Abstract
This paper studies the operating characteristics of an MX/Hk/1 queueing system under multiple vacation policy. It is assumed that the server goes for vacation as soon as the system becomes empty. When he returns from a vacation and there is one or more customers waiting in the queue, he serves these customers until the system becomes empty again, otherwise goes for another vacation. The breakdown and repair times of the server are assumed to follow a negative exponential distribution. By using a generating function, we derive various performance indices. The approximate formulas for the probability distribution of the waiting time of the customers in the system by using the maximum entropy principle (MEP) are obtained. This approach is accurate enough for practical purposes and is a useful method for solving complex queueing systems. The sensitivity analysis is carried out by taking a numerical illustration.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Background
Server vacation models are useful for queueing systems in which the server wants to utilize his idle time for different purposes. The vacation mechanism considered in this paper is termed as ‘multiple vacation policy’. That is, the server upon returning from a vacation leaves immediately for another one if the system is empty at that moment. Applications of the server with multiple vacation models can be found in manufacturing systems, designing of computer and communication systems, etc. Queueing systems with multiple server vacations have attracted the attention of numerous researchers. Baba (1986) studied batch-arrival MX/G/1 queueing systems with multiple vacations. A discrete-time Geo/G/1 queue with multiple vacations was studied by Tian and Zhang (2002). An MX/G(a,b)/1 queue with multiple vacations including closedown time has been studied by Arumuganathan and Jeykumar (2004). Kumar and Madheswari (2005) analyzed a Markovian queue with two heterogeneous servers and multiple vacations. By using the matrix geometric method, they derived the stationary queue length distribution and mean system size. Wu and Takagi (2006) investigated an M/G/1 queue with multiple vacations and exhaustive service discipline such that the server works with different rates rather than completely stopping the service during vacation. Ke (2007) studied an MX/G/1 queueing system under a variant vacation policy where the server takes at most j vacations. He derived the system size distribution as well as waiting time distribution in the queue. Ke and Chang (2009) considered an MX/(G1,G2)/1 retrial queue with general retrial times, where the server provides two phases of heterogeneous service to all customers under Bernoulli vacation schedules. They constructed the mathematical model and derived the steady-state distribution of the server state and the number of customers in the system/orbit. Ke et al. (2009) studied the vacation policy for a finite buffer M/M/c queueing system with an un-reliable server. Threshold N-policy for an MX/H2/1 queueing system with an un-reliable server and vacations was studied by Sharma (2010). Moreover, Singh et al. (2012) investigated an M/G/1 queueing model with vacation and used the generating function method for obtaining various performance measures. Very recently, an un-reliable bulk queue with state-dependent arrival rates was examined by Singh et al. (2013).
Queueing models with an un-reliable server under multiple vacation policy are more realistic representation of the systems. The service of the components may be interrupted when the operator encounters unpredicted breakdowns, and it is to be immediately recovered with a random time. When the repair is completed, the server immediately returns for service. Wang et al. (1999) extended Wang's model to the N-policy for an M/H2/1 queueing system and focused on single-arrival Erlangian service time queueing model with an un-reliable server. Wang et al. (2004) considered an M/Hk/1 queueing system with a removable and un-reliable server under N-policy and presented the optimal operating policy. Wang (2004) considered an M/G/1 queue with an un-reliable server and second optional service. Using the supplementary variable method, he obtained transient and steady-state solutions for both queueing and reliability measures of interest. Ke (2005) studied a modified T vacation policy for an M/G/1 queueing system where an un-reliable server may take at most J vacations repeatedly until at least one customer appears in the queue upon returning from vacation, and the server needs a startup time before starting each of his service periods. Li et al. (2007) proposed a single-server vacation queue with two policies, working vacation and service interruption. Choudhury and Deka (2008) studied an M/G/1 retrial queue with an additional second phase of optional service subject to breakdowns occurring randomly at any instant while serving the customers. Further, Wang and Xu (2009) obtained the solution of an M/G/1 queue with second optional service and server breakdown using the method of functional analysis. The work on an M/G/1 queue with second optional service and server breakdown has been done by Choudhury and Tadj (2009). They derived the Laplace-Stieltjes transform of busy period distribution and waiting time distribution. Further, an un-reliable server queue with multi-optional services and multi-optional vacations was analyzed by Jain et al. (2013).
