Abstract.
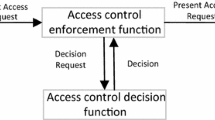
Over the years a wide variety of access control models and policies have been proposed, and almost all the models have assumed “grant the access request or deny it.” They do not provide any mechanism that enables us to bind authorization rules with required operations such as logging and encryption. We propose the notion of a “provisional action” that tells the user that his request will be authorized provided he (and/or the system) takes certain actions. The major advantage of our approach is that arbitrary actions such as cryptographic operations can all coexist in the access control policy rules. We define a fundamental authorization mechanism and then formalize a provision-based access control model. We also present algorithms and describe their algorithmic complexity. Finally, we illustrate how provisional access control policy rules can be specified effectively in practical usage scenarios.
Similar content being viewed by others
Author information
Authors and Affiliations
Additional information
Published online: 22 January 2002
Rights and permissions
About this article
Cite this article
Kudo, M. PBAC: Provision-based access control model. IJIS 1, 116–130 (2002). https://doi.org/10.1007/s102070100010
Issue Date:
DOI: https://doi.org/10.1007/s102070100010