Abstract
By now the 5-step risk and chance management process according to the generic ISO 31000 standard has been applied to a wide range of domains including organizational risk management, business continuity, safety and IT security management, as well as occupational safety. The paper motivates the context and need for an open, scalable and flexible urban (perceived) security and safety assessment and improvement process, showing that it should be applicable also at local community level. The basic ideas of the process include the division of risk and chance analysis and management (treatment) into defined phases which are addressed iteratively: (1) within a framing context, stakeholders and their objectives are identified; (2) chance events for reaching objectives or, as often more straightforward, risk events opposing objectives are identified; (3) these chances and risks on objectives are quantified in terms of probability and consequences on the identified objectives; (4) they are assessed regarding their context-sensitive societal acceptability; (5) improvement measures are selected and implemented. The process is iterated until all risks on objectives are sufficiently controlled, also the combination of risks. Concerning the methodology, a semi-formal modelling of the static and dynamic requirements of a tailored process based on ISO 31000 is provided, which in addition allows the formulation of minimum consistency and completeness requirements, e.g. for each objective at least one stakeholder and risk should be identified. For the urban domain, a classification of risk assessment techniques regarding their suitability for supporting the process is presented. A further focus is the efficient provision of best practice options for urban security enhancement. Based on the insights gained by the systematic modelling of the risk management process, a software tool was developed to facilitate the application of the process in participatory settings like round table discussions with stakeholders. The paper presents as use case the application of the tool-supported methodology in several discussion rounds within a residential district in a medium sized university town in Germany along with the discussion of the evaluations and findings. Thus, the applicability of the software-supported urban security risk management to the novel urban security domain is demonstrated. In summary, the approach is sufficiently transparent and flexible for fast summaries of round table discussions up to complex iterative decision and participatory scenarios, which have to consider multiple stakeholders and a large variety of possible urban security and safety enhancement options with a given urban context.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction: Motivation for an Open and Flexible Urban Security and Safety Improvement Process
With the rapid development of societies and economies and the acceleration of urbanization processes, urban areas expand rapidly as well as the urban population share (Leeson 2018). The task of city management is increasingly demanding. During the last decades major interest was allocated in improving the ability to deal with uncertain and specific negative impacts at the organizational level. Under the headline of “risk management”, this has led to the development of numerous techniques, processes and methodologies as well as application tools as observed already by Raz and Hillson (2005). However, even if increasingly standardized, only some of the processes seem suitable for urban risk management since existing standards focus more on technical, organizational, economic and organizational risk management, typically in business contexts.
Such approaches are not implemented as participative societal decision making but rather aim at compliancy, auditability and regulatory sound solutions. Nevertheless, they helped resolving social problems of consumers and neighbors, e.g., by improving safety and quality of products as well as occupational safety of citizens and employees. In addition, gradual improvement management often cannot meet the needs of the new situations of cities. The question arises if tailored simplified classical risk management is applicable to assess the safety and security of public spaces and if in particular this can be supported by a software tool.
Ball and Ball-King (2013) discuss safety management in particular for public spaces and ask for a more balanced risk management approach to avoid public misunderstandings. According to them, much improved urban risk assessment and management processes and methods are required that allow an integrated approach focusing on safety and security objectives. Also, it should take account of all risks, analyze and assess them. Decision making should be facilitated, which is suitable for overall risk control and resilience improvement of urban spaces, and the selection of countermeasures and improvement measures should be supported. This can be used as a list of requirements for the application of risk management to the urban domain.
Safety management aims at considering multiple objectives, challenges (issues) and improvement measures. This has to be contrasted with the assessment of selected intended improvement measures. There was already done a lot of work with a special focus, e.g. by Furlong et al. (1997) with a focus on problems of teens and young adults. Farrington and Welsh (2008) investigated the effect of street lighting.
The general aim to maintain or enhance urban security and safety seems to be, at least at abstract level, much less debatable when compared to competing aims of vivid urban societal and economic development. Example risk events for the former are ranging from minor asocial activities and minor crime like loud gatherings of young citizens, littering, alcohol-related events such as fighting, to wild graffiti, pocket theft, transport interruptions due to blocking (of transport routes, of doors), up to potential violence crime. However, terroristic attacks are not part of considerations at such level. The latter aims include economic success, social diversity, vivid street live (dance of the street), truly public spaces (spaces for all citizens), gender equality and social, economic and educational low barrier access to the public domain as well as last but not least the green, sustainable and resilient city. Hence, risk management of minor perceived safety and security events up to major events in urban spaces has to consider the named overarching and competing aims. In addition, safety and security incidents, in particular when considering major rare events, are rare or disruptive events that do not occur as the standard case. Furthermore, the main functionality or use of urban spaces and infrastructure and intended other objectives, as well as framing constraints need to be considered. Hence, in this article we aim at showing that the presented risk management for urban safety and security can consider such rich competing aims and contexts, at least as a contextual framing.
Based on similar arguments, within the complex urban context, the decision has to be taken very carefully regarding what safety and security level is societally acceptable and what to do to maintain or improve it. Even more demanding is the selection of possible best practice methods for taking up promising chances and controlling risks deemed most critical. A further demand is to determine intended as well as unintended side or secondary effects of potential measures for improvement of urban safety and security. At the same time, one should be aware that positive and negative effects on safety and security objectives may as well originate from other changing conditions. Hence, the presented approach should make explicit the decision making regarding the evaluation of risks on safety and security objectives as well as the rationale for the selection of improvement measures. This should be related to explicit acceptance criteria.
Another major need of any attempt of maintaining and improving urban safety and security on a rational decision basis is to consider that techniques and measures that proved to be successful in the past in other contexts, have to be carefully approved before being considered to be promising improvement options. Since the decision-making processes are very complex, it is a good approach to visualize the threats and measures in order to detect any interdependencies. Basu and Blanning (1994) presented a visualization tool for metagraphs supporting the decision-making process. In this paper, we present an approach and visualization method that shows the interdependencies between threats, measures and risks in order to weight the measures and to get support for a timeline (sequence) of the iterative decision-making process.
Even in the by now rather classical area of crime prevention, the selection of appropriate and validated measures is believed to need major support from an online database (CTC 2019) and processes of conducting such selections in an optimal way are still discussed (Steffen 2014). Thus, the present approach will aim at showing that the selection of improvement methods is conducted very carefully. With the approach presented it will be shown that novel threats as well as novel improvement means for all steps in the risk management process can be taken into account, since the underlying process is based on a generic standard which is per design independent from threat types and improvement measures.
A further complication of all the challenges listed above results from the observation that decisions in urban environments typically take place in very complex social systems characterized by ambiguity and hardly quantifiable goals and values (Lewis and Hartley 2001; March and Olsen 1989). Hence, in particular the chance and risk evaluation and assessment are challenged by identifying generally agreed thresholds for acceptance and acceptability. It can be stated that this also concerns the identification of the context, in particular the active inclusion of all stakeholders within the process, the security and safety objectives selection and prioritization, the risk event selection, even more their semi-quantification, as well as the winning arguments for the selection of safety and security improvement measures.
Given the listed identified major needs and challenges of urban security and safety risk analysis and management for typically minor safety and security events within scenarios in the urban public space, the question arises whether a slim, open, scalable and flexible urban security and safety assessment and improvement process can be designed that is sufficiently supported by techniques and methods within process steps, in particular for selecting best practices for the improvement of urban security and public safety. In this light the paper aims to answer the research questions whether a risk management process can be applied to urban security enhancement processes and discussions and what possible advantages can be achieved by such an approach.
This paper proposes a process (scheme of conduction, procedural model) that has been implemented in a software tool to carry out urban risk assessment and to strengthen coherence and consensus in the way policymakers plan and make decisions in current minor up to medium urban safety and security issues. The process tailors the international standard ISO 31000 (2018) on risk management to the urban application domain. The generic and seminal civil standard (level A standard) is presented and discussed, see e.g. Leitch (2010) and Purdy (2010). The aim of the paper is to show that the process contributes to a structured understanding of urban safety and security objectives and related risks on these objectives as well as chances how to better reach them. After the identification of risk events, based on a working scale of probability (likelihood) and of consequences (impact, severity), for each identified risk on objectives an expected probability and consequences can be estimated. The estimates are in the present case based on participants’ opinions and experience (stakeholder expert estimate), but could also be based on historical statistical data (e.g. number of reported risk events per year) or be based on literature results for similar application domains.
The article aims to show that the presented approach facilitates and improves collaboration across the stakeholders, i.e. citizens (e.g. neighborhood, interest groups), the private business sectors, cities, and local agencies and authorities. In such cases also national governments should be included for benchmarking, improving and expediting their own progress towards the reduction of urban risk, see for instance the recommendation for such joint approaches of The World Bank (2020). When compared to the 5Is framework (Ekblom 2008), which establishes a process model for crime prevention, the presented approach based on ISO 31000 is considered more general and also suitable for local and quarter-specific aims of safety and security.