Approximate results of many complex queueing models have been developed by several authors by applying the technique of maximum entropy principle. Jain and Singh (2000) used the principle of maximum entropy to analyze the optimal flow control of a G/G/c finite capacity queue. Jain and Dhakad (2003) provided the steady-state queue size distribution of an MX/G/1 queue using the maximum entropy approach in which the constraints are expressed in terms of mean arrival rates, mean service rates, and mean number of customers in the system. Further, Ke and Lin (2006) employed the principle of maximum entropy to derive the approximate formulas for the steady-state probability distributions of the queue length. Ke and Lin (2008) suggested the maximum entropy principle to examine the MX/G/1 queueing system in different frameworks. Omey and Gulck (2008) did maximum entropy analysis of an MX/M/1 queueing model with multiple vacations and server breakdowns. Wang and Huang (2009) analyzed a single removable and un-reliable server M/G/1 queue under the (p,N)-policy. They did the maximum entropy analysis to obtain the approximate formulas for the probability distributions of the number of customers and the expected waiting time in the system. Maximum entropy approach has been applied for an un-reliable server vacation queueing model by Jain et al. (2012).
The main objective of our study is to develop an MX/Hk/1 queueing model with an un-reliable server under multiple vacation policy. In this paper, an MX/Hk/1 queue has been analyzed including more features, namely (1) bulk arrival, (2) server breakdown, and (3) multiple vacation. The various approximate results for waiting time distribution have been analyzed using the maximum entropy principle which was not considered in the previous study. Now, we cite a real-life situation of a given model wherein all the features are encountered simultaneously. To highlight the application, we cite an example of production of heat transfer equipment. In the production of these equipment, the raw material of these equipment arrives in group (batch arrival). The production of these equipment has been done by the machine in phases (called k-type hyper-exponential distribution). During the production, the production of the equipment may be interrupted due to some machinery faults called server breakdown. After interruption in the service, the machine is immediately sent for repairing. After repairing, the machine renews and works as a new one. As the raw material of these equipment is finished, the operator may take multiple vacations till the raw material arrives again. More realistic assumptions incorporated in our model provide a new dimension in the area of queueing systems.
Our main objective of this paper is to develop an MX/Hk/1 queueing model with an un-reliable server under multiple vacation policy. Further, we intend to determine the approximate results for the steady-state probability distributions of the queue length using the maximum entropy approach. The rest of the paper is organized as follows. In the ‘Model description’ section, we describe the model and construct the steady-state equations governing the model. Afterwards, in the ‘Probability generating function’ section, we obtain the queue size distribution by using the probability generating function technique. In the ‘Performance measures’ section, we derive various performance indices. The principle of maximum entropy is described in the ‘Maximum entropy principle’ section to establish the approximate results for the expected system size and expected waiting time. In the ‘Numerical illustration and sensitivity analysis’ section, numerical illustrations and sensitivity analysis are presented to validate the analytical results. Finally, conclusion has been drawn in the ‘Conclusion’ section.
Model description
Consider a single un-reliable, removable server queue with state-dependent rates. We assume that the states of the system are described by the triplet (i,j,n), where i = 0, 1,…, k; j = V, B, D; and n = 0, 1, 2,…. Here i = 0 denotes that the customer is not in service, and i = 1, 2,…, k denotes that the customer is in the i th phase service; j = V, B, D represents that the server is on vacation, busy, and under repair after failure, respectively; and n denotes the number of customers present in the system. The service time is assumed to follow the k-type hyper-exponential distribution. It is assumed that μ i (i = 1, 2,…, k) is the service rate of i th phase service. Let the probability that the next customer to enter in the service is of type i be q i (i = 1, 2,…, k) and Other assumptions made to construct the mathematical model are as follows:
-
The customers arrive in batches according to the Poisson process with state-dependent arrival rate λ j given by
-
Let A be the random variable denoting the batch size, and then the batch size distribution is given by
-
Furthermore, the generating function for the batch size distribution is . It follows that E(A) = A′(1) and E[A(A − 1)] = A″(1).
-
When the breakdown occurs, the server is unable to render service to the customers, but after completing repair provided by a repairman, it works as efficiently as before the failure. The life time and repair time of the server are negative exponentially distributed with mean 1/α and 1/β, respectively.
-
The customers are served according to the first come, first served (FCFS) discipline.
Let us denote the steady-state probabilities depicting the system status as follows:
-
P0,V(n): Probability that there are n (n = 0, 1,…) customers in the system and the server is on vacation.
