Abstract
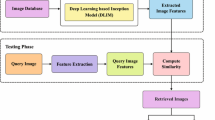
Content-based image retrieval (CBIR) uses image content features to search and retrieve digital images from a large database. A variety of visual feature extraction techniques have been employed to implement the searching purpose. Due to the computation time requirement, some good algorithms are not been used. The retrieval performance of a content-based image retrieval system crucially depends on the feature representation and similarity measurements. The ultimate aim of the proposed method is to provide an efficient algorithm to deal with the above mentioned problem definition. Here the deep belief network (DBN) method of deep learning is used to extract the features and classification and is an emerging research area, because of the generation of large volume of data. The proposed method is tested through simulation in comparison and the results show a huge positive deviation towards its performance.
















Similar content being viewed by others
References
Lew, M.S., Sebe, N., Djeraba, C., Jain, R.: Content-based multimedia information retrieval: State of the art and challenges. ACM Trans. Multimed. Comput. Commun. Appl. 2(1), 1–19 (2006)
Bringer, J., Chabanne, H., Patey, A.: Privacy-preserving biometric identification using secure multiparty computation: an overview and recent trends. IEEE Signal Process. Mag. 30(2), 42–52 (2013)
Aghasaryan, A., Bouzid, M., Kostadinov, D., Kothari, M., Nandi, A.: On the use of LSH for privacy preserving personalization. In: Proceedings of the 12th IEEE International Conference Trust, Security, Privacy in Computing and Communications (TrustCom). pp. 362–371 (2013)
Fanti, G., Finiasz, M., Ramchandran, K.: One-way private media search on public databases: the role of signal processing. IEEE Signal Process. Mag. 30(2), 53–61 (2013)
Acar, G., et al.: FPDetective: dusting the web for fingerprinters. In: Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security (CCS), pp. 1129–1140 (2013)
Balsa, E., Troncoso, C., Diaz, C.: OB-PWS: Obfuscation-based private web search. In: Proceedings of the IEEE Symposium on Security and Privacy, pp. 491–505 (2012)
Erkin, Z.: Protection and retrieval of encrypted multimedia content: when cryptography meets signal processing. EURASIP J. Inf. Secur. 2007, 20 (2007)
Lagendijk, R.L., Erkin, Z., Barni, M.: Encrypted signal processing for privacy protection: conveying the utility of homomorphic encryption and multiparty computation. IEEE Signal Process. Mag. 30(1), 82–105 (2013)
Shashank, J., Kowshik, P., Srinathan, K., Jawahar, C.V.: Private content based image retrieval. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 1–8 (2008)
Sabbu, P.R., Ganugula, U., Kannan, S., Bezawada, B.: An oblivious image retrieval protocol. In: Proceedings of the IEEE International Workshops of Advanced Information Networking and Applications (WAINA), pp. 349–354 (2011)
Erkin, Z., Franz, M., Guajardo, J., Katzenbeisser, S., Lagendijk, I., Toft, T.: Privacy-preserving face recognition. In: Proceedings of the 9th International Symposium on Privacy Enhancing Technologies (PETS), pp. 235–253 (2009)
Sadeghi, A.-R, Schneider, T., Wehrenberg, I.: Efficient privacy- preserving face recognition. In: Proceedings of the 12th International Conference on Information Security and Cryptology (ICISC), pp. 229–244 (2009)
Osadchy, M., Pinkas, B., Jarrous, A., Moskovich, B.: SCiFI—a system for secure face identification. In: Proceedings of the IEEE Symposium on Security and Privacy (SP), pp. 239–254 (2010)
Barni, M., Failla, P., Lazzeretti, R., Sadeghi, A., Schneider, T.: Privacy-preserving ECG classification with branching programs and neural networks. IEEE Trans. Inf. Forensics Secur. 6(2), 452–468 (2011)
Hsu, C.-Y., Lu, C.-S., Pei, S.-C.: Image feature extraction in encrypted domain with privacy-preserving SIFT. IEEE Trans. Image Process. 21(11), 4593–4607 (2012)
Annamalai, R., Srikanth, J.: Integrity and privacy sustenance of shared large scale images in the cloud by ring signature. Int. J. Comput. Appl. 114(12), 13–18 (2015)
Agrawal, R., Srikant, R.: Privacy-preserving data mining. In: Proceedings of the ACM SIGMOD International Conference on the Management of Data, pp. 439–450 (2000)
Duchi, J.C., Jordan, M.I., Wainwright, M.J.: Advances in Neural Information Processing Systems 25. Privacy aware learning, pp. 1430–1438. Curran Associates, Red Hook (2012)
Rane, S., Boufounos, P.T.: Privacy-preserving nearest neighbor methods: comparing signals without revealing them. IEEE Signal Process. Mag. 30(2), 18–28 (2013)