The presented approach aims at continuous risk improvement understood from a systemic urban perspective. Its five-step approach is slim and is aimed to be applicable independent of the degree of knowledge about the standard itself, mainly through the reduction to a minimum of consistency requirements. In particular, the presented approach is different from industry or application domain specific application standards of risk management. Examples for domain specific risk management applications are the NIST SP 800-30 (2012) approach on risk management for Information Technology, the DIN EN ISO 14971 (2013) for risk assessment of medical devices, compliance management (ISO 14001:2015; ISO 19600:2014), business continuity (ISO 22301:2019), the environmental domain (ISO 14001:2015), security management of supply chains (ISO 28000:2007), and emergency and incident management (ISO 22320:2018). Risk-driven assessment standards are also under development for urban resilience (ISO/AWI 22371:2020). However, there is no application standard for risk management of urban safety and security. The presented approach aims at showing that the classical risk analysis and management approach is applicable to the urban domain.
More recently approaches on risk policy and governance level were proposed for the urban domain including societal risks (Renn et al. 2018). Also risk and resilience frameworks (Bansal et al. 2013) countering natural and man-made threats for the urban domain are available, including indicators (Khazai et al. 2015). However, such approaches are more focusing on abstract policy levels, and do not focus on minor urban safety and security issues.
This reinforces the need and expected suitability of the generic risk management approach and its applicability to socio-societal issues. The effectiveness of the process can be expected in terms of making decision making more transparent and structured. When compared to the plan-do-check-act (PDCA) or Deming cycle with a business and industry background (Deming 1998), the observe-orient-decide-act (OODA) cycle with a decision making background (Richards 2004), the prepare-detect/prevent-protect-response-recover resilience cycle with a catastrophe management (Thoma et al. 2016) or the technical resilience capabilities covering sensing, sense making/world modelling, decision making and actuation with a system engineering background as well as further resilience dimensions (Häring et al. 2016), the risk management process claims to be a generic approach applicable to all domains. Compared to the aforementioned cycles it is more analytic and less operation/action focused, in particular it has no defense background like the OODA loop.
As a further motivation for the selection of the risk management approach, in addition to the advantages mentioned above, its adaptability to the urban safety and security area will be highlighted. It will be shown how it can be tailored to the available resources for decision making and how it covers the consideration of improvement measures ranging from round tables to approaches that need more technical support, see Baumann et al. (2014) for first related results.
Related work and projects relevant for the context of the present approach include work on urban risk assessment and management in the enlarged EU in Holevas et al. (2005) and in particular research conducted within the EU project BESECURE (2019) on best practice enhancers for security in urban regions for enhancing urban security. The latter comprises works on policy design and the need for an evidence-based approach (Neef et al. 2014; Crabbe 2015), reporting on insights from a southern Italian neighborhood (Bevilacqua et al. 2015), and on methods and tools for a strategic approach to urban security (Napolano and Sperber 2016). Preliminary results similar to the present approach as obtained within BESECURE are summarized in Siebold et al. (2015). Of interest in the present context is also the more recent EU project BeSecure-FeelSecure (BSFS) of the European Forum for Urban Security (EFUS 2020), and results of the European project “Methodological tools for the definition of local security policies in Europe” (AUDITS 2020). Prior to the conduction of the case study this work, practitioners of urban security enhancement reported as feedback to a presentation of the project BESECURE (2019) that they would value the ability of structuring and documenting the results of discussion rounds in an electronic form.
Through the application case urban quarter presented within the paper, the applicability of the approach will be demonstrated. The aim is to show how end users, stakeholders and decision makers can use the tool-supported risk analysis and management approach for the urban domain to generate a semi-quantitative overview of the risks considering their context. Additionally, new secondary risks produced from the improvement measures applied to the primary risks are assessed within a second iteration of the approach. It will also be shown that the approach and its software tools support to share safety and security assessments between persons involved, facilitate documentation as well as sharing and storage of knowledge. Furthermore, that the tool-support facilities to follow a directed analytical approach.
The German city of Freiburg Vauban quarter is an interesting and challenging application case while being representative for urban quarters with minor safety and security issues. Located within the Green City Freiburg (Grießhammer and Brohmann 2015), it has a history of participative planning and is a famous example of ecological sustainable design, in particular in the domain of private and public transport (Gössling et al. 2016). This also enables children to safely move in the public domain, see e.g. Höfflin (2020). It will be seen that a broad variety of stakeholders is covered, even if the inhabitants are rather homogenous in terms of age and socio-economic distribution, i.e. typically families with higher income with teen children and early adults. For this quarter application case, the work will show which safety and security objectives are of interest by different sets of stakeholders, which risks are identified regarding these objectives and which counter measures are deemed relevant.
The article is structured as follows. Section 2 describes the overall approach we followed to formalize the risk management process, collect measures and best practices for risk mitigation in the urban context and implemented the software tool. Section 3 reports on a sample case study that applies the approach to a residential district of a popular German medium sized university town and summarizes typical steps within a successful application and tailoring of the chance and risk management process to urban security and safety enhancement. Section 4 discusses the evaluation and findings from the application of the tool. Section 5 concludes and provides a broad outlook on possible enhancements concerning the developed approach and tool as well as applying it in a moderated setting.
2 Methodology
In this section we describe our approach to conceptualize and implement the software-based risk management tool. Section 1 motivated the application of classical risk management process to the urban domain. We assumed that using a software-based tool will simplify dramatically the conduction of the risk management process. This will be achieved due to the fact that the process itself is implemented in the software and does not need heavy moderation effort. Additionally, intermediate or final results and artefacts (e.g. remarks, documents, and decisions) can be stored which allows interruptions of the process any time. The web-based approach allows in principle the usage of the tool across several locations and sharing knowledge about best practices and findings across different use cases. Finally, automatic calculations of risk levels are done in an automated way which reduces manual assessment effort.
As a first step in the development of the approach and the associated software tool, we made use of the Systems Modeling Language SysML to model a generic chance risk management process, as also described in Schoppe et al. (2013). Section 2.1 summarizes that process and gives an overview of the applied methodology for deriving and testing an urban and security and safety enhancement process based on a given semi-formal model. This concerns representing and implementing the process itself—originally described in Schoppe et al. (2013) as well as a scheme for applying it efficiently. Section 2.1 also reports on the semi-formal modelling of key requirements to be fulfilled within the process and key actions to be performed in the applied chance and risk management process. This activity served as a basis to have a domain model for the software development.
The next step, described in Sect. 2.2, concerned the overall applicability of the process to the urban domain. It also exemplarily shows how to identify a broad set of methods that support all process steps. It focuses on best practices for improving urban security and safety and how to select them in the improvement measure selection step. In particular, it addresses the pre-screening of the methods. It is emphasized that the selection of methods is not complete before their effect on chance enhancement and risk reduction is assessed in the second iteration of the process.
Section 2.3 gives an overview on the risk management tool we implemented. The software tool allows assessing safety and security of urban areas based on selected key technical properties and functionalities as derived in Sect. 2.1. It emphasizes the communicative and iterative nature of the process. The process input as well as all process steps are explained.
The aforementioned steps resulted in a software tool capable of supporting the risk management process chosen for our approach. In the subsequent Sect. 3 we will report on a use case application in the urban domain and report on the fulfilment of the above listed assumptions.
2.1 SysML Model of Generic Chance Risk Management Process
In the beginning of a domain specific application software development it is important to understand the purpose and the possible usage of the software tool. The international standard ISO 31000 (2018) served as a basis for the development of the risk management software tool Issues and Decisions: Analysis and Support (IDAS), described in Sect. 2.3.
When implementing a software, it is crucial to understand the mental model of the processes and entities the software should provide, which is a key paradigm of domain driven design. Therefore, a semi-formal model of the main process steps, related requirements and overall requirements of the ISO 31000 (2018) was generated. This section outlines the semi-formal model which was presented also in the article by Schoppe et al. (2013). The Systems Modelling Language (SysML) was chosen (Object Management Group 2012; Friedenthal et al. 2011; Weilkiens 2007) since it is capable to model all relevant aspects of the risk management process. The ISO 31000 defines risk as an effect of uncertainty on objectives, either positive or negative. For being more explicit, positive effects of uncertainty on objectives are denoted as chances.
The generated semi-formal model serves as a knowledge container of the core content provided by ISO 31000 to be transported to the software IDAS. In addition to that the SysML model formalizes defined processes in a standardized language to minimize gaps in understanding processes during communication among different teams, since SysML is also meant to be a modelling language that is not focused on software development only, but to be considered multi-disciplinary.