-
Pi,B(n): Probability that there are n (n = 1, 2,…) customers in the system and the customer in service is in phase i (i = 1, 2,…, k), when the server is turned on and is in busy state.
-
Pi,D(n): Probability that there are n (n = 1, 2,…) customers in the system and the customer in service is in phase i (i = 1, 2,…, k), when the server is turned on and is in a breakdown state.
The steady-state equations governing the model are given as follows:
Probability generating function
In this section, we present the probability generating function (PGF) technique to obtain the analytical solution of Equations 1 to 6. Let us define the following partial generating functions:
Lemma 1. The expressions for the partial generating functions are obtained as follows:
where
Proof. For proof, see ‘Proof of Lemma 1’ in the Appendix.
Lemma 2. The probability P 0,V (0) is
Also, the stability condition is given by
Proof. For proof, see ‘Proof of Lemma 2’ in the Appendix.
Theorem 1. The probability generating function of the number of customers in the system is given by
Proof. For proof, see ‘Proof of Theorem 1’ in the Appendix.
Performance measures
In order to predict the system characteristics under variant circumstances, it is worthwhile to explore key aspects by establishing analytical formulae. In this section, some performance measures in terms of steady-state probabilities are obtained. The long-run probabilities of the server being on vacation, busy, and breakdown are denoted by P V , P B , and P D , respectively. Thus, we obtain
Theorem 2. The expected number of customers in the system (L N ) is given by
where
Proof. For proof, see ‘Proof of Theorem 2’ in the Appendix.
Maximum entropy principle
Exact probabilities of the system states of an MX/Hk/1 queueing system with multiple vacations and an un-reliable server have not been found earlier to the best information of the authors. In order to evaluate approximate results for the steady-state probabilities, we employ the maximum entropy approach. It is well established that the principle of maximum entropy can be used for estimating probabilistic information measures which is further used to obtain the queue size distribution of various complex queueing systems in different frameworks. In order to obtain the steady-state probabilities P 0,V (n), P i,B (n), and P i,D (n) by using the principle of maximum entropy, we formulate the maximum entropy model as follows.
The maximum entropy model
Following El-Affendi and Kouvatsos (1983), the entropy function y can be mathematically formulated as
subject to the following constraints:
-
1.
Normalizing condition
(21) -
2.
The probability that the server being busy
(22) -
3.
The probability that the server is in a breakdown state
(23) -
4.
The expected number of customers in the system
(24)
where A i = G i,B (1), E i = G i,D (1), (1 ≤ i ≤ k), and L N are given by Equations 17, 18, and 19, respectively.
After introducing Lagrange's multipliers corresponding to constraints (21) to (24), we construct Lagrange's function as
where θ1, η i (1 ≤ i ≤ k) and ξ i (1 ≤ i ≤ k + 1) are Lagrange's multipliers corresponding to constraints (21) to (24), respectively.
The maximum entropy analysis
The maximum entropy results are obtained by taking the partial derivatives of y w.r.t. P 0,V (n), P i,B (n), and P i,D (n) and equating to zero. Thus, we get
From Equations 26 to 28, we get
Denote
Then, Equations 29 to 31 can be written as
On substituting the values of P 0,V (n), P i,B (n), and P i,D (n) from Equations 32 to 34 into Equations 21 to 23, we obtain
It follows from Equations 35 to 37 that
where
On substituting the values of φ1, ψ i and δ i (1 ≤ i ≤ k) from Equations 38 to 40 into Equation 24 and after doing some algebraic manipulations, we obtain
On substituting the values of φ1, ψ i , andδ i from Equations 38 to 40 into Equations 32 to 34 and using Equation 40, we finally get
The expected waiting time in the system
Let denote the exact and the expected waiting time in the system, respectively. Then,
where λ eff = [λ0P V + λ1P B + λ2P D ]E[A].
Following the work of Wang et al. (2007), the approximate expected waiting time in the system is given by the approximate expected waiting time in
Substituting the values of P0,V(n), Pi,B(n) and Pi,D(n) from Equations 42 to 44 into Equation 46, the approximate expected waiting time in the system is given by
Numerical illustration and sensitivity analysis
In this section, we present a numerical simulation by taking the illustration of production of heat transfer equipment (HTE) discussed in the ‘Background’ section. For developing the code of computational program, we have used the ‘MATLAB’ software. For computation purposes, we assume that the raw materials arrive in batches of fixed batch size k = 3. The arrival rates are chosen as λ1 = 0.5, λ2 = 0.9, and λ3 = 0.7. The service times of the machine when producing these equipment are μ1 = 1, μ2 = 2, and μ3 = 3. The processing of the equipment may be interrupted with rate α = 0.8 and again becomes available for processing with rate β = 2. Further, the server may go for multiple vacations with rate v = 0.09. The expected number of these equipment in the system is obtained by using Equations 1 to 19 as L N = 36.
