Abstract
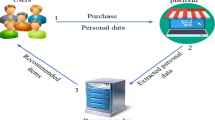
Recommendation system has witnessed a significant improvement with the introduction of data mining. Data mining services require accurate input data for their results to be meaningful, but privacy concerns may influence users to provide spurious information. In order to preserve the privacy of the client in data mining process, the issue of information protection has become more urgently demanded. In this paper, an innovative system for movies recommendation is proposed. The new proposed system is fundamentally based on modified version of multi-parameters perturbation and query restriction as well as adopting non-linear programming strategy to select optimum privacy parameters. The results showed that the proposed framework is capable of providing the maximum security for the information available without decreasing the accuracy of recommendation.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Chen, K., Liu, L.: Privacy preserving data classification with rotation perturbation. In: Proceedings of ICDM, pp. 589–592 (2005)
Jeckmans, A.J.P., Beye, M., Zekeriya, E., Pieter, H., Reginald, L.L., Quiang, T.: Privacy in recommender systems. In: Ramzan, N., van Zwol, R., Lee, J.S., Clüver, K., Hua, X.S. (eds.) Social Media Retrieval. Springer, London (2013)
Liu, K., Kargupta, H., Ryan, J.: Random projection –based multiplicative data perturbation for privacy preserving distributed data mining. IEEE Trans. Knowl. Data Eng. 18, 92–106 (2006)
Chen, K., Sun, G., Liu, L.: Towards attack-resilient geometric data perturbation. In: Proceedings of the SIAM International Conference on Data Mining, April 2007
Li, T., Li, N.: Towards optimal k-anonymization. Data Knowl. Eng. 303. (2008)
Majid, B.M., Asger Gahzi, M., Ali, R.: Privacy preserving data mining techniques: current scenario and future prospects. In: IEEE Third International Conference on Computer and Communication Technology (2012)
Agrawal, R., Srikant, R.: Privacy preserving data mining. In: Proceedings of the ACM SIGMOD International Conference on Management of data (2000)
Liu, L., Kantarcioglu, M., Thuraisingham, B.: The applicability of the perturbation based privacy preserving data mining for real-world data. Data Knowl. Eng. 65, 5–21 (2008)
Shah, A., Gulati, R.: Privacy preserving data mining: techniques, classification and implications - a survey. Int. J. Comput. Appl. (0975 – 8887) 137(12), 40–46 (2016)
Jagannathan, G., Wright, R.N.: Privacy-preserving imputation of missing data. Data Knowl. Eng. (2008)
Yang, W., Qiao, S.: A novel anonymization algorithm: Privacy protection and knowledge preservation. Expert Syst. Appl. 37, 756–766 (2007)
Mukkamala, R., Ashok, V.G: Fuzzy-based methods for privacy-preserving data mining. In: Eighth International Conference on Information Technology: New Generations (ITNG), pp. 348–353 (2011)
Poovammal, E., Ponnavaikko, M.: An improved method for privacy preserving data mining. In: IEEE International Advance Computing Conference (IACC) Patiala, India, 6–7 March 2009
Kamal, R., Hussein, W., Ismail, R.: Privacy preserving recommender system based on improved MASK and query restriction. In: IEEE Eighth International Conference on Intelligent Computing and Information Systems (ICICIS) (2017)
Lou, H., Ma, Y., Zhang, F., Liu, M., Shen, W.: Data mining for privacy preserving association rules based on improved MASK algorithm. In: Proceedings of the IEEE 18th International Conference on Computer Supported Cooperative Work in Design (2014)
Xie, Y., Wulamu, A., Hu, X.: Design and implementation of privacy-preserving recommendation system based on MASK. J. Softw. 9(10), 2607–2613 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Kamal, R., Hussein, W., Ismail, R. (2019). Adopting Non-linear Programming to Select Optimum Privacy Parameters for Multi-parameters Perturbation Algorithm for Data Privacy Improvement in Recommender Systems. In: Hassanien, A., Tolba, M., Shaalan, K., Azar, A. (eds) Proceedings of the International Conference on Advanced Intelligent Systems and Informatics 2018. AISI 2018. Advances in Intelligent Systems and Computing, vol 845. Springer, Cham. https://doi.org/10.1007/978-3-319-99010-1_55
Download citation
DOI: https://doi.org/10.1007/978-3-319-99010-1_55
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-99009-5
Online ISBN: 978-3-319-99010-1
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)