2.1.1 Fundamental Requirements for Risk Management
The ISO 31000 (2018) on risk management, principles and guidelines is a general standard for risk management that evolved from several national risk management standards. It provides a structural and systematic framework for a comprehensive understanding of all risks including the prioritization of the risks. Application of the risk management results in a structured approach for controlling and improving security within given scenarios. As it is a very general approach, the particular methods how to identify particular risks or how to prioritize the particular risk especially with respect to opportunities is mostly omitted and subject to IEC/ISO 31010 (2009). However, the methods are rather focusing on the technical domain and are only in case of more generic methods suited for the urban security and safety domain.
The two editions ISO 31000 (2018) and ISO 31000 (2009) present principles that should be followed to live an effective risk management process. Risk management has emerged as an important factor in management and control of decisions. The word risk applies to uncertain events, possible hazards or damages, or other undesirable consequences, which can be expressed by means of probabilities. So, risk management can be understood as a structured process to minimize or mitigate the effect of risk, or a proactive process of decision making that aims to minimize the consequence of negative future events by identifying potential risks, analyzing them and planning the response necessary for their monitoring and control (Oliveira et al. 2017).
We exploited the above-mentioned principles for effective risk management in the following way: The risk management principles served as the domain model for the software development and the analytical parts (e.g. how to derive risks) were used as functional requirements of the software development. The software IDAS will therefore be able to guide a user through the risk management process. Figure 1 shows a part of the SysML requirements diagram, which is based on the principles from ISO 31000 (2009), which was used for the initial modelling by Schoppe et al. (2013).
Excerpt of requirements diagram for principles for effective risk management as presented in Schoppe et al. (2013)
In the same manner as principles of risk management are modelled in Fig. 1, requirements for the framework of risk management can be modelled. The requirements for the risk management framework can be found in ISO 31000 (2018) and are modelled in Schoppe et al. (2013). Examples for requirements concerning the risk management framework are: the framework needs to be improved continually and the organization should implement the risk management process. In addition, specific requirements regarding the design of the framework of the risk management can be found in the ISO 31000 (2018), e.g. the organization should develop a plan how to communicate with external stakeholders.
2.1.2 Risk Management Process Model
The ISO 31000 (2018) formulates fundamental activities regarding the risk management process itself. The risk management process consists of several phases and activities inside these phases which organizations should perform. This leads to the derivation of a SysML activity diagram which is graphical representations of stepwise activities and actions. The corresponding activity diagram is depicted in Fig. 2.
In each of the five proposed phases of the risk management process, a list of requirements should be fulfilled as well as proposed activities shall be performed. Both, activities and requirements, were modelled and represented in Schoppe et al. (2013) with focus on requirements and actions relevant for urban security and safety.
The knowledge about processes, expected outcomes, single activities and methods forms the ground truth for the software development (incl. design, architecture, and implementation) of IDAS. Basically, this forms the functional skeleton to guide users through the processes and actions and allows collaboration between different stakeholders also on the software side. What is still missing is a data pool of concrete measures that help to tackle risks and adaptions of concrete techniques to apply for specific domains. This will be described in the domain of urban security in the following section.
2.2 Towards Repositories for Urban Security and Safety Assessment Methods and Best Practices
The generic risk management process based on ISO 31000 (2018) consists, apart from the process steps of establishing the context and treatment of risks, in its core of a risk assessment (or analysis), see also Fig. 3. In the urban security domain, many uncertainties are involved in the rationales that determine the prioritization of issues and the deployment of resources, which calls for a proper evidence base to support decisions.
This evidence base can be created by conducting a risk assessment for which numerous methods, techniques or tools are available. Such methods in parts support the general process described in Sect. 2. They can be used to identify objectives, potential risk events, risk (semi) quantification in terms of measures for probability and consequences, and the risk evaluation. However, they can also be much simpler than this framework (e.g. direct risk assessment) or go much beyond the approach (e.g. considering more risk assessment factors).
To elaborate on these and help a selection of appropriate methods and techniques the international standard ISO 31010 (2010) was put forward. This standard lists over 30 risk assessment techniques and describes each of them in more detail using a common schema.
Additionally, the techniques are compared according to certain criteria like the ability to produce quantitative outputs. While the ISO 31010 (2010) document takes a generic point of view, Schoppe et al. (2014) review the list of methods or techniques specifically regarding the suitability of their application in the urban security and public safety in mind. The aim is to support a proper selection of appropriate risk assessment techniques that satisfy given urban security needs. The classification of risk assessment techniques is based on criteria relevant for the urban security context. For instance, criteria can be the applicability within given constraints concerning the personnel required for implementation, expert knowledge, timeframes, (financial) resources or options of communication of methods and last but not least acceptance and acceptability of measures.
2.2.1 Classification of Risk Assessment Techniques Regarding their Suitability for Urban Security
This section addresses the classification of risk assessment techniques. Schoppe et al. (2013) employ a taxonomy for practical use in urban security that in some respects extends the classification taxonomy presented in ISO 31010 (2010).
For example, concerning the aspect of a digital workflow, they examine the availability of software that supports the application of a risk assessment technique by introducing a criterion “software”. Furthermore, Schoppe et al. (2014) estimate the effort that is needed to apply a risk assessment method in the field of urban security, specifically, the effort needed to adapt a technique to particular urban security needs. They assume that the effort strongly depends on the specificity of the technique, which relates first to the focus of the technique, and second to the type of system it is traditionally intended to be applied in.
The criterion “specificity” includes three levels: “generic”, “semi-specific” and “specific”. A method is rated “generic” if it is neither focused on a certain aspect nor intended for certain types of systems. A method is viewed as “specific” if it is focused on a certain aspect and intended for certain types of systems. A technique is presumed to be “semi-specific” if only one of the above holds, i.e. either focused on a certain aspect or intended for certain types of systems. Table 1 summarizes this approach of defining the three different levels of specificity.
Table 2 lists risk assessment methods and techniques and indicates their specificity as defined above.
To underpin their statements Schoppe et al. (2014) rely on the safety report of Luzern (Sozial- und Sicherheitsdirektion, Stadt Luzern 2013) to determine generic theoretical use cases like harassments in public areas, disturbances of the public and alcohol abuse in public areas.
Urban security and safety practitioners conducting risk assessments can benefit from the overview and a categorization of existing methods and techniques. Future work could include additional assessment methods and a refinement of the classification taxonomy with respect to specific fields in urban security e.g. crime prevention. Furthermore, the development of a software application is conceivable that supports urban security practitioners in the selection of appropriate methods and techniques, e.g. by presenting methods for selection.
2.2.2 Best Practice Repositories
There are several best practices for improving urban public security and safety in cities and procedures for how these can be selected in the countermeasure selection step, see Fig. 3. In particular, the counter measure selection step deals with the pre-selection of methods. It is important to stress that the selection of methods is not completed until the second iteration of the process assesses their impact on opportunity improvement and risk reduction. Final best practice selection and implementation is the main content of the risk treatment step.
In the EU project BESECURE (2019), for example, one aim was to improve urban security policy through the exchange of best practices that are applied throughout Europe. To achieve this, the project collected best practices from the eight quarters and cities participating in case studies namely: Belfast, The Hague, Freiburg, London (Tower Hamlets), London (Lewisham), Naples, Reggio di Calabria and Poznan. The practices were structured according to a specially developed pattern. The result was a database of best practices that can be searched to find suitable practices for a specific topic (Siebold et al. 2015).
When it comes to best practice approaches, there are many dimensions that can be relevant to the analysis of practices. The BESECURE tools provide support for decision makers on practices. It is therefore important to collect the information that is most relevant to them. During consultations and evaluation sessions with stakeholders, needs and requirements of decision makers regarding the types and terms of information on practices were identified. At this stage, only a few dimensions by which an approach can be classified where selected. The selection is based on a preliminary review of various practices found in the literature and on discussions with the case study leaders.
The dimensions that where selected correspond to the following questions (Siebold et al. 2015):
-
When will the approach be implemented and when are results expected? This refers to the time frame of the approach;
-
What is the approach? This refers to the specific nature of the approach;
-
Who is involved? This refers to the stakeholders involved in the approach.
Much beyond this way of working, there are different methods for selecting an approach and method evaluations for the different application areas. In the following, a non-exhaustive list of websites with international examples gives a short overview of best practices in the area of urban security: The “Grüne Liste Prävention” (Green List Prevention) is a German Database of recommended prevention programs (CTC 2019). A further German example is the “Wegweiser Prävention” (Guide Prevention), a joint project of the partners German Forum for Crime Prevention (short: DFK) and State Prevention Council of Lower Saxony (short: LPR NI). It points the way to prevention programs that have been tested for their effectiveness and practical suitability (DFK & LPR NI 2020).
