack Detection on the Internet of Things Using Machine Learning Algorithm. In: Chen, J.Y.C., Fragomeni, G., Degen, H., Ntoa, S. (eds) HCI International 2022 – Late Breaking Papers: Interacting with eXtended Reality and Artificial Intelligence. HCII 2022. Lecture Notes in Computer Science, vol 13518. Springer, Cham. https://doi.org/10.1007/978-3-031-21707-4_43
Download citation
DOI: https://doi.org/10.1007/978-3-031-21707-4_43
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-21706-7
Online ISBN: 978-3-031-21707-4
eBook Packages: Computer ScienceComputer Science (R0)