Abstract
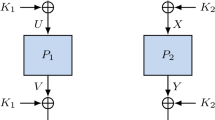
This paper investigates ciphers where the set of encryption functions is identical to the set of decryption functions, which we call reflection ciphers. Equivalently, there exists a permutation P, named the coupling permutation, such that decryption under k corresponds to encryption under P(k). We study the necessary properties for this coupling permutation. Special care has to be taken of some related-key distinguishers since, in the context of reflection ciphers, they may provide attacks in the single-key setting. We then derive some criteria for constructing secure reflection ciphers and analyze the security properties of different families of coupling permutations. Finally, we concentrate on the case of reflection block ciphers and, as an illustration, we provide concrete examples of key schedules corresponding to several coupling permutations, which lead to new variants of the block cipher prince.






Similar content being viewed by others
References
Albrecht M.R., Farshim P., Paterson K.G., Watson G.J.: On cipher-dependent related-key attacks in the ideal-cipher model. In: Fast Software Encryption—FSE 2011. Lecture Notes in Computer Science, vol. 6733, pp. 128–145. Springer, Berlin (2011).
Barreto P., Rijmen V.: The ANUBIS Block Cipher. Submission to the NESSIE project. https://www.cosic.esat.kuleuven.be/nessie/workshop/submissions.html (2000).
Barreto P., Rijmen V.: The Khazad Legacy-Level Block Cipher. Submission to the NESSIE project. https://www.cosic.esat.kuleuven.be/nessie/workshop/submissions.html (2000).
Bellare M., Kohno T.: A theoretical treatment of related-key attacks: RKA-PRPs, RKA-PRFs, and applications. In: Advances in Cryptology—EUROCRYPT 2003. Lecture Notes in Computer Science, vol. 2656, pp. 491–506. Springer, Berlin (2003).
Biryukov A.: DES-X (or DESX). In: van Tilborg H.C.A., Jajodia, S. (eds.) Encyclopedia of Cryptography and Security, 2nd edn, p. 331. Springer, Berlin (2011).
Borghoff J., Canteaut A., Güneysu T., Kavun E.B., Knežević M., Knudsen L.R., Leander G., Nikov V., Paar C., Rechberger C., Rombouts P., Thomsen S.S., Yalçın T.: PRINCE—A low-latency block cipher for pervasive computing applications. In: Advances in Cryptology—ASIACRYPT 2012. Lecture Notes in Computer Science, vol. 7658, pp. 208–225. Springer, Berlin (2012).
Canteaut A., Fuhr T., Gilbert H., Naya-Plasencia M., Reinhard J.: Multiple differential cryptanalysis of round-reduced PRINCE. In: Fast Software Encryption—FSE 2014. Lecture Notes in Computer Science, vol. 8540, pp. 591–610. Springer, Berlin (2014).
Cohen G.D., Karpovsky M.G., Mattson H.F. Jr., Schatz J.R.: Covering Radius—Survey and Recent Results. IEEE Trans. Inf. Theory 31(3), 328–343 (1985).
Coppersmith D.: The real reason for Rivest’s phenomenon. In: Advances in Cryptology—CRYPTO’85. Lecture Notes in Computer Science, vol. 218, pp. 535–536. Springer, Berlin (1985).
Dinur I.: Cryptanalytic time-memory-data tradeoffs for FX-constructions with applications to PRINCE and PRIDE. In: Advances in Cryptology—EUROCRYPT 2015, Part I. Lecture Notes in Computer Science, vol. 9056, pp. 231–253. Springer, Berlin (2015).
Even S., Mansour Y.: A construction of a cipher from a single pseudorandom permutation. In: Advances in Cryptology—ASIACRYPT’91. Lecture Notes in Computer Science, vol. 739, pp. 210–224. Springer, Berlin (1993).
Fan S., Wang X.: Primitive normal polynomials with the specified last two coefficients. Discrete Math. 309(13), 4502–4513 (2009).
Feistel H., Notz W., Smith J.: Some cryptographic techniques for machine-to-machine data communications. Proc. IEEE 63(11), 1545–1554 (1975).
Flajolet P., Sedgewick R.: Analytic Combinatorics. Cambridge University Press, Cambridge. http://algo.inria.fr/flajolet/Publications/book.pdf (2009).
Fouque P., Joux A., Mavromati C.: Multi-user collisions: applications to discrete logarithm, even-Mansour and PRINCE. In: Advances in Cryptology—ASIACRYPT 2014, Part I. Lecture Notes in Computer Science, vol. 8873, pp. 420–438. Springer, Berlin (2014).
Guo J., Peyrin T., Poschmann A., Robshaw M.J.B.: The LED block cipher. In: Cryptographic Hardware and Embedded Systems—CHES 2011. Lecture Notes in Computer Science, vol. 6917, pp. 326–341. Springer, Berlin (2011).
Harris D.G.: Critique of the related-key attack concept. Des. Codes Cryptogr. 59(1–3), 159–168 (2011).
Huczynska S.: Existence results for finite field polynomials with specified properties. In: Finite Fields and Their Applications—Character Sums and Polynomials, RSCAM, vol. 11, pp. 65–87. De Gruyter, Berlin (2013).
Jean J., Nikolic I., Peyrin T., Wang L., Wu S.: Security analysis of PRINCE. In: Fast Software Encryption—FSE 2013. Lecture Notes in Computer Science, vol. 8424, pp. 92–111. Springer, Berlin (2014).
Kara O.: Reflection cryptanalysis of some ciphers. In: Progress in Cryptology—INDOCRYPT 2008. Lecture Notes in Computer Science, vol. 5365, pp. 294–307. Springer, Berlin (2008).
Kilian J., Rogaway P.: How to protect DES against exhaustive key search (an analysis of DESX). J. Cryptol. 14(1), 17–35 (2001).
Kneževic M., Nikov V., Rombouts P.: Low-latency encryption—is “lightweight = light + wait”? In: CHES 2012. Lecture Notes in Computer Science, vol. 7428, pp. 426–446. Springer, Berlin (2012).
Nyberg K.: Differentially uniform mappings for cryptography. In: Advances in Cryptology—EUROCRYPT’93. Lecture Notes in Computer Science, vol. 765, pp. 55–64. Springer, Berlin (1993).
Soleimany H., Blondeau C., Yu X., Wu W., Nyberg K., Zhang H., Zhang L., Wang Y.: Reflection cryptanalysis of PRINCE-like ciphers. In: Fast Software Encryption—FSE 2013. Lecture Notes in Computer Science, vol. 8424, pp. 71–91. Springer, Berlin (2014).
Standaert F.X., Piret G., Rouvroy G., Quisquater J.J., Legat J.D.: ICEBERG: an involutional cipher efficient for block encryption in reconfigurable hardware. In: Fast Software Encryption—FSE 2004. Lecture Notes in Computer Science, vol. 3017, pp. 279–299. Springer, Berlin (2004).
Youssef A., Tavares S., Heys H.: A new class of substitution-permutation networks. In: Selected Areas in Cryptography—SAC’96, pp. 132–147 (1996).
Author information
Authors and Affiliations
Corresponding author
Additional information
This work has been initiated when the four authors were with DTU, Denmark.
This is one of several papers published in Designs, Codes and Cryptography comprising the “Special Issue on Coding and Cryptography”.
Rights and permissions
About this article
Cite this article
Boura, C., Canteaut, A., Knudsen, L.R. et al. Reflection ciphers. Des. Codes Cryptogr. 82, 3–25 (2017). https://doi.org/10.1007/s10623-015-0143-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-015-0143-x