Abstract
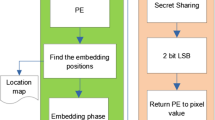
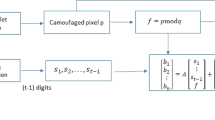
In recent years, a lot of data hiding algorithms have been proposed in the literature. Providing high payload capacity, high visual quality, and robustness is the main aim of data hiding algorithms. However, high visual quality and high payload capacity are inversely proportional. For this reason, we used a probabilistic method. Probabilistic method is one of the soft computing methods. In this paper, a new data hiding algorithm based on probabilistic XOR secret sharing (PXORSS) in lifting wavelet transform (LWT) domain is proposed for providing high capacity and high visual quality. Previous studies have used cover images as RGB images or multiple grayscale images. LWT is proposed to use secret-sharing-based data hiding algorithms with a single grayscale cover image. In the proposed method, we used low–high (LH), high–low (HL), and high–high (HH) high-pass filter bands as cover images, and the secret data are divided into three secret shares by using PXORSS scheme. The least distorted pieces of probabilities are embedded into the high-pass filter bands as the secret share of the host image. We obtained high capacity and high visual quality in LWT domain by using the proposed method.
Similar content being viewed by others
References
Lin C.C., Liu X.L., Yuan S.M.: Reversible data hiding for VQ-compressed images based on search-order coding and state-codebook mapping. Inf. Sci. 293, 314–326 (2015)
Nair N.S., Mathew T., Neethu A.S., Viswanath V.P., Nair M.S., Wilscy M.: A proactive approach to reversible data hiding in encrypted images. Proc. Comput. Sci. 46, 1510–1517 (2015)
Wu X., Sun W.: Random grid-based visual secret sharing for general access structures with cheat-preventing ability. J. Syst. Softw. 85(5), 1119–1134 (2012)
Nazari S., Moghadam A.M.E., Moin M.S.: A novel image steganography scheme based on morphological associative memory and permutation schema. Secur. Commun. Netw. 8(2), 110–121 (2015)
Choi Y., Aizawa K.: Digital watermarking technique using block correlation of DCT coefficients. Electron. Commun. Jpn. (Part II: Electronics) 85(9), 23–31 (2002)
Govind P.V.S., Wilscy M.: A new reversible data hiding scheme with improved capacity based on directional interpolation and difference expansion. Proc. Comput. Sci. 46, 491–498 (2015)
Liu J.F., Tian Y.G., Han T., Yang C.F., Liu W.B.: LSB steganographic payload location for JPEG-decompressed images. Digital Signal Process. 38, 66–76 (2015)
Lou D.C., Hu C.H.: LSB steganographic method based on reversible histogram transformation function for resisting statistical steganalysis. Inf. Sci. 188, 346–358 (2012)
Lee S.H.: DWT based coding DNA watermarking for DNA copyright protection. Inf. Sci. 273, 263–286 (2014)
Lin Y.K.: A data hiding scheme based upon DCT coefficient modification. Comput. Stand. Interfaces 36(5), 855–862 (2014)
Shamir A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Naor, M.; Shamir, A.: Visual cryptography. In: De Santis, A.(ed.) Advances in Cryptology—EUROCRYPT’94. Lecture Notes in Computer Science, vol. 950, pp. 1–12. Springer, Berlin, Heidelberg (1994)
Sencar H.T., Ramkumar M., Akansu A.N.: Data Hiding Fundamentals and Applications, Content Security in Digital Media. Elsevier Academic Press, Boston (2004)
Miller, A.: Least Significant Bit Embeddings: Implementation And Detection (2012)
Schyndel, R.G.V.; Tirkel, A.Z.; Osborne, C.F.: A digital watermark. In: Proceedings of IEEE International Conference of Image Processing 2, pp. 86–90, Austin, Texas (1994)
Sun, G.; Yu, Y.: DWT based watermarking algorithm of color images. In: Second IEEE Conference on Industrial Electronics and Application, pp. 1823–1826 (2007)
Lee C.-W., Tsai W.-H.: A secret-sharing-based method for authentication of grayscale document images via the use of the PNG image with a data repair capability. IEEE Trans. Image Process. 21(1), 207–218 (2011)
Lee, C.-W.; Tsai, W.-H.: A data hiding method based on information sharing via PNG images for applications of color image authentication and metadata embedding. Signal Process. 93(7), 2010–2025 (2013)
Gurung S., Chakravorty M., Agarwal A., Ghose M.K.: Multiple information hiding using circular random grids. Proc. Comput. Sci. 48, 65–72 (2015)
Tu S.-F., Hsu C.-S.: Protecting secret documents via a sharing and hiding scheme. Inf. Sci. 279(20), 52–59 (2014)
Yuan H.D.: Secret sharing with multi-cover adaptive steganography. Inf. Sci. 254, 197–212 (2014)
Tuncer, T.; Avci, E.: A reversible data hiding algorithm based on probabilistic DNA-XOR secret sharing scheme for color images Displays 41, 1–8 (2016)
Sweldens W.: The lifting scheme: a construction of second generation wavelets. SIAM J. Math. Anal. 29(2), 511–546 (1998)
Jia, Z.-Z.; Zhu, H.-Y.; Cheng, W.-S.: A blind watermarking algorithm based on lifting wavelet transform and scrambling technology. In: International Conference on Electrical and Control Engineering (ICECE), pp. 4576–4579 (2010)
Verma V.S., Jhab R.K., Ojha A.: Significant region based robust watermarking scheme in lifting wavelet transform domain. Expert Syst. Appl. 42, 8184–8197 (2015)
Makbol N.M., Khoo B.E.: A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition. Digital Signal Process. 33, 134–147 (2014)
Wang, D.; Li, X.; Yi, F.: Probabilistic (n,n) visual secret sharing scheme for grayscale images. In: Information Security and Cryptology, Lecture Notes in Computer Science, vol. 4990, Springer-Verlag, Berlin, pp. 192–200 (2007)
SIPI Image Database. http://sipi.usc.edu/database/. Access Date 16 June 2015
Zengzhen M.: Image quality assessment in multiband DCT domain based on SSIM. Optik 125, 6470–6473 (2014)
Kamran, A.; Khan, Malik, S.A.: A high capacity reversible watermarking approach for authenticating images: Exploiting down-sampling, histogram processing, and block selection. Inf. Sci. 256, 162–183 (2014)
Luo H., Yu F.X., Chen H., Huang Z.L., Li H., Wang P.H.: Reversible data hiding based on block median preservation. Inf. Sci. 181, 308–328 (2010)
Lin C.C., Tsai W.H.: Secret image sharing with steganography and authentication. J. Syst. Softw. 73, 405–414 (2004)
Yang C.N., Chen T.S., Yu K.H., Wang C.C.: Improvements of image sharing with steganography and authentication. J. Syst. Softw. 80, 1070–1076 (2007)
Chang C.C., Hsieh Y.P., Lin C.H.: Sharing secrets in stego images with authentication. Pattern Recognit. 41(10), 3130–3137 (2008)
Eslami Z., Ahmadabadi J.Z.: Secret image sharing with authentication-chaining and dynamic embedding. J. Syst. Softw. 84, 803–809 (2011)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Avci, E., Tuncer, T. & Avci, D. A Novel Reversible Data Hiding Algorithm Based on Probabilistic XOR Secret Sharing in Wavelet Transform Domain. Arab J Sci Eng 41, 3153–3161 (2016). https://doi.org/10.1007/s13369-016-2124-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-016-2124-4