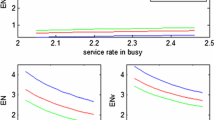
Now, we present the numerical results to demonstrate the effects of different parameters on various performance indices. The accuracy of numerical results is examined by comparing the exact waiting time (W S ) obtained in the ‘Maximum entropy principle’ section using the probability generating function approach with the approximate waiting time () obtained by the maximum entropy principle (MEP) of the MX/HK/1 queueing system under multiple vacation policy. Relative percentage error is tabulated for this purpose. The variations of different parameters on the average queue length are shown in Figures 1 and 2 graphically.
Table 1 summarizes the numerical results for long-run fraction of time of the server being in different states by varying the parameters λ, μ, α, β, and v for two different cases of q i (case 1: (q1, q2, q3) = (0.6, 0.3, 0.1) and case 2: (q1, q2, q3) = (0.7, 0.2, 0.1)). For the sake of convenience, we choose the default parameters λ1 = 0.9, λ2 = 0.8, λ3 = 0.7, μ = 1, μ1 = 1 μ, μ2 = 2 μ, μ3 = 3 μ, α = 0.2, β = 1, and v = 0.9. It is noticed that P V shows a decreasing trend with respect to the increasing values of λ, α, and v, but an increasing trend has been found with other parameters for both cases. Similarly, P B and P D increase as we increase the values of λ, α, and v and decrease with increasing values of μ and β for both cases. Table 2 presents the comparison between W S and for case 1: (q1, q2, q3) = (0.5, 0.1, 0.4) and case 2: (q1, q2, q3) = (0.4, 0.3, 0.3). We fix default parameters for numerical results summarized in Table 2 as λ1 = 0.8, λ2 = 0.7, λ3 = 0.6, μ = 1, μ1 = 1 μ, μ2 = 2 μ, μ3 = 3 μ, α = 0.2, β = 3, and v = 0.01. For both cases, W S increases as we increase the values of λ1 and α but decreases with increasing values of λ0, μ, β, and v. As we increase the values of λ1, μ, β, and v, it is seen that decreases but increases with λ0 and α for both cases. It can be observed easily from Table 2 that the relative percentage error varies from 0 % to 3 % which is reasonably less.
Figure 1a,b,c depicts the effect of different parameters on average queue length for various sets of heterogeneous arrival rate (λ0 = 1.8λ, λ1 = 0.5λ, λ2 = 0.6λ) shown by discrete lines and homogeneous arrival rate (λ0 = λ1 = λ2 = λ) shown by continuous lines. We observe that the average queue length is higher for the heterogeneous arrival rate in comparison to the homogeneous arrival rate on increasing the breakdown rate of the server. The queue length shows a gradual decreasing trend on increasing the repair rate and the vacation rate. Further, Figure 2a,b,c visualizes the effect of batch size on the average queue length. It is observed that the average queue length reveals an increasing trend with increasing values of α and β while shows a decreasing trend with increasing values of v. The tractability of numerical results shows that our model can be easily implemented for the quantitative assessment of the performance of many real-time congestion systems.
Methods
In this paper, an MX/Hk/1 queue under multiple vacations and an un-reliable server with varying arrival rates is studied. The probability generating function technique is used to determine various performance measures in explicit form. Then, MEP is further employed to compare the approximate results with exact results. For validating the analytical results, the sensitivity analysis is also carried out.
Results and discussion
The role of queueing analysis based on MEP lies in the fact that it helps basically system designers and managers to take decisions based on the performance indices determined using the probability distribution of the system size in terms of available information by MEP approach. The numerical illustration presented demonstrates that maximum entropy analysis is a simple approach to deal with complex scenarios for real-life congestion situations and can be easily applied to complex queueing scenarios for which performance measures are not easily obtained by using a classical approach. Based on the numerical experiment and sensitivity analysis carried out, we overall conclude that the comparative analysis of approximate results with exact results has demonstrated that the results obtained by MEP are reasonably good. The average queue length is higher for heterogeneous arrival rate in comparison to homogeneous arrival rate. The trends are more perceptible for larger batch size, which is quite obvious as the congestion increases significantly if the batch size of arriving customers is large.
