Abstract
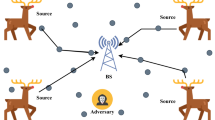
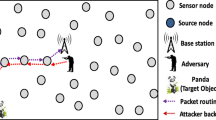
Today, communication between objects, machines, objects to machines and to humans is possible due to the Internet of Things (IoT). However, their applicability is restricted mostly to areas that are inhabited by humans. Monitoring and tracking in wilderness areas is still a challenging task to date, if not impossible. To bridge this gap, IoT networks are instrumented with Wireless Sensor Networks that are capable of providing remote services through multi-hop communication paradigm. Since these networks are deployed in deserted places, it becomes very crucial to protect the privacy of the location information of critical events or sources that these networks are monitoring. To this end, we propose a new random-walk based routing protocol namely BLS (Backward walk, L-walk, Shortest path walk) to protect the location of critical sources/events. The aim is to break the correlations between the network traffic and render the traffic-analysis efforts of the attacker, in locating the source of information, useless. In addition, we also evaluate the performance of the proposed technique by comparing it with the existing techniques using different privacy metrics such as safety period, entropy and capture ratio. Through this research work, we observed that the performance of source location privacy (SLP) preservation techniques is giving differing results for different privacy metrics. Although the proposed solution outperforms in terms of entropy metric by 104.59-folds improvements compared to Forward Random Walk technique, its performance in terms of safety period and capture ratio metrics are very poor with an improvement of just 0.65-folds and 0.1-fold respectively. Therefore, there is a dire need to come up with a right choice of metric for SLP preservation techniques.




Similar content being viewed by others
References
Kang, J. J., Yang, W., Dermody, G., Ghasemian, M., Adibi, S., & Haskell-Dowland, P. (2020). No soldiers left behind: An iot-based low-power military mobile health system design. IEEE Access, 8, 201498–201515.
“Smart parks protects endangered species with lorawan.” https://blog.semtech.com/smart-parks-protects-endangered-species-with-lorawan. Accessed: 2020-07-12
Qadri, Y. A., Nauman, A., Zikria, Y. B., Vasilakos, A. V., & Kim, S. W. (2020). The future of healthcare internet of things: A survey of emerging technologies. IEEE Communications Surveys and Tutorials, 22(2), 1121–1167.
“Smart parks protects endangered species with lorawan. ” https://lora-alliance.org/. Accessed: 2021-01-18
Conti, M., Willemsen, J., & Crispo, B. (2013). Providing source location privacy in wireless sensor networks: A survey. IEEE Communications Surveys and Tutorials, 15(3), 1238–1280.
Deng, J., Han, R., & Mishra, S. (2006). Decorrelating wireless sensor network traffic to inhibit traffic analysis attacks. Pervasive and Mobile Computing, 2(2), 159–186.
Li, N., Zhang, N., Das, S. K., & Thuraisingham, B. (2009). Privacy preservation in wireless sensor networks: A state-of-the-art survey. Ad Hoc Networks, 7(8), 1501–1514.
Ozturk, C., Zhang, Y., & Trappe, W. (2004). Source-location privacy in energy-constrained sensor network routing. In Proceedings of the 2nd ACM workshop on Security of ad hoc and sensor networks (pp. 88–93). ACM.
Wagner, I., & Eckhoff, D. (2018). Technical privacy metrics: A systematic survey. ACM Computing Surveys (CSUR), 51(3), 1–38.
Laikin, J. F., Bradbury, M., Gu, C., & Leeke, M. (2016). Towards fake sources for source location privacy in wireless sensor networks with multiple sources. In 2016 IEEE international conference on communication systems (ICCS) (pp. 1–6). IEEE.
Ozturk, C., Zhang, Y., Trappe, W., & Ott, M. (2004). Source-location privacy for networks of energy-constrained sensors. In Second IEEE workshop on software technologies for future embedded and ubiquitous systems, proceedings (Vol. 2004, pp. 68–72).
Wang, W. P., Chen, L., & Wang, J. (2008). A source-location privacy protocol in wsn based on locational angle. IEEE International Conference on Communications, 2008, 1630–1634.
Chen, H., & Lou, W. (2015). On protecting end-to-end location privacy against local eavesdropper in wireless sensor networks. Pervasive and Mobile Computing, 16, 36–50.
Raja, M., & Datta, R. (2018). An enhanced source location privacy protection technique for wireless sensor networks using randomized routes. IETE Journal of Research, 64(6), 764–776.
Han, G., Wang, H., Guizani, M., Chan, S., & Zhang, W. (2018). Kclp: A k-means cluster-based location privacy protection scheme in wsns for iot. IEEE Wireless Communications, 25(6), 84–90.
Al-Mistarihi, M. F., Tanash, I. M., Yaseen, F. S., & Darabkh, K. A. (2020). Protecting source location privacy in a clustered wireless sensor networks against local eavesdroppers. Mobile Networks and Applications, 25(1), 42–54.
Singh, P. K., Agarwal, A., Nakum, G., Rawat, D. B., & Nandi, S. (2020). Mpfslp: Masqueraded probabilistic flooding for source-location privacy in vanets. IEEE Transactions on Vehicular Technology, 69(10), 11383–11393.
Gamage, S., & Samarabandu, J. (2020). Deep learning methods in network intrusion detection: A survey and an objective comparison. Journal of Network and Computer Applications, 169, 102767.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Koduru, T., Manjula, R. Source location privacy in wireless sensor networks: What is the right choice of privacy metric?. Wireless Netw 29, 1891–1898 (2023). https://doi.org/10.1007/s11276-023-03237-4
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-023-03237-4