The Canadian Best Practices Portal (Public Health Agency of Canada 2020) acts as a central contact point and provides a comprehensive collection of links to resources and solutions for planning health promotion and disease prevention programs. It also comprises violence and crime prevention. The Violence Prevention Alliance (VPA), is a network of WHO Member States, international organizations and civil society organizations promoting the prevention of violence (The Violence Prevention Alliance 2020). The National Institute of Justice's approach CrimeSolutions.gov consists of a web-based clearing house and identification and evaluation procedures of prevention programs and practices (National Institute of Justice 2020).
2.3 Urban Security Assessment and Improvement Tool
With the SysML model described in Sect. 2.1 which forms basically the domain model for the software development and the knowledge of domain specific (i.e. urban security) repositories of best practices and techniques the foundation is set for IDAS.
In this software called “Issues and Decisions: Analysis and Support (IDAS)” results of the iterative process are documented and made accessible to collaborate via a web-based application platform. IDAS supports users to address urban security issues in a systematic way and to select appropriate measures. In this section the software IDAS is introduced and its functionality is described. In the following Sect. 3 it is shown how IDAS guides stakeholders through a risk management process in an operational setting based on a case study.
2.3.1 The Risk Management Process Supported by a Software Application
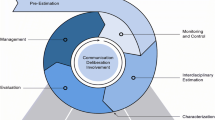
The web-based software application IDAS was developed with the aim of supporting decision makers by taking into account and answering typical questions that arise in the domain of urban security and safety (Baumann et al. 2014). Figure 3 represents the risk management process adopted by the tool, which refers to the management process of ISO 31000, each item in the web application IDAS is assigned to a step of the standard. The ISO 31000 is a general framework and a general process that has been shown to be adjustable to the particular problem (Schoppe et al. 2013).
The present approach is a chance and risk driven urban security and safety enhancement process that assumes that operational objectives can be formulated. That risks to such security and safety objectives can be identified, assessed, evaluated and mitigated, and that the overall aim is to identify, implement and monitor the most efficient mitigation measures.
The representation of the risk management process according to ISO 31000 in the web-application IDAS is illustrated in Fig. 3. The left side depicts the risk management process according to ISO 31000. The right side shows the navigation structure of the web-application IDAS. Each of the process steps correspond to a navigational item. While the steps of risk identification, analysis and evaluation are grouped under the heading risk assessment, some steps exhibit sub-items like in the case of establishing the context.
In the following, the process steps will be addressed one after the other combined with an explanation of how this step is implemented in the web-application. To illustrate the steps and the software implementation, a real but simple example of a city district will be presented in Sect. 3.
The first step in the risk management process of establishing the context is divided into three sub-steps: external context, internal context, and risk criteria. The establishment of the context frames the needs of the urban area being analyzed, as well as the relevant aspects in which risk management is performed. It is important to limit the study context in order to assess risks correctly. Some important components included in this stage are the definition of the internal and external stakeholders, the definition of the objectives to be achieved. These objectives must be linked to the risks and opportunities, the objectives to be defined must be clear, agreed and understandable for all the stakeholders. In addition, a scale of probabilities and impact will be defined.
So, the output of the first step will be: the identification of the involved stakeholders, the declaration of the objectives to be achieved, and the definition of the impact and probability scales. Concerning the important risk management element of including relevant internal and external stakeholders, for instance, police officers can be considered internal stakeholders when it comes to the issue of preventing pickpocketing at events with a large number of visitors (e.g. Christmas market, fair), since they play an active role in this issue. In this case, the visitors of a market would be considered external stakeholders.
As a further important building block of the context definition, the objectives one wants to achieve have to be determined. In a later step, these objectives are linked to risks and opportunities (chances) and represent the root of a risk identification graph. In the scope of determining the context, the application helps to define overall scales for assessing risks and opportunities, thereby addressing possible negative or positive effects on objectives. To realize this, apart from a scale for the likelihood of occurrence of risks and opportunities, their consequences are specified and measured on an impact scale. This impact scale allows a semi-quantitative comparison of the different risks and chances. The identification of stakeholders, the definition of impact scales, and the statement of objectives one wants to achieve complete the first step of the risk management process.
The term risk assessment incorporates three risk management steps, namely risk identification, risk analysis and risk evaluation. The IDAS tool can automatically propose possible risks to the previously defined objectives for the urban context based on past inputs. For consistency, for each defined objective there must be at least one identified risk. The IDAS tool allows this assignment to be carried out manually.
Next a risk assessment of the identified risks is conducted. With the scale of probabilities and impacts previously defined in the context step, the level of risk can be determined. The results are plotted in a risk matrix, which illustrates the level of risk. Acceptable risk levels should be defined in the initial steps. Based on the risk position in the matrix and color, each risk will receive a mitigation measure as needed. Each identified risk is assigned a color, which labels how to deal with the risk (e.g. mitigating, monitoring or ignoring it). The necessity to initiate measures rises from left to right and from bottom to top (see also the discussion in Sect. 4).
Control mechanisms of IDAS ensure a sufficient degree of completeness in assessing the risks, which represents a clear advantage over conventional approaches. The user can evaluate the identified and analyzed risks, which IDAS automatically places in a risk matrix. Here it becomes evident if a risk is acceptable to the user or not. The risk matrix contains all the risks (abbreviated r1, r2, etc.) that have previously been defined and assessed. Based on the position in the risk matrix and the color-coding it becomes apparent if risks need further mitigation measures. See Fig. 7 for an example of a risk matrix from our case study.
The final assessment of the risks is the risk evaluation step, which is different from the risk analysis, since it comprises a context-specific evaluation of all stakeholders based on the context framework provided in the first step.
After the risks have been assessed in the previous step, the risks classified as critical should be treated. The next step is the assignment of measures to the risks with the objective to reduce the likelihood or impact of the risk events. The first iteration of going through all the steps of the risk management process is complete when each risk that is deemed to require a mitigating measure has been linked to such a mitigation measure. This step comprises risk evaluation and risk acceptance in all cases where it is decided not to select any improvement measures for risks.
It is important to mention that the measures are evaluated regarding impact, feasibility, readiness, duration of effect, acceptance and cost. This is an approach similar as proposed in the city of Luzern’s safety report (Sozial- und Sicherheitsdirektion, Stadt Luzern 2019). See Fig. 8 for an illustration of the measure evaluation as it is realized in IDAS.
Since the implementation of new measures to the system may cause new associated risks, the tool satisfies the evaluation of these new risks through the determination of (unintended or even unexpected) secondary, and iteratively tertiary risks, etc. as obtained by a second conduction of the overall process, etc.
Figure 4 shows a risk identification graph for different objectives, associated risks, measures and secondary risks related to an example ‘security at events’. Finally, points in time can be set at which risks have to be reconsidered, re-evaluated or further measures identified, e.g. conducting the whole process every 3 months with all stakeholders.
Below the navigational items for the risk management process the IDAS tool offers the user to check the current status of the analysis offering a short summary and a quick overview of the current project. This includes both the monitored risks and a table with statistics. Also, the steps already conducted can be identified (Fig. 5).
Since the approach is aimed at continuous improvement, the risk management process is planned to be conducted in an iterative manner. This is expected to ensure that with each iteration a more realistic socio-societal (technical) systemic view is generated, risks are more realistically assessed, as well as the effects of measures. Additionally, new risks associated with the measures implemented will be evaluated in these second or third iterations. Often such implementation monitoring and adaptation is even required by the methods themselves, e.g. round table approaches for neighborhoods.
When the treatment stage is complete, the user is directed back to the risk identification stage where the second iteration of the risk management cycle begins. In this iteration, the user can identify the context and objectives changes and the secondary risks of the measures that were applied. If there are any, they are assessed and managed like the primary risks. The user has to decide if the risks need to be mitigated by measures, if they have been mitigated and should be monitored or if they remain critical, in which case the measures were not successful.
In Sect. 3 it is presented how end users, stakeholders and decision makers can apply IDAS to obtain an overview of security objectives taking account of the context, and how to identify related risks of not achieving the objectives. Within the analytical framework the risks are assessed and evaluated. For risk control the selection of measures for improving issues and their critical evaluation is strongly supported, including the iterative consideration of secondary risks.
