Abstract
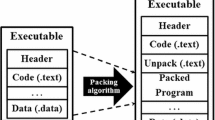
Advanced persistent attacks, incorporated by sophisticated malware, are on the rise against hosts, user applications and utility software. Modern malware hide their malicious payload by applying packing mechanism. Packing tools instigate code encryption to protect the original malicious payload. Packing is employed in tandem with code obfuscation/encryption/compression to create malware variants. Despite being just a variant of known malware, the packed malware invalidates the traditional signature based malware detection as packing tools create an envelope of packer code around the original base malware. Therefore, unpacking becomes a mandatory phase prior to anti-virus scanning for identifying the known malware hidden behind packing layers. Existing techniques of unpacking solutions increase execution overhead of AV scanners in terms of time. This paper illustrates an easy to use approach which works in two phases to reduce this overhead. The first phase (ESCAPE) discriminates the packed code from the native code (non-packed) by using random block entropy. The second phase (PEAL) validates inferences of ESCAPE by employing bi-classification (packed vs native) model using relevant hex byte features extracted blockwise. The proposed approach is able to shrink the overall execution time of AV scanners by filtering out native samples and avoiding excessive unpacking overhead. Our method has been evaluated against a set consisting of real packed instances of malware and benign programs.










Similar content being viewed by others
Notes
Internet Security Threat Report 2014. http://www.symantec.com/security_response/publications/threatreport.jsp
References
Avgerinos T, Rebert A, Cha S K and Brumley D 2014 Enhancing symbolic execution with veritesting. In: Proceedings of the 36th International Conference on Software Engineering ACM, Hyderabad, India, pp. 1083–1094
Brosch T and Morgenstern M 2006 Runtime packers: The hidden problem. In: Proceedings of Black Hat USA, Black Hat, www.blackhat.com/presentations/bh-usa-06/BH-US-06-Morgenstern.pdf
Bohne L 2008 Pandora’s Bochs: Automatic unpacking of malware. In: PHDTHESIS, pp. 1–121
Christopher A B 2010 Maitland: Analysis of packed and encrypted malware via paravirtualization extensions in https://dspace.library.uvic.ca/handle/1828/3866, pp. 1–82
Coogan K, Debray S, Kaochar T and Townsend G 2009 Automatic static unpacking of malware binaries. In: Proceedings of the 16th Working Conference on Reverse Engineering (WCRE ’09), IEEE, pp. 167–176
Dinaburg A, Royal P, Sharif M and Lee W 2008 Ether malware analysis via hardware virtualization extensions. In: Proceedings of the 15th ACM Conference on Computer and Communications Security (CCS’08), ACM, pp. 51–62
Freund Y and Schapire R E 1997 A decision-theoretic generalization of on-line learning and an application to boosting. J. Comput. Syst. Sci. 55:1, Academic Press Inc.; Orlando FL, USA; pp. 119–139
Goise F and Olla S 2001 Entropy methods for the Boltzmann equation. In: lectures from a special semester at the Centre mile Borel Institute Springer, Poincarè, Paris, pp. 1–14
Haahr M 1999 An introduction to randomness and random numbers in www.random.org/essay.html Random.org
Han S, Lee K and Lee S 2009 Packed PE file detection for malware forensics. In: Proceedings of 2nd International Conference on Computer Science and its Applications (CSA’09), IEEE, Jeju Island, Korea, pp. 1–7
Jacob G, Comparetti P M, Neugschwandtner M, Kruegel C and Vigna G 2013 A static, packer–agnostic filter to detect similar malware samples. In: Proceedings of International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA), Springer Berlin Heidelberg, pp. 102–122
Jeong G, Choo E, Lee J, Bat-Erdene M and Lee H 2010 Generic unpacking using entropy analysis. In: Proceedings of 5th International Conference on Malicious and Unwanted Software (MALWARE ’10) IEEE, pp. 98–105
