Abstract
Memristive oscillator systems are common models for many problems in physics, engineering, and systems biology. This paper presents a convergence analysis of two types of algorithms for solving a fourth-order memristive oscillator system. For the first algorithm, a parallel algorithm, a limiting state of the iterate sequence generated by a Jacobi iterative scheme and the Euler polygonal method, is a solution of the system under some weaker conditions. With the second algorithm, a partial difference method, which is based on the partial difference concept and exponential convergence, is also presented. The proposed algorithms in this paper can be applied to general nonlinear hybrid systems.
Similar content being viewed by others
1 Introduction
Recently, a large number of applications for memristive oscillator systems have been reported, including nonvolatile memristor memories, digital and analog circuits; see [1–10]. The models of memristive oscillator systems suggest possible responses of simple intelligences in biomimetics as well as new approaches for bio-inspired reconfigurable circuits. Considerable attention has been devoted to the theoretical properties of memristive oscillator systems, and their relationship to memristor dynamics (see [1–4, 6, 9, 10] and references therein). A very lower dimensional memristor equation can appear with complex double-loop behavior. Therefore, the memristive system is a complicated system that has strongly nonlinear behavior, as it includes the switched network cluster and shows a high uncertainty [11]. Deep studies of the memristive system are important in various applications due to the important guiding role in memristor-based physical commercially available devices. For example, nonlinear dynamics has been shown to play an important role in the understanding of a wide spectrum of memristor-based technological and biological systems [1–4, 6, 9–11].
In this paper, we consider a fourth-order memristive oscillator system described by the following differential equations:
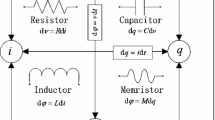
where and denote voltages, and represent capacitors, is a memductance function, and , , R, and L are magnetic flux, current, resistor, and inductor, respectively.
Using the mathematical model of a piecewise-linear memristor [3, 4], the memductance function is characterized by
where and are parameters.
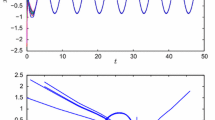
Choose parameters , , , , , , and set the initial condition , , , ; we can see that system (1) indeed generates chaotic behavior. Simulated results are depicted in Figures 1 and 2. Figure 1 displays the projections of the chaotic attractor of system (1) in the three-dimensional space. To get a better view of this chaotic attractor, Figure 2 shows the projections of the chaotic attractor of system (1) in the two-dimensional space.
To solve the state-dependent nonlinearity of system (1), fuzzy logic has attracted much attention as a powerful tool. The memristive oscillator system (1) can be represented as the following fuzzy model:
Rule 1: If , then
Rule 2: If , then
With a center-average defuzzier, the over-fuzzy system in (3) and (4) is represented as
where
Notwithstanding the vast literature on nonlinear dynamical systems, the majority of the existing studies focus on memristive oscillator systems whose inner mechanisms have never been thoroughly studied and expounded. This can mainly be attributed to the memristor nonlinearity. One such challenge in the memristive system is a state-dependent nonlinear network cluster [11]. As a result, the monitoring, control, and optimization in memristive systems will be extremely difficult.
An important research problem is to develop some rigorous algorithm theories and design tactics for solving memristive oscillator systems. Algorithm theories represent the structure common to a class of algorithms, which can provide the basis for designing tactics-specialized methods for analyzing memristive oscillator systems. The memristive differential system which is described by a state-dependent nonlinear network cluster presents a difficulty in numerical integration, since the conventional processing approaches make it hard to achieve satisfactory results. In general, solving these problems requires overcoming a number of theoretically challenging issues and even developing entirely new analytical methods. A key open problem is how to devise effective algorithms for dealing with the characteristics of memristive system. Generally, to the best of our knowledge, no relevant work as regards the algorithms and their convergence for memristive oscillator systems has been reported.
The objective of this paper is to develop some algorithms and analyze their corresponding convergence properties. This consideration does not only have theoretical value but also practical meaning. For the numerical solution of complex systems and networks, of the many methods available, a parallel algorithm and a partial difference method show good feasibility and advantages. Thus, these two algorithms are chosen for memristive oscillator systems. The constructive proofs in this paper are able to fully demonstrate that the parallel algorithm and the partial difference method have a general applicability that can make them popular in a wide variety of cases. We believe the basic algorithm and convergence in theory for memristive systems should be a significant research topic due to the potential in a variety of emerging applications.
2 Parallel algorithm
In this section, we give a constructive proof on the parallel algorithm and its convergence for system (1).
By the theories of differential inclusions and set-valued maps, from (5), it follows that
where denotes a closure of the convex hull generated by real numbers and .
Transform (6) into the compact form as follows:
where the vector ,
In (7), split the matrix A into matrices B and C, i.e., , where
Obviously, according to the Jacobi iterative scheme,
where , , is a constant.
Let , , denote , , and applying the Euler polygonal method, by (8), it follows that
then
where I is the identity matrix.
Through the first equation of (10),
where matrix . Besides, for (11), if the matrix is invertible, then is the general inverse matrix, otherwise is the generalized inverse matrix.
Substitute (11) into the second equation of (10),
where the matrix . Therefore, we get
On the other hand, by (11),
thus
through using the method of induction, and then
In fact, it is not difficult to find that
Clearly, by the iterative scheme (17), we can draw the conclusion of Theorem 1.
