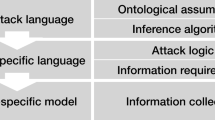
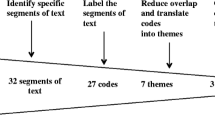
Abstract
Information technology (IT) security design and management are a major concern and substantial challenge for IT management. Today’s highly complex business and technological environments and the need to effectively communicate and justify IT security requirements and controls demand methodical support. The modeling method presented in this paper addresses this demand. The method is based on the assumption that enriched enterprise models integrating technological, business, organizational and strategic aspects provide an effective foundation for developing and managing IT security systems and facilitating communication and understanding between stakeholders. The proposed modeling method for designing and managing IT security in organizations accounts for different perspectives and is based on multi-perspective enterprise modeling. The core components of the method, based on analysis of requirements at different levels of abstraction, are: modeling language concepts specifically designed to address security issues, process models that guide the use of the resulting language, and a modeling environment. The method facilitates elaborate representations of the various aspects of IT security at different levels of abstraction and covers the entire lifecycle of IT security systems. It not only supports multi-perspective requirement analysis and design but also enables monitoring and analysis of IT security at runtime. The presented artifact is evaluated with recourse to a research method that enables the configuration of multi-criteria justification procedures.












Similar content being viewed by others
References
Accorsi R, Wonnemann C, Dochow S (2011) SWAT: a security workflow analysis toolkit for reliably secure process-aware information systems. In: Sixth international conference on availability, reliability and security (ARES), pp 692–697
Agrawal A, Finnie G, Krishnan P (2010) A general framework to measure organizational risk during information systems evolution and its customization. J Res Pract Inf Technol 42(1):37–60
Atkinson C, Kühne T (2008) Reducing accidental complexity in domain models. SoSyM 7(3):345–359
Baskerville R (1993) Information systems security design methods: implications for information systems development. ACM Comput Surv 25(4):375–414. doi:10.1145/162124.162127
Birch DGW, McEvoy NA (1992) Risk analysis for information systems. J Inf Technol 7:44–53
Bishop M (2003) What is computer security? IEEE Secur Privacy Mag 1(1):67–69. doi:10.1109/MSECP.2003.1176998
Blair G, Bencomo N, France RB (2009) Models@ run.time. Computer 42(10):22–27. doi:10.1109/MC.2009.326
BSI (2011) BSI elementary threats catalogue. https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Grundschutz/download/threats_catalogue.pdf?__blob=publicationFile. Accessed 12 Mar 2013
Caralli RA, Stevens JF, Young LR, Wilson WR (2007) The OCTAVE Allegro Guidebook, v1. 0, Software Engineering Institute
Clark T, Sammut P, Willans J (2008) Applied metamodelling: a foundation for language driven development
COBIT (2007) cobit control practices: guidance to achieve control objectives for successful IT governance, IT Governance Institute, 2nd edn. Isaca, IL
den Braber F, Hogganvik I, Lund MS, Stølen K, Vraalsen F (2007) Model-based security analysis in seven steps—a guided tour to the CORAS method. BT Technol J 25(1):101–117
Devanbu PT, Stubblebine S (2000) Software engineering for security: a roadmap. In: Finkelstein A (ed) Proceedings of the conference on the future of software engineering. ACM, New York, NY
Fabian B, Gürses S, Heisel M, Santen T, Schmidt H (2010) A comparison of security requirements engineering methods. Requir Eng 15(1):7–40. doi:10.1007/s00766-009-0092-x
Firesmith DG (2003) Common concepts underlying safety security and survivability engineering
Frank U (2006) Towards a pluralistic conception of research methods in information systems research towards a pluralistic conception in information systems research. ICB-Report
Frank U (2010) Outline of a method for designing domain-specific modelling languages. ICB-Report 42
Frank U (2011a) MEMO organization modelling language (1): focus on organizational structure. ICB-Report 48. ICB-Report
Frank U (2011b) MEMO organization modelling language (2): focus on business processes. ICB-Report 49. ICB-Report
