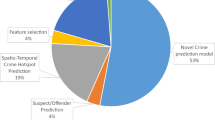
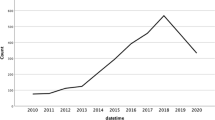
Abstract
The computational analysis of the societal dimension of crime has aroused an increasing interest in recent years. Data mining, social network analysis (SNA), and visualization techniques are offering promising opportunities to the scientific and investigative study of criminal organizations. In spite of that, the spread of technological innovation faces serious difficulties due to the concurrence of different factors: the absence of user friendly crime analysis tools, the lack of technical skills of investigators (public prosecutors, police officers), two factors that, when combined with the pressure of daily routine, often result into a resistance to change. In this work we present an ongoing research project aiming to foster the potentialities of SNA and computation into criminal investigation. We define an holistic methodology that combines document-enhancement, social network analysis, and visualization techniques to support public prosecutors and criminal investigation departments in exploring the societal dimension of criminal groups. This approach has been deployed in a computational framework, CrimeMiner, validated with a case study based on data coming from real criminal investigations.











Similar content being viewed by others
Notes
Italian Supreme Court of Cassation, 1st Criminal Division, Judgement n.13967/2016 of 05 May 2015, available online at http://www.italgiure.giustizia.it/sncass/
References
Blondel VD, Guillaume JL, Lambiotte R, Lefebvre E (2008) Fast unfolding of communities in large networks. J Stat Mech: Theory Exp 2008(10):P10,008
Byrne J, Marx G (2011) Technological innovations in crime prevention and policing. a review of the research on implementation and impact. J Police Stud 20 (3):17–40
Chan JB (2001) The technological game: How information technology is transforming police practice. Criminol Crim Just 1(2):139–159
De Pauw E, Ponsaers P, Bruggeman W, Deelman P, Van Der Vijver K (2011) Technology-led policing, Journal of Police Studies, vol. 20 Maklu
Dècary-Hètu D (2012) Dupont: The Social Network of Hackers. Glob Crime 13(3):160–175
Didimo W, Liotta G, Montecchiani F (2014) Network visualization for financial crime detection. J Vis Lang Comput 25(4):433–451
Easley D, Kleinberg J (2010) Networks, crowds, and markets: Reasoning about a highly connected world. Cambridge University Press, Cambridge
Ferrara E, Meo PD, Catanese S, Fiumara G (2014) Detecting criminal organizations in mobile phone networks. Expert Syst Appl 41(13):5733–5750
Freeman LC (1979) Centrality in social networks conceptual clarification. Soc Networks 1(3):215–239
Haynie DL (2001) Delinquent peers revisited: Does network structure matter? 1. Am J Sociol 106(4):1013–1057
Hutchins CE, Benham-Hutchins M (2010) Hiding in Plain Sight: Criminal Network Analysis. Comput Math Organ Theory 16(1):89–111
Johnson JA (2010) To catch a curious clicker a social network analysis of the online pornography industry, in Everyday Pornography Routledge
Keim DA, Mansmann F, Schneidewind J, Thomas J, Ziegler H (2008) Visual analytics: Scope and challenges Springer
Keim ED, Kohlhammer J, Ellis G (2010) Mastering the information age: Solving problems with visual analytics eurographics association
Kohlhammer J, Keim D, Pohl M, Santucci G, Andrienko G (2011) Solving Problems with Visual Analytics. Procedia Comput Sci 7:117–120. Proceedings of the 2nd European Future Technologies Conference and Exhibition 2011 (FET 11)
Krebs V (2002) Mapping Networks of Terrorist Cells. Connections 24(3):43–52
von Lampe K (2006) The interdisciplinary dimensions of the study of organized crime. Trends in Organized Crime 9(3):77–95
Lettieri N, Malandrino D, Spinelli R (2013) Text and Social Network Analysis As Investigative Tools: A Case Study. In: Nicola L., Sebastiano F. (eds) Law and Computational Social Science. ESI
Lettieri N, Malandrino D, Vicidomini L (2014) Document-enhancement and network analysis for criminal investigation: an holistic approach. In: Nicola L., Winkels R. (eds) Law and Computational Social Science. ESI. http://www.leibnizcenter.org/~winkels/NAiL2014-pre-proceedings.pdf
Lu Y, Luo X, Polgar M, Cao Y (2010) Social network analysis of a criminal hacker community. J Comput Inf Syst 51(2):31
Memon N, Larsen HL (2006) Practical algorithms for destabilizing terrorist networks. In: Proceedings of the 4th IEEE International Conference on Intelligence and Security Informatics, ISI’06. Springer, Berlin, pp 389–400
Morselli C (2009) Inside Criminal Networks Studies of Organized Crime
Patacchini E, Zenou Y (2008) The strength of weak ties in crime. Eur Econ Rev 52(2):209–236. doi:10.1016/j.euroecorev.2007.09.002, http://www.sciencedirect.com/science/article/pii/S0014292107001274
Reichert K (2001) Use of information technology by law enforcement Promising Approaches to Addressing Crime Series
Richard R (2002) From Whole Cloth: Making up the terrorist network. Connections 24(3):36–42
Schroeder J, Xu J, Chen H (2003) Crimelink explorer: Using domain knowledge to facilitate automated crime association analysis. In: Intelligence and Security Informatics. Springer, pp 168– 180
Sykes G (1992) Stability amid change. In: Police Management: Issues and Perspectives. Washington: Police Executive Research Forum
Thomas S (2001) Six degrees of mohamed atta
Wong PC, Thomas J (2004) Visual analytics. IEEE Comput Graph Appl 24(5):20–21. doi:10.1109/MCG.2004.39
Xu J, Chen H (2005) Criminal Network Analysis and Visualization. Commun. ACM 48(6):100–107
Xu JJ, Chen H (2005) Crimenet explorer: A framework for criminal network knowledge discovery. ACM Trans Inf Syst 23(2):201–226
Zhang J (2008) Visualization for Information Retrieval (The Information Retrieval Series), 1 edn
Ziegler H, Nietzschmann T, Keim DA (2008) Visual analytics on the financial market: Pixel-based analysis and comparison of long-term investments. In: Information Visualisation, 2008. IV’08. 12th International Conference, pp 287–295
Acknowledgments
We would like to thank for their useful contribution, suggestions and comments: Dr. Attilio Scaglione from the University of Palermo and Dr. Luigi Landolfi, deputy prosecutor of the Antimafia District Department of Naples. We would also thank Claudia Coscia, Francesco Orciuoli, and Raffaele Costantino for their support in the analysis phase.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
Authors declare that they have no conflict of interest. This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
The autorship of the work here presented can be attributed as follows: Nicola Lettieri: concept and functional design of CrimeMiner; legal, Computational social science and Legal informatics profiles of the research. Delfina Malandrino and Luca Vicidomini: system design, computer science profiles. The case study is the result of a joint effort of the authors.
Rights and permissions
About this article
Cite this article
Lettieri, N., Malandrino, D. & Vicidomini, L. By investigation, I mean computation. Trends Organ Crim 20, 31–54 (2017). https://doi.org/10.1007/s12117-016-9284-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12117-016-9284-1