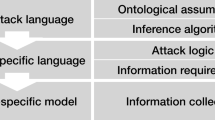
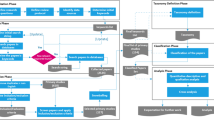
Abstract
In the development process of a secure system is essential to detect as early as possible the system’s vulnerable points, the so called attack surfaces, and to estimate how feasible it would be that known attacks breach through them. Even if attack surfaces can be sometimes detected automatically, mapping them against known attacks still is a step apart. Systems and attacks are not usually modelled in compatible formalisms. We develop a practical framework that automates the whole process. We formalize a system as SysML activity diagrams and in the same formalism we model libraries of patterns taken from standard catalogues of social engineering and technical attacks. An algorithm that we define, navigates the system’s diagrams in search for its attack surfaces; then it evaluates the possibility and the probability that the detected weak points host attacks among those in the modelled library. We prove the correctness and the completeness of our approach and we show how it works on a use case scenario. It represents a very common situation in the domain of communication and data security for corporations.






Similar content being viewed by others
References
Abrams MD (1998) Nims information security threat methodology. In: Mitre Technical Report MTR 98 W000009, MITRE, Center for Advanced Aviation System Development. McLean, Virgini
Bella G, Giustolisi R, Lenzini G (2013) A socio-technical understanding of TLS cerficate validation. In: Proceedings of 7th IFIP international conference on trust management (IFIPTM2013). Malaga. IFIP
Checkoway S, McCoy D, Kantor B, Anderson D, Shacham H, Savage S, Koscher K, Czeskis A, Roesner F, Kohno T (2011) Comprehensive experimental analyses of automotive attack surfaces. In: Proceedings of the 20th USENIX Conference on Security (SEC 11). USENIX Association, pp 6–6
Clarke EM, Emerson EA, Sistla AP (1983) Automated verification of finite state concurrent systems using temporal logic specifications: a practical approach. In: Proceedings of POPL, pp 117–126
Clarke EM, Klieber W, Novacek M, Zuliani P (2012) Model checking and the state explosion problem. In: Meyer B, Nordio M (eds) Tools for practical software verification. Lecture notes in computer science. Springer, Berlin
Dolev D, Yao AC (1983) On the security of public key protocols. IEEE Trans Inf Theory 29(2):198–208 (ISSN 0018–9448)
Francesco C, Ciaramella A, Staiano A (2013) Machine learning and soft computing for ict security: an overview of current trends. J Ambient Intell Humaniz Comput 4(2):235–247 (ISSN 1868–5137)
Frigault M, Wang L (2009) Measuring network security using Bayesian network-based attack graphs. In: Proceedings of the 32nd IEEE international computer software and applications conference (COMPSAC ’08), pp 698–703
Gegick M, Williams L (2007) On the design of more secure software-intensive systems by use of attack patterns. Inf Softw Technol 49:381–397
Grunske L, Joyce D (2008) Quantitative risk-based "security prediction for component-based systems with explicitly modeled attack profiles. J Syst Softw 81:1327–1345
Holt J, Perry S (2008) SysML for systems engineering. Professional Applications of Computing Series 7, Institution of Engineering and Technology, London, UK
Houmb SH, Islam S, Knauss E, Jürjens J, Schneider K (2010) Eliciting security requirements and tracing them to design: an integration of common criteria, heuristics, and UMLsec. Requir Eng 15:63–93 (ISSN 0947–3602)
Huang H, Zhang S, Ou X, Prakash A, Sakallah KA (2011) Distilling critical attack graph surface iteratively through minimum-cost sat solving. In: ACSAC’11, pp 31–40
Information technology, Security techniques, Information security risk management ISO (2008) International organization for standardization
Jürjens J, Shabalin P (2004) Automated verification of UMLsec models for security requirements. In: UML 2004. The unified modeling language, LNCS vol 2460. Springer, Berlin, pp 412–425
Kantola D, Chin E, He W, Wagner D (2012) Reducing attack surfaces for intra-application communication in android. In: Proceedings of the 2nd ACM Work. On security and privacy in smartphones and mobile devices (SPSM 12), ACM, pp 69–80
Kent Sherman and Collected Essays the Board of National Estimates (2008) Kent‘s Words of Estimative Probability. https://www.cia.gov/library
Manadhata PK, Wing JM (2011) An attack aurface metric. IEEE Trans Soft Eng 37(3):371–386 (ISSN 0098–5589)
Mauw S, Oostdijk M (2005) Foundations of attack trees. In: International conference on information security and cryptology ICISC 2005. LNCS, vol 3935. Springer, Berlin, pp 186–198
Morais A, Hwang I, Cavalli A, Martins E (2013) Generating attack scenarios for the system security validation. Netw Sci 2(3–4):69–80 (ISSN 2076–0310)
OMG (2007a) OMG systems modeling language (OMG SysML) specification. Object management group
OMG (2007b) OMG unified modeling language: superstructure 2.1.2. Object management group
Ouchani S (2014) Lenzini G (2014) Attacks generation by detecting attack surfaces. Procedia Comput Sci 32:529–536 [ISSN 1877–0509. The 5th international conference on ambient aystems, networks and technologies (ANT-2014)]
Sawilla R, Defence R&D Canada Ottawa (2007). Googling attack graphs. Technical memorandum. Defence R&D Canada-Ottawa
Sheyner OM (2004) Scenario graphs and attack graphs. PhD thesis, School of Computer Science. Pittsburgh, pp AAI3126929
Siveroni Igor, Zisman Andrea, Spanoudakis George (2010) A UML-based static verification framework for security. Requir Eng 15:95–118
Solhaug B, Seehusen F (2014) Model-driven risk analysis of evolving critical infrastructures. J Ambient Intell Humaniz Comput 5(2):187–204 (ISSN 1868–5137)
Symantec Corporation (2014) Internet security threat report-2014
Vijayakumar H, Jakka G, Rueda S, Schiffman J, Jaeger T (2012) Integrity walls: finding attack surfaces from mandatory access control policies. In: Proceedings of the 7th ACM symposium on information, computer and communications security (ASIACCS 12). ACM, pp 75–76
Acknowledgments
The research leading to the results presented in this work received funding from the Fonds National de la Recherche Luxembourg, project “Socio-Technical Analysis of Security and Trust”, C11/IS/1183245, STAST, and the European Commissions Seventh Framework Programme (FP7/2007-2013) under grant agreement number 318003 (TREsPASS).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ouchani, S., Lenzini, G. Generating attacks in SysML activity diagrams by detecting attack surfaces. J Ambient Intell Human Comput 6, 361–373 (2015). https://doi.org/10.1007/s12652-015-0269-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-015-0269-8