Conclusion
In this paper, an MX/Hk/1 queue with multiple vacations and an un-reliable server has been studied in order to facilitate various performance indices in explicit form by using an analytical approach based on the generating function method and maximum entropy principle. The incorporation of some more realistic features such as multiple vacations, un-reliable server, and batch arrival makes our model closer to real-life congestion situations. This model depicts many real-time embedded systems, namely production system, computer system, data communication system, etc. The numerical results and sensitivity analysis obtained provide an insight into how the system can be made more efficient by controlling the sensitive parameters. The queueing model studied can be further extended by taking the concept of k-phase optional repair. The concept of working vacation, N-policy, and multi-repair can also be included which is the topic of our future research work.
Appendix
Proof of Lemma 1
Multiplying Equation 1 by appropriate powers of z and then summing over n, we get
Substituting in Equation 48, we have
Multiplying Equation 2 by q i z, Equation 3 by z2, and Equation 4 by zn+1 and then adding these equations term by term for all possible values of n, finally, we obtain
After multiplying Equation 5 by z and Equation 6 by zn and then adding these equations term by term for all possible values of n, thus, we obtain
Using Equation 51, we have
Now put i = 1 in Equation 50 and using Equation 52 into Equation 50, we have
Again put i = 2 in Equation 50 and using Equation 52 into Equation 50, we obtain
Similarly, repeating this process for i = k, we get
We use Cramer's rule to solve Equations 53 to 55. Now we get
Proof of Lemma 2
Using Lemma 1, we obtain
where
The L-Hospital rule has been applied to compute the above results.
To determine P0,V(0), we use the normalizing condition given by
On substituting the values of G0,V(1), Gi,B(1), and Gi,D(1) from Equations 57 to 59 into Equation 60, we obtain the value of P0,V(0).
For finding the result of the stable condition, we use the condition
Using Equation 13 into Equation 61, we have
After some algebraic manipulations, Equation 62 provides the result given in Equation 14.
Proof of Theorem 1
In order to prove Equation 15, we have
On substituting the values of G0,V(z), Gi,B(z), and Gi,D(z) from Lemma 1 into Equation 63, we get Equation 15.
Proof of Theorem 2
The average system size is computed using
The L-Hospital rule is applied twice to compute the results given in Equation 19.
References
Arumuganathan R, Jeykumar S: Analysis of bulk queue with multiple vacations and closedown times. Int J Inform Manage Sci 2004,15(1):45–60.
Baba Y: On the MX/G/1 queue with vacation time. Oper Res Lett 1986, 5: 93–98. 10.1016/0167-6377(86)90110-0
Choudhury G, Deka K: An M/G/1 retrial queueing system with two phases of service subject to server breakdown and repair. Perf Eval 2008,65(10):714–724. 10.1016/j.peva.2008.04.004
Choudhury G, Tadj L: An M/G/1 queue with two phases of service subject to the server breakdown and delayed repair. Appl Math Comp 2009,33(6):2699–2709.
El-Affendi MA, Kouvatsos DD: A maximum entropy analysis of the M/G/1 and G/M/1 queueing systems at equilibrium. Acto Info 1983, 19: 339–355. 10.1007/BF00290731
Jain M, Dhakad MJ: Queueing distribution Mx/G/1 model using principle of maximum entropy. J Dec Math Sci 2003,8(1–3):37–44.
Jain M, Sharma GC, Sharma R: Maximum entropy approach for un-reliable server vacation queueing model with optional bulk service. JKAU: Eng Sci 2012,23(2):89–113.
Jain M, Sharma GC, Sharma R: Unreliable server M/G/1 queue with multi-optional services and multi-optional vacations. Int J Math Oper Res 2013,5(2):145–169. 10.1504/IJMOR.2013.052458
Jain M, Singh M: Diffusion process for optimal flow control of G/G/c finite capacity queue. J MACT 2000, 33: 80–88.
Ke JC, Chang FM: MX/(G 1 , G 2 )/1 retrial queue under Bernoulli vacation schedules with general repeated attempts and starting failures. Appl Math Model 2009,32(4):443–458.
Ke JC: Modified T vacation policy for an M/G/1 queueing system with unreliable server and startup. Appl Math Model 2005, 41: 1267–1277.
