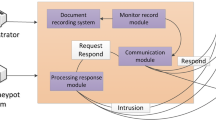
Abstract
A mimicry honeypot framework based on game theory is presented in our work, which can calculate the equilibrium strategy of the deceptive game using non-cooperative incomplete dynamic game theory, and make decisions for the mimicry framework to deploy the simple service, the honeypot and the fake honeypot. A mimicry prototype is implemented using NS2 platform, and simulation experiments are launched to validate the decision-making result and the deceptive performance of the mimicry honeypot. The empirical study shows that the mimicry honeypot framework based on game theory can be able to influence the equilibrium strategy results by dynamically changing the deployment vector of the mimicry system. It validates that the mimicry honeypot framework has better flexibility, activeness and fraudulence than the traditional honeypot.
Similar content being viewed by others
References
Duncan C, Sheppard P. Sensory discrimination and its role in the evolution of Bayesian mimicry [J]. Behavior, 1965, 24(3/4): 269–282.
Shi L Y, Jiang L, Liu D, et al. Mimicry honeypots: a brief introduction [C] // WiCOM2012. Shanghai: IEEE Computer Society, 2012: 1–4.
Shi L Y, Liu D, Xing W, et al. Evolution Mechanism for mimicry honeypot through adaptive genetic algorithm [J]. Journal of Huazhong University of Science & Technology (Natural Science Edition), 2015, 43(5): 68–73 (Ch).
Shi L Y, Jiang L, Xin Liu, et al. Game theoretic analysis for the feature of mimicry honeypot [J]. Journal of Electronics & Information Technology, 2013, 35(5): 1063–1068 (Ch).
Kiekintveld C, Lisý V, Píbil R. Game-Theoretic foundations for the strategic use of honeypots in network security [M] // Cyber Warfare. Berlin: Springer-Verlag, 2015: 81–101.
Wagener G, State R, Dulaunoy A, et al. Self-adaptive high interaction honeypots driven by game theory [C] // Stabilization, Safety, and Security of Distributed Systems, LNCS 5873. Berlin: Springer-Verlag, 2009: 741–755.
Garg N, Grosu D. Deception in honeynets: a game-theoretic analysis [C] // Proceedings of IEEE Information Assurance and Security Workshop. New York: IEEE Press, 2007: 20–22.
Carroll T, Grosu D. A game theoretic investigation of deception in network security [J]. Security and Communication Networks, 2011, 4(10):1162–1172.
Hayatle O, Otrok H. A game theoretic investigation for high interaction honeypots [C] // IEEE International Workshop on Security and Forensics in Communication Systems. Ottawa: IEEE Press, 2012: 6662–6667.
Simmons C B, Shiva S G, Bedi H S, et al. ADAPT: A game inspired attack-defense and performance metric taxonomy [C] // IFIP International Federation for Information Processing. Heidelberg: Springer-Verlag, 2013: 344–365.
Cai J, Yegneswaran V, Alfeld C, et al. An attacker-defender game for honeynets [C] // Computing and Combinatorics, LNCS 5609. Berlin: Springer-Verlag, 2009: 7–16.
Cai J, Yegneswaran V, Alfeld C, et al. Honeygames: A game theoretic approach to defending network monitors [J]. Journal of Combinatorial Optimization, 2011, 22(3): 305–324.
Pibil R, Liisy V, Kiekintveld C, et al. Game theoretic model of strategic honeypot allocation in computer networks [C] // Decision and Game Theory for Security, LNCS 7638. Berlin: Springer-Verlag, 2012: 201–220.
Li H, Yang X, Qu L. On the offense and defense game in the network honeypot [C] // Advances in Automation and Robotics, Lecture Notes in Electrical Engineering 123. Berlin: Springer-Verlag, 2012: 239–246.
Wei L, Wang X. Research on honeypot information fusion based on game theory [C] // Second International Conference on Computer Research and Development. Washinton D C: IEEE Press, 2010: 803–806.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the National Natural Science Foundation of China (61309024) and the Funding of Shanghai Key Laboratory of Financial Information Technology
Biography: SHI Leyi, male, Professor, Ph.D., research direction: network and information security, cyber defense, game theory, and mobile Internet
Rights and permissions
About this article
Cite this article
Shi, L., Zhao, J., Jiang, L. et al. Game theoretic simulation on the mimicry honeypot. Wuhan Univ. J. Nat. Sci. 21, 69–74 (2016). https://doi.org/10.1007/s11859-016-1140-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-016-1140-2