Kang M G, Poosankam P and Yin H 2007 Renovo: A hidden code extractor for packed executables. In: Proceedings of the 2007 ACM Workshop on Recurring Malcode (WORM ’07) ACM, New York, USA, pp. 46–53
Kevin T 2010 Malware validation techniques. In: http://blogs.cisco.com/security/malware_validation_techniques/
Kohavi R 1995 A study of cross-validation and bootstrap for accuracy estimation and model selection. In: Proceedings of the 14th International Joint Conference on Artificial Intelligence (IJCAI’95) 2, Morgan Kaufmann Publishers, San Francisco, CA, USA, pp. 1137–1143
Laxmi V, Gaur M S, Faruki P and Naval S 2011 PEAL-packed executable analysis. In: Proceedings of the 2011 International Conference on Advanced Computing, Networking and Security (ADCONS’11) Springer, pp. 237–243
Lyda R and Hamrock J 2007 Using entropy analysis to find encrypted and packed malware. IEEE Security and Privacy 5:2, Piscataway, NJ, USA, pp. 40–45
Martignoni L, Christodorescu M and Jha S 2007 OmniUnpack: Fast, generic, and safe unpacking of malware. In: Proceedings of Twenty-Third Annual Computer Security Applications Conference (ACSAC 2007) IEEE, pp. 431–441
Naval S, Laxmi V, Gaur M S and Vinod P 2012 ESCAPE: Entropy score analysis of packed executable. In: Proceedings of the Fifth International Conference on Security of Information and Networks (SIN’12) ACM, New York USA, pp. 197–200
Payam R, Lei T and Huan L 2009 Cross-validation. In: Encyclopedia of Database systems pp. 532–538
Perdisci R, Lanzi A and Wenke L 2008 McBoost: Boosting scalability in malware collection and analysis using statistical classification of executables. In: Proceedings of Computer Security Applications Conference (ACSAC 2008) pp. 301–310
Royal P, Halpin M, Dagon D, Edmonds R and Lee W 2006 PolyUnpack: Automating the hidden-code extraction of unpack-executing malware. In: Proceedings of the 22nd Annual Computer Security Applications Conference (ACSAC ’06) IEEE, Washington, DC, USA, pp. 289–300
Sang-Bum K, Kyoung-Soo H, Hae-Chang R and Sung-Hyon M 2006 Some effective techniques for naive bayes text classification. IEEE Transaction on Knowledge and Data Engineering 18:11, pp. 1457–1466
Saxena P, Poosankam P, McCamant S and Song D 2009 Loop-extended symbolic execution on binary programs. In: Proceedings of the Eighteenth International Symposium on Software Testing and Analysis ACM, Chicago, IL, USA, pp. 225–236
Shafiq M Z, Tabish S M, Mirza F and Farooq M 2009 PE-Miner: Mining structural information to detect malicious executables in realtime. In: Recent advances in intrusion detection 5758, Springer, pp. 121–141
Shannon C E and Weaver W 1963 The mathematical theory of communication. University of Illinois Press
Ugarte-Pedrero X, Santos I and Garcia-Bringas P 2011 Structural feature based anomaly detection for packed executable identification. In: Proceedings of Computational Intelligence in Security for Information Systems (CISIS’11), LNCS, pp. 230–237
Vilkeliskis T 2009 Automated unpacking of executables using dynamic binary instrumentation. http://vilkeliskis.com/_static/research/2009-unpackdbi-paper.pdf pp. 1–14
Vinod P, Laxmi V and Gaur M S 2012 REFORM: Relevant feature for malware analysis. In: Proceedings of Sixth IEEE international conference of security and Multimodality in Pervasive Environment (SMPE-2012) Fukuoka, Japan, pp. 26–29
Wei Y, Zheng Z and Ansari N 2008 Revealing packed malware. In: IEEE Security and Privacy 6:5, pp. 65–69
Yang-Seo C, Ik-kyun K, Jin-Tae O and Jae-Cheol R 2008 PE File Header analysis-based packed PE file detection technique (PHAD). In: Proceedings of International Symposium on Computer Science and its Applications (CSA ’08) pp. 28–31
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
NAVAL, S., LAXMI, V., GAUR, M.S. et al. An efficient block-discriminant identification of packed malware. Sadhana 40, 1435–1456 (2015). https://doi.org/10.1007/s12046-015-0399-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12046-015-0399-x