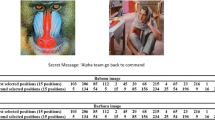
Abstract
To address the need for secure digital image transmission an algorithm that fulfils all prominent prerequisites of a steganography technique is developed. By incorporating the salient features of fractal cover images, dual-layer encryption using the standard chaotic map and DNA-hyperchaotic cryptography along with DWT-SVD embedding, key aspects like robustness, better perceptual quality and high payload capacity are targeted to build a blind colour image steganography algorithm in this work. A fractal cover image is used to hide a DNA-chaotic encrypted colour image using DWT-SVD embedding method. A two-dimensional standard chaotic map, which exhibits robust chaos for a very large range of parameter, is used to generate the pseudo-random number sequences of cryptographic qualities. One of the core novelty of the proposed method is the 2 layers chaotic encryption method to generate the DNA encrypted secret image which is finally embedded in a fractal cover image using DWT-SVD transform domain technique capable of withstanding the false positive attack. The comprehensive statistical security tests and the standard evaluation benchmarks depict that this efficient yet simple hybrid steganography algorithm is highly robust as well as sustainable against removal, geometrical, image enhancement and histogram attacks, offers better perceptual image quality and also contributes high perceptual quality of the extracted image.












Similar content being viewed by others
References
Shi Y (2022) Advances in Big Data Analytics: Theory, Algorithm and Practice, Springer, Singapore.
Olson DL, Shi Y (2007) Introduction to business data mining. McGraw-Hill/Irwin, New York
Valandar M, Ayubi P, Barani M (2017) A New Transform Domain Steganography Based on Modified Logistic Chaotic Map for Color Images. Information Security and Applications 34:142–151. https://doi.org/10.1016/j.jisa.2017.04.004
Yang L, Jindong Z (2020) A Multidimensional Chaotic Image Encryption Algorithm based on DNA Coding. Multimedia Tools and Applications 79(29–30):21579–21601. https://doi.org/10.1007/s11042-020-08880-z
Shi Y, Tian YJ, Kou G, Peng Y, Li JP (2011) Optimization based data mining: theory and applications. Springer, Berlin
Gutub A, Al-Shaarani F (2020) Efficient Implementation of Multi-image Secret Hiding Based on LSB and DWT Steganography Comparisons. Arab J Sci Eng 45:2631–2644. https://doi.org/10.1007/s13369-020-04413-w
Cheddad A, Condell J, KCurran, Kevitt PM, (2009) Digital Image Steganography: Survey and Analysis of Current Methods. Signal Process 90:727–752. https://doi.org/10.1016/j.sigpro.2009.08.010
Swain G (2019) Very High Capacity Image Steganography Technique Using Quotient Value Differencing and LSB Substitution. Arab J SciEng 44:2995–3004. https://doi.org/10.1007/s13369-018-3372-2
Tien JM (2017) Internet of things, real-time decision making, and artificial intelligence. Ann Data Sci 4(2):149–178
Zhan K, Dong W, Shi J, Yu J (2017) Cross-utilizing hyperchaotic and DNA sequences for image encryption. J Electron Imaging 26(1):013021. https://doi.org/10.1117/1.JEI.26.1.013021
Romany FM, Elsaid M (2019) A An evolutionary computing enriched RS attack resilient medical image steganography model for telemedicine applications. MultidimSyst Sign Process 30:791–814. https://doi.org/10.1007/s11045-018-0575-3
Ghada H, Marey M, Sayed S, Tolba M (2016) Comparative Study for Various DNA Based Steganography Techniques with the Essential Conclusions about the Future Research. Proceedings of IEEE, International Conference on Computer Engineering and Systems. Pp: 220–225. https://doi.org/10.1109/ICCES.2016.7822003