Lu, W., Swaminathan, A., Varna, A.L., Wu, M.: Enabling search over encrypted multimedia databases. In: Proceedings of the SPIE, Media Forensics and Security, vol. 7254, pp. 725418-1–725418-11, (2009)
Hoiem, D., Sukthankar, R., Schneiderman, H., Huston, L.: Object-based image retrieval using the statistical structure of images? In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition, (2004)
Xue, B., Wanjun, L.: Research of Image Retrieval Based on Color. In: Proceedings of the IEEE International Forum on Computer Science-Technology and Applications, pp. 283–286 (2009)
Huang, Z.C., Chan, P.P.K., Ng, W.W.Y., Yeung, D.S.: Content-based image retrieval using color moment and Gabor texture feature, in Proceedings the IEEE Ninth International Conference on Machine Learning and Cybernetics, Qingdao. pp. 719-724 (2010)
Lu, W., Varna, A.L., Swaminathan, A., Wu, M.: Secure image retrieval through feature protection. In: Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, (ICASSP). pp. 1533–1536 (2009)
Annamalai, R., Srikanth, J.: Accessing the data efficiently using prediction of dynamic data algorithm. Int. J. Comput. Appl. 116(22), 39–42 (2015)
Andoni, A., Indyk, P.: Near-optimal hashing algorithms for approx- imate nearest neighbor in high dimensions. Commun. ACM 51(1), 117–122 (2008)
Boufounos, P., Rane, S.: Secure binary embeddings for privacy pre- serving nearest neighbors. In: Proceedings of the IEEE International Workshop on Information Forensics and Security, (WIFS), pp. 1–6 (2011)
Gasarch, W.: A Survey on Private Information Retrieval, in Bulletin of the EATCS, vol. 82, pp. 72–107. EATCS, Rio (2004)
Ostrovsky, R., Skeith, W.E.: A survey of single-database private information retrieval: techniques and applications. In: Proceedings of the 10th International Conference on the Practice and Theory in Public-Key Cryptography, pp. 393–411 (2007)
Danezis, G., Gürses, S.: A critical review of 10 years of privacy technology. In: Proceedings of the 4th Surveillance and Society Conference, (2010)
Weinzaepfel, P., Jégou, H., Perez, P.: Reconstructing an image from its local descriptors. In: Proceedings of the IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR), pp. 337–344 (2011)
Khelifi, F., Jiang, J.: Perceptual image hashing based on virtual watermark detection. IEEE Trans. Image Process. 19(4), 981–994 (2010)
Özer, H., Sankur, B., Memon, N., Anarim, E.: Perceptual audio hashing functions. EURASIP J. Appl. Signal Process. 2005, 1780–1793 (2005)
Varna, A.L., Wu, M.: Modeling and analysis of correlated binary fin- gerprints for content identification. IEEE Trans. Inf. Forensics Secur. 6(3), 1146–1159 (2011)
Cano, P., Batlle, E., Kalker, T., Haitsma, J.: A review of audio fingerprinting. J. VLSI Signal Process. Syst. 41(3), 271–284 (2005)
Andoni, A., Indyk, P.: Near-optimal hashing algorithms for approximate nearest neighbor in high dimensions. In: Proceedings of the 47th Annual IEEE Symposium on Foundations of Computer Science (FOCS), pp. 459–468 (2006)
Yan, S., Xu, D., Zhang, B., Zhang, H.-J., Yang, Q., Lin, S.: Graph embedding and extensions: a general framework for dimensionality reduction. IEEE Trans. Pattern Anal. Mach. Intell. 29(1), 40–51 (2007)
Mu, Y., Shen, J., Yan, S.: Weakly-supervised hashing in kernel space. In: Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 3344–3351 (2010)
Cao, L., Li, Z., Mu, Y., Chang, S.-F.: Submodular video hashing: a unified framework towards video pooling and indexing. In: Proceedings of the 20th ACM International Conference on Multimedia, pp. 299–308 (2012)
Lv, Q., Josephson, W., Wang, Z., Charikar, M., Li, K.: Multi-probe LSH: Efficient indexing for high-dimensional similarity search. In: Proceedings of the 33rd International Conference on Very Large Data Bases (VLDB), pp. 950–961 (2007)
Joly, A., Buisson, O.: “A posteriori multi-probe locality sensitive hashing,” in Proc. 16th ACM Int. Conf. Multimedia. pp. 209–218 (2008)
Zhang, W., Gao, K., Zhang, Y.-D., Li, J.-T.: Data-oriented locality sensitive hashing. In: Proceedings of the ACM International Conference on Multimedia, pp. 1131–1134 (2010)
Hinton, G.E., Osindero, S., Teh, Y.-W.: A fast learning algorithm for deep belief nets. Neural Comput. 18(7), 1527–1554 (2006)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Saritha, R.R., Paul, V. & Kumar, P.G. Content based image retrieval using deep learning process. Cluster Comput 22 (Suppl 2), 4187–4200 (2019). https://doi.org/10.1007/s10586-018-1731-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-018-1731-0