Ke JC: Operating characteristic analysis on the MX/G/1 system with variant vacation policy and balking. Appl Math Model 2007,31(7):1321–1337. 10.1016/j.apm.2006.02.012
Ke JC, Lin CH: Maximum entropy solutions for batch-arrival with an un-reliable server and delaying vacations. Appl Math Comp 2006,183(2):1328–1340. 10.1016/j.amc.2006.05.174
Ke JC, Lin CH: Maximum entropy approach for batch-arrival queue under N policy with an un-reliable server and single vacation. Comp Appl Math 2008,221(1):1–15. 10.1016/j.cam.2007.10.001
Ke JC, Lin CH, Yang JY, Zhang ZG: Optimal (d, c) vacation policy for a finite buffer M/M/c queue with unreliable servers and repairs. Appl Math Model 2009,33(10):3949–3962. 10.1016/j.apm.2009.01.008
Kumar BK, Madheswari SP: An M/M/2 queueing system with heterogeneous servers and multiple vacations. Math Comp Model 2005,41(13):1415–1429. 10.1016/j.mcm.2005.02.002
Li JH, Tian NS, Ma ZY: Performance analysis of GI/M/1 queue with working vacations. Oper Res Lett 2007,35(5):595–600. 10.1016/j.orl.2006.12.007
Omey E, Gulck SV: Maximum entropy analysis of the MX/M/1 queueing system with multiple vacation and server breakdowns. Comp Indus Eng 2008,54(4):1078–1086. 10.1016/j.cie.2007.10.019
Sharma R: Threshold N-policy for MX/H 2 /1 queueing system with un-reliable server and vacations. J Int Acd Phy Sci 2010, 14: 1–11.
Singh CJ, Jain M, Kumar B: Analysis of M/G/1 queueing model with state dependent arrival and vacation. J Indus Eng Int 2012,8(2):1–8.
Singh CJ, Jain M, Kumar B: Analysis of unreliable bulk queue with state dependent arrival. J Indus Eng Int 2013,9(21):1–9.
Tian N, Zhang ZG: The discrete-time GI/Geo/1 queue with multiple vacations. Queue Sys 2002,40(3):283–294. 10.1023/A:1014711529740
Wang J: An M/G/1 queue with second optional service and server breakdowns. Comp Math Appl 2004,47(10–11):1713–1723.
Wang KH, Chan MC, Ke JC: Maximum entropy analysis of Mx/M/1 queueing system with multiple vacations and server breakdowns. Comp Indus Eng 2007, 52: 192–202. 10.1016/j.cie.2006.11.005
Wang KH, Chang KW, Sivazlian BD: Optimal control of a removable and non-reliable in an infinite and a finite M/H 2 /1 queueing system. Appl Math Model 1999, 23: 651–666. 10.1016/S0307-904X(99)00002-5
Wang KH, Huang KB: A maximum entropy approach for the p, N-policy M/G/1 queue with removable and unreliable server. Appl Math Model 2009,33(4):2024–2034. 10.1016/j.apm.2008.05.007
Wang KH, Kao HT, Chen G: Optimal management of a removable and non-reliable server in an infinite and a finite M/H k /1 queueing system. Qual Tech Quant Mang 2004,1(2):325–339.
Wang WL, Xu GQ: The well-posedness of an M/G/1 queue with second optional service and server breakdown. Comp Math Appl 2009,57(5):729–739. 10.1016/j.camwa.2008.09.038
Wu DA, Takagi H: An M/G/1 queues with multiple working vacations and exhaustive service discipline. Perf Eval 2006,63(7):654–681. 10.1016/j.peva.2005.05.005
Acknowledgements
The authors are thankful to the learned referee and editor for their valuable comments and suggestions for the improvement of the paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Competing interests
The authors declare that they have no competing interests.
Authors’ contributions
MJ has worked on MX/Hk/1 queueing system under multiple vacation policy. Various performance indices including queue size using generating function and the approximate formulas for waiting time of the customers using the maximum entropy principle have been obtained by RS. GC has performed numerical results by taking an illustration.
Authors’ original submitted files for images
Below are the links to the authors’ original submitted files for images.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License ( https://creativecommons.org/licenses/by/2.0 ), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Jain, M., Sharma, R. & Sharma, G.C. Multiple vacation policy for MX/Hk/1 queue with un-reliable server. J Ind Eng Int 9, 36 (2013). https://doi.org/10.1186/2251-712X-9-36
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/2251-712X-9-36