Abstract
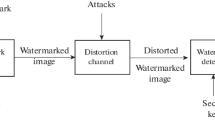
The protection of images made available on public web portals on the Internet can be implemented only through technical mechanisms intrinsic to the images themselves. A digital watermarking service can be used in an automated way to provide such a mechanism without human involvement beyond the initial setup of the service and its integration with the web portal software. Images are published only after they pass through the service which supplies them with a proper signature identifying the copyright holder and the terms of use. A complementary steganalysis service identifies the presence of the digital watermarking data and, depending on its usage, retrieves the embedded copyright information.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Cox, I.J., Miller, M., Bloom, J., Fridrich, J., Kalker, T.: Digital Watermarking and Steganography, 2nd edn. Morgan Kaufmann Publishers (2008)
Cole, E.: Hiding in Plain Sight: Steganography and the Art of Covert Communication, 1st edn. Wiley (2003)
Lin, E., Delp, J.: A review of data hiding in digital images. In: Proceedings of the Image Processing, Image Quality, Image Capture Systems Conference (PICS ‘99), Savannah, Georgia, pp. 274–278 (1999)
Lu, C.: Multimedia Security: Steganography and Digital Watermarking Techniques for Protection of Intellectual Property, 1st edn. Idea Group Publishing (2005)
Curran, K., Bailey, K.: An evaluation of image based steganography methods. Int. J. Digital Evid. 2(2) (2003)
Izadinia, H., Sadeghi, F., Rahmati, M.: A new steganographic method using quantization index modulation. In: International Conference on Computer and Automation Engineering (ICCAE), pp. 181–185 (2009)
Zhao, R.-M., Lian, H., Pang, H.-W., Hu, B.-N.: A watermarking algorithm by modifying AC coefficies in DCT domain. In: International Symposium on Information Science and Engieering (ISISE), vol. 2, Shanghai, China, pp. 159–162 (2008)
Zhang, X.-P., Li, K., Wang, X.: A novel look-up table design method for data hiding with reduced distortion. IEEE Trans. Circuits Syst. Video Technol. 18(6), 769–776 (2008)
Friedrich, J., Goljan, M., Chen, Q., Pathak, V.: Lossless data embedding with file size preservation. In: Proceedings EI SPIE, San Jose, CA (2004)
Chang, C.-C., Chen, T.-S., Chung, L.-Z.: A steganographic method based upon JPEG and quantization table modification. Inf. Sci. Inf. Comput. Sci. 141(1–2), 123–138 (2002)
Fridrich, J.: Image watermarking for tamper detection. In: IEEE International Conference on Image Processing (ICIP), Chicago (1998)
Fridrich, J., Goljan, M., Hogea, D.: Steganalysis of JPEG images: breaking the F5 algorithm. In: 5th Information Hiding Workshop, Noordwijkerhout, The Netherlands, pp. 310–323 (2002)
Westfeld, A.: F5—a steganographic algorithm. In: Proceedings of the 4th International Workshop on Information Hiding, Lecture Notes In Computer Science, vol. 2137, pp. 289–302 (2001)
Lin, C.-Y., Chang, S.-F.: Semi-fragile watermarking for authenticating JPEG visual content. In: SPIE International Conference on Security and Watermarking of Multimedia Contents II, vol. 3971, San Jose, California, USA (2000)
Ilchev, S., Ilcheva, Z.: Modular data hiding for digital image authentication. In: Proceedings of the IADIS European Conference on Data Mining, Freiburg, Germany, pp. 122–127. ISBN 978-972-8939-23-6 (2010)
Ilchev, S., Ilcheva, Z.: Modular data hiding approach for web based applications. In: Proceedings of the International Conference “Automatics and Informatics’10”, Sofia, Bulgaria, pp. I253–I256. ISSN 1313-1850 (2010)
Ilchev, S.: Accurate data embedding in JPEG images for image authentication. In: Comptes rendus de l’Acad´emie bulgare des Sciences, vol. 66, no. 9, pp. 1247–1254. ISSN 1310-1331 (2013)
Ilchev, S., Ilcheva, Z.: Correlation-based steganalysis of modular data hiding methods. In: 15th International Conference on Computer Systems and Technologies (CompSysTech ‘14), Ruse, Bulgaria, pp. 108–115. ISBN: 978-1-4503-2753-4. doi:10.1145/2659532.2659611 (2014)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing Switzerland
About this chapter
Cite this chapter
Ilchev, S., Ilcheva, Z. (2016). Modular Digital Watermarking and Corresponding Steganalysis of Images on Publicly Available Web Portals. In: Margenov, S., Angelova, G., Agre, G. (eds) Innovative Approaches and Solutions in Advanced Intelligent Systems . Studies in Computational Intelligence, vol 648. Springer, Cham. https://doi.org/10.1007/978-3-319-32207-0_12
Download citation
DOI: https://doi.org/10.1007/978-3-319-32207-0_12
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-32206-3
Online ISBN: 978-3-319-32207-0
eBook Packages: EngineeringEngineering (R0)