Abstract
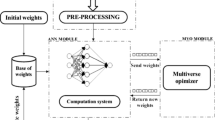
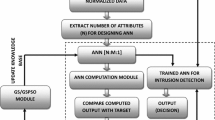
The need to avoid computer system breaches is increasing. Many researchers have adopted different approaches, such as intrusion detection systems (IDSs), to handle various threats. Intrusion detection has become an imperative system to detect various security breaches. Until today, researchers face the problem of building reliable and effective IDSs that can handle numerous attacks with changing patterns. This paper deals with feed-forward neural network (FNN) training problems using the application of a recently invented meta-heuristic optimization algorithm locust swarm optimization (LSO) for the first time. FNN is combined with LSO (FNN-LSO) to build an advanced detection system and improve the performance of IDS. Our method is applied to a series of experiments to study the capability and performance of the proposed approach. Experimental studies began by using intrusion detection evaluation data, namely, NSL-KDD and UNSW-NB15, to benchmark the performance of the proposed approach. The most common evolutionary trainers, namely, particle swarm optimizer PSO-based trainer and genetic algorithm GA-based trainer, were implemented to verify the results. Compared with existing methods in the literature, our proposed approach provides to be more accurate to be an alternative solution for IDS. The experimental results show that our training algorithm not only attained a very good performance in terms of speed convergence but also achieved reliability due to the reduced likelihood of being trapped in local minima. Furthermore, our proposed model improves the detection rate.








Similar content being viewed by others
References
Xie G, Xie K, Huang J, Wang X, Chen Y, Wen J (2017) Fast low-rank matrix approximation with locality sensitive hashing for quick anomaly detection. In: 2017 IEEE Conference on computer communications (INFOCOM)
Bamakan SMH, Amiri B, Mirzabagheri M, Shi Y (2015) A new intrusion detection approach using pso based multiple criteria linear programming. Procedia Comput Sci 55:231–237
Demertzis K, Iliadis L (2014) A hybrid network anomaly and intrusion detection approach based on evolving spiking neural network classification. Springer International Publishing, Cham, pp 11–23
Dash T (2017) A study on intrusion detection using neural networks trained with evolutionary algorithms. Soft Comput 21(10):2687–2700
Tang A, Sethumadhavan S, Stolfo SJ (2014) Unsupervised anomaly-based malware detection using hardware features. Springer International Publishing, Cham, pp 109–129
Ghorbani AA, Lu W, Tavallaee M (2010) Detection approaches. Springer, Boston, pp 27–53
Rastegari S (2015) Intelligent network intrusion detection using an evolutionary computation approach
Tian WJ, Liu JC (2010) Network intrusion detection analysis with neural network and particle swarm optimization algorithm. In: 2010 Chinese control and decision conference, pp 1749–1752
Lotfi Shahreza M, Moazzami D, Moshiri B, Delavar MR (2011) Anomaly detection using a self-organizing map and particle swarm optimization. Sci Iran 18(6):1460–1468
Gomathy A, Lakshmipathi B (2011) Network intrusion detection using genetic algorithm and neural network. Springer, Berlin Heidelberg, Berlin, pp 399–408
Pal B, Hasan MAM (2012) Neural network amp; genetic algorithm based approach to network intrusion detection amp; comparative analysis of performance. In: 2012 15th international conference on computer and information technology (ICCIT), pp 150–154
Ozturk C, Karaboga D (2011) Hybrid artificial bee colony algorithm for neural network training. In: 2011 IEEE congress of evolutionary computation (CEC), pp 84–88
Hassim YMM, Ghazali R (2014) Optimizing functional link neural network learning using modified bee colony on multi-class classifications. Springer, Berlin, pp 153–159
Chattopadhyay M (2015) Modelling of intrusion detection system using artificial intelligence—evaluation of performance measures. Springer International Publishing, Cham, pp 311–336
Akkar HA, Mahdi FR (2016) Evolutionary algorithms for neural networks binary and real data classification. Int J Sci Technol Res 5(7):55–60
Abdalla OA, Elfaki AO, Almurtadha YM (2014) Optimizing the multilayer feed-forward artificial neural networks architecture and training parameters using genetic algorithm. Int J Comput Appl 96(10):42–48 Full text available
Garro BA, Vázquez RA (2015) Designing artificial neural networks using particle swarm optimization algorithms. Intell Neurosci 2015:61
Faris H, Aljarah I, Mirjalili S (2016) Training feedforward neural networks using multi-verse optimizer for binary classification problems. Appl Intell 45(2):322–332
Bui NT, Hasegawa H (2015) Training artificial neural network using modification of differential evolution algorithm. Int J Mach Learn Comput 5(1):1–6
Ding S, Li H, Chunyang S, Junzhao Y, Jin F (2013) Evolutionary artificial neural networks: a review. Artif Intell Rev 39(3):251–260
Cuevas E, González A, Zaldívar D, Pérez-Cisneros M (2015) Multithreshold segmentation by using an algorithm based on the behavior of locust swarms. Math Probl Eng 2015(805357):25
