Abstract
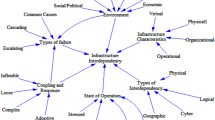
Assessment and modeling associated with the examination of vulnerability and reliability in network based infrastructure have long been recognized as important and necessary. Recent years have seen a growth of activity in vulnerability modeling given natural disasters, human error and terrorist activities. This is due to increased reliance on networked based systems in our everyday lives, as well as the interconnectedness of a range of infrastructures like telecommunications, transportation, electricity, water, etc. This paper provides an overview of the evolution of modeling approaches to examine network vulnerability. Reviewed approaches are characterized in terms of how system performance is accounted for. Interdiction scenarios for each performance class are discussed, illustrating the unique attributes of the various modeling approaches.







Similar content being viewed by others
Notes
Interdiction is a term that refers to the unintentional or intentional loss of one or more network components.
This could be represented and illustrated using a loop arc. It is not used here to avoid potential confusion.
References
Albert, R., Jeong, H., & Barabasi, A. L. (2000). Error and attack tolerance of complex networks. Nature, 406, 378–382.
Arulselvan, A., Commander, C. W., Elefteriadou, L., & Pardalos, P. M. (2009). Detecting critical nodes in sparse graphs. Computers & Operations Research, 36, 2193–2200.
Baran, P. (1964). On distributed communications networks. IEEE Transactions on Communications Systems, 12, 1–9.
Brown, G., Carlyle, M., Salmeron, J., & Wood, K. (2006). Defending critical infrastructure. Interfaces, 36, 530–544.
CBS News. (2010). Death toll rises from massive chile quake. URL: http://www.cbsnews.com/stories/2010/02/27/world/main6249181.shtml (last accessed 3/16/10).
Church, R. L., & Scaparra, M. P. (2007). Protecting critical assets: The r-interdiction median problem with fortification. Geographical Analysis, 39, 129–146.
Church, R. L., Scaparra, M. P., & Middleton, R. S. (2004). Identifying critical infrastructure: The median and covering facility interdiction problems. Annals of the Association of American Geographers, 94, 491–502.
Colbourn, C. J. (1987). The Combinatorics of network reliability. New York: Oxford University Press.
Corley, H. W., & Sha, D. Y. (1982). Most vital links and nodes in weighted networks. Operations Research Letters, 1, 157–160.
Demsar, U., Spatenkova, O., & Virrantaus, K. (2008). Identifying critical locations in a spatial network with graph theory. Transactions in GIS, 12, 61–82.
Ford, L. R., & Fulkerson, D. R. (1962). Flows in networks. Princeton, NJ: Princeton University Press.
Fulkerson, D. R., & Harding, G. C. (1977). Maximizing the minimum source-sink path subject to a budget constraint. Mathematical Programming, 13, 116–118.
Ghare, P. M., Montgomery, D. C., & Turner, W. C. (1971). Optimal interdiction policy for a flow network. Naval Research Logistics Quarterly, 18, 37–45.
Grubesic, T. H., & Murray, A. T. (2006). Vital nodes, interconnected infrastructures and the geographies of network reliability. Annals of the Association of American Geographers, 96, 64–83.
Grubesic, T. H., O’Kelly, M. E., & Murray, A. T. (2003). A geographic perspective on commercial internet survivability. Telematics and Informatics, 20, 51–69.
Grubesic, T. H., Matisziw, T. C., Murray, A. T., & Snediker, D. (2008). Comparative approaches for assessing network vulnerability. International Regional Science Review, 31, 88–112.
Israeli, E., & Wood, R. K. (2002). Shortest-path network interdiction. Networks, 40, 97–111.
Lim, C., & Smith, J. C. (2007). Algorithms for discrete and continuous multicommodity flow network interdiction problems. IIE Transactions, 39, 15–26.
Matisziw, T. C., & Murray, A. T. (2009). Connectivity change in habitat networks. Landscape Ecology, 24, 89–100.
Matisziw, T. C., Murray, A. T., & Grubesic, T. H. (2009). Exploring the vulnerability of network infrastructure to interdiction. Annals of Regional Science, 43, 307–321.
Mouawad, J., & V. Bajaj. (2005). Hurricane Katrina: The oil supply; gulf oil operations remain in disarray. The New York Times, September 2, 2005. URL: http://query.nytimes.com/gst/fullpage.html?res=9503E4DF1431F931A3575AC0A9639C8B63 (last accessed 3/16/10).
Murray, A. T., Matisziw T. C., & Grubesic T. H. (2005). Simulating impacts of network interdiction on O-D flow activity. Paper presented at 52nd North American meeting of the regional science association international, Las Vegas, Nevada, USA, 10–12.
Murray, A. T., & Grubesic, T. (2007). Reliability and vulnerability in critical infrastructure: A quantitative geographic perspective. Heidelberg: Springer.
Murray, A. T., Matisziw, T. C., & Grubesic, T. H. (2007). Critical network infrastructure analysis: Interdiction and system flow. Journal of Geographical Systems, 9, 103–117.
Murray, A. T., Matisziw, T. C., & Grubesic, T. H. (2008). Methodological overview of network vulnerability analysis. Growth and Change, 39, 573–592.
Myung, Y. S., & Kim, H. J. (2004). A cutting plane algorithm for computing k-edge survivability of a network. European Journal of Operational Research, 156, 579–589.
Scaparraa, M. P., & Church, R. L. (2008a). A bilevel mixed-integer program for critical infrastructure protection planning. Computers & Operations Research, 35, 1905–1923.
Scaparraa, M. P., & Church, R. L. (2008b). An exact solution approach for the interdiction median problem with fortification. European Journal of Operational Research, 189, 76–92.
Shooman, M. L. (2002). Reliability of computer systems and networks: Fault tolerance, analysis, and design. New York: Wiley.
Snediker, D., Murray, A. T., & Matisziw, T. C. (2008). Decision support for network disruption mitigation. Decision Support Systems, 44, 954–969.
Snyder, L. V., Scaparra M. P., Daskin M. S., & Church R. L. (2006). Planning for disruptions in supply chain networks. INFORMS Tutorials in Operations Research, 234–257.
Urban, D., & Keitt, T. H. (2001). Landscape connectivity: A graph-theoretic perspective. Ecology, 82, 1205–1218.
Wollmer, R. (1964). Removing arcs from a network. Operations Research, 12, 934–940.
Woo, S. (2009). Bridge fix awaits further tests. The Wall Street Journal, October 29, 2009. URL: http://online.wsj.com/article/SB125673037933212851.html (last accessed 3/16/10).
Wood, R. K. (1993). Deterministic network interdiction. Mathematical and Computer Modeling, 17, 1–18.
Acknowledgments
This material is based upon work supported by the National Science Foundation under Grants No. 0908030 and 0718091. Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Murray, A.T. An overview of network vulnerability modeling approaches. GeoJournal 78, 209–221 (2013). https://doi.org/10.1007/s10708-011-9412-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10708-011-9412-z