2.3.2 Technology used for the Implementation of the Software Application
The web-application IDAS was developed based on the open source web framework ASP.NET (ASP.NET 2020) as well as the template based text generation framework T4 “Text Template Transformation Toolkit” (Microsoft 2016a). IDAS is mainly written in the programming language C#. Additionally JavaScript (Mozilla 2016) is employed for functions which affect the layout and behavior of the web-pages. To realize a web server, Internet Information Server (IIS) was chosen (Microsoft 2016b). In this way C# and HTML code can be easily combined. For some functions which affect the layout and behavior of the pages JavaScript scripts are used. The application runs on Microsoft Internet Information Server and the integrated development environment (IDE) used is Microsoft Visual Studio. For further technical details also see Baumann et al. (2014).
3 Use Case: Practical Application in an Urban Residential Area
In this section, the practical application of the IDAS approach is illustrated using the real case study of a quarter in the German city of Freiburg. The Vauban district was built on the site of a former Wehrmacht base, which was taken over by the French army after the end of the Second World War and held until its withdrawal due to German reunification in August 1992. The French name Vauban was retained for the newly created residential quarter which was built as a sustainable model district.
About one third of the population here is under 18 years old, of whom the proportion of children is again very high. This makes the district one of the richest in children in Freiburg. There is also a large number of accommodations for students and refugees.
The district was planned very well as a model district for young families with small children, but its infrastructure did not grow with its population in age. Today there is a shortage of outdoor places and activities for young people, but there are many playgrounds for children as it was originally planned for a different population structure. This leads to several problems that were examined in the study described hereafter. The district is struggling especially at night with various problems such as noise pollution from partying teenagers, vandalism, littering, and several more. This has enormous negative consequences for the residents in this quarter who mainly have condominiums and now suffer from health problems and therefore think about selling their condominiums and moving to other places.
With the help of the Fraunhofer EMI software tool IDAS the quarter council (German: Quartiersarbeit) Vauban was supported in developing a concept to counteract these problems. The procedure described in the following was applied in several meetings over a year and has proved to be successful (see Table 3). The main objectives of the study were to hand over a structured evaluation of the results to the quarter council Vauban in order to prioritize its measures. Thereby the Fraunhofer EMI experts hoped to receive useful information on the use of IDAS as a service in further projects in the future.
In a first appointment discussion, the risk management process was roughly outlined and explained to the stakeholders (including representatives of the quarter council, city officials, the youth center, police, hotel managers, and business owners). Then the objectives, risks, possible measures and secondary risks were collected in a brainstorming session and formulated moderated by the Fraunhofer EMI experts. Subsequently, the collected aspects were structured using the IDAS method and sorted according to the given categories on objectives, risks, measures and secondary risks.
Subsequently, the structuring was again discussed with the stakeholders in a discussion round moderated by the Fraunhofer EMI experts. Further questions to be answered were for example which measures concern the individual objectives or which secondary risks may arise from a certain measure. Finally, the risks and measures were assessed—first separately by the Fraunhofer EMI experts using IDAS and then again in a discussion round moderated by the EMI staff together with the various stakeholders.
Figure 6 shows the overall result of applying the IDAS risk management software via a moderated discussion in the Vauban quarter case study. The individual columns represent the outcomes of the analysis conducted in IDAS: definition of objectives, the three core risk assessment steps (risk identification, risk analysis, risk evaluation), risk treatment (finding and evaluation of measures), and identification of secondary risks. Additionally the determined connections between the elements in neighbouring columns are indicated. For instance, the connections between the elements in the two leftmost columns signify which risks have been associated with which objectives.
In the following paragraphs the outcomes of the analysis conducted in IDAS are described in more detail as well as how they were obtained.
3.1 Definition of Objectives
In the first discussion, two main objectives were formulated that should be achieved in any case, serving as main guidelines for the further actions. The first objective aims to ensure and improve security and safety in the Vauban district, and the second objective deals with the public order. As Fig. 6 shows in the left row, these two protection goals form the basis for the following analysis and conclude the definition of objectives.
3.2 Risk Assessment
On the basis of the initially roughly formulated protection goals, the resulting risks were then formulated in the course of further discussions on current experiences and problems of the city district. Nine central risks (in the following labelled r1 to r9) have been identified and were further investigated:
(r1) Night time disturbance: Young people meet in the evening at the Vauban in central places, because there are no alternatives for them to go. Even the JUKS (JUgend und KinderhauS Vauban/Youth and children's house Vauban) is not accepted by the teenagers as an alternative, because the closing times of JUKS are too early and alcohol is generally forbidden there. This leads to frequent disturbances of the peace at night, as the young people often get drunk in the streets and then start having loud conversations. This is a very serious problem for the people living there and should not be underestimated, as it can lead to residents thinking about selling their apartments (health damage due to noise peaks, financial loss).
(r2) Vandalism: Vandalism often has its cause in boredom, as teenagers find too few alternatives and mutually challenge themselves for entertainment, for example with tests of courage. Past vandalism actions included graffiti spraying, destroying telephone booths, pulling out bollards, damaging the signs of doctors' practices, and throwing paint bags at windows.
(r3) Littering: Usually fast food packaging such as pizza boxes or glass bottles are left lying around, resulting in glass fragments and risk of injury to humans, especially children and animals. Too much rubbish in the streets and public places also has a negative impact on the city image, as the district actually gives great importance to environmental protection.
(r4) Alcohol abuse: Alcohol abuse among teenagers is a general social problem. In Germany, teenagers are allowed to buy and drink wine and beer from the age of 16, stronger liquors are allowed from the age of 18 onward. The problem with alcohol abuse affects young people in particular, who do want to test or do not know their limits. In the worst case, alcohol is bought by older teenagers and passed on to underage children. Long opening hours even on weekends until 10 pm of supermarkets selling alcohol aggravate the problem.
(r5) Assault and battery: In the district, assault and physical injury cases are rare but were mainly committed by rival youth groups. Moreover, it can be assumed that the few cases where bodily injuries occurred were escalating disputes between drunken teenagers.
(r6) Aggressive teenagers: In some cases there were problems with apparently unprovoked aggressive adolescents from time to time. Experience showed that these were more rarely resident teenagers, but more often aggressors from youth groups from other districts. These non-local teenagers probably felt anonymous and thought they could act unrecognized, so they had less inhibitions to attack passers-by verbally or physically.
(r7) Inhibition to call the police: In the past, incidents such as assault and battery were not always reported to the police. Cases of lack of personal courage have also been reported where witnesses preferred to look away and not to come to help.
(r8) Reduced accessibility for police vehicles: In an emergency, police vehicles have relatively long journey times. For offenders, grass embankments in the district offer good escape and hiding places. In this way, criminal prosecution is somewhat more difficult.
(r9) Vulgar behavior/Insulting behavior: Provocative behavior by groups of young people occurs repeatedly in central squares. Individuals and weaker, older people may feel threatened.
The jointly identified risks concerning the formulated objectives were subsequently discussed in more detail and assessed with regard to their probability of occurrence and severity of damage on a five-point scale ranging from “very low” over “low”, “medium” and “high” to “very high” as shown in Table 4.
Table 4 with its entries were transferred to a classical risk matrix, depicted in Fig. 7 in the following way: The columns “occurrence probability” and “severity of damage” serve as the two dimensions of the risk matrix. The individual cells of the risk matrix are assigned to sectors of high, medium and low risk via a three-stage color coding of red, yellow and green, corresponding to the last column “Risk value” of Table 4. Risks, numbered in the first column “Risk” of Table 4 were then positioned in the according matrix cells by using only the abbreviation, e.g. r1.
Initially, we proposed a color scheme with four colors ranging from green over yellow and orange to red in the software tool. This color scheme was perceived by the end-users in the evaluation runs as an unnecessary complexity. Therefore, we reverted to a color scheme with three colors green, yellow and red.
Based on the values for probability of occurrence and severity of damage that were worked out as shown in Table 4, the derived risk matrix indicates where there is a particular need for action. Figure 7 shows a high need for action in the red sector of the risk matrix, this concerns r1 and r5.
Medium risks such as r2, r3, r4, r6, r7 and r9 can be found in the yellow medium sector. Finally, the low risk r8 is located in the green low-risk sector. The findings from the risk matrix help in selecting and prioritizing risk mitigation measures, as illustrated in the next section.
3.3 Risk Treatment
In order to treat the identified risks, the following 13 countermeasures cm1 to cm13 were jointly developed. These countermeasures were also weighted with regard to their acceptance among the surrounding population and with regard to their practicability meaning if they can be implemented immediately or need a certain preparation to set-up and how cost-intensive they are.
(cm1) Self-defense courses: This measure can be implemented by the JUKS Youth Centre. The young people would have a meaningful occupation and could use sport positively to reduce their potential for aggression. The courses are not too elaborate in preparation and implementation and could be carried out in a short time. Furthermore, they would not be too expensive.