González A, Cuevas E, Fausto F, Valdivia A, Rojas R (2017) A template matching approach based on the behavior of swarms of locust. Appl Intell 47(4):1087–1098
Lee W, Stolfo SJ, Mok KW (2000) Adaptive intrusion detection: a data mining approach. Artif Intell Rev 14(6):533–567
Ahmad I, Abdullah AB, Alghamdi AS (2009) Application of artificial neural network in detection of probing attacks. In: 2009 IEEE symposium on industrial electronics applications, vol 2, pp 557–562
Li J, Zhang G-Y, Gu G-C (2004) The research and implementation of intelligent intrusion detection system based on artificial neural network. In: Proceedings of 2004 international conference on machine learning and cybernetics (IEEE Cat. No.04EX826), vol 5, pp 3178–3182
Berlin H, Djionang L, Tindo G (2017) A new networks intrusion detection architecture based on neural networks. Glob J Comput Sci Technol Netw Web Secur 17(1):19–27
Lu C, Zhai L, Liu T, Li N (2016) Network intrusion detection based on neural networks and D-S evidence. Springer International Publishing, Cham, pp 332–343
Gonzalez F, Gomez J, Kaniganti M, Dasgupta D (2003) An evolutionary approach to generate fuzzy anomaly (attack) signatures. In: IEEE systems, man and cybernetics society information assurance workshop, 2003, pp 251–259
Qinzhen X, Yang L, Zhao Q, He Z (2006) A novel intrusion detection mode based on understandable neural network trees. J Electrons (China) 23(4):574–579
Ke G, Hong YH (2014) The research of network intrusion detection technology based on genetic algorithm and bp neural network. In: Frontiers of manufacturing science and measuring technology IV, vol 599 of applied mechanics and materials. Trans Tech Publications, pp 726–730
Han S-J, Cho S-B (2005) Evolutionary neural networks for anomaly detection based on the behavior of a program. IEEE Trans Syst Man Cybern Part B (Cybernetics) 36(3):559–570
Michailidis E, Katsikas SK, Georgopoulos E (2008) Intrusion detection using evolutionary neural networks. In: 2008 Panhellenic conference on informatics, pp 8–12
Qiu C, Shan J (2015) Research on intrusion detection algorithm based on bp neural network. Int J Secur Appl 9(6):247–259
Maarouf M, Sosa A, Galván B, Greiner D, Winter G, Mendez M, Aguasca R (2015) The role of artificial neural networks in evolutionary optimisation: a review. Springer International Publishing, Cham, pp 59–76
Zhu A-X (2017) Artificial neural networks. In: International encyclopedia of geography. American Cancer Society, Atlanta, Georgia, US, pp 1–6
Chen J-F, Do QH, Hsieh H-N (2015) Training artificial neural networks by a hybrid pso-cs algorithm. Algorithms 8(2):292–308
Chen S (2009) An analysis of locust swarms on large scale global optimization problems. Springer, Berlin, pp 211–220
Cuevas E, González A, Zaldívar D, Pérez-Cisneros M (2015) An optimisation algorithm based on the behaviour of locust swarms. Int J Bioinspired Comput 7(6):402–407
Topaz CM, Bernoff AJ, Logan S, Toolson W (2008) A model for rolling swarms of locusts. Eur Phys J Spec Top 157:93–109
Cortes C, Gonzalvo X, Kuznetsov V, Mohri M, Yang S (2016) Adanet: adaptive structural learning of artificial neural networks. CoRR. arXiv:abs/1607.01097
The Cyber Range Lab of the Australian Centre for Cyber Security (ACCS). Unsw-nb15 dataset. http://www.accs.unsw.adfa.edu.au/. Accessed May 2015
Moustafa N, Slay J (Nov 2015) Unsw-nb15: a comprehensive data set for network intrusion detection systems (unsw-nb15 network data set). In: 2015 military communications and information systems conference (MilCIS), pp 1–6
Moustafa N, Slay J (2016) The evaluation of network anomaly detection systems: statistical analysis of the unsw-nb15 data set and the comparison with the kdd99 data set. Inf Secur J A Glob Perspect 25(1–3):18–31
Khammassi C, Krichen S (2017) A ga-lr wrapper approach for feature selection in network intrusion detection. Comput Secur 70(Supplement C):255–277
NSLKDD. Nsl-kdd dataset. http://nsl.cs.unb.ca/NSL-KDD. Accesses Jun 2013
Feng W, Zhang Q, Hu G, Huang JX (2014) Mining network data for intrusion detection through combining svms with ant colony networks. Future Gener Comput Syst 37(Supplement C):127–140 (Special section: innovative methods and algorithms for advanced data-intensive computing special section: semantics, intelligent processing and services for big data special section: advances in data-intensive modelling and simulation special section: hybrid intelligence for growing internet and its applications)
Chung YY, Wahid N (2012) A hybrid network intrusion detection system using simplified swarm optimization (sso). Appl Soft Comput 12(9):3014–3022
Tang TA, Mhamdi L, McLernon D, Zaidi SAR, Ghogho M (2016) Deep learning approach for network intrusion detection in software defined networking. In: 2016 international conference on wireless networks and mobile communications (WINCOM), pp 258–263
Guo C, Ping Y, Liu N, Luo S-S (2016) A two-level hybrid approach for intrusion detection. Neurocomputing 214(Supplement C):391–400
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Benmessahel, I., Xie, K., Chellal, M. et al. A new evolutionary neural networks based on intrusion detection systems using locust swarm optimization. Evol. Intel. 12, 131–146 (2019). https://doi.org/10.1007/s12065-019-00199-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12065-019-00199-5