Frank U (2011c) MEMO organizational modelling language: requirements and core diagram types. ICB-Report 47
Frank U (2011d) The MEMO meta modelling language (MML) and language architecture. ICB-Report 43. ICB-Report
Frank U (2013) Multi-perspective enterprise modeling: foundational concepts, prospects and future research challenges. Softw Syst Model. doi:10.1007/s10270-012-0273-9
Frank U (2014) Multilevel modeling. Bus Inf Syst Eng 6(6):319–337. doi:10.1007/s12599-014-0350-4
Frank U, Strecker S (2009) Beyond ERP systems: an outline of self-referential enterprise systems. Requirements, conceptual foundation and design options. ICB-Research Report 31
Frank U, Heise D, Kattenstroth H, Ferguson D, Hadar E, Waschke M (2009) ITML: a domain-specific modeling language for supporting business driven it management. In: Proceedings of the 9th workshop on domain-specific modeling (DSM) at the international conference on object oriented programming, systems, languages and applications (OOPSLA), Orlando, FL
Gaaloul K, Proper E, Charoy F (2012) An extended RBAC model for task delegation in workflow systems. In: Aalst W, Mylopoulos J, Rosemann M, Shaw MJ, Szyperski C, Niedrite L, Strazdina R, Wangler B (eds) Workshops on business informatics research, vol 106. Springer, Berlin, pp 51–63
Giorgini P, Massacci F, Mylopoulos J, Zannone N (2005) Modeling security requirements through ownership, permission and delegation. In: 13th IEEE international conference on requirements engineering
Goldstein A, Frank U (2012a) A language for multi-perspective modelling of IT security: objectives and analysis of requirements. In: Rosa M, Soffer P (eds) Business process management workshops. BPM 2012 International Workshops, Tallinn, Estonia, September 3, 2012. Revised papers, vol 132. Springer, Berlin, pp 636–648
Goldstein A, Frank U (2012b) Augmented enterprise models as a foundation for generating security-related software: requirements and prospects. In: Proceedings of the workshop on model-driven security. ACM, [S.l.]
Graumann C (1993) Perspektivität in Kognition und Sprache. SPIEL 12(2):156–172
Gulden J, Frank U (2010) MEMOCenterNG. A full-featured modeling environment for organisation modeling and model-driven software development. In: Soffer P, Proper E (eds) Information systems evolution proceedings of the CAiSE forum of the 22nd international conference on advanced information systems engineering (CAiSE’10). Selected extended papers. Springer, Berlin, pp 7–11
Habermas J (1984) The theory of communicative action. Beacon Press, Boston
Hafner M, Breu R, Agreiter B, Nowak A (2006) SECTET: an extensible framework for the realization of secure inter-organizational workflows. Internet Res 16(5):491–506
Hatfield AJ, Hipel KW (2002) Risk and systems theory. Risk Anal 22(6):1043–1057
Heidegger M (2006) Sein und Zeit, 19th edn. Niemeyer, Tübingen
ISO/IEC (2012) Common Criteria for Information Technology Security Evaluation, Version 3.1
ISO/IEC 27001 (2013) ISO/IEC 27001:2013 information technology—security techniques—information security management systems—requirements
ISO/IEC27000 (2009) Information technology—Security techniques—Information security management systems—Overview and vocabulary
ISO/IEC27005 (2008) Information technology. Security techniques. Information security risk management
ITIL (2007) ITIL service design, 1st edn. The Stationery Office, London
Jürjens J (2002) UMLsec: extending UML for secure systems development. In: UML2002—the unified modeling language. Springer, Berlin
Kant I (1998) Critique of pure reason. Cambridge University Press, Cambridge, MA
Kiczales G, Lamping J, Mendhekar A, Maeda C, Lopes C, Loingtier J, Irwin J (1997) Aspect-oriented programming. In: Aksit, Mehmet and Matsuoka, Satoshi (ed) The 11th European conference on object-oriented programming (ECOOP). Springer, Berlin
Kirchner L (2005) Cost oriented modelling of IT-landscapes: generic language concepts of a domain specific language. In: Proceedings of the workshop on enterprise modelling and information systems architectures (EMISA 2005), pp 166–179
Köhling C (2013) Entwurf einer konzeptuellen Modellierungsmethode zur Unterstützung rationaler Zielplanungsprozesse in Unternehmen. Cuvillier, Göttingen
Kokolakis SA, Demopoulos AJ, Kiountouzis EA (2000) The use of business process modelling in information systems security analysis and design. Inf Manage Comput Secur 8(3):107–116