(cm2) Teen disco (prevention event): This measure could also be implemented by the Youth Centre. The advantage would be that the young people can enjoy themselves and still be supervised. But of course, a disco also has loud music and this could be too loud for the neighbors. Another serious question was what the young people would do when the disco closes, e.g. at 11 pm. If possible, they should not stay in front of the building and be a source of noise for the neighbors, e.g. by singing or talking loudly.
(cm3) Addiction counselling: This is a very important measure for the teenagers, but it could not be performed by everyone. An addiction expert would be needed, and this could be very expensive.
(cm4) Increased police presence: This countermeasure on police presence increasement was defined as the ultima ratio, it should be the last measure that could be carried out. The district would like to solve its problems without police intervention in the first instance, so the central opinion. The aim is to calm the situation and to provide possible improvements for both the young people and the local residents.
(cm5) Information events of the police: The police can go into schools and inform about alcohol, drugs or the health consequences of too much noise, for example. In this way, an attempt could be made to create an understanding for the problems of local residents and the needs of the young persons.
(cm6) Night walkers, night walks: This measure can be performed easily. Street workers can walk with teenagers in the nights on nice paths, e.g. exploring the district. The advantage would be that the teenagers have a meaningful employment. But the risk is to create too much noise or that some teenagers would go their own ways.
(cm7) "Happy Hour" at JUKS: This measure can also be performed quite easily. The teenagers would have a nice evening with a happy hour and cheap alcohol-free drinks in the Youth Centre (JUKS). But the risk would be again the potential noise after the happy hour and progression to alcoholic drinks.
(cm8) Advertising space as information space: This measure can also be performed quite easily. Free advertising spaces like bus stations can be used to put information there on addiction counselling or maybe upcoming events for teenagers on the next evenings or weekends.
(cm9) Extended opening hours at JUKS: This measure can also be performed quite easily and would be a meaningful employment for the teenagers. But the risk again is the potential noise after the youth center closes.
(cm10) Leisure activities for young people at night: Indoor activities such as billiards or table football in the youth center can be mentioned as examples. The advantage compared to outdoor activities is to reduce the noise for the neighbors.
(cm11) Round table "Vauban by night": It is time-consuming to implement this measure, since various discussions with heterogeneous persons are needed. But if the results of the Round Table are implemented, they would persist for a long time.
(cm12) Additional waste bins: This measure is quite easy to implement. However, it requires additional costs due to the additional organizational effort that the bins are expected to be emptied more often as standard bins.
(cm13) Cleaning also at the weekend: The public spaces and waste bins etc. have to be cleaned during the weekend. This needs extra human effort and payment.
In addition, the following option was discussed: Further leisure activities for young people could be developed and possible outdoor places for young people should be found where they can meet without disturbing the residents too much, for example a half pipe for skateboards as a sportive event in a turning loop at the end of the city tram. These ideas and places should be discussed with the young people to see if they would accept them and then propose them to the City of Freiburg.
An easily understandable overall assessment per measure is usually requested by the users.
In order to support the selection of the best suited risk treatment options, the IDAS method allows to evaluate the proposed countermeasures with respect to the following six criteria: impact, feasibility, readiness, duration of effect, acceptance among the population and costs to implement them. For each of the criteria the evaluation scale ranges from “high” over “medium” to “low”. The individual criteria are combined to form a summarizing qualitative evaluation result with an associated color coding: “good” (green), “ok” (yellow) and “bad” (red). See Fig. 8 for a screenshot from IDAS concerning the evaluation of a measure. The same color coding as described above is used for depicting the individual countermeasures in the third column of the graph representing the overall results as shown in Fig. 6. To distinguish the appearance of the measures from the risks a different color hue was used for the base colors red, yellow and green.
Additionally, to the graph in Fig. 6 a compact representation concerning the evaluation of the measures and their relation to the identified risks is shown in Table 5. The tabular presentation makes the relationships between risks and countermeasures easier to determine especially for large graphs with numerous connections. The table with its columns and rows offers at a glance both the individual assessment of the risks (shown in the appropriate coloring in the second row) and the countermeasures and their evaluation results with the levels “bad”, “okay” and “good” according to Fig. 8. Fields with the symbol “- “ mean that there is no connection in the graph between the respective risk and measure signifying that the measure is not related to the risk or has no effect.
3.4 Secondary Risk Identification
Secondary risks are risks that would arise and be caused by the application of the countermeasures. In this example, as Fig. 6 shows, the most obvious secondary risk was identified as the displacement effect, i.e. the shifting of the problem to other districts. However, displacements do not only occur spatially. Other forms of displacement include variations in time, type of target or offence as well as changes in tactic. Hodgkinson et al. (2020) give a current overview over this topic. In our case study the discussion was limited to spatial displacement as an obvious example demonstrating in principle the capability of the software to account for secondary risks.
4 Discussion: Evaluation and Findings
The software tool IDAS bridges the gap between risk assessment expertise and non-experts in risk analysis. An initial usage of the tool in a moderated way is seen as useful. The tool IDAS is perceived by the (expected or designated) end users to be very scientific. E.g. the initially proposed four-stage color coding including yellow and orange as a differentiation between the two middle ranges was simplified to three stages as a feedback result from the participants of the case study since a definition of the orange and yellow meaning was very difficult. The reduction of the color scheme had the aim on the one hand to reduce complexity. On the other hand, this led to a situation that the majority of identified risks were positioned in the middle area of risk.
It was observed that the larger the amount and the more heterogeneous the stakeholders are, the greater the variation in objectives, risks and measures, but also the greater the trade-offs in the assessment of risks and measures. The time for the discussions is very important but it has to be limited, otherwise the results would be too generic.
The moderator has to remind the stakeholders very often to the initial question that has to be discussed. From a scientific point of view, this pattern of behavior follows known theories of society ("tendency towards the middle"). Hence, it would also be interesting to have the risks and measures assessed only by the individual interest groups (separated according to e.g. municipal representatives, police, and young people) and to compare them or to select one per group. A conclusion out of this can be that IDAS itself could provide time-limit hints or even hard deadlines technically implemented in the software, e.g. in form of countdowns that forces users to enter information within a limited time to avoid defocusing of discussions.
The more heterogeneous the stakeholders, the more general are the discussions and the more compromises have to be found for evaluating the measures and risks. For instance, this means that sometimes it might be difficult to agree on appropriate measures since ideally these should be marked green in their overall evaluation. In our case study roughly half of the measures are marked green. The other half is predominantly considered to be “ok” (yellow) due to compromising. But clear results at the margins indicating that a measure is “very urgent” or “not needed at all” are very rare the more heterogeneous are the members in the discussion and the wider the discussion spectrum is. And vise-versa, the more homogeneous the background of the members in the discussion is, the narrower is the discussion line and hence, the more common are also clear results at the margins. This is a well-known phenomenon.
The IDAS tool was perceived to be too complex in some aspects for a live application by the participants of the case study and the scientific staff. This might be due to the fact that the software was initially designed as a web-application for a single user but not for direct presentation in a group setting.
Possibly in the future usage of a traditional whiteboard and cards could enhance the moderated discussion process. Different colors could be used to collect objectives, risks, measures and secondary risks later to be entered into the software tool.
In summary, it turned out that it is important for the use of the IDAS method to be clear about the main objective of its application. On the one hand an expert opinion could be sought. Then the results are expected to be very specific and can also be in the red and green assessment range. Alternatively, a general opinion could be formed. Then a broad and heterogeneous survey is important and results with compromises to determine tendencies and arrive at valid majority decisions. This implies to use sufficiently broad interest groups for authoritative and acceptable decisions.
5 Summary and Conclusion
Urban security and safety are of paramount importance for the individual, social and socio-economic development of modern societies. In the past, a number of frameworks for assessing the security and safety of public spaces have been proposed and applied in various case studies. However, systematic approaches to assess and improve the risk control and resilience of public spaces, using established risk and chance management processes, have not yet been comprehensively reported. Transparent and open support for the creation of urban security and safety remains an open issue. In comparison with current methods, the most important difference to the present approach is that these are not tailored to the urban security and safety domain and are not supported by a software tool.
In this paper this gap has been closed, because it tailors the generic risk analysis and management process of ISO 31000 to the urban domain. It serves as a basis for the IDAS web application and the corresponding semi-quantitative risk and opportunity management for the assessment, resilience and improvement of urban safety with best practices. It is shown that the application of ISO 31000 provides a general framework and process that can be adapted to specific urban security and safety problems. It also provides a minimum set of rules to ensure consistency, e.g. ensuring objectives for all stakeholders, and identifying risks for all objectives.
In summary, the following steps were conducted deriving, implementing and validating the urban security and safety enhancement process:
-
(a)
Based on a thorough literature research the main needs for an open, scalable and flexible urban security and safety assessment and improvement process were identified.