Theorem 1 If , then the iterative scheme (17) is convergent, i.e., (17) converges to a fixed state, where denotes spectral radius of the matrix F.
Theorem 2 If , then the iterative scheme (17) is convergent, i.e., (17) converges to a fixed state, where denotes the norm of the matrix F.
Proof Since , according to Theorem 1, it follows that Theorem 2 holds. □
Theorem 3 The fixed state of iterative scheme (17) is the solution of system (1).
Proof When , take the limit of (8), then
thus , which satisfies (1). □
3 Partial difference method
In this section, we present a constructive proof to illustrate the partial difference method and the related convergence analysis for system (1).
Through the theories of the Taylor formula and the partial difference method, from (5), it follows that
where is a constant.
Equations (19)-(22) are a generic form of a first-order partial difference method for system (5). When , (19)-(22) are said to be the forward partial difference method for system (5). When , (19)-(22) are said to be the backward partial difference method for system (5).
In the following, we consider the convergence of the first-order partial difference method for system (5).
By (19)-(22), we obtain
Transform (23)-(26) into the compact form as follows:
then we have
where
Let
where denotes the closure of the convex hull generated by the real numbers and .
Obviously, by the iterative scheme (28), we can draw the conclusions of Theorems 4 and 5.
Theorem 4 If , and the eigenvalues of only correspond to the elementary divisors of the matrix , then the iterative scheme (28) is convergent, i.e., (28) converges to a fixed state, where and denote the spectral radius and matrix module of , respectively.
Theorem 5 If , then the iterative scheme (28) is convergent, i.e., (28) converges to a fixed state, where denotes spectral radius of the matrix .
Theorem 6 If , then the iterative scheme (28) is convergent, i.e., (28) converges to a fixed state, where denotes the norm of the matrix .
Proof Since , according to Theorem 5, it follows that Theorem 6 holds. □
Remark 1 In fact, in Theorems 5 and 6, according to the theory of stability for discrete dynamical systems, we find that the iterative scheme (28) is exponentially convergent when or .
4 Conclusion
The area of memristive oscillator systems is ripe with open problems and challenges, and more exploratory analyses will encourage and motivate researchers to enter this exciting field of research. In this paper, we investigate the convergence analysis of two types of algorithms for solving a class of memristive oscillator systems. Some preliminary results have been shown. We hope that such theoretical analysis in this area will contribute to further ignition of interest and promotion of multi-discipline studies.
References
Bao BC, Liu Z, Xu JP: Steady periodic memristor oscillator with transient chaotic behaviours. Electron. Lett. 2010, 46(3):237–238.
Corinto F, Ascoli A, Gilli M: Nonlinear dynamics of memristor oscillators. IEEE Trans. Circuits Syst. I, Regul. Pap. 2011, 58(6):1323–1336.
Itoh M, Chua LO: Memristor oscillators. Int. J. Bifurc. Chaos 2008, 18(11):3183–3206. 10.1142/S0218127408022354
Muthuswamy B, Kokate PP: Memristor based chaotic circuits. IETE Tech. Rev. 2009, 26(6):417–429. 10.4103/0256-4602.57827
Riaza R: First order mem-circuits: modeling, nonlinear oscillations and bifurcation. IEEE Trans. Circuits Syst. I, Regul. Pap. 2013, 60(6):1570–1583.
Sun JW, Shen Y, Yin Q, Xu CJ: Compound synchronization of four memristor chaotic oscillator systems and secure communication. Chaos 2013., 23(1): Article ID 013140
Talukdar A, Radwan AG, Salama KN: Generalized model for memristor-based Wien family oscillators. Microelectron. J. 2011, 42(9):1032–1038. 10.1016/j.mejo.2011.07.001
Talukdar A, Radwan AG, Salama KN: Non linear dynamics of memristor based 3rd order oscillatory system. Microelectron. J. 2012, 43(3):169–175. 10.1016/j.mejo.2011.12.012
Wu AL: Hyperchaos synchronization of memristor oscillator system via combination scheme. Adv. Differ. Equ. 2014., 2014: Article ID 86
Wu AL, Zhang J: Compound synchronization of fourth-order memristor oscillator. Adv. Differ. Equ. 2014., 2014: Article ID 100
Wu AL, Zeng ZG, Xiao J: Dynamic evolution evoked by external inputs in memristor-based wavelet neural networks with different memductance functions. Adv. Differ. Equ. 2013., 2013: Article ID 258
Acknowledgements
The work is supported by the Natural Science Foundation of China under Grant 61304057, the Project funded by China Postdoctoral Science Foundation under Grant 2014M550495, the Postdoctoral Research Program of Shaanxi Province of China, the Research Program of College of Arts and Science of Hubei Normal University under Grant Ky201302.
Author information
Authors and Affiliations
Corresponding author
Additional information
Competing interests
The authors declare that they have no competing interests.
Authors’ contributions
All the authors contributed equally to this work. They all read and approved the final version of the manuscript.
Authors’ original submitted files for images
Below are the links to the authors’ original submitted files for images.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 2.0 International License (https://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
About this article
Cite this article
Wu, A., Fu, CJ. Convergence analysis of algorithms for memristive oscillator system. Adv Differ Equ 2014, 160 (2014). https://doi.org/10.1186/1687-1847-2014-160
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/1687-1847-2014-160