Patidar V, Pareek N, Purohit G (2018) A Novel Quasigroup Substitution Scheme for Chaos Based Image Encryption. Applied Nonlinear Dynamics 7(4):393–412. https://doi.org/10.5890/JAND.2018.12.007
Patidar V, Sud K (2009) A Novel Pseudo Random Bit Generator Based on Chaotic Standard Map and its Testing. Electron J Theor Phys 6(20):327–344
Durafe A, Patidar V (2020) Development and analysis of IWT-SVD and DWT-SVD steganography using fractal cover. Journal of King Saud University - Computer and Information Sciences. https://doi.org/10.1016/j.jksuci.2020.10.008
Valandar M, Barani M, Ayubi P, Aghazadeh M (2018) An integer wavelet transform image steganography method based on 3D sine chaotic map. Multimedia Tools and Applications 78:9971–9989. https://doi.org/10.1007/s11042-018-6584-2
Meena K, Menaka K, Subramanian RK (2016) Secure Message Transfer Using DNA Sequences. J Comput Intell Bioinforma 9(1):1–6
Khalifa A, Elhadad A, Hamad S (2016) Secure Blind Data Hiding into Pseudo DNA Sequences Using Playfair Ciphering and Generic Complementary Substitution. Appl Math Inf sci 10(4):1483–1492
Santoso K et al (2016) Sector based DNA information hiding method. Security and Communication Networks 9(17):4210–4226. https://doi.org/10.1002/sec.1599
Mumthas S, Lijiya, (2017) A Transform Domain Video Steganography Using RSA, Random DNA Encryption and Huffman Encoding. Procedia Computer Science 115:660–666. https://doi.org/10.1016/j.procs.2017.09.152
Anbarasi L, Jani G, Mala A, Modigari N (2015) DNA Based Multi-Secret Image Sharing. Procedia Computer Science 46:1794–1801. https://doi.org/10.1016/j.procs.2015.02.135
Halagowda S, Lakshminarayana S (2017) Image Encryption Method Based on Hybrid Fractal-Chaos Algorithm. International Journal of Intelligent Engineering and Systems.10:221–229. https://doi.org/10.22266/ijies2017.1231.24
Wu Y, Noonan JP (2012) Image Steganography Scheme Using Chaos and Fractals with the Wavelet Transform. International Journal of Innovation, Management and Technology 3:285–289
Subhedar M, Mankar V (2014) Current Status and Key Issues in Image Steganography: A Survey. Computer Science Review. I3-I4:95–113
Jero SE, Ramu P, Ramakrishnan S (2014) Discrete Wavelet Transform and Singular Value Decomposition Based ECG Steganography for Secured Patient Information Transmission. J Med Syst 38:132. https://doi.org/10.1007/s10916-014-0132-z
Singh D, Singh S (2017) DWT-SVD and DCT based robust and blind watermarking scheme for copyright protection. Multimed Tools Appl 76:13001–13024. https://doi.org/10.1007/s11042-016-3706-6
Kominek J (1995) Algorithm for Fast Fractal Image Compression, Proceedings of SPIE - The International Society for Optical Engineering. 2419
Kaur R, Singh B (2020) A hybrid algorithm for robust image steganography. MultidimSyst Sign Process. https://doi.org/10.1007/s11045-020-00725-0
Kaur G, Agarwal R, Patidar V (2020) Chaos based multiple order optical transform for 2D image encryption. Engineering Science and Tecgnology, an international journal 23:998–1014. https://doi.org/10.1016/j.jestch.2020.02.007
Naik RB, Singh U (2022) A Review on Applications of Chaotic Maps in Pseudo-Random Number Generators and Encryption. Ann Data Sci. https://doi.org/10.1007/s40745-021-00364-7
Chokri N, Guennoun ZA (2019) A Pseudo Random Bit Generator Based on a Modified Chaotic Map International Journal of Network Security 21(3):402–408. https://doi.org/10.6633/IJNS.201905
Misbahuddin M (2017) An Efficient Solution for Remote User Authentication Using DNA Crypto and Steganography. Int'l Conf. Security and Management, SAM'18. 91:399–404