-
(b)
The literature research was extended discussing the applicability and transferability of the chance and risk management process to the urban domain.
-
(c)
Semi-formal modelling of static and dynamic requirements of the chance and risk management process to identify minimum and consistency requirements.
-
(d)
Selection of techniques, measures and methods supporting the process steps, in particular risk for risk assessment.
-
(e)
Identification, selection and pre-screening of best practices for urban security enhancement.
-
(f)
Software tool design and implementation of the urban security and safety enhancement process.
-
(g)
Conduction of an application case in an urban residential area.
-
(h)
Observations and recommendations for further improvements, tailoring of the security and resilience enhancement process.
The development of the approach and the implementation process was explained. In particular, how semiformal SysML modelling can be leveraged to better tailor the 5 steps and requirements of ISO 31000 to the urban domain. The application of risk management leads to a structured approach to control and improve security within given scenarios.
The paper also showed how the iterative and communicative approach converges to overall acceptable risks when improvement measures are selected that are considered efficient and effective. The paper documented the risk assessment approach, its methodology and implementation through the IDAS application software tool and its validation in the Vauban district case study.
The following findings can be derived from the real case study on the application of the IDAS method. Various stakeholders were involved within an interdisciplinary team, who allowed a comprehensive picture of the risks to be compiled, numerous possible measures to be determined and appropriate compromises to be made in the risk assessment.
During the application of the IDAS expert tool, the need for a practical introduction to the risk management process for practitioners as well as the big advantages of a tool supported risk management became apparent in a moderated discussion round. The documentation of the results within the case study work enabled the structured recording of objectives, risks in terms of their probability and consequences, and improvement measures. The tool supports the identification and definition of interrelationships and allows the evaluation of objectives, risks and measures according to defined criteria.
In conclusion, it can be stated that the presented risk-based approach to urban safety management can accelerate the achievement of urban safety management objectives in a systematic, participatory and citizen-oriented way. Among the most important advantages of the approach presented here are the rich application context, the efficient procedure, the various possibilities of graphical representation, the targeted selection of measures, and the monitoring of results through regular execution. In this way, the IDAS approach can make a sustainable and effective contribution to improve urban safety.
Future work could concentrate on improving repositories for potential inputs, in particular regarding objectives, risks on objectives and improvement measures. Also, more averaging approaches could be provided to identify tendencies of stakeholder assessments even if groups are very heterogeneous and large. This includes assessment techniques to avoid group-enforced consensus making. Last but not least, the live presentation of the approach could be much improved in terms of graphics and direct distributed input of stakeholders, e.g. using smartphones.
Regarding repositories a possible straightforward future step will be to apply IDAS to a different domain and enhance the software in a way that domain specific best practice catalogues and techniques can easily be integrated. By this IDAS will provide the capability to be easily adapted to arbitrary domains.
Furthermore, future work could analyze the potential of the approach for (semi) automated risk analysis, in particular when risk related key performance indicators can be technically monitored and fed into the process automatically. Key performance indicators could be related to symptoms, e.g. number of disruptive events, or to (probable) causing factors, e.g. average person density at exposed times.
References
ASP.NET (2020). Microsoft. Available online at https://dotnet.microsoft.com/apps/aspnet, checked on 4/28/2020
AUDITS (2020): Methodological tools for the definition of local security policies in Europe (AUDITS). EFUS-European Forum For Urban Security. Available online at https://efus.eu/en/topics/tools-and-methods/audits-and-evaluation/efus/9883/, checked on 5/6/2020
Ball DJ, Ball-King L (2013) Safety management and public spaces: restoring balance. Risk Analysis Off Publ Soc Risk Anal 33(5):763–771. https://doi.org/10.1111/j.1539-6924.2012.01900.x
Bansal N, Mukherjee M, Gairola A (2013) URBAN RISK MANAGEMENT. In: Conference: International Conference on Challenges in Disaster Mitigation and Management. At: 15–17 February, 2013 at Centre of Excellence in Disaster Mitigation and Management, Indian Institute of Technology Roorkee – 247 667, INDIA. Available online at https://www.researchgate.net/publication/332330497_URBAN_RISK_MANAGEMENT. Accessed 5 May 2020
Basu A, Blanning RW (1994) Metagraphs: a tool for modeling decision support systems. Manag Sci 40(12):1579–1600
Baumann D, Häring I, Siebold U, Finger J (2014) A web application for urban security enhancement. In: Thoma K, Häring I, Leismann T (eds) 9th Future Security. Security Research Conference. Future Security. Berlin, September 16–18, 2014. Security Research Conference. Stuttgart: Fraunhofer Verlag, pp 17–25
BESECURE (2019): Best practice Enhancers for Security in Urban Environments. FP7-SECURITY - Specific Programme "Cooperation": Security. Grant agreement ID: 285222. Available online at https://cordis.europa.eu/project/id/285222. Accessed 21 Jan 2020
Bevilacqua C, Trillo C, Pizzimenti P, Maione C (2015) Urban Form and Urban Security: Insights from a Southern Italian Neighbourhood. In: Schrenk M, Popovich VV, Zeile P, Elisei P, Beyer C (eds) REAL CORP 2015. Plan Together - Right Now - Overall. From Vision to Reality for Vibrant Cities and Regions. Proceedings of the 20th International Conference on Urban Planning, Regional Development and Information Society. neue Ausg. Vienna: CORP - Competence Center of Urban and Regional Planning, pp 651–659
Carla N, Sebastian S (2016) Methods and tools for a strategic approach to urban security. European Forum for Urban Security, Paris
Crabbe S (2015) BESECURE: best practice enhancers for security in urban regions (9). Eur CIIP Newsl (ECN) 1:21–24
CTC (2019) Grüne Liste Prävention – CTC - Datenbank empfohlener Präventionsprogramme. CTC-Communities that care. Available online at https://www.gruene-liste-praevention.de/nano.cms/datenbank/information. Accessed 21 Jan 2020
de Oliveira UR, Marins FAS, Rocha HM, Salomon VAP (2017) The ISO 31000 standard in supply chain risk management. J Clean Prod 151:616–633. https://doi.org/10.1016/j.jclepro.2017.03.054
Deming WE (1998) Out of the crisis, vol 26. Massachusetts Institute of Technology, Cambridge
DFK & LPR NI (2020) Wegweiser Prävention. Edited by Deutsches Forum Kriminalprävention (DFK) & Landespräventionsrat Niedersachsen (LPR NI). Available online at https://www.wegweiser-praevention.de/
EFUS (2020) European forum for urban security. Available online at https://efus.eu/en/. Accesed 21 Jan 2020
Ekblom P (2008) The 5Is framework: a practical tool for transfer and sharing of crime prevention and community safety knowledge: Design Against Crime Research Centre, Central Saint Martins College of Art and Design, University of the Arts London. Available online at http://www.designagainstcrime.com/files/crimeframeworks/04_5i_framework.pdf.
Friedenthal S, Moore A, Steiner R (2011) A practical guide to SysML. The systems modeling language, 2nd edn. Morgan Kaufmann, Amsterdam, Boston
Furlong A, Cartmel F, Powney J, Hall S (1997) Evaluating youth work with vulnerable young people. Edinburgh: Scottish Council for Research in Education (SCRE) (SCRE Research Report n.83)
Gössling S, Schröder M, Späth P, Freytag T (2016) Urban space distribution and sustainable transport. Transp Rev 36(5):659–679. https://doi.org/10.1080/01441647.2016.1147101
Grießhammer R, Brohmann B (2015) 4 Green City Freiburg. In: Grießhammer R, Brohmann B (eds) How Transformations and Social Innovations Can Succeed. Nomos, pp 59–64
Häring I, Ebenhöch S, Stolz A (2016) Quantifying resilience for resilience engineering of socio technical systems. Eur J Sec Res 1(1):21–58
Hodgkinson T, Saville G, Andresen MA (2020) The diffusion of detriment: tracking displacement using a city-wide mixed methods approach. Br J Criminol 60(1):198–218
Höfflin P (2020) Eine Stadt für alle. Sozialwirtschaft 30(1):20–22. https://doi.org/10.5771/1613-0707-2020-1-20
Holevas K, Bonazountas M, Sabanegh R (2005) Urban risk assessment and management in the enlarged EU, recent status and trends. In: Brebbia CA, Bucciarelli T, Garzia F, Guarascio M (eds) Safety and Security Engineering, vol. 82. Vatican City State Senate Republic Chamber Deputies Presidency Council Minist Italy CNR, Italy Presidency Council Minist, Dept Civil Protect Natl Inst Nucl Phys Natl Inst Geophys & Volcanol Minist Innovat & Technologies Minist Commun Univ & Res, Minist Educ Minist Environm Minist Hlth Minist Infrastruct & Transport Minist Product Activities Natl Council Engineers FASTIGI Consortium WIT Transact Built Environm Wessex Inst Technol Univ Rome La Sapienza, Fac Engn Natl Fire Dept. Ashurst Lodge, Southampton SO40 7AA, Ashurst, England: WIT Press (WIT transactions on the built environment), pp 223–232
IEC/ISO 31010:2009 (2009) Risk management – Risk assessment techniques
ISO 14001:2015 (2015) Environmental management systems - Requirements with guidance for use. Available online at https://www.iso.org/standard/60857.html, checked on 10/17/2020
ISO 19600:2014 (2014) Compliance management systems - Guidelines. Available online at https://www.iso.org/standard/62342.html, checked on 10/17/2020
ISO 22301:2019 (2019) Security and resilience — Business continuity management systems — Requirements. Available online at https://www.iso.org/standard/75106.html, checked on 10/17/2020
ISO 22320:2018 (2018) Security and resilience — Emergency management — Guidelines for incident management. Available online at https://www.iso.org/standard/67851.html, checked on 10/17/2020
ISO 28000:2007 (2007) Specification for security management systems for the supply chain. Available online at https://www.iso.org/standard/44641.html, checked on 10/17/2020
ISO 31000:2009 (2009): Risk management — Principles and guidelines: ISO.
