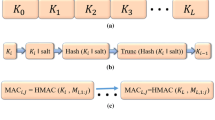
Abstract
Physical layer security has emerged as a promising approach to strengthen security of wireless communications. Particularly, extracting secret keys from channel randomness has attracted an increasing interest from both academic and industrial research groups. In this paper, we present a complete implantation of a secret key generation (SKG) protocol which is compliant with existing widespread Radio Access Technologies. This protocol performs the quantization of the channel state information, then information reconciliation and privacy amplification. We also propose an innovative algorithm to reduce the correlation between quantized channel coefficients that significantly improves the reliability and the resilience of the complete SKG scheme. Finally we assess the performance of our protocol by evaluating the quality of secret keys generated in various propagation environments from real single sense LTE signals, and real single and dual sense WiFi signals.




















Similar content being viewed by others
References
ZEIT, Wie Merkels Handy abgehört werden konnte. Available: http://www.zeit.de/digital/datenschutz/2014-12/umts-verschluesselung-umgehen-angela-merkel-handy 18 Dec 2014.
Ccc-Tv, SS7map: mapping vulnerability of the international mobile roaming infrastructure, [En ligne]. Available: https://media.ccc.de/v/31c3_-_6531_-_en_-_saal_6_-_201412272300_-_ss7map_mapping_vulnerability_of_the_international_mobile_roaming_infrastructure_-_laurent_ghigonis_-_alexandre_de_oliveira#video.
I. Surveillance, Rayzone-piranha-lte-imsi-catcher, [En ligne]. Available: https://insidersurveillance.com/rayzone-piranha-lte-imsi-catcher/.
T. intercept, The Great SIM Heist, Hows Spies kept the key of the Encrypton Castle, [En ligne]. Available: https://firstlook.org/theintercept/2015/02/19/great-sim-heist/.
Wallace, J., & Sharma, R. (2010). Automatic secret keys from reciprocal MIMO Wireless channels: measurement and analysis. IEEE Transactions on Information Forensics and Security, 5(3), 381–392.
He H. D. X. (2013). Is link signature dependable for Wireless Security?. In Proceeding IEEE INFOCOM, pp. 200–204.
Maurer, U., & Wolf, S. (2003). Secret-key agreement over unauthenticated public channels. II. Privacy amplification. IEEE Transactions on Information Theory, 49(14), 839–851.
Dodis, Y., Reyzin, L., & Smith, A. (2004). Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In C. Cachin & J. L. Camenisch (Eds.), Advances in Cryptology—EUROCRYPT. Lecture notes in computer science (Vol. 3027, pp. 523–540). Springer-Verlag.
Bennett, C., Brassard, G., Crepeau, C., & Maurer, U. (1995). Generalized privacy amplification. IEEE Transactions on Information Theory, 41(6), 1915–1923.
National Institute of Standards and Technology Special Publication 800-22 revision 1a. (2010). A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications.
National Institute of Standards and Technology Special Publication 800-90B (Second DRAFT). (2016). Recommendation for the Entropy Sources Used for Random Bit Generation.
Hamburg, M., Kocher, P., & Marson, M. E. (2012). Analysis of Intel’s Ivy Bridge Digital Random Number Generator. Technical Report Cryptographic research INC.
Hamburg, M., Kocher, P., & Marson, M. E. (2012). Analysis of Intel’s Ivy Bridge Digital Random Number Generator.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kameni Ngassa, C.L., Molière, R., Delaveau, F. et al. Secret key generation scheme from WiFi and LTE reference signals. Analog Integr Circ Sig Process 91, 277–292 (2017). https://doi.org/10.1007/s10470-017-0941-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10470-017-0941-3