Abstract
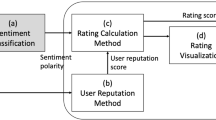
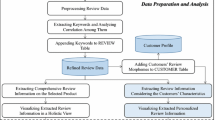
Reviews are a powerful decision-making tool for potential new customers, since they can significantly influence consumer purchase decisions, hence resulting in financial gains or losses for businesses. In striving for trustworthy review systems, validating reviews that could negatively or positively bias new customers is of utmost importance. To this goal, we propose VISIO: a visualization based representation of reviews that enables quick analysis and elicitation of interesting patterns and singularities. In fact, VISIO is meant to amplify cognition, supporting the process of singling out those reviews that require further analysis. VISIO is based on a theoretically sound approach, while its effectiveness and viability is demonstrated applying it to real data extracted from Tripadvisor and Booking.com.
This research has been partially supported by the MIB (My Information Bubble) project of Registro.it.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
- 2.
- 3.
The authors of [11] used data from STR: www.str.com.
References
Beutel, A., Xu, W., Guruswami, V., Palow, C., Faloutsos, C.: Copycatch: stopping group attacks by spotting lockstep behavior in social networks. In: WWW 2013, Rio de Janeiro, Brazil, pp. 119–130 (2013)
Chen, C., Wu, K., Srinivasan, V., Zhang, X.: Battling the Internet water army: detection of hidden paid posters. In: ASONAM 2013, Niagara, ON, Canada, pp. 116–120 (2013)
Colantonio, A., Di Pietro, R., Ocello, A., Verde, N.V.: Visual role mining: a picture is worth a thousand roles. IEEE Trans on Knowl. Data Eng. 24(6), 1120–1133 (2012)
David, S., Pinch, T.: Six degrees of reputation: the use and abuse of online review and recommendation systems (originally published in March 2006). First Monday (2006). http://firstmonday.org/ojs/index.php/fm/article/view/1590
Geerts, F., Goethals, B., Mielikäinen, T.: Tiling databases. In: Suzuki, E., Arikawa, S. (eds.) DS 2004. LNCS (LNAI), vol. 3245, pp. 278–289. Springer, Heidelberg (2004)
Jindal, N., Liu, B.: Opinion spam and analysis. In: WSDM 2008, pp. 219–230. ACM (2008)
Lee, K., Tamilarasan, P., Caverlee, J.: Crowdturfers, campaigns, and social media: tracking and revealing crowdsourced manipulation of social media. In: ICWSM 2013, Cambridge, Massachusetts, USA (2013)
Li, F., Huang, M., Yang, Y., Zhu, X.: Learning to identify review spam. In: IJCAI 2011 - Volume Three, Barcelona, Catalonia, Spain, pp. 2488–2493 (2011)
Liu, B.: Sentiment Analysis and Opinion Mining. Synthesis Lectures on Human Language Technologies. Morgan & Claypool Publishers, San Rafael (2012)
Lyon, T.P., Maxwell, J.W.: Astroturf: interest group lobbying and corporate strategy. J. Econ. Manag. Strategy 13(4), 561–597 (2004)
Mayzlin, D., Dover, Y., Chevalier, J.: Promotional reviews: an empirical investigation of online review manipulation. Am. Econ. Rev. 104(8), 2421–2455 (2014). http://www.aeaweb.org/articles.php?doi=10.1257/aer.104.8.2421
Mukherjee, A., Liu, B., Glance, N.S.: Spotting fake reviewer groups in consumer reviews. In: WWW 2012, Lyon, France, pp. 191–200 (2012)
Ott, M., Choi, Y., Cardie, C., Hancock, J.T.: Finding deceptive opinion spam by any stretch of the imagination. In: Proceedings of 49th Annual Meeting of the Association for Computational Linguistics: Human Language Technologies-Volume 1, pp. 309–319 (2011)
Puolamäki, K., Fortelius, M., Mannila, H.: Seriation in paleontological data using Markov Chain Monte Carlo methods. PLoS Comput. Biol. 2(2), e6 (2006)
Santamaria, R., Theron, R., Quintales, L.: BicOverlapper: a tool for bicluster visualization. Bioinformatics 24(9), 1212–1213 (2008)
Shmulevich, I., Zhang, W.: Binary analysis and optimization-based normalization of gene expression data. Bioinformatics 18(4), 555–565 (2002)
Sun, G., Wu, Y., Liang, R., Liu, S.: A survey of visual analytics techniques and applications: state-of-the-art research and future challenges. J. Comput. Sci. Technol. 28(5), 852–867 (2013)
Thomas, J.J., Cook, K.A.: A visual analytics agenda. IEEE Comput. Graph. Appl. 26(1), 10–13 (2006)
Wang, G., Wilson, C., Zhao, X., Zhu, Y., Mohanlal, M., Zheng, H., Zhao, B.Y.: Serf and turf: crowdturfing for fun and profit. In: WWW 2012, Lyon, France, pp. 679–688 (2012)
Wang, G., Xie, S., Liu, B., Yu, P.S.: Review graph based online store review spammer detection. In: ICDM 2011, pp. 1242–1247. Vancouver, BC, Canada (2011)
Wu, G., Greene, D., Smyth, B., Cunningham, P.: Distortion as a validation criterion in the identification of suspicious reviews. In: Proceedings of 1st Workshop on Social Media Analytics, pp. 10–13. ACM (2010)
Xie, Z., Zhu, S.: Grouptie: toward hidden collusion group discovery in app stores. In: WiSec 2014 (2014)
Zaki, M.J., Hsiao, C.-J.: Efficient algorithms for mining closed itemsets and their lattice structure. IEEE Trans. Knowl. Data Eng. 17(4), 462–478 (2005)
Acknowledgements
The authors warmly thank Vittoria Cozza for her support to the realization of this work.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Colantonio, A., Di Pietro, R., Petrocchi, M., Spognardi, A. (2015). VISIO: A Visual Approach for Singularity Detection in Recommendation Systems. In: Fischer-Hübner, S., Lambrinoudakis, C., López, J. (eds) Trust, Privacy and Security in Digital Business. TrustBus 2015. Lecture Notes in Computer Science(), vol 9264. Springer, Cham. https://doi.org/10.1007/978-3-319-22906-5_3
Download citation
DOI: https://doi.org/10.1007/978-3-319-22906-5_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-22905-8
Online ISBN: 978-3-319-22906-5
eBook Packages: Computer ScienceComputer Science (R0)