ISO 31000:2018 (2018) Risk management – Guidelines: ISO
ISO 31010 (2010) Risikomanagement: Verfahren zur Risikobeurteilung (IEC/ISO 31010:2009): Deutsche Fassung EN 31010:2010. DIN - Deutsches Institut für Normung e.V. Berlin: Beuth Verlag GmbH
ISO/AWI 22371:2020 (2020) Security and resilience - Urban resilience - Framework, model and guidelines for strategy and implementation, Under development. Available online at https://www.iso.org/standard/50274.html; https://www.iso.org/news/ref2412.html, checked on 10/17/2020
Khazai B, Bendimerad F, Cardona O.-D, Carreno M.-L, Barbat A.-H, Burton C.-G (2015) A guide to measuring urban risk resilience. Principles, tools and practice of urban indicators. Earthquakes and Megacities Initiative. Available online at https://www.cedim.kit.edu/download/Guidebook_URR_ME-July-2015.pdf, checked on 5/5/2020
Leeson GW (2018) The growth, ageing and urbanisation of our world. Popul Ageing 11(2):107–115. https://doi.org/10.1007/s12062-018-9225-7
Leitch M (2010) ISO 31000:2009–The new international standard on risk management. Risk Anal Off Publ Soc Risk Anal 30(6):887–892. https://doi.org/10.1111/j.1539-6924.2010.01397.x
Lewis M, Hartley J (2001) Evolving forms of quality management in local government: lessons from the Best Value pilot programme. Policy Polit 4:477–496
March JG, Olsen JP (1989) Rediscovering institutions: the organizational basis of politics. The Free press, New York
Microsoft (2016a) Code generation and T4 Text Templates. Available online at http://msdn.microsoft.com/de-de/library/bb126445.aspx
Microsoft (2016b) The Official Microsoft IIS Site. Available online at https://www.iis.net/
Mozilla (2016) JavaScript Reference. Available online at https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference
National Institute of Justice (2020) CrimeSolutions. Available online at https://www.crimesolutions.gov/default.aspx
Neef M, Duijnhoven H, van Buul-Besseling K (2014) Enhancing urban security policy design – the need for an evidence-based approach. In: Thoma K, Häring I, Leismann T (eds) 9th Future Security. Security Research Conference. Future Security. Berlin, September 16–18, 2014. Security Research Conference. Stuttgart: Fraunhofer Verlag, pp 618–620
Object Management Group (2012) OMG Systems Modeling Language (OMG SysML™). Version 1.3. Available online at http://www.omg.org/spec/SysML/1.3/, checked on 10/15/2014
Public Health Agency of Canada (2020): The Canadian Best Practices Portal. Available online at https://cbpp-pcpe.phac-aspc.gc.ca/
Purdy G (2010) ISO 31000:2009-Setting a new standard for risk management. Risk Anal 30(6):881–886. https://doi.org/10.1111/j.1539-6924.2010.01442.x
Raz T, Hillson D (2005) A comparative review of risk management standards. Risk Manag 7(4):53–66. https://doi.org/10.1057/palgrave.rm.8240227
Renn O, Klinke A, Schweizer P-J (2018) Risk governance: application to urban challenges. Int J Disaster Risk Sci 9(4):434–444. https://doi.org/10.1007/s13753-018-0196-3
Richards CW (2004) Certain to win. The strategy of John Boyd, applied to business. [Philadelphia, Pennsylvania]: Xlibris
Schoppe CA, Häring I, Siebold U (2013) Semi-formal modeling of risk management process and application to chance management and monitoring. European Safety and Reliability Conference (ESREL) 2013, Safety, Reliability and Risk Analysis: Beyond the Horizon, Editors: R.D.J.M. Steenbergen, P.H.A.J.M. van Gelder, S. Miraglia, A.C.W.M. Vrouwenvelder, 30.09–02.10.2013, Pages 1411–1418, Amsterdam, Netherlands, Taylor and Francis Group, London, ISBN 9781138001237, http://www.crcpress.com/product/isbn/9781138001237
Schoppe C, Zehetner J, Finger J, Baumann D, Siebold U, Häring I (2014) Risk assessment methods for improving urban security. In: Nowakowski T, Młyńczak M, Jodejko-Pietruczuk A, Werbińska-Wojciechowska S (eds) Safety and reliability. Methodology and applications. European Safety and Reliability Conference, ESREL 2014. Wrocław, Poland, 14–18 September 2014. London: Taylor & Francis Group, pp 701–708
Siebold U, Finger J, Baumann D, Häring I (2015): Decision support for urban security: a web application for risk managements. Project booklet BESECURE (Best Practice Enhancers for Security in Urban Environments), pp 55–58
Sozial- und Sicherheitsdirektion, Stadt Luzern (2013) Sicherheitsbericht Stadt Luzern 2013. Beurteilung der Sicherheitslage (Klimawandel und Sicherheit). EBP Schweiz AG. Available online at https://zora-cep.ch/cmsfiles/2013-07-22_sicherheitsbericht_stadt_luzern_2013_def.pdf, checked on 5/6/2020
Sozial- und Sicherheitsdirektion, Stadt Luzern (2019) Sicherheitsbericht Stadt Luzern 2019. Beurteilung der Sicherheitslage (Klimawandel und Sicherheit). EBP Schweiz AG. Available online at https://www.ebp.ch/de/pdf/generate/node/1957, checked on 5/6/2020
Steffen W (Ed.) (2014) Report for the 19th German Congress of Crime Prevention. DPT-Deutscher Präventionstag. Karlsruhe, 12.05.-14.05.2014. Available online at https://www.praeventionstag.de/dokumentation/download.cms?id=2065&datei=1-Wiebe-SteffenF_2065.pdf, checked on 1/21/2020
The Violence Prevention Alliance (2020) Global campaign for violence prevention. Available online at https://www.who.int/violenceprevention/en/
The World Bank (2020) Building urban resilience: an evaluation of the world bank group's evolving experience (2007–2017). Available online at https://openknowledge.worldbank.org/handle/10986/32622.
Thoma K, Scharte B, Hiller D, Leismann T (2016) Resilience engineering as part of security research: definitions, concepts and science approaches. Eur J Secur Res 1(1):3–19. https://doi.org/10.1007/s41125-016-0002-4
Weilkiens T (2007) Systems engineering with SysML/UML. Modelingm analysis, design. Morgan Kaufmann (The OMG Press), Burlington, Mass
Welsh BC, Farrington DP (2008) Effects of improved street lighting on crime. Campbell Syst Rev 4(1):1–51. https://doi.org/10.4073/csr.2008.13
Acknowledgements
This publication results in parts from the BESECURE project (Best practice Enhancers for Security in Urban Environments, see https://cordis.europa.eu/project/id/285222), funded by the European Union FP7 Security Programme under grant agreement ID 285222. A further partial funding source is the RESILENS project (Realising European Resilience for Critical infrastructure, see https://cordis.europa.eu/project/id/653260), funded by the European Union Horizon 2020 Societal Challenges program under the grant agreement ID 653260.
Funding
Open Access funding enabled and organized by Projekt DEAL.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Finger, J., Ross, K., Häring, I. et al. Open Chance and Risk Management Process Supported by a Software Tool for Improving Urban Security. Eur J Secur Res 6, 39–71 (2021). https://doi.org/10.1007/s41125-021-00072-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s41125-021-00072-6