Landin PJ (1964) The mechanical evaluation of expressions. Comput J 6(4):308–320
Lankhorst M (2005) Enterprise architecture at work. Modelling, communication, and analysis. Springer, Berlin
Lodderstedt T, Basin DA, Doser J (2002) SecureUML: a UML-based modeling language for model-driven security. In: Jézéquel J, Hußmann H, Cook S (eds) The unified modeling language, UML2002. SpringerLink [host], Berlin [etc.], pp 426–441
Luhmann N (1979) Trust and power. Two works. Wiley, Chichester
Matulevičius R, Mouratidis H, Mayer N, Dubois E, Heymans P (2012) Syntactic and semantic extensions to secure tropos to support security risk management. J Univ Comput Sci 18(6):816–844
Mayer N, Heymans P, Matulevicius R (2007) Design of a modelling language for information system security risk management. In: The 1st international conference on research challenges in information science (RCIS 2007)
McDermott JP, Fox C (1999) Using abuse case models for security requirements analysis. In: 15th annual computer security applications conference (ACSAC). IEEE Computer Society, pp 55–64
Nakamura Y, Tatsubori M, Imamura T, Ono K (2005) Model-driven security based on a web services security architecture. In: IEEE international conference on services computing, 2005. 11–15 July 2005, Orlando, FL, vol 1. IEEE Computer Society, Los Alamitos, CA [u.a.], pp 7–15
NIST (2002) Risk management guide for information technology systems
Odell JJ (1994) Power types. Object Orient Progr 7(2):8–12
Pfleeger CP, Pfleeger SL (2007) Security in computing, 4th edn. Prentice Hall, Upper Saddle River, NJ
Rodriguez A, Fernandez-Medina E, Piattini M (2006) Security requirement with a UML 2.0 profile. In: The first international conference on availability, reliability and security, 2006. (ARES 2006). IEEE Computer Society
Rorty R (1999) Philosophy and social hope. Penguin Books, New York
Schauer H (2009) Unternehmensmodellierung für das Wissensmanagement. Eine multi-perspektivische Methode zur ganzheitlichen Analyse und Planung. VDM-Verl, Müller, Saarbrücken
Scheer AW (2000) ARIS: business process modeling, 3rd edn. Springer, Berlin
Schelp J, Winter R (2006) Method engineering: Lessons learned from reference modeling. In: First international conference on design science research in information systems and technology. Claremont
Schütz A (1981) Der sinnhafte Aufbau der sozialen Welt, 2nd edn. Suhrkamp, Frankfurt am Main
Sindre G, Opdahl AL (2005) Eliciting security requirements with misuse cases. Requir Eng 10(1):34–44. doi:10.1007/s00766-004-0194-4
Strecker S, Heise D, Frank U (2011a) Prolegomena of a modelling method in support of audit risk assessment: outline of a domain-specific modelling language for internal controls and internal control systems. Enterp Model Infor Syst Arch Int J 6(3):5–24
Strecker S, Heise D, Frank U (2011b) RiskM: a multi-perspective modeling method for IT risk assessment. Inf Syst Front 13(4):595–611. doi:10.1007/s10796-010-9235-3
Strecker S, Frank U, Heise D, Kattenstroth H (2012) MetricM: a modeling method in support of the reflective design and use of performance measurement systems. Inf Syst E-Bus Manage 10(2):241–276. doi:10.1007/s10257-011-0172-6
van Lamsweerde A (2004) Elaborating security requirements by construction of intentional anti-models. In: The 26th international conference on software engineering, pp 148–157
von Solms B (2001) Information security—a multidimensional discipline. Comput Secur 20(6):504–508. doi:10.1016/S0167-4048(01)00608-3
Wollnik M (1986) Implementierung computergestützter Informationssysteme. Perspektive und Politik informationstechnologischer Gestaltung. W. de Gruyter, Berlin
Wolter C, Schaad A (2007) Modeling of task-based authorization constraints in BPMN. In: Business process management. Springer, Berlin, pp 64–79
Wolter C, Menzel M, Meinel C (2008) Modelling security goals in business processes. In: Kühne T (ed) Modellierung 2008. 12–14 März 2008 Berlin. GI, Bonn, pp 197–212
Zuccato A (2007) Holistic security management framework applied in electronic commerce. Comput Secur 26(3):256–265
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Goldstein, A., Frank, U. Components of a multi-perspective modeling method for designing and managing IT security systems. Inf Syst E-Bus Manage 14, 101–140 (2016). https://doi.org/10.1007/s10257-015-0276-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10257-015-0276-5