Panda D, Molla K, Baig A, Swain M J, Behera A D, Dash M (2018) DNA as a digital information storage device: hope or hype? 3 Biotech, 8(5):239, https://doi.org/10.1007/s13205-018-1246-7
Ahmadi SB, Zhang BG, Wei S (2020) Robust and hybrid SVD-based image watermarking schemes: A survey. Multimedia Tools and Applications 79:1075–1117. https://doi.org/10.1007/s11042-019-08197-6
Thakral S, Manhas P (2018) Image Processing by Using Different Types of Discrete Wavelet Transform. Intl. conf. Advanced Informatics for Computing Research 499–507. https://doi.org/10.1007/978-981-13-3140-4_45
Steve JL (1996) Linear Algebra with Applications. Macmillan Publishing Company, New York
Khare P, Srivastava VK (2021) A reliable and secure image watermarking algorithm using homomorphic transform in DWT domain. Multidimension Syst Signal Process 32(1):131–160. https://doi.org/10.1007/s11045-020-00732-1
Sajjad BBA, Gongxuan Z, Songjie W (2020) Robust and hybrid SVD-based image watermarking schemes: A survey. Multimedia Tools and Applications 79(1–2):1075–1117. https://doi.org/10.1007/s11042-019-08197-6
Ahmad T, Holil M, Wibisono W, IRoyyana M ( 2013) An improved Quad and RDE-based medical data hiding method. In: International Conference on Computational Intelligence and Cybernetics (CYBERNETICSCOM) 141–145
Fu Y, Wang S (2016) A No Reference Image Quality Assessment Metric Based on Visual Perception MDPI Journal 9(4):87. https://doi.org/10.3390/a9040087
Mohammed A, Fadhil A H (2015) Image Steganography Method Preserves the Histogram Shape of Image, European Journal of Scientific Research ISSN 1450–216X / 1450–202X 130:101–106. http://www.europeanjournalofscientificresearch.com
https://csrc.nist.gov/projects/random-bit-generation/documentation-and-software
Luo T, Jiang G, Yu M, Xu H, Gao W (2018) Sparse recovery based reversible data hiding method using the human visual system. Multimedia Tools Applications 77:19027–19050. https://doi.org/10.1007/s11042-017-5356-8
Shah PD, Bichkar R (2021) Secret data modification based image steganography technique using genetic algorithm having a flexible chromosome structure. Engineering Science and Technology, an International Journal 24:782–794
Miri A, Faez K (2017) Adaptive image steganography based on transform domain via genetic algorithm. Optik (Stuttg) 145:158–168. https://doi.org/10.1016/j.ijleo.2017.07.043
Qin C, Chang C, Huang YH, Liao LT (2013) An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism. IEEE Trans Circuits Syst Video Technol 23:1109–1118. https://doi.org/10.1109/TCSVT.2012.2224052
Hamid N, Yahya A, Ahmad R B, Al-Qershi O (2012) Characteristic region based image steganography using Speeded-Up robust features technique, in: Proceedings of the 2012 International Conference on Future Communication Networks pp. 141–146. https://doi.org/10.1109/ICFCN.2012.6206858
Funding
One of us (VP) has received the MATRICS Grant (MTR/2018/000203) from the Science and Engineering Research Board (SERB), Department of Science and Technology, Government of India.
Author information
Authors and Affiliations
Contributions
Have made a substantial contribution to the concept or design of the article; or the acquisition, analysis, or interpretation of data for the article; AND 2. Helped in drafting the article or revised it critically for important intellectual content.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Durafe, A., Patidar, V. Image Steganography Using Fractal Cover and Combined Chaos-DNA Based Encryption. Ann. Data. Sci. (2022). https://doi.org/10.1007/s40745-022-00457-x
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s40745-022-00457-x